Cyber security news and services
FCC Accuses Stealthy Startup of Launching Rogue Satellites

On 12 January, a Polar Satellite Launch Vehicle (PSLV) rocket blasted off from India’s eastern coast. While its primary cargo was a large Indian mapping satellite, dozens of secondary CubeSats from other countries travelled along with it. Seattle-based Planetary Resources supplied a spacecraft that will test prospecting tools for future asteroid miners, Canadian company Telesat launched a broadband communications satellite, and a British Earth-observation mission called Carbonite will capture high-definition video of the planet’s surface.
…APT Hackers Infect Routers to Covertly Implant Slingshot Spying Malware
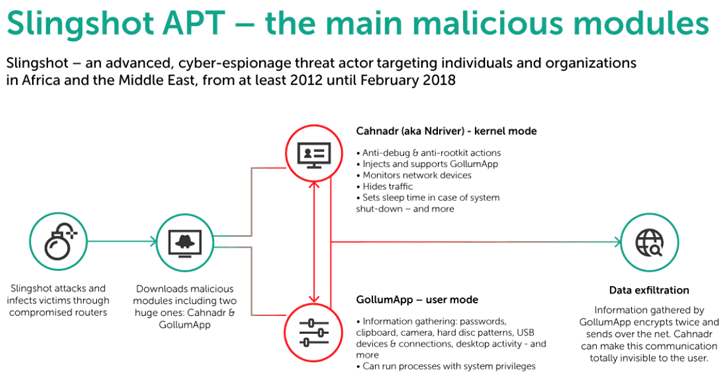
Researchers Uncovers a Previously Undetected Highly-Skilled APT Hacking Group Operating Covertly Since 2012, Infecting Mikrotik Routers to Implant Advance ‘Slingshot’ Spying Malware
Source: thehackernews.com
…Getting any Facebook user’s friend list and partial payment card details
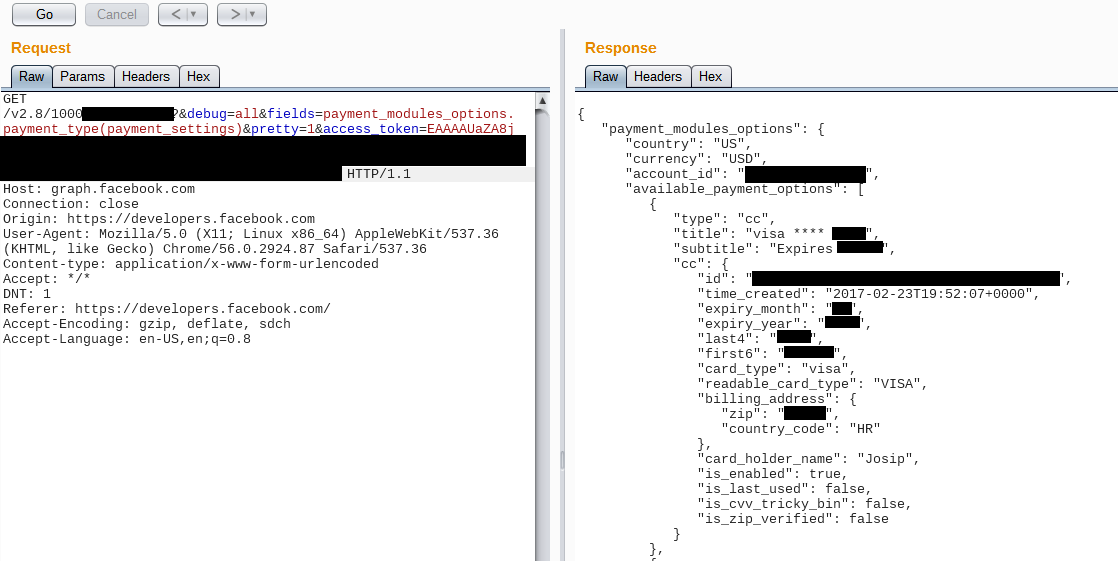
Facebook has a GraphQL endpoint which can only be used by some of their own first-party applications. Generally, you need a user (or page) access_token to query the GraphQL endpoint.
I have decided to try using Facebook for Android application’s client token, but the endpoint returned an error message:
Source: josipfranjkovic.com
…ISPs Caught Injecting Cryptocurrency Miners and Spyware In Some Countries
Governments and Internet Service Providers in Turkey, Syria and Egypt Caught Infecting Citizens with Cryptocurrency Mining and surveillance malware.
Source: thehackernews.com
…Echidna, a smart fuzzer for Ethereum

