Cyber security news and services
This coal power plant is being reopened for blockchain mining

That’s the idea behind the Blockchain Application Centre — an Aussie tech initiative that will see one of the country’s now-shuttered coal-fired power plants reopened to provide cheap power for blockchain applications.
Source: cnet.com
…Agent Smith: How I Build a Profitable Crypto Arbitrage Bot

Inefficiencies exploitable by arbitrage are inherintly zero sum: there is only a fixed amount of money to be made, and a lot of people are out to get it. This is the reason you won’t find any good arbitrage bots online.
Source: wizb.it
…People Who Own Cryptocurrency Are Getting Slammed With More Taxes Than They Expected

The IRS has since clarified that virtual currency is to be “treated as property for US federal tax purposes,” meaning any gains between the time bitcoins were bought and when they were sold (due to price deflation) must be treated as capital gains. Yet four years since Cross’s Reddit post, paying cryptocurrency taxes hasn’t gotten much easier. After Bitcoin’s biggest year yet—with a high of $19,000 USD for one bitcoin in December—most clients are getting hit with way more taxes than they anticipated.
…Malware monitor – leveraging PyREBox for malware analysis
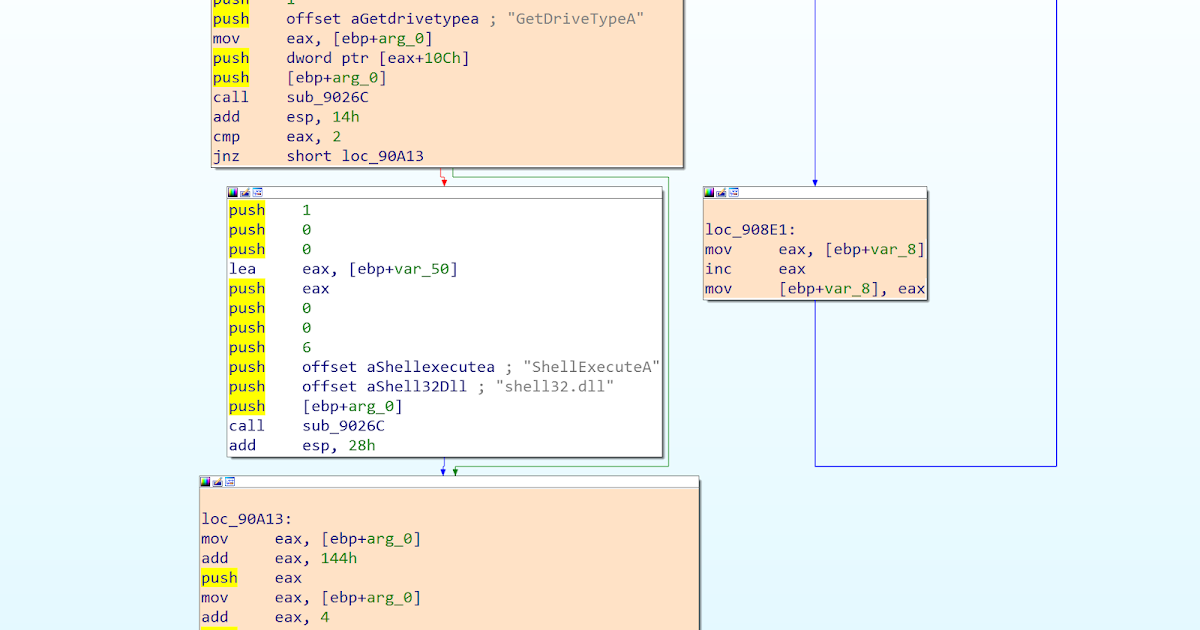
In July 2017 we released PyREBox, a Python Scriptable Reverse Engineering Sandbox as an open source tool. This project is part of our continuous effort to create new tools to improve our workflows. PyREBox is a versatile instrumentation framework based on QEMU.
It allows us to run a whole operating system in a virtual environment (emulator), and to inspect and modify its memory and registers at run-time. A small set of QEMU modifications allows users to instrument certain events such as instruction execution or memory read/writes.
…Coinsecure, not so secure: Millions in cryptocurrency stolen, CSO branded as thief

Coinsecure has become the latest in a long line of cryptocurrency exchanges which has lost investor funds to attack — but in this case, it appears to be an inside job.
Source: zdnet.com
…Goodbye ICOs, hello ILPs?

