Cyber security news and services
Breaking the Ledger Crypto Wallet Security Model

In this post, I’m going to discuss a vulnerability I discovered in Ledger hardware wallets. The vulnerability arose due to Ledger’s use of a custom architecture to work around many of the limitations of their Secure Element.
Source: saleemrashid.com
…Dynamic analysis of iOS apps without Jailbreak
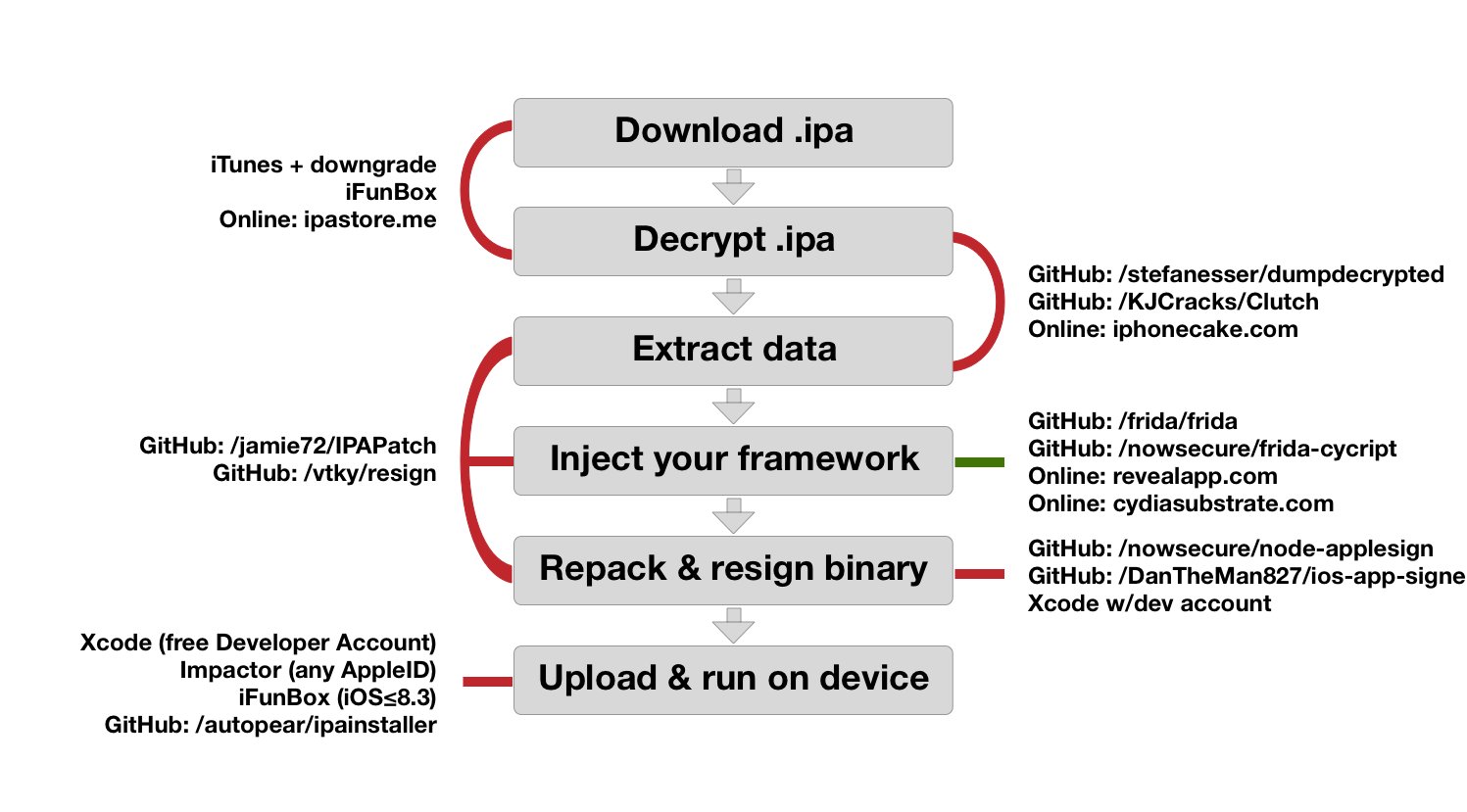
Dynamic analysis of iOS apps without JailbreakIn the article I will share my experience in solving some of the problems I faced when analyzing the security of iOS applications. All the tricks and approaches (if it is not listed separately) applicable on iOS device without Jailbreak.
Source: medium.com
…Scan for open S3 buckets and dump
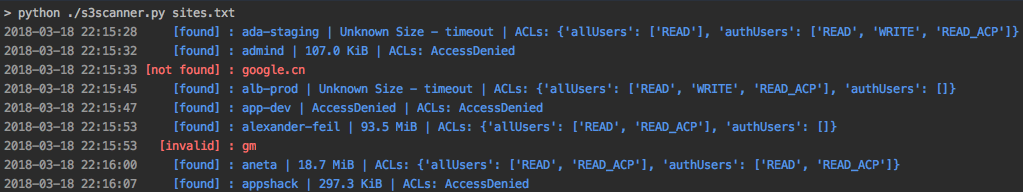
The tool takes in a list of bucket names to check. Found S3 buckets are output to file. The tool will also dump or list the contents of ‘open’ buckets locally.
Source: github.com
…Why It’s Important That Monero Rejects Compatibility With Bitmain’s New Antminer

