May. 3, 2018

The vulnerability was discovered inthe Volkswagen Golf GTE and an Audi3 Sportback e-tron, which were both manufactured in 2015. Computest researchers Daan Keuper and Thijs Alkemade, who discovered the flaw, said that under certain conditions the IVI vulnerability could enableattackers to commandeer the on-board microphone to listen in on the conversations of the driver, turn the microphone on and off, and access the system’s complete address book and the conversation history. There is also a possibility of hackers tracking the car through the navigation system at any given time, they said.
Apr. 30, 2018

But when we say “memory leak”, what do we actually mean? In my experience, apparent memory leaks divide into three broad categories, each with somewhat different behavior, and requiring distinct tools and approaches to debug. This post aims to describe these classes, and provide tools and techniques for figuring out both which class you’re dealing with, and how to find the leak.
Source: nelhage.com
Apr. 29, 2018

Recently, further developments into other methods to achieve RCE were uncovered. Drupal released advisory SA-CORE-2018-004 with updated versions and patches to fix the newly identified flaws.
Source: trustwave.com
Apr. 27, 2018

To be effective, Clear wouldn’t be binding on just Apple but rather manufacturers of all computing devices, many of them low-cost products made by bootstrapped manufacturers. That means there would be dozens, hundreds, or probably thousands of PIN vaults mandated under Clear. And each of them would be a potential target for hackers all around the world.
Source: arstechnica.com
Apr. 27, 2018

The flaw exists in the Drupal core package in all supported versions of Drupal, eg. 7.x and 8.x releases. This vulnerability allows attackers to exploit Drupal powered sites from numerous attack vectors.
The end result being the site compromised as remote code can be executed, possibly giving unrestricted control to the hosting environment.
Source: drupal.sh
Apr. 25, 2018

If you open the booby-trapped document, which is denoted by Qihoo as containing some unspecified sort of shellcode, Internet Explorer is apparently activated in the background, ultimately leading to an executable program being downloaded and executed without any visible warning.
Source: sophos.com
Apr. 23, 2018

Hundreds of multi-ton liabilities—soaring faster than the speed of sound, miles above the surface of the earth—are operating on Windows-95.
Source: theoutline.com
Apr. 23, 2018

The newly disclosed bypass is a medium-severity issue that affects Windows 10 S or any Windows 10 machine with user mode code integrity (UMCI) enabled, such as enterprise Windows 10 PCs configured with Microsoft’s virtual container known as Device Guard.
Source: zdnet.com
Apr. 19, 2018

Researchers found a new iOS vulnerability called ‘trustjacking,’ which exploits a feature called iTunes Wi-Fi Sync to give attackers persistent control over victims’ devices.
Source: threatpost.com
Apr. 13, 2018

This project is an initiative of NCC Group. It is an open and collaborative project to join efforts in discovering smart contract vulnerabilities within the security community.
Source: dasp.co
Apr. 10, 2018

Hackers equipped with just a laptop and a $30 handheld FM radio could have hijacked the emergency alert system sirens of San Francisco. The hack could have made them go off whenever they wanted, and made the system broadcast custom messages, according to researchers.
Source: vice.com
Apr. 10, 2018

The makers of the programmable Fuze smart card say it’s powerful enough to be your wallet in one card yet secure enough to be used the same way as traditional payment cards—including trusting it to restaurant servers when paying the bill. But it turns out that convenience comes with a major catch. A flaw makes it possible for anyone with even brief physical control of the card to surreptitiously siphon all data stored on the device.
Apr. 7, 2018

Learn how to exploit Bluetooth Low Energy for IoT Devices using a step-by-step guide. In this post, we are using Gattacker to perform sniffing and replay based attacks.
Source: attify.com
Apr. 7, 2018

The company admitted on Twitter that it stores at least part of their customer’s passwords in plaintext. This is a big no-no in this day and age because if anyone breaches T-Mobile (and companies are breached all the time), they could likely guess or brute-force every user’s password. If the passwords were fully encrypted or hashed, it wouldn’t be that easy.
Apr. 6, 2018

