Cyber security news and services
A new massive cryptomining campaign target Linux servers exploiting old flaw

Trend Micro uncovered a new crypto mining campaign targeting Linux servers that exploit the CVE-2013-2618 flaw in Cacti’s Network Weathermap plug-in, which system administrators use to visualize network activity.
Source: securityaffairs.co
…Thousands of etcd installs leak 750MB worth of passwords and keys

According to the researcher Giovanni Collazo, querying the popularShodan search engine he found almost 2,300 servers exposed online that were runningetcd, which is a distributed key value store that provides a reliable way to store data across a cluster of machines.
Source: securityaffairs.co
…Facebook scraped call, text message data for years from Android phones
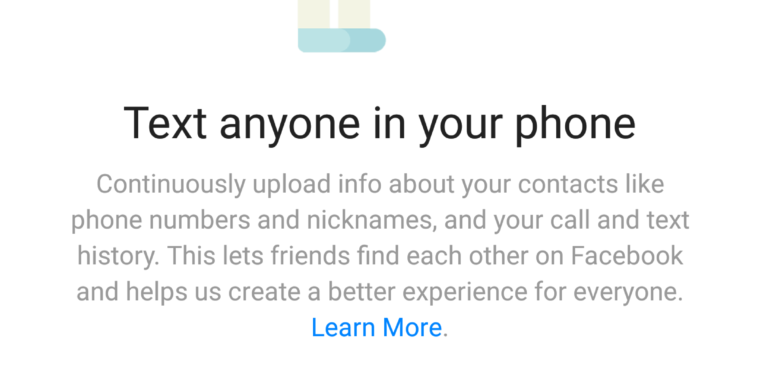
This past week, a New Zealand man was looking through the data Facebook had collected from him in an archive he had pulled down from the social networking site. While scanning the information Facebook had stored about his contacts, Dylan McKay discovered something distressing: Facebook also had about two years worth of phone call metadata from his Android phone, including names, phone numbers, and the length of each call made or received.
…GhostMiner: Cryptomining Malware Goes Fileless

This post describes a recent attack Minerva’s research team dissected, dubbed GhostMiner, after our solution prevented this infection at a customer site. It provides an example of how malicious miners are evolving to use advanced fileless techniques to succeed in mining Monero and spreading silently on a global scale. In this attack, we also witnessed how competing miners are fighting each other to generate more income for themselves, removing other miners on the endpoint.
…State Department Seemingly Buys $15,000 iPhone Cracking Tech GrayKey

As the FBI pushes once again for backdoors in consumer encryption products, the State Department is apparently taking advantage of a $50 per iPhone unlocking product from Grayshift, a company with an ex-Apple engineer on its staff.
Source: vice.com
…US Military Aims to Start Using Laser Weapon That Produces Voices by 2021

The US military is working on an experimental laser technology that could create the sound of voices out of thin air by altering atoms. The US military’s Joint Non-Lethal Weapons Program, or JNLWD, thinks it can achieve this goal in the next few years.
Source: interestingengineering.com
…Our suite of Ethereum security tools

Two years ago, when we began taking on blockchain security engagements, there were no tools engineered for the work. No static analyzers, fuzzers, or reverse engineering tools for Ethereum.
Source: trailofbits.com
…Hansen: Omaha man ‘liked’ a tweet, and then he lost his dream job

Roy Jones says he got no training on how to handle issues that might inflame the Chinese government. “My job isn’t to decide whether Tibet is a country. I’m a customer care rep in Omaha, Nebraska,” he said.
Source: omaha.com
…Facebook Logs Calls, Texts
In the wake of the Cambridge Analytica scandal, many Facebook users have been downloading their Facebook posts. And some of them are finding call and text-message logs from 2015 through 2017, although not the actual content of the calls or texts.
Source: tomsguide.com
…Life Cycle of a Web App 0 Day

