Cyber security news and services
Practical passwordless authentication comes a step closer with WebAuthn

The World Wide Web Consortium (W3C) and FIDO Alliance today announced that a new spec, WebAuthn (‘Web Authentication’) had been promoted to the Candidate Recommendation stage, the penultimate stage in the Web standards process.
Source: arstechnica.com
…How we made $100K arbitraging CryptoKitties
The inside story behind how we made $107K investing in CryptoKitties and briefly set the record for the highest sale ever. Later, we made ~$8K running an automated arbitrage bot.
Source: hackernoon.com
…After CryptoKitties, the ‘Cryptocollectibles’ Business Is Booming

Development for CryptoPets started just four days after CryptoKitties’ launch on November 28, and is basically a cross between Pokémon and CrytoKitties. Owners’ pets can battle each other, and those who put in time and effort to “train” their pets will increase their value in the “adoption center,” Mitchell Opatowsky, project manager at CryptoPets, explained to Motherboard in an email.
Source: vice.com
…China forces spyware onto Muslim’s Android phones, complete with security holes

JingWang (“clean internet” in Chinese) doesn’t just block access to specific websites. It also searches your Android phone for “illegal” images, audio recordings, and videos, and can upload them to an external server – alongside identifying details of your phone such as its IMEI number, model, phone number, and manufacturer.
Source: bitdefender.com
…Researchers Rickrolled Emergency Alert Sirens in Proof-of-Concept Hack

Hackers equipped with just a laptop and a $30 handheld FM radio could have hijacked the emergency alert system sirens of San Francisco. The hack could have made them go off whenever they wanted, and made the system broadcast custom messages, according to researchers.
Source: vice.com
…Whatever you do, don’t give this programmable payment card to your waiter

The makers of the programmable Fuze smart card say it’s powerful enough to be your wallet in one card yet secure enough to be used the same way as traditional payment cards—including trusting it to restaurant servers when paying the bill. But it turns out that convenience comes with a major catch. A flaw makes it possible for anyone with even brief physical control of the card to surreptitiously siphon all data stored on the device.
…Under a millimeter wide and powered by light, tiny cameras could hide anywhere
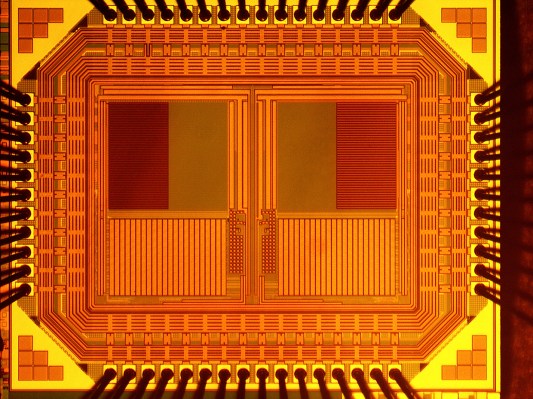
As if there weren’t already cameras enough in this world, researchers created a new type that is both microscopic and self-powered, making it possible to embed just about anywhere and have it work perpetually. It’s undoubtedly cool technology, but it’s probably also going to cause a spike in tinfoil sales.
Source: techcrunch.com
…Chinese Government Forces Residents To Install Surveillance App With Awful Security

In Xinjiang, a part of western China that a Muslim minority population calls home, the government forces residents to install an Android app that scans devices for particular files. Now, cybersecurity researchers have found that the so-called JingWang app has horrendous security practices for transferring data, and uncovered more details on what exactly the app does to phones.
Source: vice.com
…How to Mine Bitcoin for Free With Google BigQuery

Cryptocurrency miners are always looking for a way to save on electricity costs. Sometimes that involves funding huge mining operations moving to small towns to take advantage of cheap hydro power, or developing obscure mining rig set ups that use Teslas or human body heat as their source of power.
Source: vice.com
…What Is an ASIC Miner and Is It the Future of Cryptocurrency?

On April 6, Monero tweaked its mining algorithm “to curb any potential threat of ASICs and preserve ASIC resistance.” That same day, Ethereum core developers met to discuss whether they should change Ethereum’s algorithm and ultimately decided not to for the time being, much to the chagrin of the Ethereum community.
Source: vice.com
…Sodexo Filmology data breach – Users need cancel their credit cards

Sodexo food services and facilities management company notified a number of customers that it was the victim of a targeted attack on its cinema vouchers platform Sodexo Filmology.
Source: securityaffairs.co
…Hacker mines up to $1 million in Verge after exploiting major bug

Due to several bugs in the XVG code, you can exploit this feature by mining blocks with a spoofed timestamp. When you submit a mined block, as a malicious miner or pool, you simply set a false timestamp to this block one hour ago and XVG will then “think” the last block mined on that algorithm was one hour ago. Your next block, the subsequent block, will then have the correct time.
…New Matrix Ransomware Variants Installed Via Hacked Remote Desktop Services

