Mar. 6, 2019

Ghidra is a software reverse engineering (SRE) framework developed by NSA’s Research Directorate for NSA’s cybersecurity mission. It helps analyze malicious code and malware like viruses, and can give cybersecurity professionals a better understanding of potential vulnerabilities in their networks and systems.
Source: nsa.gov
May. 12, 2018

The researchers found evidence that the threat has been around since at least late 2014.TreasureHunt was firstdiscoveredby researchers at theSANS Institute who noticed the malware generating mutex names to evade detection. TreasureHunt enumerates the processes running on the infected systemsand implement memory scraping functions to extractcredit and debit card information. Stolen payment card data are sent to C&C servers throughHTTP POST requests.
May. 9, 2018

In late April 2018, a new zero-day vulnerability for Internet Explorer (IE) was found using our sandbox; more than two years since the last in the wild example (CVE-2016-0189). This particular vulnerability and subsequent exploit are interesting for many reasons. The following article will examine the core reasons behind the latest vulnerability, CVE-2018-8174.
Source: securelist.com
May. 1, 2018

This post outlines and presents the rediscovery, vulnerability analysis and exploitation of a zero-day vulnerability that was originally discovered and exploited by the CIA’s ‘Engineering Development Group’; remotely targeting MikroTik’s RouterOS embedded operating system that was discovered during the ‘Vault 7’ leak via WikiLeaks in March of 2017.
Source: seekintoo.com
Apr. 29, 2018

The Zebrocy family consists of three components. In the order of deployment these are a Delphi downloader, an AutoIt downloader and a Delphi backdoor. Figure 1 shows the relationship between these components.
In this article we describe this family and how it can coexist with the older Seduploader reconnaissance tools. We will talk about some similarities to and differences from Downdelph at the end.
Apr. 27, 2018

Wow did I underestimate this one! I told myself it would take quite some time to build a reliable exploit once I found a bug in Adobe Reader. There are so many mitigations to work through once you have an exploitable crash.
Amongst others: Data Execution Protection (DEP: prevents your code from being executed), Address Space Layout Randomization (ASLR: where in memory is my code anyway?), Sandboxing (you need to escape this one, it limits what your code can do). Itâs hard to end up with reliable code execution.
Apr. 24, 2018
The researchers at CSE ZLab have spotted a new family of malware, tracked as Bandios spreading in the wild. The peculiarity of Bandios malware is the fact that this malware is in a rapid and constant evolution and development.
Source: securityaffairs.co
Apr. 19, 2018

An arbitrary file write vulnerability is where a user can create or modify a file in a location they could not normally access. This might be due to a privileged service incorrectly sanitizing information passed by the user or due to a symbolic link planting attack where the user can write a link into a location which is subsequently used by the privileged service. The ideal vulnerability is one where the attacking user not only controls the location of the file being written but also the entire contents.
Apr. 19, 2018
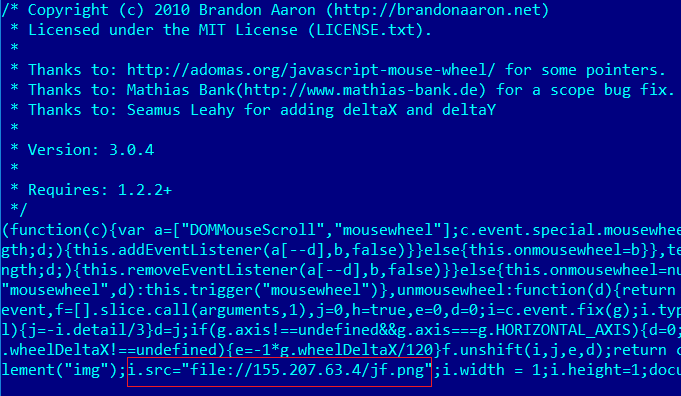
Hackers initially got onto Piriform’s London networks by using stolen credentials to log into a TeamViewer remote desktop account on a developer PC. From there, the attackers moved laterally to a second computer, always working outside office hours when it was unlikely that people would be using the machines. The attackers installed malware called ShadowPad, sort of customizable malware platform that can be used for an assortment of attacks from DDoS to keylogging, on the compromised computers.
Apr. 15, 2018

