Cyber security news and services
Why ‘remote detonator’ is a bad name for your Wi-Fi network

He brought it to the attention of the manager, who promptly evacuated the 24-hour gym and called police. According to Saginaw Township Police Chief Donald Pussehl, a bomb-sniffing dog made a sweep of the premises, but it didn’t turn up any explosives.
Source: sophos.com
…ODNS: Oblivious DNS

To address this type of attacker, we present Oblivious DNS (ODNS), which is a new design of the DNS ecosystem that allows current DNS servers to remain unchanged and increases privacy for data in motion and at rest. In the ODNS system, both the client is modified with a local resolver, and there is a new authoritative name server for .odns. To prevent an eavesdropper from learning information, the DNS query must be encrypted; the client generates a request for www.foo.com, generates a session key k, encrypts the requested domain, and appends the TLD domain .odns, resulting in {www.foo.com}k.odns.
…T-Mobile fined $40M for deceiving customers with fake ring tones

T-Mobile admitted its deceptive scheme to the commission and received a $40 million fine. Given that the trick affected “hundreds of millions” of people in rural areas and perhaps billions of calls, the fine represents just a few cents per call. Even worse: Consumers will not see a cent for this deception that.
According to Ars Technica,FCC Commissioner Mignon Clyburn–who just stepped down from her post–was deeply critical of the fine, calling it absurdly low. The compliance plan contained in the FCC ruling, she says, “does not contain any concessions that would explain such a massive discount.” With Trump-appointed Ajit Pai in charge of the FCC, the treatment of telecomm companies probably won’t change any time soon.
…Over 20,000,000 of Chrome Users are Victims of Fake Ad Blockers

According to the PageFair 2014 report, Google Chrome is a major driver of adblock growth. 20% of users discovered ad blocking by browsing “available browser extensions”. Given how popular ad blocking is, it is quite a lot.
This also explains why ‘cloning’ wide-spread ad blockers has become so popular among online crooks. Seven months ago big news broke: 37,000 users were tricked into installing a fake Adblock Plus extension.
…Inside the Unnerving CCleaner Supply Chain Attack
Hackers initially got onto Piriform’s London networks by using stolen credentials to log into a TeamViewer remote desktop account on a developer PC. From there, the attackers moved laterally to a second computer, always working outside office hours when it was unlikely that people would be using the machines. The attackers installed malware called ShadowPad, sort of customizable malware platform that can be used for an assortment of attacks from DDoS to keylogging, on the compromised computers.
…Millions of Apps Leak Private User Data Via Leaky Ad SDKs

Millions of apps leak personal identifiable information such as name, age, income and possibly even phone numbers and email addresses. At fault are app developers who do not protect ad-targeting data transmitted to third-party advertisers.
Source: threatpost.com
…Proof-Of-Work is a Decentralized Clock

This is an explanation of the key function on Proof-of-Work in the Bitcoin blockchain. It focuses on the one feature of Proof-of-Work that is essential and shows that other features often talked about such as security are secondary side-effects, useful, but not essential.
Source: grisha.org
…This Is the Facial Recognition Tool at the Heart of a Class Action Suit Against Facebook

As Reuters reports, the lawsuit alleges that Facebook improperly collected and stored users’ biometric data. It was originally filed in 2015 by Facebook users in Illinois, which passed the Biometric Information Privacy Act (BIPA) in 2008. The law regulates the collection and storage of biometric data, and requires that a company receive an individual’s consent before it obtains their information.
…Magnitude exploit kit switches to GandCrab ransomware

The GandCrab ransomware is reaching far and wide via malspam, social engineering schemes, and exploit kit campaigns. On April 16, we discovered that Magnitude EK, whichhad been loyal to its own Magniber ransomware, was now being leveraged to push out GandCrab, too.
Source: malwarebytes.com
…Intel Processors Now Allows Antivirus to Use Built-in GPUs for Malware Scanning

