Cyber security news and services
Fin7: The Billion-Dollar Hacking Group Behind a String of Big Breaches
This week, Saks Fifth Avenue, Saks Off 5th, and Lord & Taylor department stores—all owned by The Hudson’s Bay Company—acknowledged a data breach impacting more than five million credit and debit card numbers. The culprits? The same group that’s spent the last few years pulling off data heists from Omni Hotels & Resorts, Trump Hotels, Jason’s Deli, Whole Foods, Chipotle: A mysterious group known as Fin7.
…Dot-cm Typosquatting Sites Visited 12M Times So Far in 2018
Those figures suggest that the total number of visits to these typosquatting sites in the first quarter of 2018 was approximately 12 million, or almost50 million hits per year. Certainly, not everyone visiting these sites will have the experience that Chambers’ users reported (being bombarded with misleading malware alerts and redirected to scammy and spammy Web sites), but it seems clear this network could make its operators a pretty penny regardless of the content that ends up getting served through it.
…Intel Admits It Won’t Be Possible to Fix Spectre (V2) Flaw in Some Processors
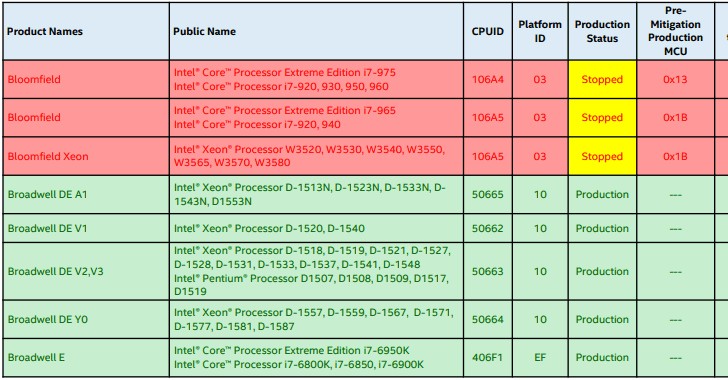
Some Intel processors will not receive security patches for the Spectre (variant 2) side-channel analysis attack.
Source: thehackernews.com
…Pocket cryptofarms

In recent months, the topic of cryptocurrency has been a permanent news fixture — the value of digital money has been see-sawing spectacularly. Such pyrotechnics could hardly have escaped the attention of scammers, which is why cryptocurrency fluctuations have gone hand in hand with all kinds of stories. These include hacked exchanges, Bitcoin and Monero ransoms, and, of course, hidden mining.
Source: securelist.com
…Man Who Spent $100K to Remove a Lie from Google

In Europe, an Internet user can force Google to hide search results that are inaccurate or just too personal. But Americans don’t have the same legal protections — even in the most extreme cases.
Source: npr.org
…Ethereum Founder Vitalik Buterin Is Beefing With the Guy Who Claimed to Be Satoshi Nakamoto

At the 2018 Deconomy conference in Seoul, South Korea, Buterin and Wright were both booked as speakers, and the sparks flew. During question period for a panel that included Wright, Buterin (according to audience video from multiple angles posted to social media) stood up in the audience and asked, “Given he makes so many non-sequiturs and mistakes, why is this fraud allowed to speak at this conference?” The audience, video shows, went wild.
…The Feds Charged the Masterminds Behind a DJ Khaled-Endorsed ICO With Fraud

On Monday, the US Securities and Exchange Commission (SEC) filed a complaint against the masterminds of an initial coin offering (ICO) promoted by the boxer Floyd Mayweather and producer DJ Khaled, charging them with fraud. The founders were separately arrested and charged by law enforcement.
Source: vice.com
…Floyd Mayweather-backed cryptocurrency ICO was fraud, SEC says

