Sep. 25, 2020

Gangs of cybercriminals forced British companies to pay out more than £200 million in ransoms last year, experts have revealed. The extortionists, many from Russia or Eastern European countries, are targeting well-known businesses with malicious software and then charging them tens of millions of pounds to regain access to networks. Companies fearful of public embarrassment, lost data and fines from regulators are now showing “more willingness to pay the ransom”, experts said.
Sep. 25, 2020

The incident marks the first recorded casualty as a consequence of cyberattacks on critical healthcare facilities, which has ramped up in recent months. The attack, which exploited a Citrix ADCCVE-2019-19781vulnerability to cripple the hospital systems on September 10, is said to have been ‘misdirected’ in that it was originally intended for Heinrich Heine University, according to an extortion note left by the perpetrators. After law enforcement contacted the threat actors and informed them that they had encrypted a hospital, the operators behind the attack withdrew the ransom demand and provided the decryption key.
Oct. 5, 2019

All three hospitals that make up the DCH Health System in Alabama were closed to new patients on Tuesday as officials there coped with an attack that paralyzed the health network’s computer system. The hospitals—DCH Regional Medical Center in Tuscaloosa, Northport Medical Center, and Fayette Medical Center—are turning away ‘all but the most critical new patients’ at the time this post was going live. Local ambulances were being instructed to take patients to other hospitals when possible.
May. 22, 2019

It’s been nearly two weeks since the City of Baltimore’s networks were shut down in response to a ransomware attack, and there’s still no end in sight to the attack’s impact. It may be weeks more before the city’s services return to something resembling normal—manual workarounds are being put in place to handle some services now, but the city’s water billing and other payment systems remain offline, as well as most of the city’s email and much of the government’s phone systems. The ransomware attack came in the midst of a major transition at City Hall.
Jun. 15, 2018
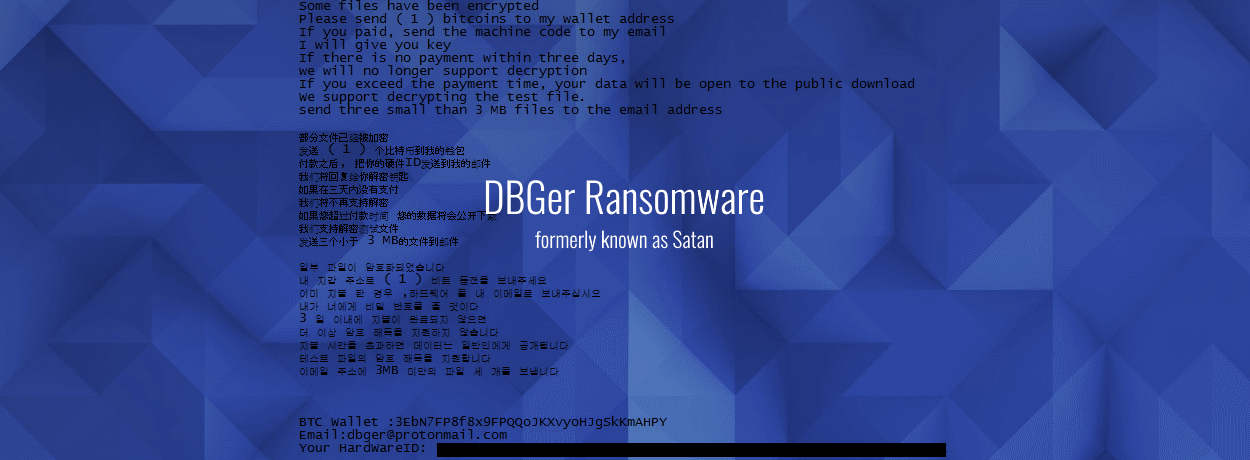
The change was not only in name but also in the ransomware’s modus operandi. According to the researcher, whose discovery was later confirmed by an Intezer code similarity analysis, the new (Satan) DBGer ransomware now also incorporates Mimikatz, an open-source password-dumping utility. The purpose of DBGer incorporating Mimikatz is for lateral movement inside compromised networks.
This fits a recently observed trend in Satan’s modus operandi. The Satan ransomware launched in January 2017 as a Ransomware-as-a-Service (RaaS) portal, allowing anyone to register and create custom versions of the Satan ransomware. First versions were unsophisticated, as most new ransomware variants tend to be.
Jun. 6, 2018