Global chip-maker Intel on Tuesday announced two new technologies—Threat Detection Technology (TDT) and Security Essentials—that not only offer hardware-based built-in security features across Intel processors but also improve threat detection without compromising system performance. Intel’s Threat Detection Technology (TDT) offers a new set of features that leverage hardware-level telemetry to help security products detect new classes of threats and exploits. It includes two main capabilities—Accelerated Memory Scanning and Advanced Platform Telemetry.
…Crypto YouTuber hacked out of $2M during a livestream
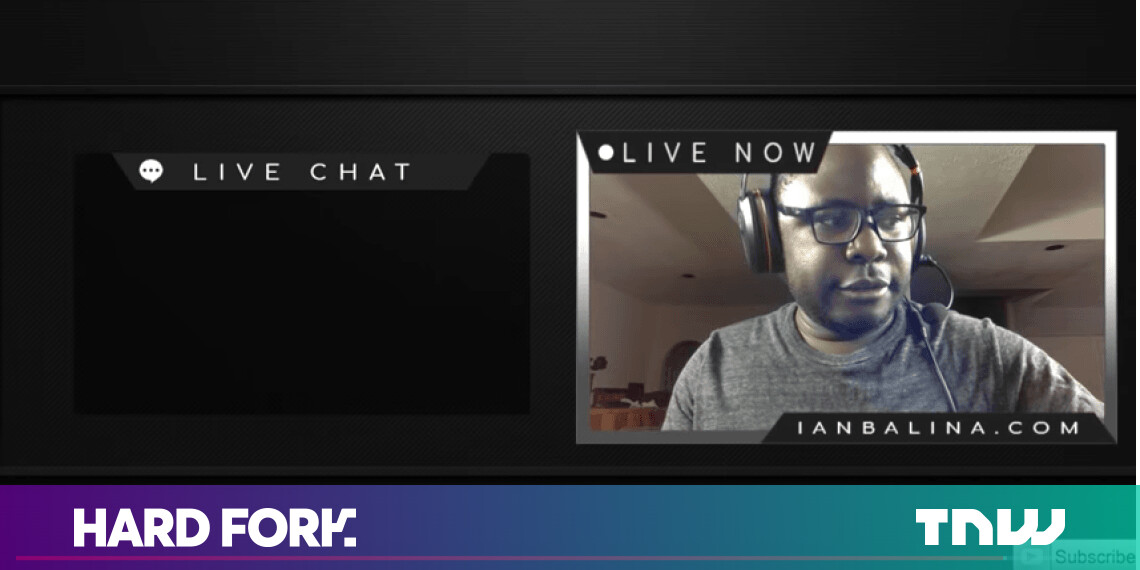
The wallet transactions on Etherscan show that almost all of Balina’s tokens were withdrawn from his account during the livestream. This included more than 20 million Nucleus Vision, 2 million Pareto Network, and 1 million Loom among others.
Source: thenextweb.com
…US Navy Accused of Tech Piracy

The Navy is entangled in two long-running federal court cases involving IP theft. In March, German software company Bitmanagement asked a federal court for a summary judgement after accusing the Navy of illegally installing $600 million in software on more than 500,000 computers.
Source: vice.com
…Facial recognition cameras on lamp posts to be tested in Singapore

Singapore last year announced that it wants to convert every single lamp post in the country – there are about 110,000 in the island state – into an interconnected network of wireless sensors.
Source: sophos.com
…Roaming Mantis uses DNS hijacking to infect Android smartphones

In March 2018, Japanese media reported the hijacking of DNS settings on routers located in Japan, redirecting users to malicious IP addresses. The redirection led to the installation of Trojanized applications named facebook.apk and chrome.apk that contained Android Trojan-Banker. According to our telemetry data, this malware was detected more than 6,000 times, though the reports came from just 150 unique users (from February 9 to April 9, 2018).
…The Bitcoin Standard – a critical review

There is no better evidence for this than the fact that the rarest metal in the crust of the earth, gold, has been mined for thousands of years and continues to be mined in increasing quantities as technology advances over time, as shown in Chapter 3. If annual production of the rarest metal in the earth’s crust goes up every year, then it makes no sense to talk of any natural element as being limited in its quantity in any practical sense.
…IRS Says Fewer Than 100 People Have Reported Bitcoin Holdings So Far

Credit Karma Tax, the tax prep branch of the popular credit score site, said April 13 that fewer than100 of the 250,000 most recent tax filers through the servicehave reported cryptocurrency transactions. One of the biggest questions this tax season has been the impact that last year’s cryptocurrency boom would have on filers across the U.S. In 2017, cryptocurrencies became among the very trendiest investment (or speculation, depending upon your perspective) opportunities.
…WhatsApp photo drug dealer caught by ‘groundbreaking’ work