The two founders of a cryptocurrency firm called Centra have been charged with with carrying out a fraudulent initial coin offering (ICO) by the Securities and Exchange Commission (SEC). Centra raised $32 million via an ICO which was promoted by boxer Floyd Mayweather.
Sohrab ‘Sam’ Sharma and Robert Farkas, co-founders of Centra were arrested.
Source: cnbc.com
…Intel FSP reverse engineering: finding the real entry point
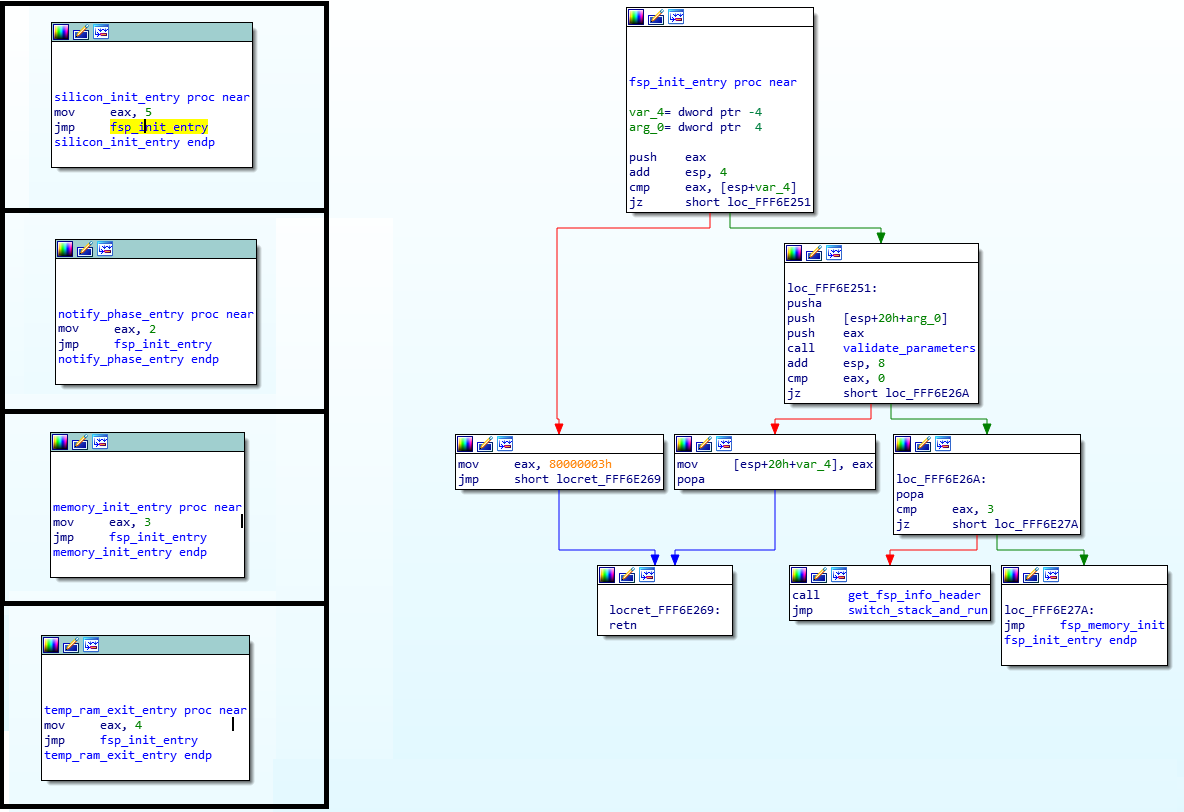
After attending 34C3 in Leipzig at the end of December, in which we (Zlatan and me) met with some of you, and had a lot of fun, I took some time off to travel Europe and fall victim to the horrible Influenza virus that so many people caught this year. After a couple more weeks of bed rest, I continued my saga in trying to find the real entry point of the Intel FSP-S module.
…Backdooring popular windows plugins
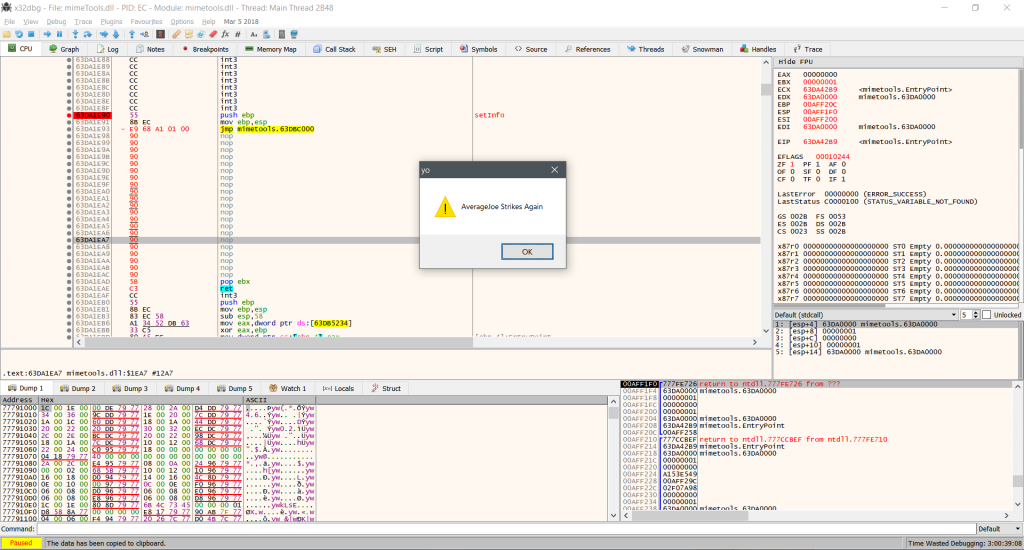
Today let’s scope in on backdooring some plugins for popular software. I will be covering a bunch of other programs, mainly stuff already on my computer.
Source: gironsec.com
…Panera Bread did nothing about its customer data vulnerability for eight months
First, the proof that I reported this, and the beginning of the timeline. I reported this vulnerability in August 2017, which is shown by the following email exchange with Panera Bread’s Information Security Director, Mike Gustavison. After attempting to contact them through a generic [email protected] email address (which bounced), Twitter and even LinkedIn and email messages to Mike Gustavison (whose information I found on LinkedIn), I was formally introduced by an industry contact who had a mutual connection.
…Panerabread.com leaks millions of customer records
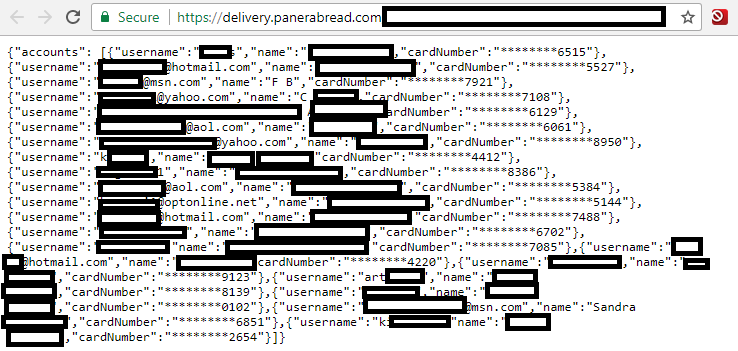
The data available in plain text from Panera’s site appeared to include records for any customer who has signed up for an account to order food online via panerabread.com. The St. Louis-based company, which has more than 2,100 retail locations in the United States and Canada, allows customers to order food online for pickup in stores or for delivery.
Source: krebsonsecurity.com
…Chrome Is Scanning Files on Your Computer, and People Are Freaking Out