The Atlanta Police Department has lost years worth of police car dashcam videos following the March ransomware attack that affected most of the city’s IT infrastructure. Chief Shields said footage from body-worn cameras was not compromised in the cyber-attack that crippled Atlanta city IT systems for almost two months, but only videos recorded by police car dashcams. The normal train of thought is that the loss of the dashcam data could affect some DUI investigations, but Chief Shields downplayed the importance of the dashcam footage in pursuing DUI charges.
May. 12, 2018

Secret Service agents are now investigating the point of entry for both infections, hoping to find clues and track down the hackers. The first ransomware infection took place on April 23, last month and encrypted ten months worth of work data related to active investigations. Officials said they didn’t pay the ransom and were able to recover some of the data from previous backups.
May. 8, 2018
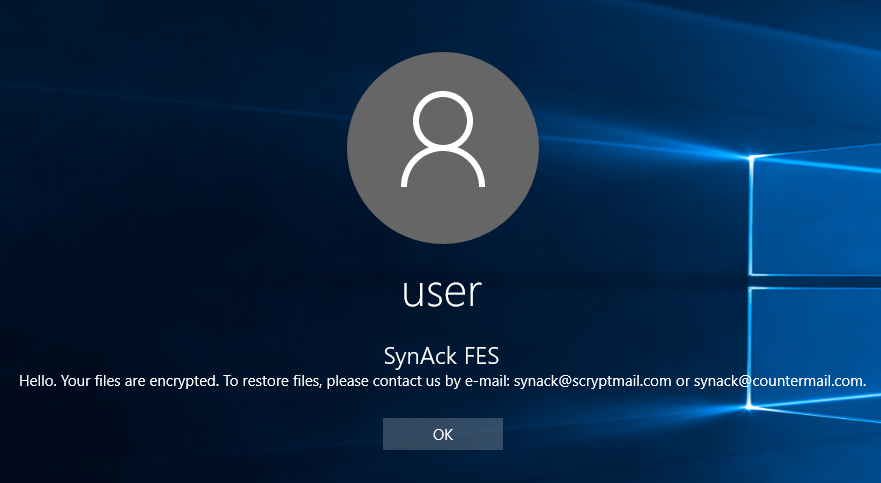
The Process Doppelgänging technique was first presented in December 2017 at the BlackHat conference. Since the presentation several threat actors have started using this sophisticated technique in an attempt to bypass modern security solutions. In April 2018, we spotted the first ransomware employing this bypass technique – SynAck ransomware.
It should be noted that SynAck is not new – it has been known since at least September 2017 – but a recently discovered sample caught our attention after it was found to be using Process Doppelgänging. Here we present the results of our investigation of this new SynAck variant.
May. 3, 2018

And despite the nefarious nature of the school system’s lockdown, there is no criminal investigation into the matter because solving this crime is “impossible,” said Interim Leominster Police Chief Michael Goldman.
Source: cbslocal.com
Apr. 30, 2018

