Cyber security news and services
Cortana Hack Lets You Change Passwords on Locked PCs
Microsoft has patched a vulnerability in the Cortana smart assistant that could have allowed an attacker with access to a locked computer to use the smart assistant and access data on the device, execute malicious code, or even change the PC’s password to access the device in its entirety. The issue was discovered by Cedric Cochin, Cyber Security Architect and Senior Principle Engineer at McAfee. Cochin privately reported the problems he discovered to Microsoft in April.
…UK’s Dixons Carphone admits huge data breach

Dixons Carphone has admitted a huge data breach involving 5.9 million payment cards and 1.2 million personal data records. It is investigating the hacking attempt, which began in July last year. Dixons Carphone said it had no evidence that any of the cards had been used fraudulently following the breach.
There was ‘an attempt to compromise’ 5.8 million credit and debit cards but only 105,000 cards without chip-and-pin protection had been leaked, it said. The hackers had tried to gain access to one of the processing systems of Currys PC World and Dixons Travel stores, the firm said. Dixons Carphone shares were down more than 3% in early afternoon trading.
…Code Injection in Moodle

Moodle is a widely-used open-source e-Learning software with more than 127 million users allowing teachers and students to digitally manage course activities and exchange learning material, often deployed by large universities. In this post we will examine the technical intrinsics of a critical vulnerability in the previous Moodle release detected by RIPS Code Analysis. It is located in the Quiz component of Moodle and can be successfully exploited through the teacher role in order to perform remote code execution.
…Simple technique bypassed macOS signature checks by third-party tools
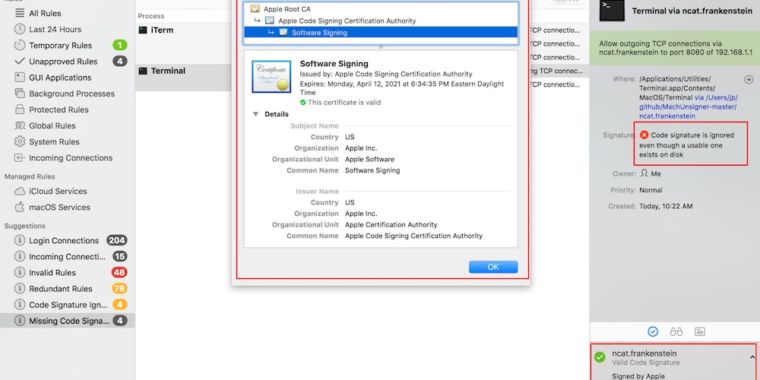
For almost 11 years, hackers have had an easy way to get macOS malware past the scrutiny of a host of third-party security tools by tricking them into believing the malicious wares were signed by Apple, researchers said Tuesday. Digital signatures are a core security function for all modern operating systems. The cryptographically generated signatures make it possible for users to know with complete certainty that an app was digitally signed with the private key of a trusted party.
…Florida skips gun background checks for a year after employee forgets login

