Cyber security news and services
Critical Cisco WebEx Bug Allows Remote Code Execution

The bug (CVE-2018-0264) exists in the platform’s Recording Player for Advanced Recording Format (ARF), which allows users to play back WebEx meeting recordings. The player is installed automatically when a user accesses a recording file hosted on a WebEx server. Cisco WebEx Business Suite meeting sites, Cisco WebEx Meetings sites, the Cisco WebEx Meetings Server and the Cisco WebEx ARF Player itself are all affected.
…Nigerian Email Scammers Are More Effective Than Ever

You would think that after decades of analyzing and fighting email spam, there’d be a fix by now for the internet’s oldest hustle—the Nigerian Prince scam. There’s generally more awareness that a West African noble demanding $1,000 in order to send you millions is a scam, but the underlying logic of these “pay a little, get a lot” schemes, also known as 419 fraud, still ensnares a ton of people. In fact, groups of fraudsters in Nigeria continue to make millions off of these classic cons.
…Oscar Mayer’s Cringey ‘Cryptocurrency’ Promotion Got Hit With a Cease-and-Desist

Because we live in a meme-saturated hellworld, meat and cold cut company Oscar Mayer is running a promotion called “Bacoin,” a cryptocurrency-inspired redemption program designed to get people to promote bacon on social media. This is lame and I’m sorry to have made you read that, but dear reader, something has happened that makes this branding play improbably, unbelievably, sort of interesting.
…Cyberespionage operation targets Android users in the Middle East

ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation infect Android devices using several generations of malware, with the attackers including new features in each iteration. We label them from v1-v4, with v4 being the most recent version deployed in 2017.
From the technical point of view, the evolution of ZooPark has shown notable progress: from the very basic first and second versions, the commercial spyware fork in its third version and then to the complex spyware that is version 4. This last step is especially interesting, showing a big leap from straightforward code functionality to highly sophisticated malware.
…New Rowhammer Attack Hijacks Android Smartphones Remotely
The proof of concept attack the researchers created to demonstrate their technique takes about two minutes, from a malicious site loading their javascript in the browser to running code on the victim’s phone. It can only run that code, however, within the privileges of the browser. That means it can potentially steal credentials or spy on browsing habits, but it can’t gain deeper access without a hacker exploiting other bugs in the phone’s software.
…Hello Kitty: Malware targets Drupal to mine for cryptocurrency

Kitty, a Monero cryptocurrency which utilizes open-source mining software for browsers, executes a bash script, kdrupal.php, which is written to an infected server disc. This then establishes a backdoor into an infected system separate from the Drupal vulnerability.
Source: zdnet.com
…Eltoo: A Simplified Update Mechanism for Lightning and Off-Chain Contracts

A little over a year ago, the three Lightning Network implementation teams joined forces to work on a common specification for the protocol stack. Now that both that specification and our three implementations are becoming stable and usable, it is time to look forward: to further improve the protocol, to add new features, to simplify, and to fix downsides.
Source: blockstream.com
…Don’t Give Your DNA to Giant Genetic Databases

DNA sequencing is cheap and accessible; companies with large databases of genetic material have to think about how (and if) they’ll protect it; and yes, the FBI is interested. Much of the panel focused on two news items:
Source: vice.com
…Volkswagen Cars Open To Remote Hacking, Researchers Warn

The vulnerability was discovered inthe Volkswagen Golf GTE and an Audi3 Sportback e-tron, which were both manufactured in 2015. Computest researchers Daan Keuper and Thijs Alkemade, who discovered the flaw, said that under certain conditions the IVI vulnerability could enableattackers to commandeer the on-board microphone to listen in on the conversations of the driver, turn the microphone on and off, and access the system’s complete address book and the conversation history. There is also a possibility of hackers tracking the car through the navigation system at any given time, they said.
…A New Cryptocurrency Mining Virus is Spreading Through Facebook
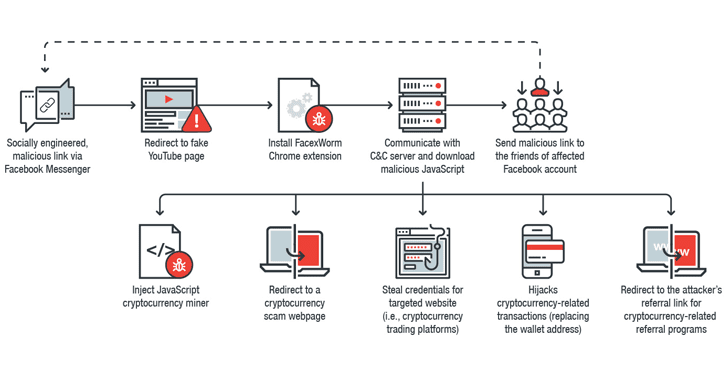
To spread itself further like a worm, the malware requests OAuth access token for the Facebook account of the victim, using which it then automatically obtains the victim’s friend list and sends that malicious, fake YouTube video link to them as well.
Source: thehackernews.com
…The ‘Holy Grail’ of Cryptocurrency Looks Like the Banks We Already Know and Hate

