Apr. 19, 2018

The malware was designed to copy the credentials in a way that wouldn’t be detected by antivirus programs. The copying process, for instance, remained active for less than one minute. The malware didn’t steal general credentials, and it copied cookies and saved passwords by querying copies of the original cookies and LoginData files rather than through other means.
Source: arstechnica.com
Apr. 18, 2018

The GandCrab ransomware is reaching far and wide via malspam, social engineering schemes, and exploit kit campaigns. On April 16, we discovered that Magnitude EK, whichhad been loyal to its own Magniber ransomware, was now being leveraged to push out GandCrab, too.
Source: malwarebytes.com
Apr. 18, 2018

Global chip-maker Intel on Tuesday announced two new technologies—Threat Detection Technology (TDT) and Security Essentials—that not only offer hardware-based built-in security features across Intel processors but also improve threat detection without compromising system performance. Intel’s Threat Detection Technology (TDT) offers a new set of features that leverage hardware-level telemetry to help security products detect new classes of threats and exploits. It includes two main capabilities—Accelerated Memory Scanning and Advanced Platform Telemetry.
Apr. 14, 2018
In July 2017 we released PyREBox, a Python Scriptable Reverse Engineering Sandbox as an open source tool. This project is part of our continuous effort to create new tools to improve our workflows. PyREBox is a versatile instrumentation framework based on QEMU.
It allows us to run a whole operating system in a virtual environment (emulator), and to inspect and modify its memory and registers at run-time. A small set of QEMU modifications allows users to instrument certain events such as instruction execution or memory read/writes.
Apr. 13, 2018

In this paper we provide an implementation, evaluation, and analysis of PowerHammer, a malware (bridgeware [1]) that uses power lines to exfiltrate data from air-gapped computers. In this case, a malicious code running on a compromised computer can control the power consumption of the system by intentionally regulating the CPU utilization. Data is modulated, encoded, and transmitted on top of the current flow fluctuations, and then it is conducted and propagated through the power lines.
Apr. 13, 2018

Researchers have identified what they are calling an Early Bird code injection technique used by the Iranian group APT33 to burrow the TurnedUp malware inside infected systems while evading anti-malware tools.
Source: threatpost.com
Apr. 12, 2018

The campaign, which has been running for at least four months, is able to compromise websites running a variety of content management systems, including WordPress, Joomla, and SquareSpace. That’s according to a blog post by Jérôme Segura, lead malware intelligence analyst at Malwarebytes. The hackers, he wrote, cause the sites to display authentic-appearing messages to a narrowly targeted number of visitors that, depending on the browsers they’re using, instruct them to install updates for Firefox, Chrome, or Flash.
Apr. 6, 2018

The nature of the malware involved has not been disclosed and it remains unclear whether the payment card information, which Delta say was entered by the customers themselves, got intercepted in transit or was improperly stored.
Source: gizmodo.com
Apr. 3, 2018

Several days ago, EST Security published a post concerning a fake antivirus malware targeting the Android mobile platform. In the Korean media, it was mentioned that there could be a link between this Android malware and Group 123. Talos decided to investigate this malware.
And due to our reporting and history of following of Group 123, we discovered some interesting elements.
Source: talosintelligence.com
Mar. 31, 2018