The gold-rush mentality currently surrounding the use of initial coin offerings (ICOs) has at times led to projects being used irresponsibly and investors suffering harm as a result. To date, no jurisdiction has provided a bespoke set of legal and technical controls to manage this risk. Instead, some have acted retrospectively by either banning ICOs or applying existing regulatory frameworks relating to other asset classes that are not necessarily compatible.
…An Alleged $660 Million ICO Scam Sparked a Protest In Vietnam

According to Reuters, dozens of people gathered outside the offices of Modern Tech JSC alleging “the largest ever cryptocurrency fraud involving 15 trillion dong,” which works out to more than $650 million USD. According to local news outlet Tuoi Tre News, the protesters allege that Modern Tech defrauded more than 30,000 investors by encouraging them to invest in digital tokens—called IFan and Pincoin—with the promise of regular payouts in real money.
…Cops Around the Country Can Now Unlock iPhones, Records Show

A Motherboard investigation has found that law enforcement agencies across the country have purchased GrayKey, a relatively cheap tool for bypassing the encryption on iPhones, while the FBI pushes again for encryption backdoors.
Source: vice.com
…List of the top smart contract vulnerabilities

This project is an initiative of NCC Group. It is an open and collaborative project to join efforts in discovering smart contract vulnerabilities within the security community.
Source: dasp.co
…PowerHammer: Exfiltrating Data from Air-Gapped Computers through Power Lines

In this paper we provide an implementation, evaluation, and analysis of PowerHammer, a malware (bridgeware [1]) that uses power lines to exfiltrate data from air-gapped computers. In this case, a malicious code running on a compromised computer can control the power consumption of the system by intentionally regulating the CPU utilization. Data is modulated, encoded, and transmitted on top of the current flow fluctuations, and then it is conducted and propagated through the power lines.
…New ‘Early Bird’ Code Injection Technique Helps APT33 Evade Detection

Researchers have identified what they are calling an Early Bird code injection technique used by the Iranian group APT33 to burrow the TurnedUp malware inside infected systems while evading anti-malware tools.
Source: threatpost.com
…Some Android Phone Manufacturers Lying to Users About Security Updates

SRL researchers Karsten Nohl and Jakob Lell spent two years analyzing Android devices, checking to see if the phones actually had installed the security patches that the software said it had. The pair found that many devices had what they call a “patch gap,” where the phone’s software would claim it was up to date with security patches but was, in reality, missing up to a dozen of the patches.
…All Your Base64 Are Belong To Us – Dynamic vs. Static Analysis of Web Content
I recently encountered an interesting phishing scheme when reviewing telemetry of incidents blocked by Trustwave Secure Web Gateway (SWG). My investigation into the scheme uncovered some interesting points and led me here:
Source: trustwave.com
…Breaking RSA OAEP with Manger Attack

The RSA cryptosystem has had its fair share of attacks over the years, but among the most impressive, you can find the infamous Bleichenbacher attack [Ble98], which doomed PKCS v1.5 in 1998. Nineteen years later, the ROBOT attack proved that the Bleichenbacher attack was still a concern today. Now, what alternatives to RSA PKCS v1.5 do we have?
Well, itssuccessor, RSA OAEP also known as RSA PKCS v2.1 is obviously a good candidate.
…Post-quantum confidentiality for TLS

In 2016, my colleague, Matt Braithwaite, ran an experiment in Google Chrome which integrated a post-quantum key-agreement primitive (NewHope) with a standard, elliptic-curve one (X25519). Since that time, the submissions for the 1st round of NIST’s post-quantum process have arrived. We thus wanted to consider which of the submissions, representing the new state of the art, would be most suitable for future work on post-quantum confidentiality in TLS.
…Thousands of hacked websites are infecting visitors with malware

The campaign, which has been running for at least four months, is able to compromise websites running a variety of content management systems, including WordPress, Joomla, and SquareSpace. That’s according to a blog post by Jérôme Segura, lead malware intelligence analyst at Malwarebytes. The hackers, he wrote, cause the sites to display authentic-appearing messages to a narrowly targeted number of visitors that, depending on the browsers they’re using, instruct them to install updates for Firefox, Chrome, or Flash.
…Breach at UK’s Great Western Railway: Commuters told to reset passwords

Great Western Rail is urging all customers to change their passwords after identifying a successful attack to access GWR.com accounts over the last week.
Source: co.uk
…Google, Microsoft, and Mozilla Put Their Backing Behind New WebAuthn API

Three major browser makers —Google, Microsoft, and Mozilla—have put their official backing behind a new W3C API called Web Authentication (WebAuthn) that is advertised as a reliable alternative to passwordless online authentication.
Source: bleepingcomputer.com
…Web Browsers Reject About Two-Thirds of Cookies
Ad serving firm Flashtalking analyzed 20 advertisers worldwide throughout Q4 2017 and found that 64% of their tracking cookies were either blocked or deleted by web browsers. According to the research, rejection rates on mobile devices were particularly high—75% of mobile cookies were rejected, compared with 41% on desktop.
Source: emarketer.com
…Cryptocurrency traders use gold to woo Muslim investors

A local start-up company founded last year, OneGram, is issuing a gold-backed cryptocurrency — part of efforts to convince Muslims that investing in cryptocurrencies complies with their faith.
Source: venturebeat.com
…