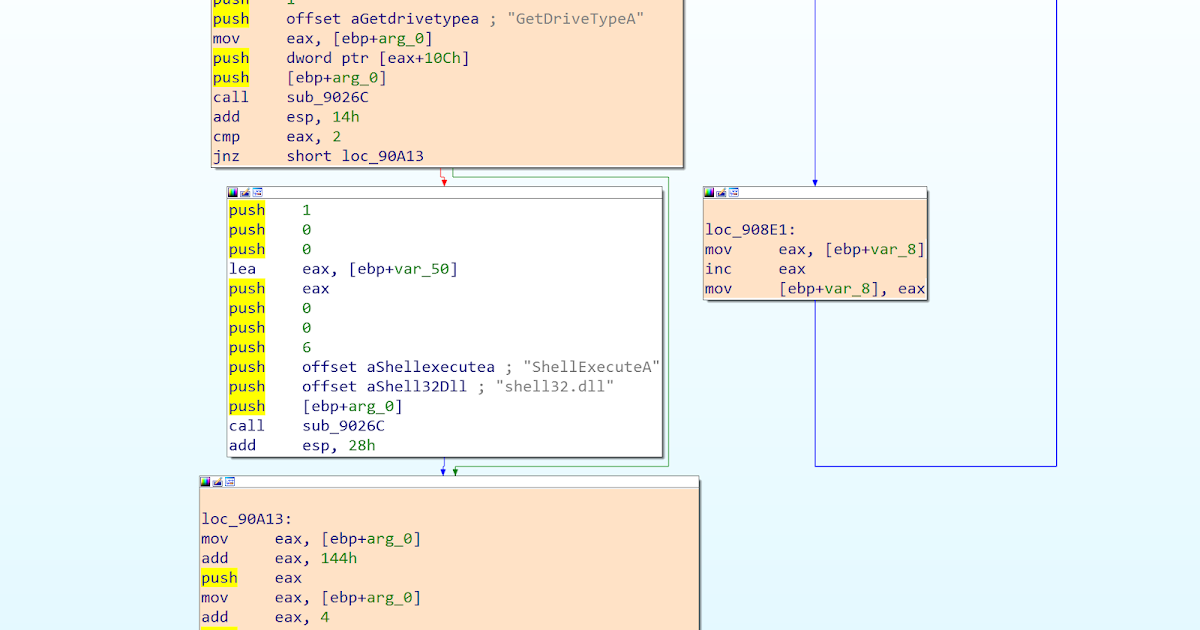
CVE-2017-0263 is a UAF vulnerability in Menu Management Component in win32k kernel module of Windows operating system, which was reported to be used to attack with an EPS vulnerability to interfere the French election. This article will simply analyze the CVE-2017-0263 part of the attacking sample in order to come up with the operation principle and basic exploiting idea of this vulnerability, and make a brief investigation into the Menu Management Component of Windows Window Manager Subsystem. The analyzing environment is Windows 7 x86 SP1 basic virtual machine.
Apr. 14, 2018
In July 2017 we released PyREBox, a Python Scriptable Reverse Engineering Sandbox as an open source tool. This project is part of our continuous effort to create new tools to improve our workflows. PyREBox is a versatile instrumentation framework based on QEMU.
It allows us to run a whole operating system in a virtual environment (emulator), and to inspect and modify its memory and registers at run-time. A small set of QEMU modifications allows users to instrument certain events such as instruction execution or memory read/writes.
Apr. 4, 2018
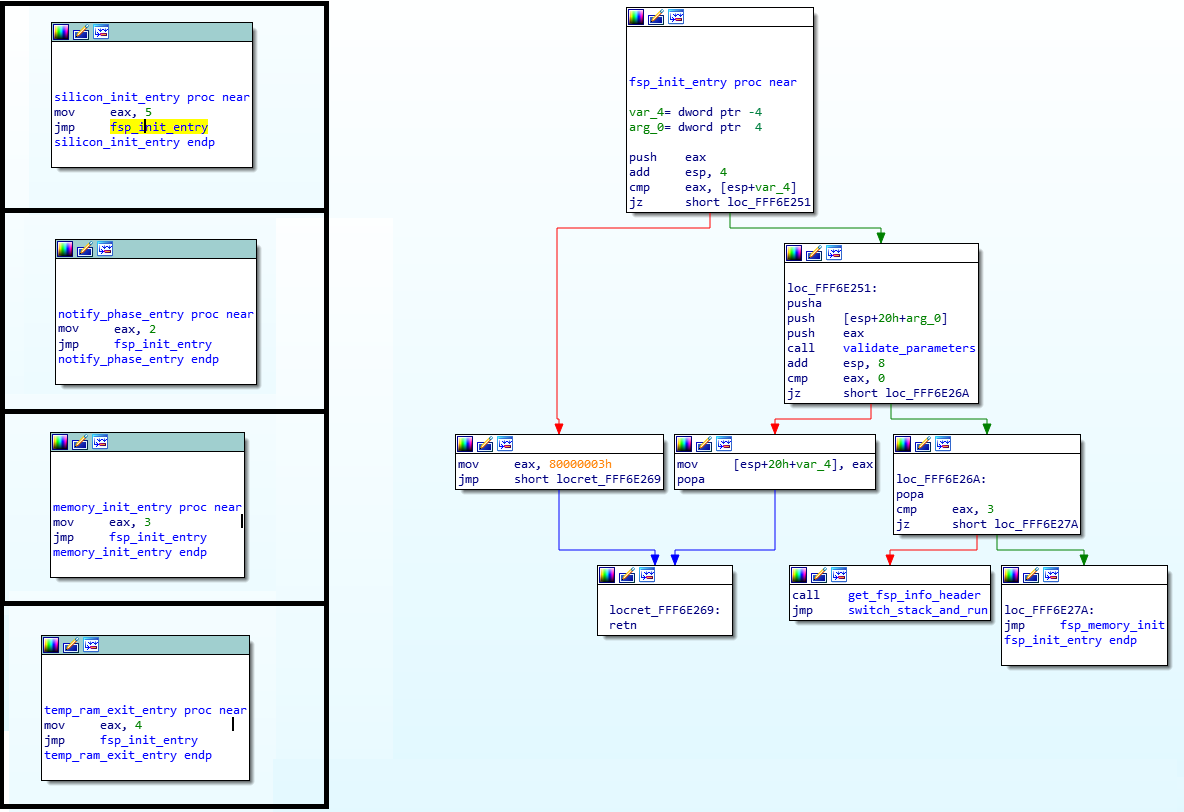
After attending 34C3 in Leipzig at the end of December, in which we (Zlatan and me) met with some of you, and had a lot of fun, I took some time off to travel Europe and fall victim to the horrible Influenza virus that so many people caught this year. After a couple more weeks of bed rest, I continued my saga in trying to find the real entry point of the Intel FSP-S module.
Apr. 4, 2018
Today let’s scope in on backdooring some plugins for popular software. I will be covering a bunch of other programs, mainly stuff already on my computer.
Source: gironsec.com
Mar. 31, 2018