Upon release, the company received instant criticism from the community at large for selling a ‘useless miner.’ The cryptographic algorithm it is designed for, CryptoNight, is mainly used by coins focused on privacy. Monero, the most widely used privacy coin based on CryptoNight, has already proclaimed it will tweak its technology to avoid being minable via the Antminer X3, hence the debate.
…A Flash of Insights on Lightning Network

I’m saying this to emphasize the point that for some of us, that has always been the vision. One of the first burning questions I had when I was first introduced to Bitcoin was how the whole thing was supposed to scale. Concepts I’ve learned of since then—like SPV and pruning—helped, but I wasn’t completely satisfied.
Ever since I heard about channels and thought about how they could be used in a network, that would become one of the first things I would reference whenever discussions of scalability came up.
…Facebook’s Mark Zuckerberg Lost $6 Billion the Day After Cambridge Analytica’s Data Misuse Was Revealed

The Facebook’s co-founder and CEO lost $6.06 billion in stock value, according to CNBC, when reports that Cambridge Analytica, a firm hired by Donald Trump’s campaign during the 2016 U.S. presidential election, improperly used the social network’s user data.
Source: fortune.com
…Taking down Gooligan the infamous Android botnet – a retrospective analysis

This series of posts recounts how, in November 2016, we hunted for and took down Gooligan, the infamous Android OAuth stealing botnet. What makes Gooligan special is its weaponization of OAuth tokens, something that was never observed in mainstream crimeware before. At its peak, Gooligan had hijacked over 1M OAuth tokens in an attempt to perform fraudulent Play store installs and reviews.
…For $15,000, GrayKey promises to crack iPhone passcodes for police

Security firm Malwarebytes also obtained information on the device and wrote-up a technical post on the technology. Once the box has determined the password, it displays the code on the iPhone screen. Four-digit passcodes can take minutes to a few hours, but six-digit passcodes — now the default on iPhones — can take three days or longer to crack.
But that’s still a significantly shorter amount of time than other known phone-cracking techniques.
…This Android malware redirects calls you make to your bank to go to scammers instead

Once installed the malware will intercept mobile calls you attempt to make to your bank, and instead direct them to a scammer impersonating an agent working for the bank.
Source: grahamcluley.com
…A picture got my PostgreSQL database to start mining Monero