Over the past few months, I’ve been monitoring the proliferation of exploits for some of my disclosed WordPress Plugin and Joomla Extension vulnerabilities against Akamai customers. I started this observation process which leads to an expected conclusion – severe vulnerabilities like SQL Injection, RFI and LFI would receive the most attention for any CMS platform. While less severe vulnerabilities such as XSS and path disclosure would likely receive less attention from the attackers.
…Deep dive on the most severe Kubernetes vulnerabilities to date – CVE-2017-1002101 and CVE-2017

Two vulnerabilities were reported and fixed in Kubernetes two weeks ago. The GitHub issues discussing the vulnerabilities and fixes were vague, so in this post I will review the bugs in additional detail and suggest remediation methods.
Source: twistlock.com
…Tracking ransomware end-to-end

You get two for the price of one with today’s paper! Firstly, it’s a fascinating insight into the ransomware business and how it operates, with data gathered over a period of two years. Secondly, since ransomware largely transacts using Bitcoin, the methods used by the research team to uncover and trace ransomware activity are also of interest in their own right.
Source: acolyer.org
…South Korea Planning to Formally Allow ICOs

Regional news sources report South Korea’s financial authorities are working on legislation to formally allow initial coin offerings (ICOs) in an effort to appear more welcoming to the larger financial technology community.
Source: bitcoin.com
…France to create legal framework for ICOs
France plans to create a legal framework for raising funds via cryptocurrencies and aims to become a leading center for offerings in bitcoin-style digital currencies, its finance minister wrote on a news website.
Source: reuters.com
…Behavioral Crypto-Economics: The challenge and promise of blockchain incentive design
In 2009, Satoshi Nakamoto designed Bitcoin to align the incentives of computers. In 2018, we are building multi-billion dollar blockchain projects, incentivizing humans using the same principles. We are assuming the efficient market hypothesis and the wisdom of the crowds.
But what happens when the crowds are not thatwise?
Source: medium.com
…Responsibility Deflected, the CLOUD Act Passes

Because of this failure, U.S. and foreign police will have new mechanisms to seize data across the globe. Because of this failure, your private emails, your online chats, your Facebook, Google, Flickr photos, your Snapchat videos, your private lives online, your moments shared digitally between only those you trust, will be open to foreign law enforcement without a warrant and with few restrictions on using and sharing your information. Because of this failure, U.S. laws will be bypassed on U.S. soil.
…Atlanta city government systems down due to ransomware attack

According to a report from Atlanta NBC affiliate WXIA, a city employee sent the station a screen shot of a ransomware message demanding a payment of $6,800 to unlock each computer or $51,000 to provide all the keys for affected systems. Employees received emails from the city’s information technology department instructing them to unplug their computers if they noticed anything suspicious. An internal email shared with WXIA said that the internal systems affected include the city’s payroll application.
…Pablo Escobar’s Brother Says He Met an FBI Agent Posing As Satoshi Nakamoto

In it, Roberto claims that he had a close encounter with a US government agent posing as the pseudonymous creator of Bitcoin, Satoshi Nakamoto. This encounter led Roberto to conclude that the US government created Bitcoin and will one day crash the market by selling all of Nakamoto’s stashed bitcoins.
Source: vice.com
…Survey: Americans Spent $1.4B on Credit Freeze Fees in Wake of Equifax Breach

Almost 20 percent of Americans froze their credit file with one or more of the big three credit bureaus in the wake of last year’s data breach at Equifax, costing consumers an estimated $1.4 billion, according to a new study. The findings come as lawmakers in Congress are debating legislation that would make credit freezes free in every state.
…Ransomware Takes Open-Source Path, Encrypts With GNU Privacy Guard

McAfee Labs has recently observed a new variant of ransomware that relies on the open-source program GNU Privacy Guard (GnuPG) to encrypt data. GnuPG is a hybrid-encryption software program that uses a combination of conventional symmetric-key cryptography for speed and public-key cryptography to ease the secure key exchange. Although ransomware using GnuPG to encrypt files is not unique, it is uncommon.
…