Cyber security news and services
Systems built on trust, norms, and institutions function better than blockchain

Blockchain is not only crappy technology but a bad vision for the future. Its failure to achieve adoption to date is because systems built on trust, norms, and institutions inherently function better than the type of no-need-for-trusted-parties systems blockchain envisions. That’s permanent: no matter how much blockchain improves it is still headed in the wrong direction.
Source: medium.com
…FUZE — This $2.5 Million ‘Secure’ Bluetooth Credit Card Might Be Leaking Bank Data

Secure, affordable and convenient. That’s how the makers of the FUZE Card describe their creation, designed to act as a whole wallet in a single thin device. It can store up to 30 different credit cards and uses a lock to protect the data within.
Such a hit was it with consumers it raised nearly $2.5 million in Indiegogo funding, with the original cost starting at $160.
…This Tool Can Help Identify Leakers Who Copy and Paste Secret Info

I rarely think that the text I’m copying and pasting has something hidden within it that could reveal my sources. And I probably should worry about that because it’s incredibly easy to hide invisible characters—so-called “zero-width” characters—within text and use those as a watermark or fingerprint of sorts. In some situations, that could reveal to the original author who you are, or the fact that you copy pasted the original text and put it somewhere else.
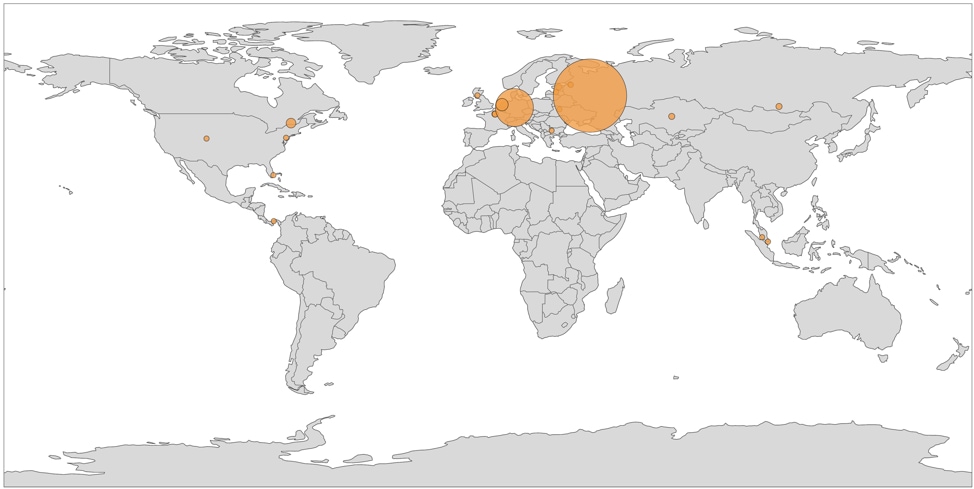
…Cyberinsurance Tries to Tackle the Unpredictable World of Hacks
In 2016, the cyberinsurance market brought in around $3.5 billion in premiums globally, of which $3 billion came from US-based companies, according to the Organisation for Economic Co-operation and Development. That’s not an enormous amount of money compared to other insurance markets; motor vehicle insurance premiums in the US, for instance, total more than $200 billion annually. But cyberinsurance premiums have grown steadily at a rate of roughly 30 percent every year for the past five years, in an industry unaccustomed to such spikes.
…Ethereum’s Compact Merkle Trie

This is the third post in a series on implementing the Ethereum Virtual Machine in Clojure.
Source: nervous.io
…Hacker Uses Exploit to Generate Verge Cryptocurrency out of Thin Air

The Verge development team is preparing a hard-fork of the entire cryptocurrency code to fix the issue and revert the blockchain to a previous state before the attack to neutralize the hacker’s gains.
Source: bleepingcomputer.com
…Sears Holdings, Delta and others leak credit cards in “multibreach”

Last week, on March 28, Delta was notified by [24]7.ai, a company that provides online chat services for Delta and many other companies, that [24]7.ai had been involved in a cyber incident. It is our understanding that the incident occurred at [24]7.ai from Sept. 26 to Oct. 12, 2017, and that during this time certain customer payment information for [24]7.ai clients, including Delta, may have been accessed – but no other customer personal information, such as passport, government ID, security or SkyMiles information was impacted.
…“Open sesame”: Industrial network gear hackable with the right username

This week, two separate security alerts have revealed major holes in devices from Moxa, an industrial automation networking company. In one case, attackers could potentially send commands to a device’s operating system by using them as a username in a login attempt. In another, the private key for a Web server used to manage network devices could be retrieved through an HTTP GET request.
…Malware Attack on Vendor to Blame for Delta and Sears Data Breach Affecting ‘Hundreds of Thousands’ of Customers

The nature of the malware involved has not been disclosed and it remains unclear whether the payment card information, which Delta say was entered by the customers themselves, got intercepted in transit or was improperly stored.
Source: gizmodo.com
…Bitcoin Tracker Chainalysis Raises $16 Million, Plans to Track 10 More Cryptocurrencies