The malware stores encrypted buffers, “hidden” directly within the text section. The address of each encrypted buffer is retrieved thanks to a trick commonly used by malware. Since a call instruction pushes on the stack the address of the instruction to execute when returning from the callee, a call instruction (0xE8) with an operand of 0x00000000 leads to a jump at the address following the call.
Mar. 29, 2018

QuantLoader is a Trojan downloader that has been used in campaigns serving a range of malware, including ransomware, Banking Trojans, and RATs. In this post, we’ll take a high-level look at the campaign flow, as well as a deep dive into how the malware executes.
Source: malwarebytes.com
Mar. 20, 2018
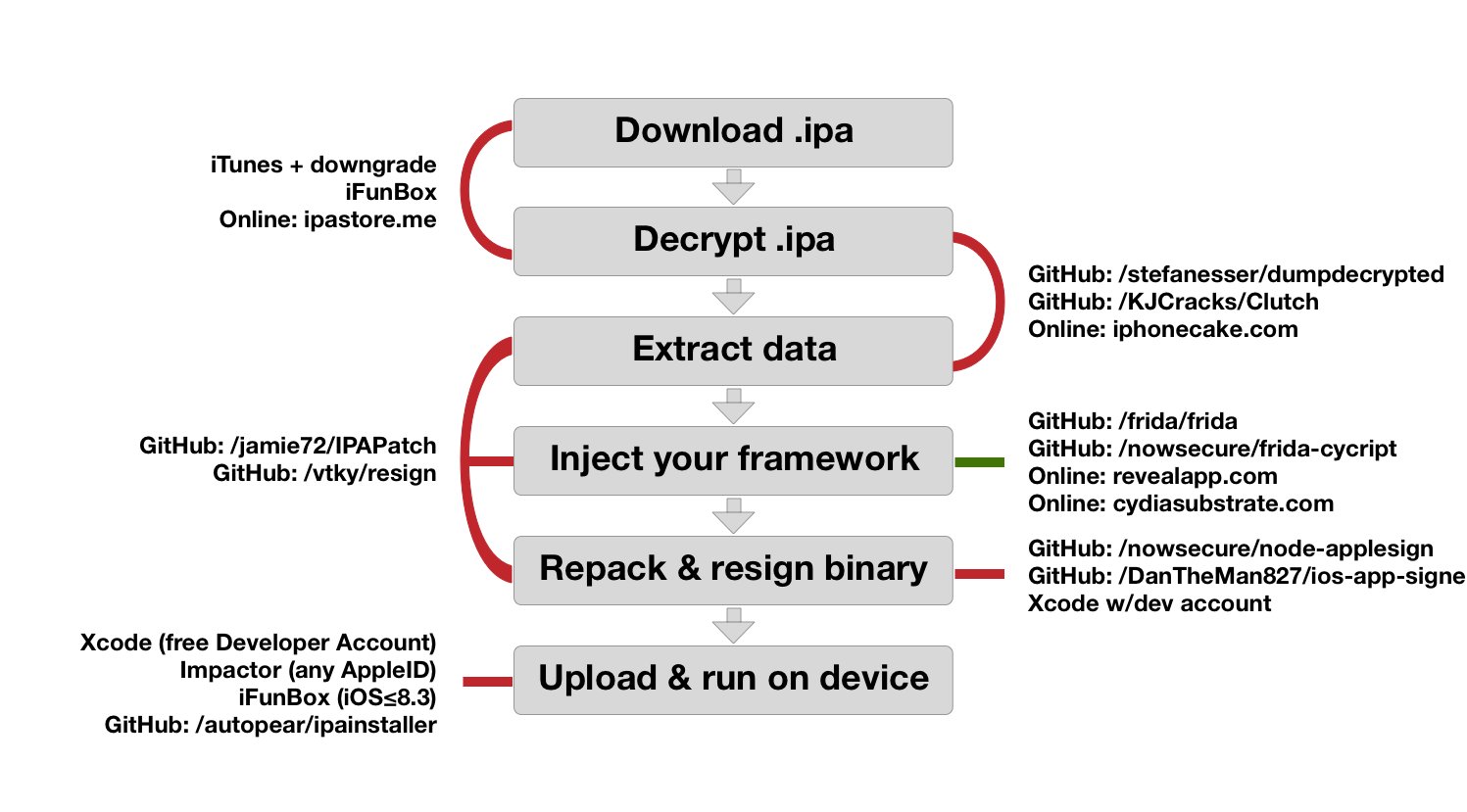
Dynamic analysis of iOS apps without JailbreakIn the article I will share my experience in solving some of the problems I faced when analyzing the security of iOS applications. All the tricks and approaches (if it is not listed separately) applicable on iOS device without Jailbreak.
Source: medium.com
Mar. 16, 2018