There is nothing impressive about them, in fact just the opposite. I would say they are boring at best. So why are we writing about one of them?
The analysis of Spartacus can essentially be used as a base knowledge and reference for anyone analyzing variants of these basic .NET ransomware that they may come across in the future.
Source: malwarebytes.com
Apr. 27, 2018
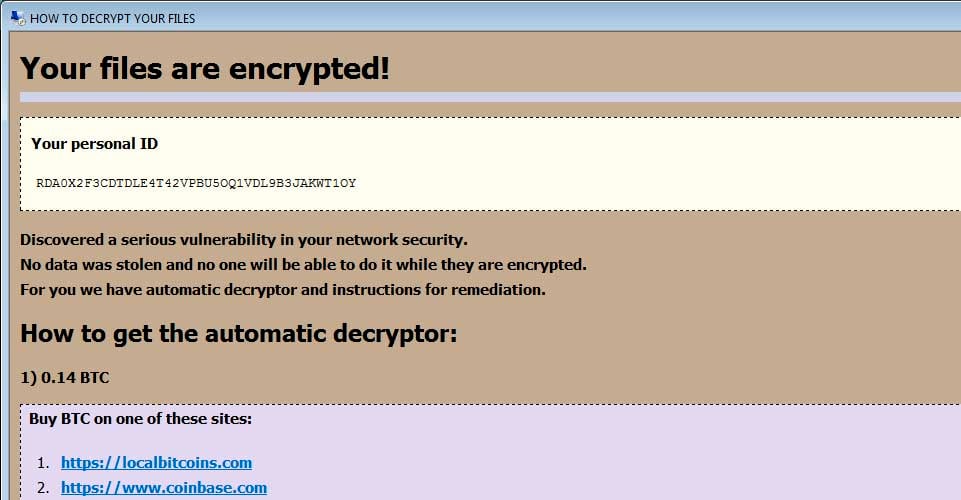
A new in-development ransomwarewas discovered that has an interesting characteristic. Instead of the distributed executable performing the ransomware functionality, the executablescompiles an embedded encrypted C# program at runtime and launches it directly into memory.
Source: bleepingcomputer.com
Apr. 24, 2018

The City of Atlanta spent more than $2.6 million on emergency efforts to respond to a ransomware attack that destabilized municipal operations last month. Attackers, who infected the city’s systems with the pernicious SamSam malware, asked for a ransom of roughly $50,000 worth of bitcoin. (The exact value has fluctuated due to bitcoin’s volatility.)
Atlanta officials haven’t said whether they paid the ransom, or even tried, but it seems that they may not have even had the chance; the attackers quickly took the payment portal offline, and left the city to fend for itself. So far, the recovery has been far more costly than the initial demand.
Apr. 15, 2018
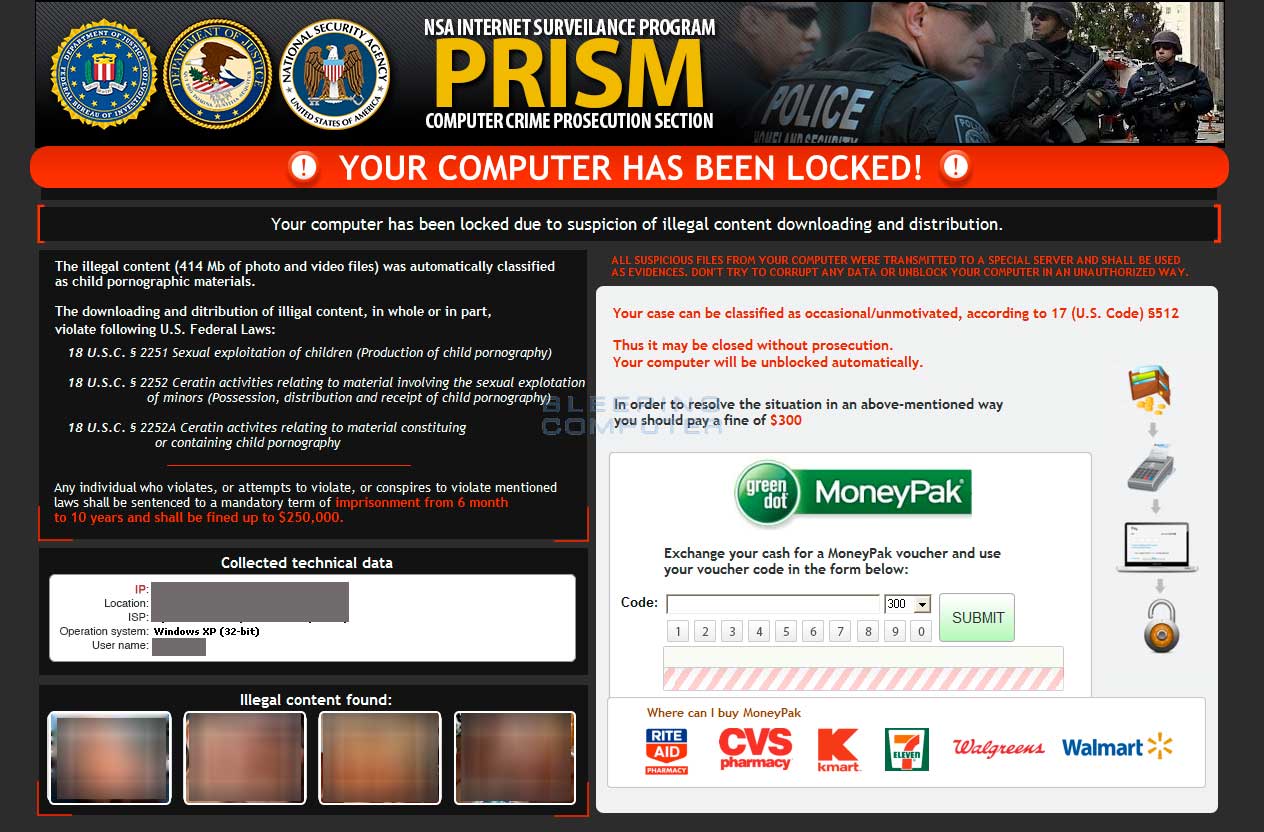
The accused is Raymond Uadiale, 41, a naturalized US citizen of Nigerian descent, who currently works for Microsoft in Seattle since 2014, according to his LinkedIn page.
Source: bleepingcomputer.com
Apr. 10, 2018