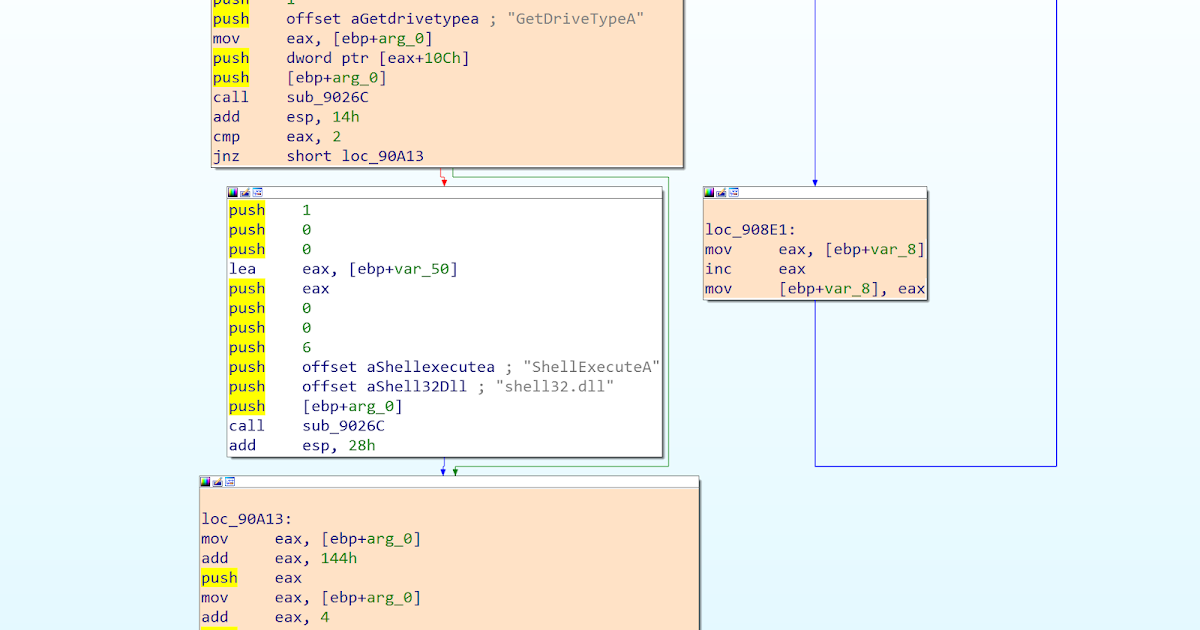
The malware stores encrypted buffers, “hidden” directly within the text section. The address of each encrypted buffer is retrieved thanks to a trick commonly used by malware. Since a call instruction pushes on the stack the address of the instruction to execute when returning from the callee, a call instruction (0xE8) with an operand of 0x00000000 leads to a jump at the address following the call.
Mar. 29, 2018

QuantLoader is a Trojan downloader that has been used in campaigns serving a range of malware, including ransomware, Banking Trojans, and RATs. In this post, we’ll take a high-level look at the campaign flow, as well as a deep dive into how the malware executes.
Source: malwarebytes.com
Mar. 29, 2018

While doing threat research, teams need a lot of tools and systems to aid their hunting efforts – from systems storing Passive DNS data and automated malware classification to systems allowing researchers to pattern-match a large volume of data in a relatively short period of time. These tools are extremely useful when working on APT campaigns where research is very agile and spans multiple months. One of the most frequently used tools for hunting new variants of malware is called YARA and was developed by Victor Manuel Alvarez while working for VirusTotal, now part of Alphabet.
Mar. 28, 2018

For those looking to learn about and share malware samples, a site called VirusBay may be what you are looking for. VirusBay’s goal is to make malware analysis more social by providing a place for researchers to upload samples, request samples, and discuss them with other researchers.
Source: bleepingcomputer.com
Mar. 26, 2018

According to Europol, the cybercriminals have been active since 2013, striking banks in over 40 countries in order to steal at least €1 billion, estimated at roughly €10 million per successful heist.
Source: zdnet.com
Mar. 19, 2018

Once installed the malware will intercept mobile calls you attempt to make to your bank, and instead direct them to a scammer impersonating an agent working for the bank.
Source: grahamcluley.com
Mar. 16, 2018

Security researchers have discovered a massive continuously growing malware campaign that has already infected nearly 5 million mobile devices worldwide. Dubbed RottenSys, the malware that disguised as a ‘System Wi-Fi service’ app came pre-installed on millions of brand new smartphones manufactured by Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung and GIONEE—added somewhere along the supply chain. All these affected devices were shipped through Tian Pai, a Hangzhou-based mobile phone distributor, but researchers are not sure if the company has direct involvement in this campaign.
Mar. 16, 2018

Researchers say a massive phishing campaign targeting Asia and Middle East regions is linked to an Iranian-based threat actorTEMP.Zagros, also known as MuddyWater. This latest attack illustrates an evolution by the threat actor, which has now adopted new tactics, techniques and procedures.
Source: threatpost.com
Mar. 16, 2018

Martisevs’ service was designed to keep new malware out of the hands of anti-virus makers. It didn’t report the detection of malicious files, thereby keeping anti-virus makers in the dark about new threats. The service had quite the palate: malware submitted to it included, among other types, crypters meant to hide malware from anti-virus programs, remote-access Trojans (RATs), keyloggers, and malware tool kits to create customized malicious files.
Mar. 16, 2018

A recent malware campaign that attempted to install a resource-draining currency miner on more than 400,000 computers in 12 hours was caused by a malicious backdoor that was sneaked into a BitTorrent application called Mediaget, a Microsoft researcher said Tuesday.
Source: arstechnica.com
Mar. 16, 2018

A recent malware campaign that attempted to install a resource-draining currency miner on more than 400,000 computers in 12 hours was caused by a malicious backdoor that was sneaked into a BitTorrent application called Mediaget, a Microsoft researcher said Tuesday.
Source: arstechnica.com


