In Florida, the site of recent mass shootings such as at the Stoneman Douglas High School and the Pulse nightclub, more than a year went by in which the state approved applications without carrying out background checks. This meant the state was unaware if there was a cause to refuse a licence to allow somebody to carry a hidden gun – for example, mental illness or drug addiction. The reason is dismayingly banal: an employee couldn’t remember her login.
…Ethereum “Giveaway” Scammers Have Tricked People Out of $4.3 Million
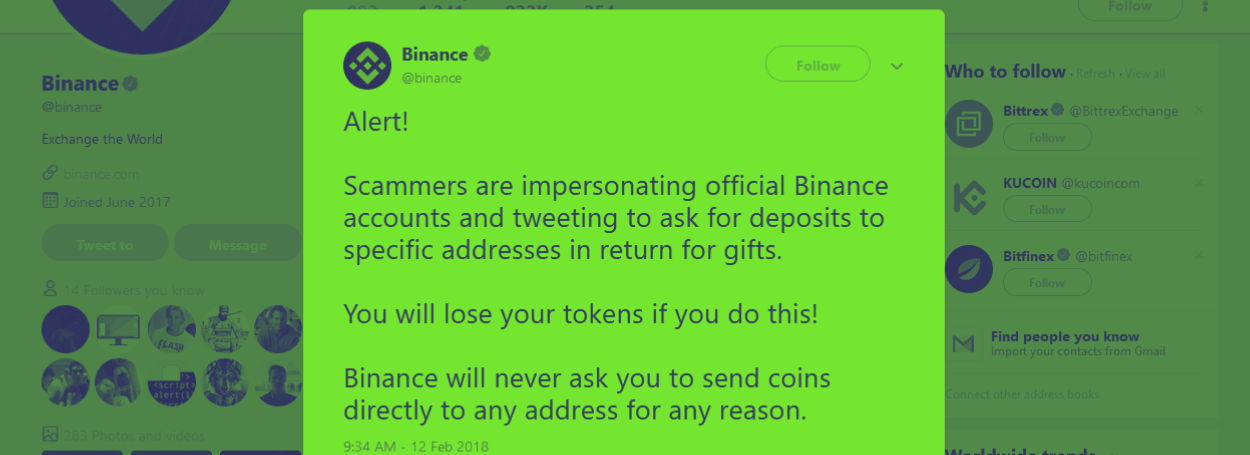
The EtherScamDB website was created by the team behind the MyCrypto wallet service for the purpose of tracking various types of online scams centering around the Ethereum platform and associated cryptocurrencies and assets. For the past few months, the website has been inventorying various types of Ethereum scams, such as classic phishing sites that imitate legitimate apps and wallets, trust-trading sites that push inaccurate advice or recommendations, but also online giveaways scams that promise to multiply Ether funds if victims transfer crooks a small sum of money. The latter category has recently become rampant on Twitter, and on a daily basis, the social network’s most popular tweets are often inundated by these ‘Ether giveaway’ scams.
…Apple Bans Apps That Mine Cryptocurrencies
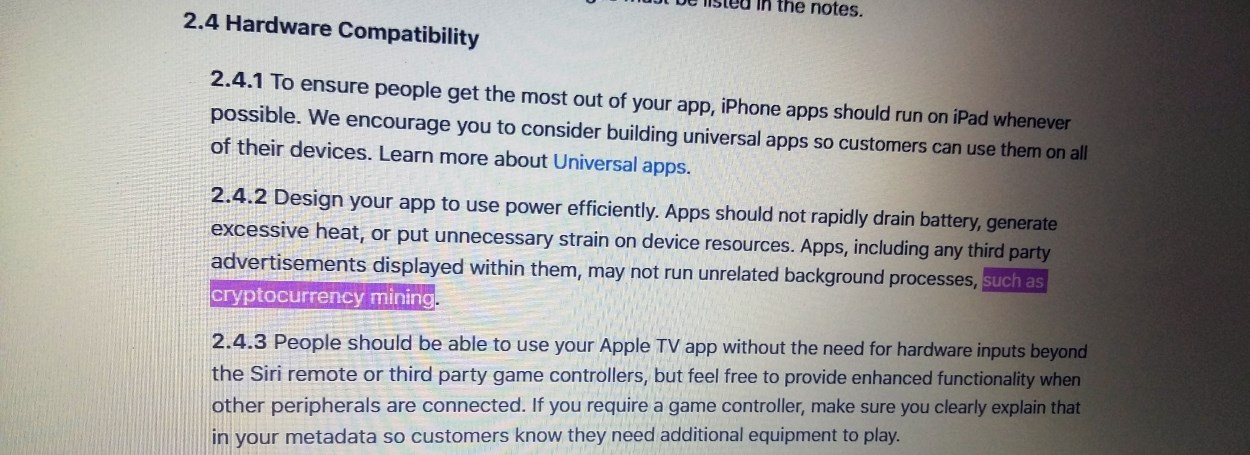
Apple has updated its review guidelines to specifically prohibit iOS and Mac apps uploaded on the company’s official App Store from utilizing users’ devices for cryptocurrency mining operations. The ban applies for apps designed explicitly with mining operations in mind. Other cryptocurrency-related functions, like managing or trading cryptocoin funds, are still permitted.
Two sections have been updated in the new App Store Review Guidelines —section 2.4.2 (Hardware Compatibility) and 3.1.5 (b) (ii) (Cryptocurrencies). Apple updated its App Store review guidelines last week, during the WWDC 2018 conference. The company took this step after hidden cryptocurrency mining has become the most popular cybercrime trend among malware developers this past year.
…Bitcoin price takes a dive after another cryptocurrency exchange hack

The exchange in question is called Coinrail, and if you visit its website right now you’ll see a “System maintenance” message that tells you more than they’re just updating the servers. The devil’s in the detail – the site is down because it got hacked over the weekend. The statement on Coinrail’s website says that some (but not all) of the cryptocurrency exchange’s digital currency was stolen by hackers.
…Tens of Thousands of Android Devices Are Exposing Their Debug Port

The issue is not new, being first spotted by the team at Qihoo 360 Netlab in February, this year, when they detected an Android worm that was spreading from Android device to Android device, infecting them with a cryptocurrency miner named ADB.Miner. The ADB.Miner worm exploited the Android Debug Bridge (ADB), a feature of the Android OS used for troubleshooting faulty devices. In the default version of the Android OS, the ADB feature is turned off, and users need to manually enable it while connecting their device via a USB connection.
…Canada using Excel function for immigration lottery
/arc-anglerfish-tgam-prod-tgam.s3.amazonaws.com/public/GP5OOKYKKRIUTKKYHXMRX2HIRQ.jpg)
Canada’s family-reunification program is using a common spreadsheet application to select candidates as part of a process critics say is flawed and open to manipulation. As the first step in the program, the federal government uses Microsoft Excel to randomly pick applications in its lottery, The Globe and Mail has learned. Experts have warned that using Excel to conduct such a sensitive lottery could be problematic, and that the lottery process itself may make the system less fair over all.
…Hackers Crashed a Bank’s Computers While Attempting a SWIFT Hack