Throughout last year, mysterious ailments struck dozens of U.S. andCanadian diplomats and their families living in Cuba. Symptoms includeddizziness, sleeplessness, headache, and hearing loss; many of the afflictedwere in their homes or in hotel rooms when theyheard intense, high-pitched sounds shortly before falling ill. In February, neurologists who examined the diplomats concluded that the symptoms were consistent with concussion, but without any blunt trauma to the head.
Mar. 13, 2018
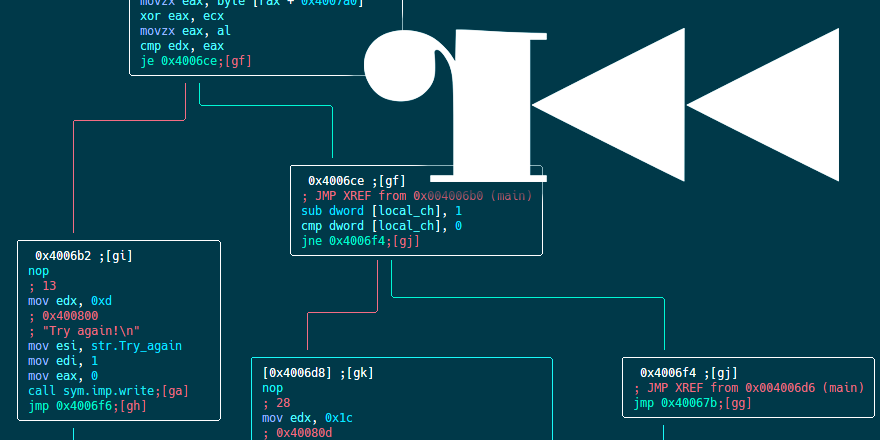
It took me three months to finish writing this article. I had so many tasks on my to-do list that sadly this one was pushed down to the bottom of the list. Last weekend I made a promise to myself that until Sunday I’m going to finish writing it, I successfully kept my word and here it is, another radare2 tutorial.
Source: megabeets.net
Mar. 13, 2018

To find a potential entry point into medical infrastructure, we extract the IP ranges of all organizations that have the keywords “medic”, “clinic”, “hospit”, “surgery” and “healthcare” in the organization’s name, then we start the masscan (port scanner) and parse the specialized search engines (like Shodan and Censys) for publicly available resources of these organizations.
Source: securelist.com
Mar. 6, 2018

When someone commits a crime, it’s safe to assume that person wants to get rid of the evidence; they may wear gloves, or conceal their identity. But criminals get caught, often on the most incidental oversights—some as small and seemingly innocent as a knot in a string.
Source: atlasobscura.com


















