Mar. 16, 2018

In August, a petrochemical company with a plant in Saudi Arabia was hit by a new kind of cyberassault. The attack was not designed to simply destroy data or shut down the plant, investigators believe. It was meant to sabotage the firm’s operations and trigger an explosion.
Source: nytimes.com
Mar. 15, 2018

Late last summer, I ‘Googled’ my regular diner to confirm its closing time, and was shocked to find that the site had marked it Permanently Closed. I quickly called the restaurant and learned, thankfully, that it hadn’t shut down; however, its Google presence had been hijacked. And
despite the owners’ best efforts
Source: forbes.com
Mar. 12, 2018

The researchers at Kaspersky Lab ICS CERT decided to check the popular smart camera to see how well protected it is against cyber abuses. This model has a rich feature list, compares favorably to regular webcams and can be used as a baby monitor, a component in a home security system or as part of a monitoring system.
Source: securelist.com
Mar. 12, 2018

DJI drones have been on the radar of the hacker community for quite a long time. The interest of its members revolves mostly around unblocking some features of drones, setting control channels of drones to a higher frequency, and removing such restrictions as flight altitude limits or strictly set no-fly zones. Moreover, there are piles of publicly available info about jailbreaking drones.
The most useful know-hows produced by the community are gathered in several Github cross-referenced repositories. Those striving for knowledge may also check the community wiki dji.retroroms.info. For quite a while the website has been accessible as a web archive only, but now the wiki is available again.
Mar. 10, 2018

The capabilities of its flagship product, the Remote Control System (RCS), include extracting files from a targeted device, intercepting emails and instant messaging, as well as remotely activating a device’s webcam and microphone. The company has been criticized for selling these capabilities to authoritarian governments – an allegation it has consistently denied.
Source: welivesecurity.com
Mar. 9, 2018

GrayShift is a new lawful access company, with an ex-Apple engineer on its staff, that promises to break into the latest iPhones. At least one local police department has already signed up to its GrayKey service.
Source: vice.com
Mar. 7, 2018

The government malware market is beyond saturated at this point, with myriad companies looking to sell mobile phone and computer monitoring software to authorities around the world, but still more firms are jumping into the industry.
Source: vice.com
Mar. 7, 2018

The number of Flash Player exploits has recently declined, due to Adobe’s introduction of various measures to strengthen Flash’s security. Occasionally, however, an exploit still arises. On January 31, Kr-Cert reported a zero-day vulnerability, identified as CVE-2018-4878, being exploited in the field.
(Adobe has released an update to fix this flaw.) We analyzed this vulnerability and found that it bypassed the byte array mitigation feature that was introduced to prevent “length corruption” attacks in Flash. This post will focus on how the exploit bypasses the length checks.
Mar. 7, 2018

The Devcore researchers said as many as 400,000 servers are at risk. Queries on the Shodan computer search engine identified a large number of servers that reported running vulnerable versions. The developers published a fix with version 4.90.1, which was released on February 10.
Any organization that uses Exim should ensure it’s using the latest version.
Source: arstechnica.com
Mar. 7, 2018

The company, called Grayshift, has released marketing materials to police and forensics organizations promising to unlock iPhones with its GrayKey tool, according to Forbes, which obtained a copy of those materials. GrayKey will cost law enforcement $15,000 for 300 uses. Those that want to be able to unlock iPhones an unlimited number of times will need to pay $30,000.
Mar. 7, 2018

Continuing on in our Encryption 101 series, where we gave a malware analyst’s primer on encryption and demonstrated encryption techniques using ShiOne ransomware, we now look at what it takes to break an encryption. In order for something as powerful as encryption to break, there needs to be some kind of secret flaw. That flaw is often a result of an error in implementation.
Mar. 5, 2018
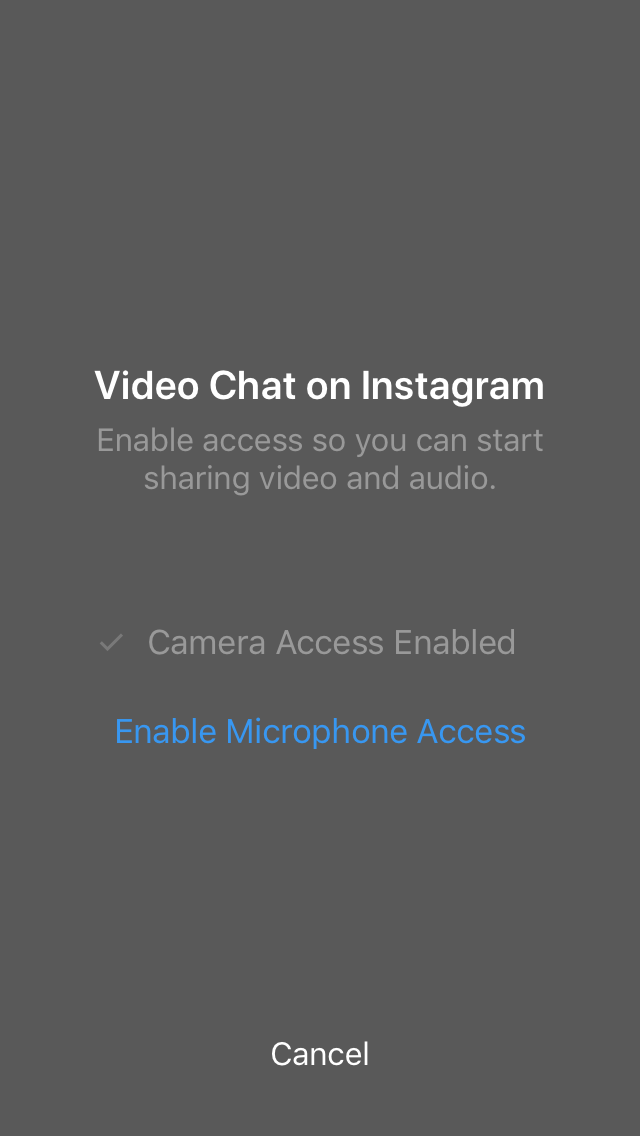
Yesterday I managed to grab some screenshots of a video calling UI on Instagram. This is the story of how that happened. I think the description of the process will be pretty useful to anyone who’s interested in reverse engineering to find hidden features.
Source: medium.com
Mar. 1, 2018

Unauthorized mobile phone number porting is not a new problem, but T-Mobile said it began alerting customers about it earlier this month because the company has seen a recent uptick in fraudulent requests to have customer phone numbers ported over to another mobile provider’s network.
Source: krebsonsecurity.com
Mar. 1, 2018

In this project you will find a full implementation of the “bpf” kernel exploit for the PlayStation 4 on 4.55. It will allow you to run arbitrary code as kernel, to allow jailbreaking and kernel-level modifications to the system. This release however, does not contain any code related to defeating anti-piracy mechanisms or running homebrew.
This exploit does include a loader that listens for payloads on port 9020 and will execute them upon receival.
Mar. 1, 2018

Honeytrap is an extensible and opensource system for running, monitoring and managing honeypots.
Source: github.com












