Aug. 7, 2020
Updated Switzerland-based IT consultant Tillie Kottmann on Thursday published a trove of confidential Intel technical material, code, and documents related to various processors and chipsets. A spokesperson for Intel told us the information was likely taken from its Resource and Design Center, which is a private library of resources for computer manufacturers and the like to build systems using Intel’s silicon. Access to this center is not open to the public as its content is intended to be used, for instance, to craft firmware and design motherboards compatible with Chipzilla’s microprocessors.
Jun. 22, 2020

An activist group has published on Friday 296 GB of data they claim have been stolen from US law enforcement agencies and fusion centers. The data has been made available online on a searchable portal. According to the BlueLeaks portal, the leaked data contains more than one million files, such as scanned documents, videos, emails, audio files, and more.
Jun. 9, 2020

Earlier this year, Bleeping Computer reported how invite links to private groups of messaging apps like WhatsApp and Telegram were visible on Google, letting anyone join the groups. This week, security researcher Athul Jayaram highlighted an issue with WhatsApp’s “wa.me” domain “leaking” contact phone numbers on Google. As stated by Jayaram and confirmed by BleepingComputer, there is no “robots.txt” file on “wa.me” or “api.whatsapp.com” domains that instructs search engines not to crawl phone numbers on the website.
Jan. 24, 2020

UpGuard can now disclose that a repository hosted on GitHub with data from an Amazon Web Services engineer containing personal identity documents and system credentials including passwords, AWS key pairs, and private keys has been secured from public access. The data was committed to a public repository on the morning of 13 January, 2020. It was detected within half an hour by UpGuard analysts, reported to AWS Security, and secured that same day
Nov. 29, 2018
Today I wanna write about a finding I discovered during a research project where the aim was to find critical vulnerabilities in Alexa Top 1 Million websites. The main focus was to discover common configuration issues which do not require sophisticated exploits, which are easy to find and which can have a high impact on businesses. Some results of this research were presented at ITSECX 2018, an Austrian IT-Security conference.
Jun. 2, 2018

A popular fitness app that claims over six million users was leaking private and sensitive data, including health information and private messages sent between users. PumpUp, an Ontario-based company, bills itself as a fitness community, allowing subscribers to discover new workouts and record their results, and get advice from fitness coaches and other users. But the company left a core backend server, hosted on Amazon’s cloud, exposed without a password, allowing anyone to see who was signing on and who was sending messages — and their contents — in real-time.
May. 18, 2018
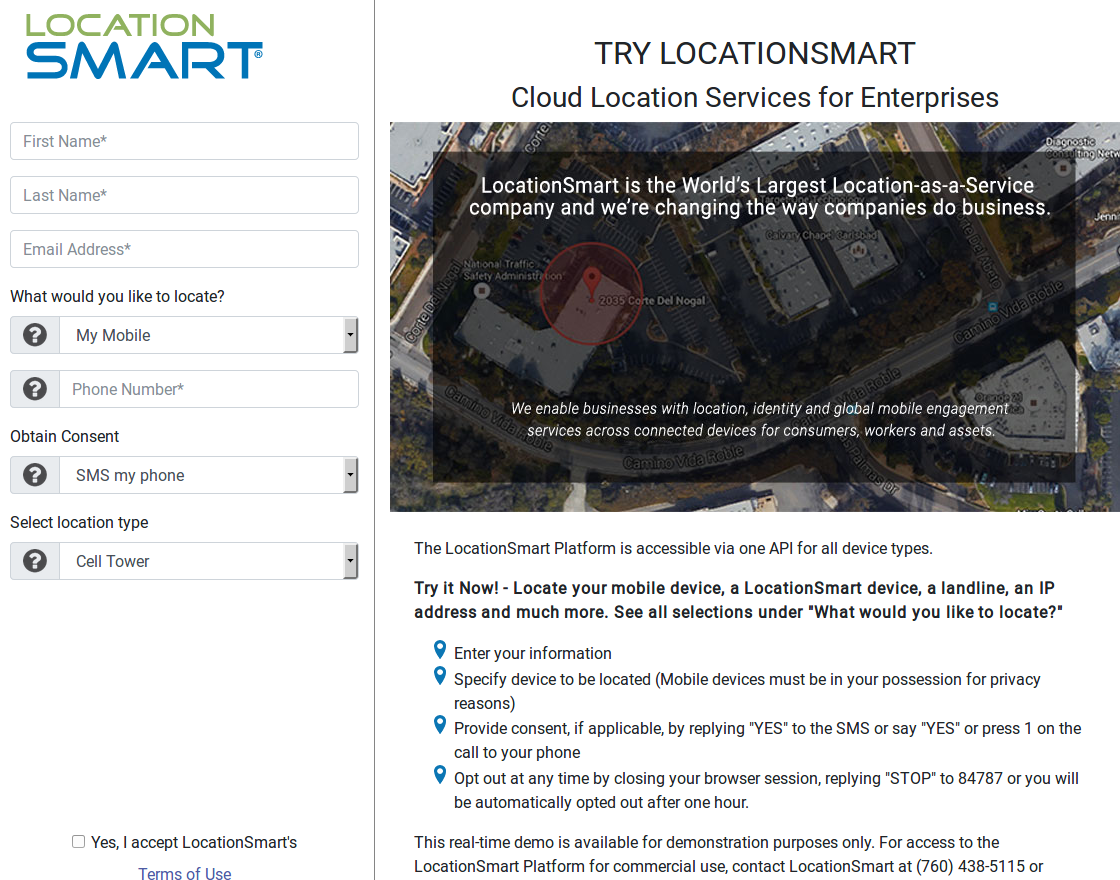
LocationSmart’s demo is a free service that allows anyone to see the approximate location of their own mobile phone, just by entering their name, email address and phone number into a form on the site. LocationSmart then texts the phone number supplied by the user and requests permission to ping that device’s nearest cellular network tower. Once that consent is obtained, LocationSmart texts the subscriber their approximate longitude and latitude, plotting the coordinates on a Google Street View map.
May. 16, 2018

