How I Dumped eBay Japan’s Website Source Code
Today I wanna write about a finding I discovered during a research project where the aim was to find critical vulnerabilities in Alexa Top 1 Million websites. The main focus was to discover common configuration issues which do not require sophisticated exploits, which are easy to find and which can have a high impact on businesses. Some results of this research were presented at ITSECX 2018, an Austrian IT-Security conference.
The slides of my talk can be found here. I found out, that www.ebay.co.jp runs a version control repository on their production site which was not properly secured. This gave me access to the .git folder in the webroot directory which further allowed me to download the entire source code of www.ebay.co.jp including database passwords and much more.
The initial research for this topic was performed back in 2015 by internetwache.org – their blog post about their findings can be found here and I highly recommend to read it! I used the GitTools published by internetwache.org which can be found here.
I ran this script through millions of Alexa Top 1 Million subdomains. When checking the results, eBay Japan popped up.
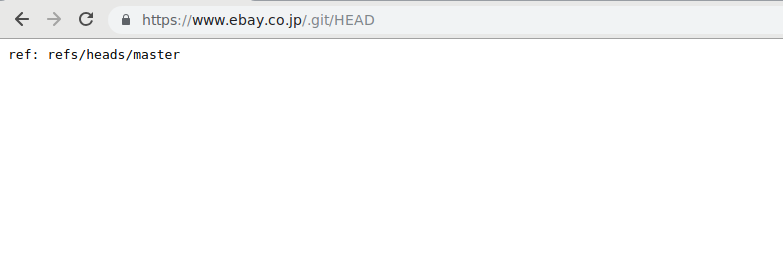
In order to initially verify the bug, I accessed www.ebay.co.jp/.git/HEAD and the following came up:
Source: slashcrypto.org