Hackers have used a disk-wiping malware to sabotage hundreds of computers at a bank in Chile to distract staff while they were attempting to steal money via the bank’s SWIFT money transferring system. The attempted hack took place on May 24, this year. On that day, the Banco de Chile, the country’s biggest bank, reported all-around systems failures that affected the computers at several of its branches.
…Chinese hackers ‘steal US navy data on undersea warfare and supersonic missiles’

China’s state hackers have reportedly stolen a large amount of highly-sensitive US navy data on its undersea warfare, including plans for supersonic anti-ship missiles on submarines. Government experts were said to have compromised the computers of a US navy contractor, giving them access to the information, according to the Washington Post, citing unnamed American officials. They said – on the condition of anonymity about an ongoing investigation – that the security breaches were believed to have taken place in January and February.
…Flash zero-day exploit

Adobe is aware of a report that an exploit for CVE-2018-5002 exists in the wild, and is being used in limited, targeted attacks against Windows users. These attacks leverage Office documents with embedded malicious FlashPlayercontent distributed via email. Unlike the critical vulnerabilities patched in Adobe’sMarch, Apriland May updates, CVE-2018-5002 isn’t a remotely exploitable flaw that cybercriminals might decide to exploit in future, it’s one that we only know about because they’re exploiting it now, a so-called zero-day.
…Blocking facial recognition surveillance using AI

If Artificial Intelligence (AI) is increasingly able to recognise and classify faces, then perhaps the only way to counter this creeping surveillance is to use another AI to defeat it. We’re in the early years of AI-powered image and face recognition but already researchers at the University of Toronto have come up with a way that this might be possible. The principal at the heart of this technique is adversarial training, in which a neural AI network’s image recognition is disrupted by a second trained to understand how it works.
…Malta Pilots Blockchain-Based Credentials Program

Malta, an island nation in the Mediterranean Sea, is completing the first ever attempt by a nation state to tie citizen records to the blockchain. If successful, a scaled-up version of the pilot program will give Malta’s 400,000 residents the ability to retrieve and share educational records and transcripts for free. What’s more, it wouldprovide a proof-of-concept that could inspire other countries to adopt similar programs.
…Years of Police Dashcam Video Lost in Atlanta Ransomware Incident

The Atlanta Police Department has lost years worth of police car dashcam videos following the March ransomware attack that affected most of the city’s IT infrastructure. Chief Shields said footage from body-worn cameras was not compromised in the cyber-attack that crippled Atlanta city IT systems for almost two months, but only videos recorded by police car dashcams. The normal train of thought is that the loss of the dashcam data could affect some DUI investigations, but Chief Shields downplayed the importance of the dashcam footage in pursuing DUI charges.
…MyHeritage Genealogy Site Announces Mega Breach Affecting 92 Million Accounts

Family genealogy and DNA testing site MyHeritage announced on Monday a security breach during which an attacker made off with account details for over 92 million MyHeritage users. The incident came to light after a security researcher found an archive on a third-party server containing the personal details of 92,283,889 MyHeritage users. The archive contained only emails and hashed passwords, but not payment card details or DNA test results.
…Fitness app PumpUp leaked health data, private messages

A popular fitness app that claims over six million users was leaking private and sensitive data, including health information and private messages sent between users. PumpUp, an Ontario-based company, bills itself as a fitness community, allowing subscribers to discover new workouts and record their results, and get advice from fitness coaches and other users. But the company left a core backend server, hosted on Amazon’s cloud, exposed without a password, allowing anyone to see who was signing on and who was sending messages — and their contents — in real-time.
…Hacker Defaces Ticketfly’s Website, Steals Customer Database

A hacker briefly took over Ticketfly’s website, defacing it with a picture of the V for Vendetta character and a claim of responsibility. The hacker also sent Motherboard files of what they say is employee and customer information taken from Ticketfly’s database. Ticketfly, which is owned by Eventbrite, took down the site and posted a message saying that the company had been “the target of a cyber incident.”
…An Exploit Left Millions of Steam Users Vulnerable for the Past 10 Years

The vulnerability has been present and exploitable in Steam for at least 10 years, according to Tom Court, a security researcher at Contextis, who wrote about the bug on Wednesday. Court said the bug left all 125 million Steam users vulnerable until March of this year, when Valve, the developers of Steam, patched it. In other words, by exploiting this bug, hackers could have executed code on the victim’s machine, effectively taking full control over it.
…