DBGer Ransomware Uses EternalBlue and Mimikats to Spread Across Networks
Jun 15, 2018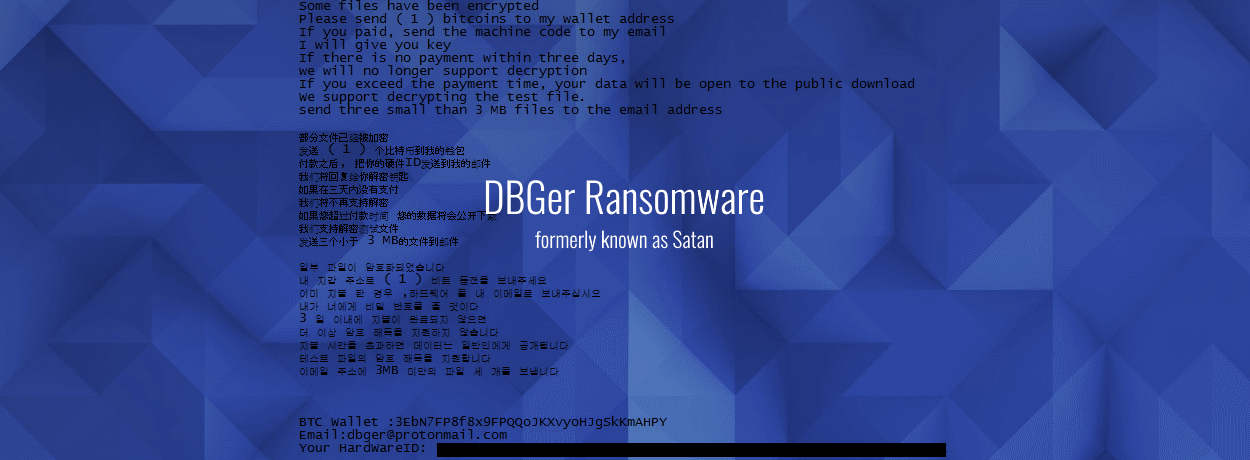
The change was not only in name but also in the ransomware’s modus operandi. According to the researcher, whose discovery was later confirmed by an Intezer code similarity analysis, the new (Satan) DBGer ransomware now also incorporates Mimikatz, an open-source password-dumping utility. The purpose of DBGer incorporating Mimikatz is for lateral movement inside compromised networks.
This fits a recently observed trend in Satan’s modus operandi. The Satan ransomware launched in January 2017 as a Ransomware-as-a-Service (RaaS) portal, allowing anyone to register and create custom versions of the Satan ransomware. First versions were unsophisticated, as most new ransomware variants tend to be.
For a long time, the Satan crew rented its ransomware to other crooks, who then distributed it to victims, mostly via email spam (malspam) campaigns. With time, the ransomware gained a lot of reputation and clients on the criminal underground. The group behind the LockCrypt ransomware started as Satan RaaS customers before developing their own strain.
Further, other ransomware devs took inspiration from the Satan code, such as the Iron ransomware group. But the Satan crew didn’t stand idly either. As the ransomware scene evolved in 2017, they evolved as well.
Changes in the ransomware scene of 2017 included self-spreading mechanisms (seen in the three ransomware outbreaks of last year) and a move to infecting larger networks instead of home users (because of larger payouts and payout rate). Around November 2017, Satan devs started their plans of updating the ransomware to better fit these trends.
Source: bleepingcomputer.com