Two new Matrix Ransomware variants were discovered this week by MalwareHunterTeamthat arebeing installed through hacked Remote Desktop services. While both of these variants encrypt your computer’s files, one is a bit more advanced with more debugging messages and the use of cipher to wipe free space.
Source: bleepingcomputer.com
Mar. 29, 2018

According to areport from theSeattle Times, the dreaded WannaCry ransomware hit a Boeing production plant in Charleston, South Carolina on Wednesday.
Source: securityaffairs.co
Mar. 24, 2018

You get two for the price of one with today’s paper! Firstly, it’s a fascinating insight into the ransomware business and how it operates, with data gathered over a period of two years. Secondly, since ransomware largely transacts using Bitcoin, the methods used by the research team to uncover and trace ransomware activity are also of interest in their own right.
Source: acolyer.org
Mar. 23, 2018

According to a report from Atlanta NBC affiliate WXIA, a city employee sent the station a screen shot of a ransomware message demanding a payment of $6,800 to unlock each computer or $51,000 to provide all the keys for affected systems. Employees received emails from the city’s information technology department instructing them to unplug their computers if they noticed anything suspicious. An internal email shared with WXIA said that the internal systems affected include the city’s payroll application.
Mar. 22, 2018

McAfee Labs has recently observed a new variant of ransomware that relies on the open-source program GNU Privacy Guard (GnuPG) to encrypt data. GnuPG is a hybrid-encryption software program that uses a combination of conventional symmetric-key cryptography for speed and public-key cryptography to ease the secure key exchange. Although ransomware using GnuPG to encrypt files is not unique, it is uncommon.
Mar. 16, 2018

For those behind GandCrab, staying profitable and staying one-step ahead of white hats means adopting a never-before-seen agile malware development approach, said Check Point.
Source: threatpost.com
Mar. 1, 2018

In part one of this series, Encryption 101: a malware analyst’s primer, we introduced some of the basic encryption concepts used in malware. If you haven’t read it, we suggest going back for a review, as it’s necessary in order to be able to fully follow part two, our case study. In this study, we will be reviewing the encryption of the ransomware ShiOne line by line.



