We just saw an interesting attack technique applied to one of our PostgreSQL servers. After logging into the database, the attacker continued to create different payloads, implement evasion techniques through embedded binaries in a downloaded image, extract payloads to disk and trigger remote code execution of these payloads. Like so many attacks we’ve witnessed lately, it ended up with the attacker utilizing the server’s resources for cryptomining Monero.
…First U.S. cryptocurrency ban outlaws Venezuela’s ‘Petro’ coin

The U.S. executive branchissued an executive order prohibiting the use or purchase of Venezuela’s Petro cryptocurrency, claiming the currency was issued unlawfully in an effort to circumvent U.S. sanctions against Venezuela, and in particular the President Nicolás Maduro’s regime.
Source: digitaltrends.com
…When China hoards its hackers everyone loses

It’s a worrying development in the direction of isolationism and away from the benefits of competition in the spirit of improving security for all. It comes at a time when relations between the US and China strain under the weight of Huawei security concerns, which are not at all new, but are certainly coming to a head as American companies sever business ties with the firm.
…Report: Twitter to Ban Many Cryptocurrency Ads

Twitter will ban advertisements for several kinds of cryptocurrency products and projects. The policy, according to Sky News, would go into effect in two weeks and would block ads for initial coin offerings, token sales, and cryptocurrency wallets. It could also encompass a ban on ads for cryptocurrency exchanges.
Source: fortune.com
…Ether plunges after SEC says “dozens” of ICO investigations underway

The SEC’s decision to aggressively police cryptocurrency offerings is particularly significant for the Ethereum community because many new cryptocurrency offerings are built on top of the Ethereum platform. People creating a new token on the Ethereum blockchain need to buy ether, the currency used to pay for Ethereum transactions. So if aggressive SEC enforcement ends the Initial Coin Offering (ICO) boom—which seems to be cooling anyway—it would remove a major factor that pushed ether’s value upward during 2017.
…Meltdown, Spectre, and the Costs of Unchecked Innovation

Both attacks rely on using high-speed timing measurements to detect sensitive information, so somewhat counterintuitively, the patches had to decrease the speed of seemingly mundane computations. The first change was to slow down the performance API for web browsers, which had previously been able to analyze the behavior of a page at speeds fast enough to be used in an attack; the second change removed SharedArrayBuffer, a new kind of data structure atop which similar timers could be trivially rebuilt. Similar changes were also soon also implemented by Microsoft for Internet Explorer and Edge browsers and also by WebKit, a tool for viewing the web that is used to build Safari, Mobile Safari, Android Browser, and the dedicated browsers embedded on many other devices.
…Schools Are Spending Millions on High-Tech Surveillance of Kids

Advanced surveillance technologies once reserved for international airports and high-security prisons are coming to schools across America. From New York to Arkansas, schools are spending millions to outfit their campuses with some of the most advanced surveillance technology available: face recognition to deter predators, object recognition to detect weapons, and license plate tracking to deter criminals. Privacy experts are still debating the usefulness of these tools, whom they should be used on, and whom they should not, but school officials are embracing them as a way to save lives in times of crisis.
…To find suspects, police quietly turn to Google

Raleigh police used search warrants to demand Google accounts not of specific suspects, but from any mobile devices that veered too close to the scene of a crime, according to a WRAL News review of court records. These warrants often prevent the technology giant for months from disclosing information about the searches not just to potential suspects, but to any users swept up in the search.
…50M Facebook profiles harvested for Cambridge Analytica in major data breach