You can think of Chainalysis as a blockchain detective. The New York-based firm is best known for its forensic tools that help law enforcement agencies track the movement of bitcoin, but it also helps financial financial firms keep tabs on who is using digital currencies.
Source: fortune.com
…OSX_OCEANLOTUS.D, a new macOS backdoor linked to APT 32 group

The APT32 group has been active since at least 2013, according to the experts it is astate-sponsored hacking group. The hackers hit organizations across multiple industries and have also targeted foreign governments, dissidents, and journalists.
Source: securityaffairs.co
…Okay, Let’s Talk About John McAfee’s Paid Cryptocurrency Promotions

John McAfee, founder of the security software company, revealed on Friday that he charges $105,000 USD to post a tweet promoting a client’s cryptocurrency to his 813,000 Twitter followers.
Source: vice.com
…Secret Service Warns of Chip Card Scheme

The U.S. Secret Service is warning financial institutions about a new scam involving the temporary theft of chip-based debit cards issued to large corporations. In this scheme, the fraudsters intercept new debit cards in the mail and replace the chips on the cards with chips from old cards. When the unsuspecting business receives and activates the modified card, thieves can start draining funds from the account.
…Smoking Out the Rarog Cryptocurrency Mining Trojan
Rarog has been seen primarily used to mine the Monero cryptocurrency, however, it has the capability to mine others. It comes equipped with a number of features, including providing mining statistics to users, configuring various processor loads for the running miner, the ability to infect USB devices, and the ability to load additional DLLs on the victim.
Source: paloaltonetworks.com
…Why Investors Are Betting Millions On Bitcoin Surveillance

Tracking the myriad cryptocurrencies as they ping around the world en masse every day is no simple task. Ask 27-year-old British entrepreneur Jonathan Levin, co-founder and chief operating officer of Chainalysis, one of the hottest companies in the burgeoning business of digital currency tracking. In its early days, in 2014, Chainalysis would do its best to retroactively monitor transactions and follow the money of nefarious types on the blockchain, largely for the benefit of U.S. government investigators hunting fraudsters and launderers.
…The FBI could have broken into San Bernadino shooter’s phone without Apple

The Department of Justice’s Office of the Inspector General (OIG) last week released a new report that supports what EFF has long suspected: that the FBI’s legal fight with Apple in 2016 to create backdoor access to a San Bernardino shooter’s iPhone was more focused on creating legal precedent than it was on accessing the one specific device.
…India’s central bank bans all cryptocurrency dealings

India virtually banned cryptocurrencies like bitcoin with the Reserve Bank of India barring regulated entities from providing services to any individual or business dealing in digital currencies. The central bank has given three months to regulated entities like banks to unwind their positions with the entities related to cryptocurrencies, RBI Deputy Governor BP Kanungo said in a media conference. The regulator, however, decided that it will promote the use of blockchain – a public ledger that serves as the backbone of bitcoin – in financial services for strengthening transparency and improving inclusion.
…Fixed security exploit in Google’s search engine
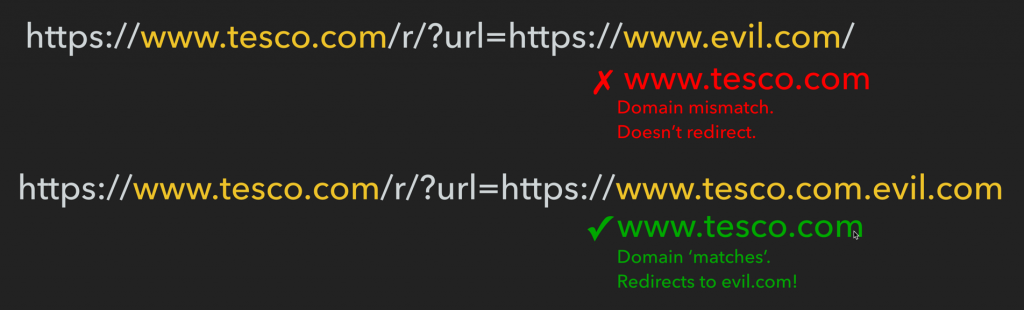
For the $12 cost of a domain, I was able to rank in Google search results with Amazon, Walmart etc. for high value money terms in the US. The Adwords bid price for some these terms is currently around $1 per click, and companies are spendings 10s of thousands of dollars a month to appear as ads on these search results, and I was appearing for free.
…MailChimp’s Ban on Cryptocurrency Marketing Is Causing Collateral Damage

The promise of cryptocurrencies, and blockchain technology in general, is decentralization. Proponents say that if power is spread out to many different people and groups, then no single entity can impose its agenda on the whole network. In practice, however, cryptocurrency communities rely on many centralized tools.
For example, much of the discussion within cryptocurrency communities takes place on Twitter and Reddit. Using popular services like these is good for accessibility, but occasionally relying on an mainstream entity backfires on the cryptocurrency proponents.
…Intel Tells Remote Keyboard Users to Delete App After Critical Bug Found

The Intel Remote Keyboard product is an Android and iOS app that works in conjunction with Intel’s mini-PC platform called Next Unit of Computing (NUC) and with the chipmaker’s Compute Stick. NUCs are similar in size and function to Raspberry Pi systems. Compute Sticks are about the size of a large flash drive and are single-board computers used both in classrooms, kiosks and in some network computer environments.
…