Mar. 7, 2018

The Devcore researchers said as many as 400,000 servers are at risk. Queries on the Shodan computer search engine identified a large number of servers that reported running vulnerable versions. The developers published a fix with version 4.90.1, which was released on February 10.
Any organization that uses Exim should ensure it’s using the latest version.
Source: arstechnica.com
Mar. 7, 2018

Academics from the University of Michigan have shown that one single malicious car could trick US-based smart traffic control systems into believing an intersection is full and force the traffic control algorithm to alter its normal behavior, and indirectly cause traffic slowdowns and even block street intersections.
Source: bleepingcomputer.com
Mar. 7, 2018
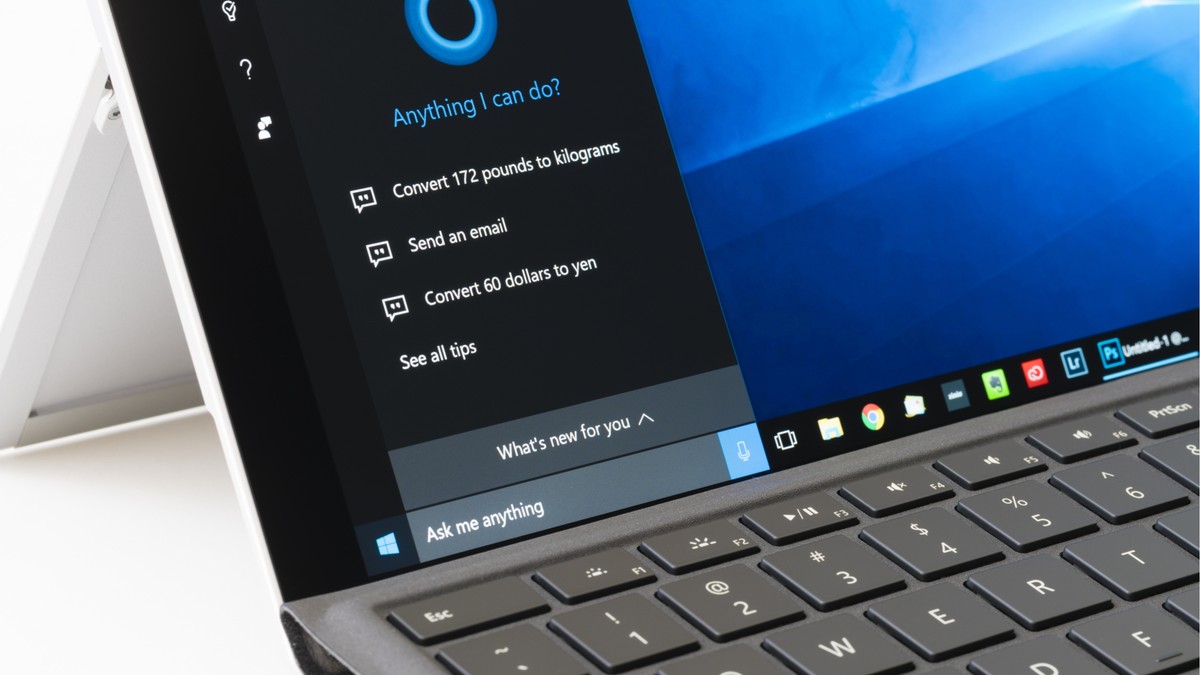
Tal Be’ery and Amichai Shulman found that the always-listening Cortana agent responds to some voice commands even when computers are asleep and locked, allowing someone with physical access to plug a USB with a network adapter into the computer, then verbally instruct Cortana to launch the computer’s browser and go to a web address that does not use https—that is, a web address that does not encrypt traffic between a user’s machine and the website. The attacker’s malicious network adapter then intercepts the web session to send the computer to a malicious site instead, where malware downloads to the machine, all while the computer owner believes his or her machine is protected.
Mar. 6, 2018

There have been lots of reasons to be concerned about how easily someone with the right tools and knowledge could do very bad things with cellular communications networks. And while none of them have necessarily been to the level of some of the fictional stunts pulled off on television (see Mr. Robot), new research shows that things are even worse than they appear—and in many cases, that’s because of how carriers have implemented cellular standards.
Mar. 6, 2018
It was a hot summer evening back in August 2014. I was working on my master’s thesis project. The project was about building software controlling a group of mobile robots and at that time I was running some simulations.
The main part was running on a Linux machine, but the simulator had to be run on Windows, so I decided to put it in VMware virtual machine. Looking back, I must admit it was very overcomplicated, but I was still a student and I had a lot of free time.
Mar. 6, 2018

Phone numbers are not reliable. Phone numbers can be hijacked. Phone numbers change.
Phone numbers stop working when you are traveling and not roaming. Phone numbers don’t work when you are using in-flight Wi-Fi. Phone numbers can stop receiving text messages/calls for a million of other reasons, effectively either (1) locking users out of an account or (2) compromising the account altogether.
Mar. 5, 2018

A scan of nearly one million Ethereum smart contracts has identified 34,200 vulnerable contracts that can be exploited to steal Ether, and even freeze or delete assets in contracts the attackers don’t own.
Source: bleepingcomputer.com
Mar. 3, 2018

A slew of newly discovered vulnerabilities can wreak havoc on 4G LTE network users by eavesdropping on phone calls and text messages, knocking devices offline, and even spoofing emergency alerts.
Source: zdnet.com
Mar. 3, 2018

This paper presents a detailed and up-to-date security analysis of the voting software used in Brazilian elections. It is based on results obtained by the authors in a recent hacking challenge organized by the Superior Electoral Court (SEC), the national electoral authority. Duri…
Source: researchgate.net
Mar. 2, 2018

Data exposure reports have reached a dizzying pace in the past few months, and the security community has been focused on the risk from multiple angles. Now, a new study from HTTPCS gives us new insight into rates of vulnerable S3 configurations.
Source: tripwire.com
Mar. 1, 2018

The WordPress plugin WooCommerce runs on approximately 2,300,000 live websites1 and is currently the most prominent eCommerce platform used on the Web. During our research we discovered a PHP object injection vulnerability in WooCommerce that allows to escalate privileges. The vulnerability was responsibly disclosed to the Automattic security team and was fixed last year with the release of version 3.2.4.
In this blog post we investigate how recent changes in the WordPress core database driver opened the doors for this vulnerability. Furthermore, we describe how the circumstances could be exploited with a unique and interesting injection technique.