This week, two separate security alerts have revealed major holes in devices from Moxa, an industrial automation networking company. In one case, attackers could potentially send commands to a device’s operating system by using them as a username in a login attempt. In another, the private key for a Web server used to manage network devices could be retrieved through an HTTP GET request.
Apr. 5, 2018
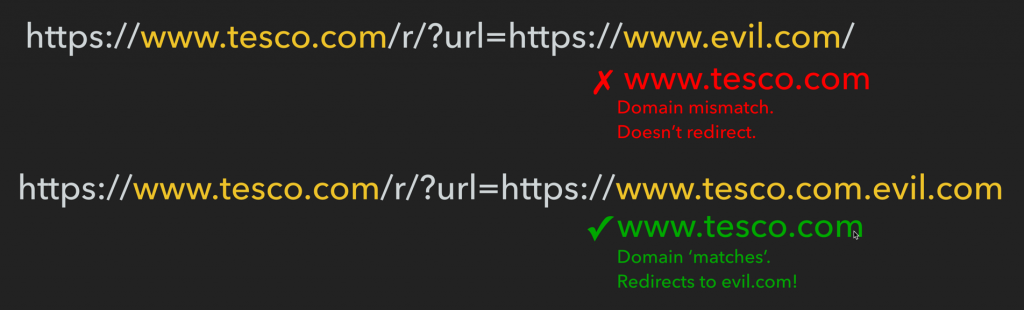
For the $12 cost of a domain, I was able to rank in Google search results with Amazon, Walmart etc. for high value money terms in the US. The Adwords bid price for some these terms is currently around $1 per click, and companies are spendings 10s of thousands of dollars a month to appear as ads on these search results, and I was appearing for free.
Apr. 5, 2018

The Intel Remote Keyboard product is an Android and iOS app that works in conjunction with Intel’s mini-PC platform called Next Unit of Computing (NUC) and with the chipmaker’s Compute Stick. NUCs are similar in size and function to Raspberry Pi systems. Compute Sticks are about the size of a large flash drive and are single-board computers used both in classrooms, kiosks and in some network computer environments.
Mar. 31, 2018
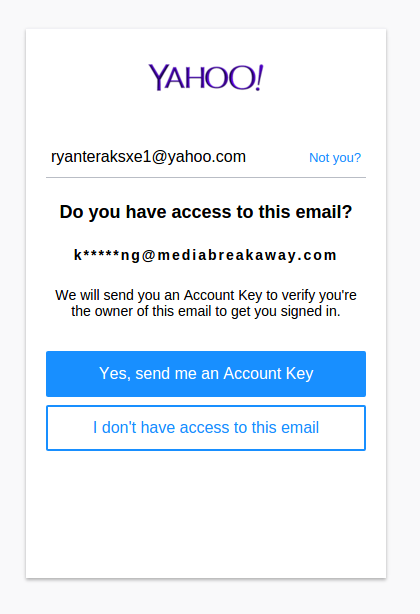
Chambers said the user who visited that domain told him that after typing in espn.com he quickly had his computer screen filled with alerts about malware and countless other pop-ups. Security logs for that user’s system revealed the user had actually typed espn[dot]cm, but when Chambers reviewed the source code at that Web page he found an innocuous placeholder content page instead.
Mar. 29, 2018

All versions of the Drupal content management system are affected by a highly critical vulnerability that can be easily exploited to take complete control of affected websites in what may turn out to be Drupalgeddon 2.0.
Source: securityweek.com
Mar. 27, 2018
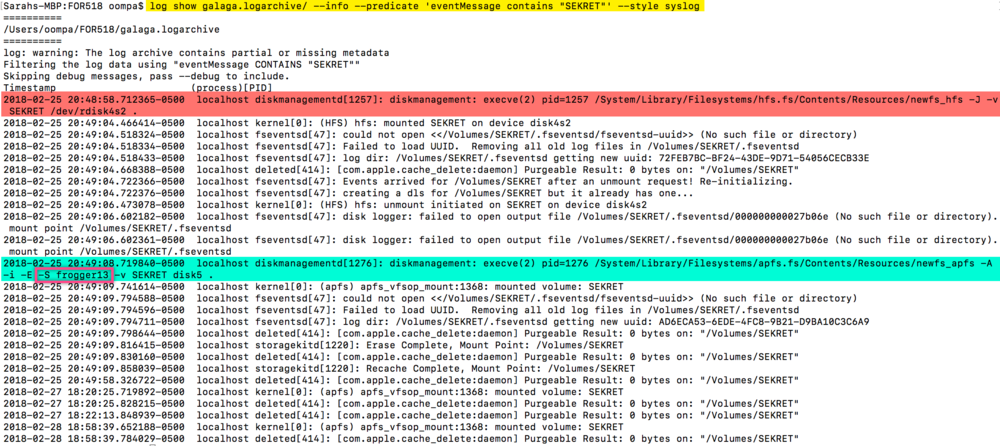
It may not be noticeable at first (apart from the highlighting I’ve added of course), but the text “frogger13” is the password I used on a newly created APFS formatted FileVault Encrypted USB drive with the volume name “SEKRET”. (The new class images have a WarGames theme, hence the shout-outs to classic video games!)
Source: mac4n6.com


