A pioneering fingerprint technique used to convict a drugs gang from a WhatsApp message ‘is the future’ of how police approach evidence to catch criminals.
Source: bbc.com
…Microsoft Engineer Charged in Reveton Ransomware Case
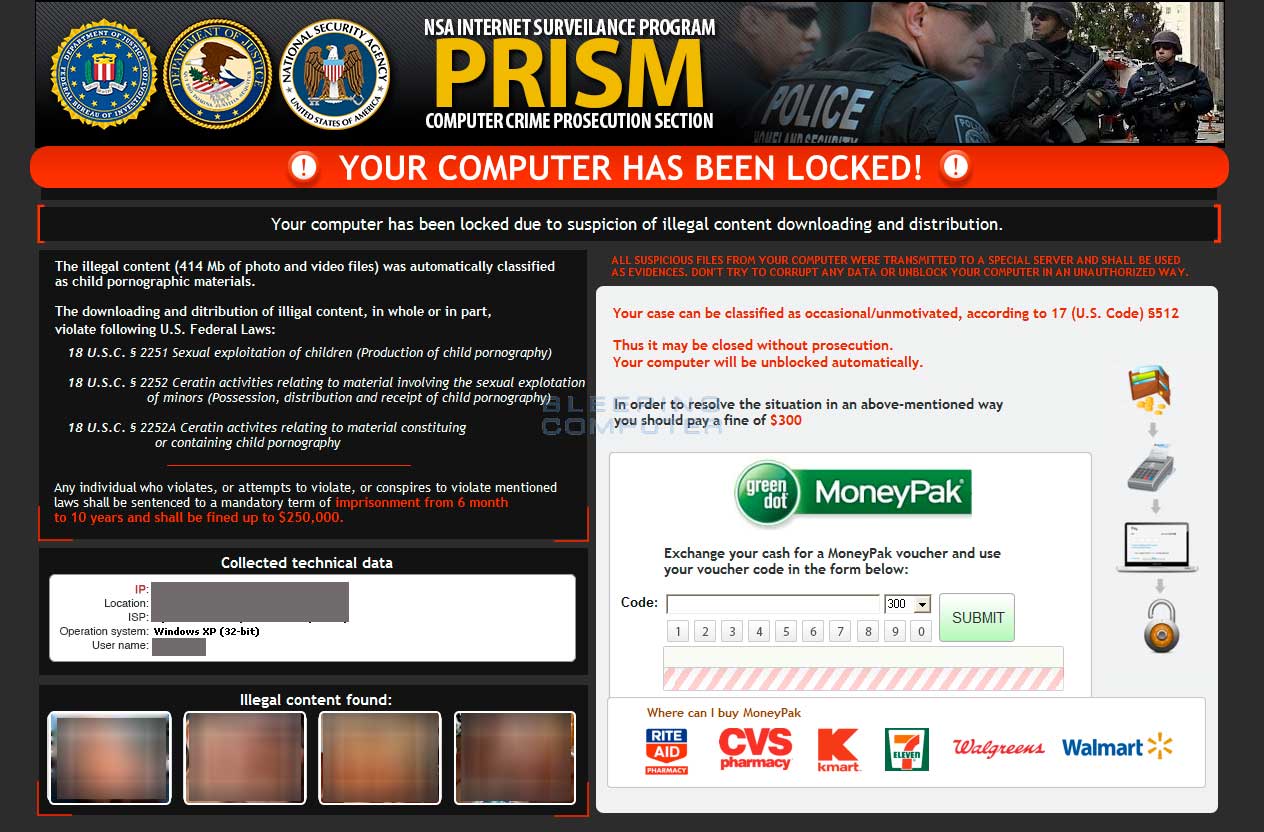
The accused is Raymond Uadiale, 41, a naturalized US citizen of Nigerian descent, who currently works for Microsoft in Seattle since 2014, according to his LinkedIn page.
Source: bleepingcomputer.com
…Understanding Bitcoin Transactions

How hard could it be to send some bitcoin from a JavaScript library? I decided to try on the ‘testnet’. I downloaded Bitcoin Core, configured it for the testnet, waited a few hours for it to sync the testnet blockchain, created an ‘address’, and found a ‘testnet faucet’ to send my new address some testnet bitcoin.
Source: jonathanotto.com
…CVE-2017-0263 – reported exploit used to interfere the French election

CVE-2017-0263 is a UAF vulnerability in Menu Management Component in win32k kernel module of Windows operating system, which was reported to be used to attack with an EPS vulnerability to interfere the French election. This article will simply analyze the CVE-2017-0263 part of the attacking sample in order to come up with the operation principle and basic exploiting idea of this vulnerability, and make a brief investigation into the Menu Management Component of Windows Window Manager Subsystem. The analyzing environment is Windows 7 x86 SP1 basic virtual machine.
…