In March 2017, the FBI agents raided the Manhattan apartment of former NSA and CIA operative Joshua Schulte looking for top secret documents and hacking tools that the defendant allegedly leaked to WikiLeaks. We don’t know if they found what they were looking for, but according to court transcripts and documents reviewed by Motherboard, the feds did find at least 10,000 images of child porn on his personal computer, and an IRC-focused file-sharing server that had at least 5 terabytes of data on it. Roughly two weeks before the raid, on March 7, 2017, WikiLeaks started releasing top secret documents allegedly stolen from a CIA hacking group.
Apr. 26, 2018

Kromtech Security said that it found the unprotected data on March 30, adding that it included a treasure-trove of information ranging from “full names, (street) addresses, email addresses, encrypted passwords, wallet information, along with links to scanned passports, driver’s licenses and other IDs,” according to the researchers.
Source: threatpost.com
Apr. 26, 2018

Update your Careem passcode, and then update your password on any other accounts using the same or similar details. Make your new one good and strong. Here’s how.
And if we’ve said it once, we’ve said it a million times: reusing passwords is really, truly a terrible idea. So don’t! Watch out for spearphishers.
Unsolicited communications that try to get personal information out of you, or send you to a site that wants your account credentials, should be greeted with your hairiest of eyeballs. Don’t click on links or download attachments from unfamiliar emails. Keep an eye on your bank account and credit card statements for suspicious activity.
Apr. 24, 2018
MEDantex, a Kansas-based company that provides medical transcription services for hospitals, clinics and private physicians, took down its customer Web portal last week after being notified by KrebsOnSecurity that it was leaking sensitive patient medical records — apparently for thousands of physicians.
Source: krebsonsecurity.com
Apr. 22, 2018
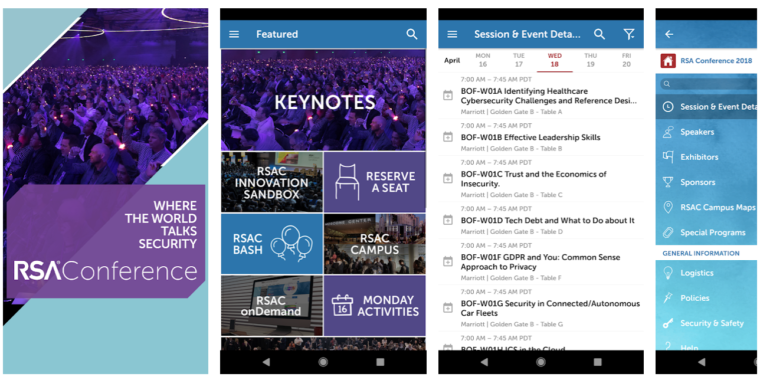
A mobile application built by a third party for the RSA security conference in San Francisco this week was found to have a few security issues of its own—including hard-coded security keys and passwords that allowed a researcher to extract the conference’s attendee list. The conference organizers acknowledged the vulnerability on Twitter, but they say that only the first and last names of 114 attendees were exposed.
Apr. 18, 2018

Millions of apps leak personal identifiable information such as name, age, income and possibly even phone numbers and email addresses. At fault are app developers who do not protect ad-targeting data transmitted to third-party advertisers.
Source: threatpost.com
Apr. 7, 2018