Today we released Echidna, our next-generation EVM smart fuzzer at EthCC. It’s the first-ever fuzzer to target smart contracts, and has powerful features like abstract state-machine modeling and automatic minimal test case generation. We’ve been working on it for quite some time, and are thrilled to finally share it with the world.
Source: trailofbits.com
…New traces of Hacking Team in the wild

The capabilities of its flagship product, the Remote Control System (RCS), include extracting files from a targeted device, intercepting emails and instant messaging, as well as remotely activating a device’s webcam and microphone. The company has been criticized for selling these capabilities to authoritarian governments – an allegation it has consistently denied.
Source: welivesecurity.com
…Russian hackers stole 860,000 euros from 32 ATMs belonging to the Raiffeisen Romania in just one night

Cybercriminals stole 3.8 million slopes (860,000 euros) from 32 ATMs belonging to the Raiffeisen Romania bank using an infected RTF document. The criminal organization led by Dmitriy Kvasov operated in Romania, the gang stole the money in just one night in 2016.
Source: securityaffairs.co
…This Is What Happens When Bitcoin Miners Take Over Your Town

Hands on the wheel, eyes squinting against the winter sun, Lauren Miehe eases his Land Rover down the main drag and tells me how he used to spot promising sites to build a bitcoin mine, back in 2013, when he was a freshly arrived techie from Seattle and had just discovered this sleepy rural community.
Source: politico.com
…Documents Prove Local Cops Have Bought Cheap iPhone Cracking Tech

GrayShift is a new lawful access company, with an ex-Apple engineer on its staff, that promises to break into the latest iPhones. At least one local police department has already signed up to its GrayKey service.
Source: vice.com
…Amazon Partnership with British Police Alarms Privacy Advocates

A partnership with police will permit some Amazon Echo owners to report crimes directly through their smart speakers.
Source: theintercept.com
…New Cryptocurrency Mining Malware Infected Over 500,000 PCs in Just Few Hours

Two days ago, Microsoft encountered a rapidly spreading cryptocurrency-mining malware that infected almost 500,000 computers within just 12 hours and successfully blocked it to a large extent. Dubbed Dofoil, aka Smoke Loader, the malware was found dropping a cryptocurrency miner program as payload on infected Windows computers that mines Electroneum coins, yet another cryptocurrency, for attackers using victims’ CPUs.
…Look-Alike Domains and Visual Confusion
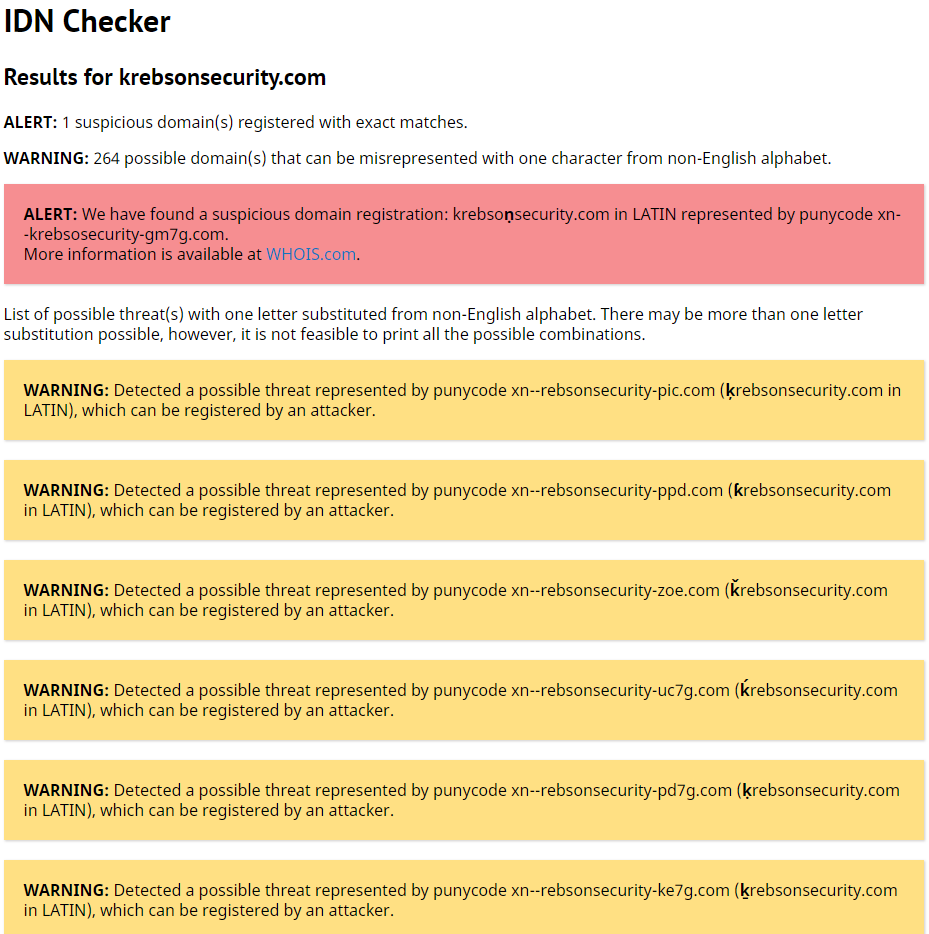
Go ahead and click on the link above or cut-and-paste it into a browser address bar. If you’re using Google Chrome, Apple’s Safari, or some recent version of Microsoft‘s Internet Explorer or Edge browsers, you should notice that the address converts to “xn–80a7a.com.” This is called “punycode,” and it allows browsers to render domains with non-Latin alphabets like Cyrillic and Ukrainian.
Source: krebsonsecurity.com
…That Sketchy Steven Seagal-Endorsed ICO Is Under Siege By State Regulators

