DNS Poisoning or BGP Hijacking Suspected Behind Trezor Wallet Phishing Incident
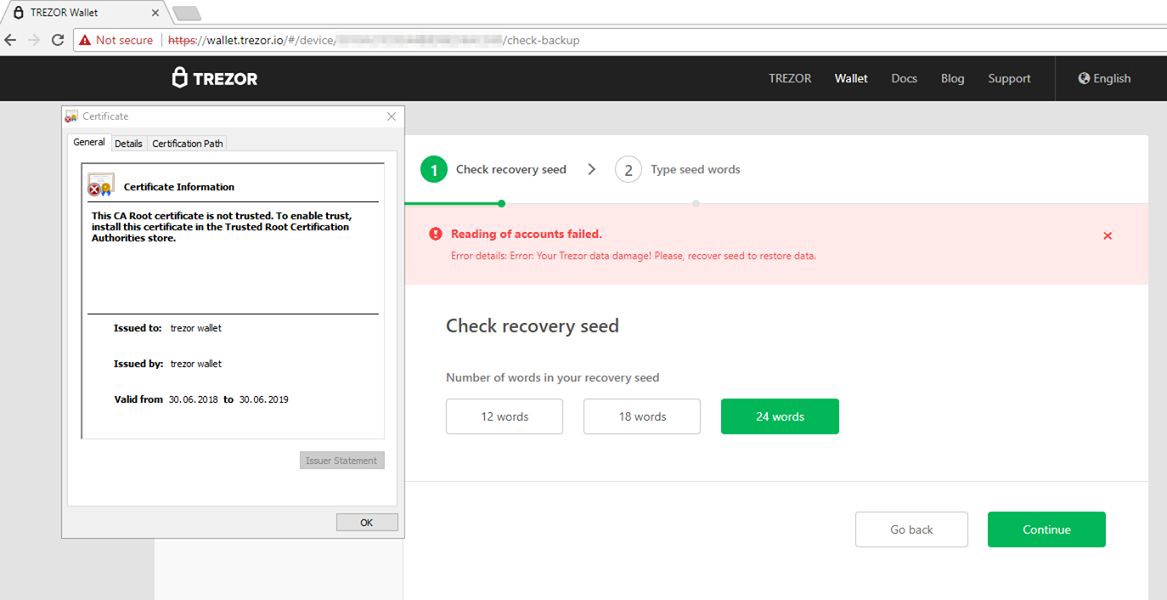
The Trezor team says ‘signs point toward DNS poisoning or BGP hijacking’ as the means attackers hijacked legitimate traffic meant for the official wallet.trezor.io domain but redirected these users to a malicious server hosting a fake website. An investigation is still underway to determine the exact cause. The incident came to light after users complained that they encountered an invalid HTTPS certificate when landing on Trezor’s web wallet portal.
An invalid certificate usually means that the website on which users landed was not the actual portal, but someone posing as the Trezor website, which could not cryptographically verify itself as the real website. This error alerted the Trezor community, whose members quickly reported the incident to the Trezor team, who later confirmed the phishing attempt and warned users about the attack on early Sunday morning (US timezones). The Trezor team said they determined this was a legitimatee phishing attack and not just random SSL server error (which tend to happen some of the time) because they spotted two problems with the fake website.
The first was an error message that was worded differently from the original Trezor site, which told users that syncing data their Trezor hardware wallet and their Trezor web account had failed. Second, the fake website was asking users to enter a copy of their ‘recovery seed,’ something the Trezor team said would never do.
Source: bleepingcomputer.com