Cryptocurrencies came into being with an anti-bank fervor that still runs hot in the technology community. Libertarians see Bitcoin and the rest as an alternative to fiat money controlled by financial institutions and the government. But the quest to create a cryptocurrency with a stable $1 value—a so-called “stable coin”—has startups acting like banks.
Source: vice.com
…7-Zip: From Uninitialized Memory to Remote Code Execution
Very abstractly, the bug can be described as follows: The initialization of some member data structures of the RAR decoder classes relies on the RAR handler to configure the decoder correctly before decoding something. Unfortunately, the RAR handler fails to sanitize its input data and passes the incorrect configuration into the decoder, causing usage of uninitialized memory.
Source: landave.io
…China Claims It’s Scanning Workers’ Brainwaves to Increase Efficiency and Profits

At a factory in Hangzhou, China, production line workers are allegedly being outfitted with brain-reading hats and helmets. They read workers’ emotions and use artificial intelligence algorithms to “detect emotional spikes such as depression, anxiety or rage,” according to the South China Morning Post.
Source: vice.com
…School District Pays $10,000 Bitcoin Ransom To Hackers After Cyberattack

And despite the nefarious nature of the school system’s lockdown, there is no criminal investigation into the matter because solving this crime is “impossible,” said Interim Leominster Police Chief Michael Goldman.
Source: cbslocal.com
…This malware checks your system temperature to sidestep sandboxing

By taking thermal readings, the Remote Access Trojan (RAT), which has become a recent menace in India, attempts to find out whether or not VMs are being employed for the purpose of decompiling efforts and reverse engineering.
Source: zdnet.com
…Man Who Hacked Jail Systems to Release His Friend Early Gets 7-Years in Prison

Konrads Voits of Ypsilanti, Michigan, has been sentenced to seven years and three months in prison for attempting to hack the Washtenaw County Jail computer system and modifying prison records to get his friend released early. Besides spending 87 months in prison, Voits has also been ordered to pay $235,488 in fine to Washtenaw County for the cost accrued in investigating and cleaning up the infiltration that resulted in the compromise of personal information of around 1,600 employees, the US Justice Department announced last week.
…Rediscovery, analysis and exploitation of a CIA zero-day MikroTik Vulnerability

This post outlines and presents the rediscovery, vulnerability analysis and exploitation of a zero-day vulnerability that was originally discovered and exploited by the CIA’s ‘Engineering Development Group’; remotely targeting MikroTik’s RouterOS embedded operating system that was discovered during the ‘Vault 7’ leak via WikiLeaks in March of 2017.
Source: seekintoo.com
…Spartacus ransomware: introduction to a strain of unsophisticated malware

There is nothing impressive about them, in fact just the opposite. I would say they are boring at best. So why are we writing about one of them?
The analysis of Spartacus can essentially be used as a base knowledge and reference for anyone analyzing variants of these basic .NET ransomware that they may come across in the future.
Source: malwarebytes.com
…This Russian Company Sells Zero-Day Exploits for Hospital Software

In one video uploaded to Vimeo, Gleg shows an exploit being used against a hospital health information management system (HHIMS). A list of MedPack updates includes a zero-day to replace files in a piece of software from a company called MediTEX. MediTEX makes scheduling software as well as a platform for documenting therapy and quality assurance for reproductive medicine, according to the company’s website.
…Home Chip Fabrication in 66 Steps

Without further ado, I present the first home(garage)made lithographically-fabricated integrated circuit – the “Z1” PMOS dual differential amplifier chip. I say “lithographically-fabricated” becauseJeri Ellsworth made the first transistors and logic gates (meticulously hand wired with conductive epoxy) andshowedthe world that this is possible. Inspired by her work, I have demonstratedICsmade by a scalable, industry-standard, photolithographic process.
Needless to say, this is the logical step-up from my previous replication of Jeri’s FET fabrication work.
…