Two new Matrix Ransomware variants were discovered this week by MalwareHunterTeamthat arebeing installed through hacked Remote Desktop services. While both of these variants encrypt your computer’s files, one is a bit more advanced with more debugging messages and the use of cipher to wipe free space.
Source: bleepingcomputer.com
…Cryptocurrency and taxes – it’s complicated

If you were mining for someone else, your earnings are considered wages, subject to regular wage withholding by your employer. If you were doing it as an independent contractor,those earnings have to be considered self-employment earnings. In other words, those earnings will not be reported as capital.
So you have both the initial difficulty of determining fair market value of the virtual currency and the added complication of properly categorizing your mining activity. Note, this is assuming employees or contractors are getting paid in cryptocurrency; regular salary paid in cash and similar payments are treated under standard income tax principles.
…Don’t Give Away Historic Details About Yourself
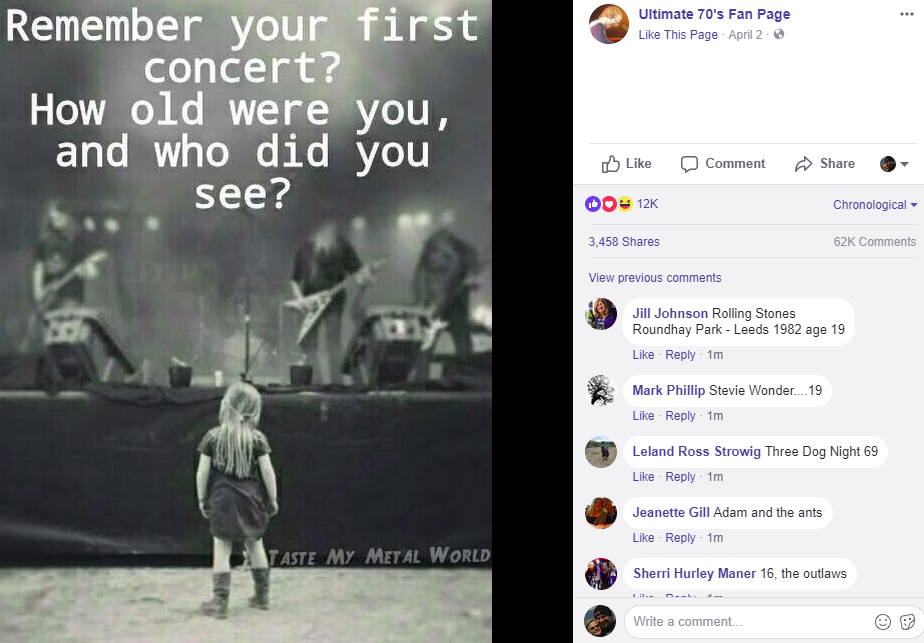
Social media sites are littered with seemingly innocuous little quizzes, games and surveys urging people to reminisce about specific topics, such as “What was your first job,” or “What was your first car?” The problem with participating in these informal surveys is that in doing so you may be inadvertently giving away the answers to “secret questions” that can be used to unlock access to a host of your online identities and accounts.
…How to keep your ISP’s nose out of your browser history with encrypted DNS

Encrypting DNS traffic between your device and a ‘privacy-focused’ provider can keep someone from spying on where your browser is pointed or using DNS attacks to send you somewhere else.
Source: arstechnica.com
…Iran hit by global cyber attack that left U.S. flag on screens
The statement said the attack, which hit internet service providers and cut off web access for subscribers, was made possible by a vulnerability in routers from Cisco which had earlier issued a warning and provided a patch that some firms had failed to install over the Iranian new year holiday.
Source: reuters.com
…Three Execs Get Prison Time for Pirating Oracle Firmware Patches

An Ohio court sentenced yesterday four high-ranking TERiX executives for their role in a pirating scheme through which they stole and resold Sun and Oracle firmware patches. Three of the four execs received prison sentences.
Source: bleepingcomputer.com
…Exploiting Bluetooth Low Energy using Gattacker for IoT – Step-by-Step Guide

Learn how to exploit Bluetooth Low Energy for IoT Devices using a step-by-step guide. In this post, we are using Gattacker to perform sniffing and replay based attacks.
Source: attify.com
…T-Mobile Stores Part of Customers’ Passwords In Plaintext, Says It Has ‘Amazingly Good’ Security

The company admitted on Twitter that it stores at least part of their customer’s passwords in plaintext. This is a big no-no in this day and age because if anyone breaches T-Mobile (and companies are breached all the time), they could likely guess or brute-force every user’s password. If the passwords were fully encrypted or hashed, it wouldn’t be that easy.
…