In practice, Chome on Windows looks through your computer in search of malware that targets the Chrome browser itself using ESET’s antivirus engine. If it finds some suspected malware, it sends metadata of the file where the malware is stored, and some system information, to Google. Then, it asks you to for permission to remove the suspected malicious file.
…Google Bans All Cryptomining Extensions From the Chrome Store
In theory, cryptojacking can be used for legitimate purposes, like raising revenue for a publishing platform or collecting funds for charitable causes. But in practice, the technology has largely been implemented maliciously, or at least secretly, consuming processing resources on victim devices and potentially interfering with and damaging these targets. Bad actors can use locally installed malware to steal a victim device’s computing power, embed miners directly into websites to target casual web users without needing to install anything, or hide miners in the most innocuous applets and tools.
…Commonwealth Bank of Australia Tries to Explain Coding Errors Found After 4 Years

The coding errors were created in July 2011 when the bank introduced an automated decision tool to process customer overdraft applications, but the problems weren’t discovered until September 2015. During the calculations that decided whether a customer could actually afford an overdraft, one software error in the decision tool’s algorithm failed to count a customer’s rental expenses, while another error accessed a wrong data field that was used for determining a customer’s overall household expenditures. The result was that a customer’s true expenses where likely underestimated or under-assessed.
…Cloudflare Launches Publicly DNS-Over-HTTPS Service

On Sunday, the security focused content delivery network provider, Cloudflare, opened up a global Domain Name System (DNS) for consumers to run both DNS-over-TLS and DNS-over-HTTPS. The service is called 1.1.1.1. That is the IPv4 address for Cloudflare’s DNS resolver (along with 1.0.0.1).
Source: threatpost.com
…Fake AV Investigation Unearths KevDroid, New Android Malware

Several days ago, EST Security published a post concerning a fake antivirus malware targeting the Android mobile platform. In the Korean media, it was mentioned that there could be a link between this Android malware and Group 123. Talos decided to investigate this malware.
And due to our reporting and history of following of Group 123, we discovered some interesting elements.
Source: talosintelligence.com
…Credit Card Data Swiped From 5M Saks, Lord & Taylor Customers

Gemini Advisory said that it appears that all Lord & Taylor and 83 US-based Saks Fifth Avenue locations have been compromised, and the majority of stolen credit cards were obtained from New York and New Jersey locations. Gemini Advisory estimated the window of compromise to be May 2017 to present.
Source: threatpost.com
…China Slaps Tariffs on U.S. Products

The Chinese Ministry of Commerce indicated that the tariffs, which it first publicly suggested almost two weeks ago, were intended to pressure the Trump administration to back down from a simmering trade war. In addition to imposing additional tariffs on steel and aluminum from China and other countries, President Trump has threatened to put protective duties on other Chinese-made products worth $60 billion.
Source: nytimes.com
…The most honest Ponzi scheme of all time

We’ve built a Ponzi scheme for the Digital Age. Thanks to the smart contracts on the Ethereum blockchain our platform is transparent and immutable.
Source: ponzischeme.io
…