Secure, affordable and convenient. That’s how the makers of the FUZE Card describe their creation, designed to act as a whole wallet in a single thin device. It can store up to 30 different credit cards and uses a lock to protect the data within.
Such a hit was it with consumers it raised nearly $2.5 million in Indiegogo funding, with the original cost starting at $160.
Apr. 4, 2018
First, the proof that I reported this, and the beginning of the timeline. I reported this vulnerability in August 2017, which is shown by the following email exchange with Panera Bread’s Information Security Director, Mike Gustavison. After attempting to contact them through a generic [email protected] email address (which bounced), Twitter and even LinkedIn and email messages to Mike Gustavison (whose information I found on LinkedIn), I was formally introduced by an industry contact who had a mutual connection.
Apr. 4, 2018
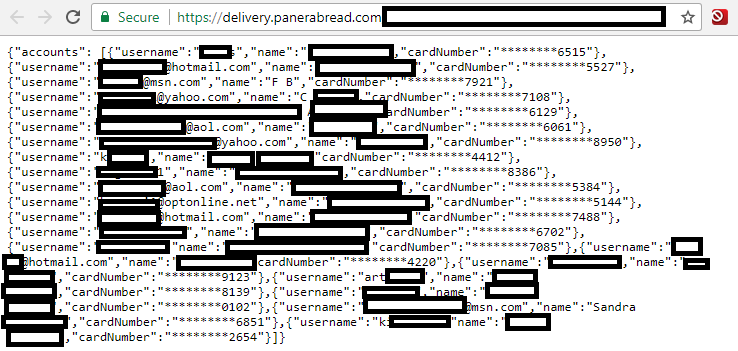
The data available in plain text from Panera’s site appeared to include records for any customer who has signed up for an account to order food online via panerabread.com. The St. Louis-based company, which has more than 2,100 retail locations in the United States and Canada, allows customers to order food online for pickup in stores or for delivery.
Source: krebsonsecurity.com
Mar. 26, 2018

Coming amidst a firestorm of scrutiny about how political operations can use and harvest consumer information, including from social media networks like Facebook, the UpGuard Cyber Risk Team can now reveal that a large code repository originating from AggregateIQ, a Canadian political data firm active in the 2016 US presidential race, was left publicly downloadable online. Revealed within this repository is a set of sophisticated applications, data management programs, advertising trackers, and information databases that collectively could be used to target and influence individuals through a variety of methods, including automated phone calls, emails, political websites, volunteer canvassing, and Facebook ads. Also exposed among these tools are numerous credentials, keys, hashes, usernames, and passwords to access other AIQ assets, including databases, social media accounts, and Amazon Web Services repositories, raising the possibility of attacks by any malicious actors encountering the exposure.
Mar. 25, 2018

According to the researcher Giovanni Collazo, querying the popularShodan search engine he found almost 2,300 servers exposed online that were runningetcd, which is a distributed key value store that provides a reliable way to store data across a cluster of machines.
Source: securityaffairs.co
Mar. 21, 2018

On Monday, the Feds confirmed to The Register they have executed a search warrant at the Virginia home of John Glenn Weed, who worked for the National Reconnaissance Office – which runs Uncle Sam’s spy satellite fleet. The NRO called in the g-men after a screenshot of its classified source code was posted in 2017 on a Facebook profile belonging to one William Amos.
Mar. 5, 2018
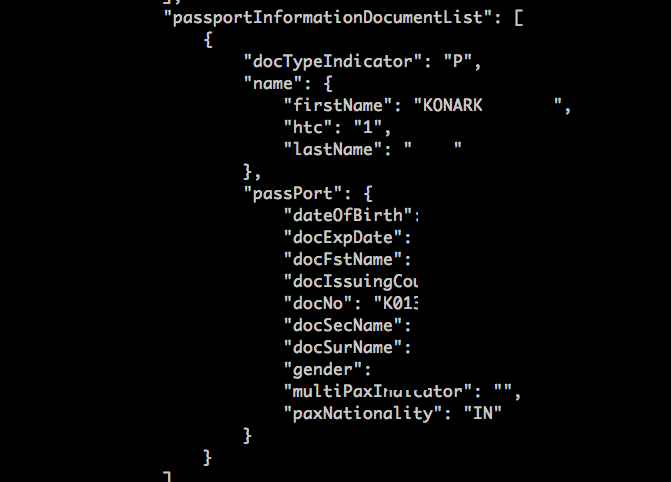
Now imagine this, I said “You try to check-in for your flight online, and see the error message — This booking does not exist. You try again, this surely is a mistake. Nope, still the same error message.
The call center person repeats the same words. This has to be a mistake! You check your email, and there it is — staring back at you — email confirmation of cancellation.



