Bitcoiin—an Etheruem-based token that is not associated with Bitcoin—markets itself as the “next generation of Bitcoin” and is selling tokens to investors after recently completing an Initial Coin Offering (ICO) that the startup claims raised $75 million USD. “In actuality,” a cease-and-desist order filed on Wednesday by the State of new Jersey Bureau of Securities reads, “Bitcoiin is fraudulently offering unregistered securities in violation of the Securities Law.” Whoops!
…How Dutch Police Took Over Hansa, a Top Dark Web Market
For anyone who has watched the last few years of cat-and-mouse games on the dark web’s black markets, the pattern is familiar: A contraband bazaar like the Silk Road attracts thousands of drug dealers and their customers, along with intense scrutiny from police and three-letter agencies. Authorities hunt down its administrators, and tear the site offline in a dramatic takedown—only to find that its buyers and sellers have simply migrated to the next dark-web market on their list.
…Spyware maker shuts down surveillance services after hacks

Retina-X has had it with the hacking. On Monday, it threw in the towel on all of the aforementioned tools. The company put an announcement at the top of its site saying that while no personal data was accessed during the year of attacks, some “photographic material” of TeenShield and PhoneSheriff customers had been exposed.
Source: sophos.com
…Corero Network discovered a Kill Switch for Memcached DDoS attacks

Memcached DDoS attacks made the headlines due to the magnitude observed in recent offensives. While two PoC exploits for Memcached DDoS attacks have been released online, experts at security firm Corero Network announced they have discovered a ‘kill switch’ to address the Memcached vulnerability.
Source: securityaffairs.co
…Unprompted, creepy laughter from Alexa is freaking out Echo users

Don’t be alarmed! Your Alexa-enabled device may lapse into a sudden fit of giggles, but Amazon is aware of the problem. Recent reports detail a quirky bug that has Amazon’s virtual assistant Alexa laughing for no apparent reason, scaring the daylights out of unsuspecting users.
Source: arstechnica.com
…FBI again calls for magical solution to break into encrypted phones

The FBI maintains an office, known as the National Domestic Communications Assistance Center (NDCAC), which actively provides technical assistance to local law enforcement in high-profile cases. In its most recently published minutes from May 2017, the NDCAC said that one of its goals is to make commercial tools like those from Israeli data extraction company Cellebrite ‘more widely available’ to state and local law enforcement.
…Bitcoin falls 10 percent after SEC warns about unregulated exchanges

So in recent months, the SEC has stepped up its enforcement activities, shutting down the most obviously fraudulent ICOs and warning the public that stricter regulations were likely to follow later. Now the feds appear to be getting ready to rein in cryptocurrency exchanges, an important part of the ICO ecosystem that has, until now, operated largely outside of the law.
…Statement on Potentially Unlawful Online Platforms for Trading Digital Assets (ICO)

Online trading platforms have become a popular way investors can buy and sell digital assets, including coins and tokens offered and sold in so-called Initial Coin Offerings (‘ICOs’). The platforms often claim to give investors the ability to quickly buy and sell digital assets.
Many of these platforms bring buyers and sellers together in one place and offer investors access to automated systems that display priced orders, execute trades, and provide transaction data.
…