A whistleblower has revealed to the Observer how Cambridge Analytica – a company owned by the hedge fund billionaire Robert Mercer, and headed at the time by Trump’s key adviser Steve Bannon – used personal information taken without authorisation in early 2014 to build a system that could profile individual US voters, in order to target them with personalised political advertisements.
…Top Five Ways I gained access to Your Corporate Wireless Network
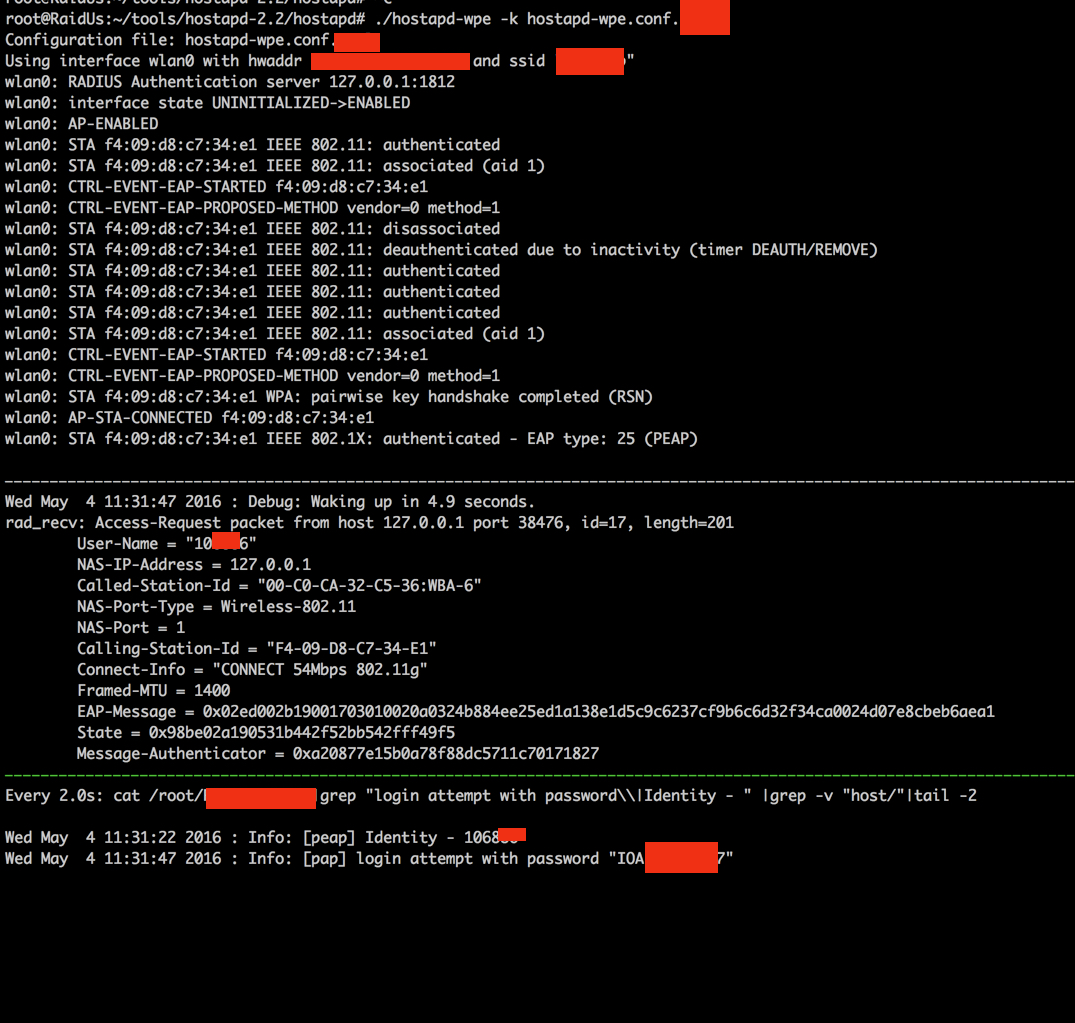
Common configuration mistakes, vulnerabilities, and chaining common network attacks while performing a wireless assessment can lead to corporate network access before lunch. Like my last Top 5 series, many of the same attack vectors used years ago still work in 2018.
Source: medium.com
…Chinese Hackers Hit U.S. Firms Linked to South China Sea Dispute

The suspected Chinese cyber-espionage group dubbed TEMP.Periscope appeared to be seeking information that would benefit the Chinese government, said FireEye, a U.S.-based provider network protection systems. The hackers have focused on U.S. maritime entities that were either linked to — or have clients operating in — the South China Sea, said Fred Plan, senior analyst at FireEye in Los Angeles.
…