Cyber security news and services
An in-depth malware analysis of QuantLoader

QuantLoader is a Trojan downloader that has been used in campaigns serving a range of malware, including ransomware, Banking Trojans, and RATs. In this post, we’ll take a high-level look at the campaign flow, as well as a deep dive into how the malware executes.
Source: malwarebytes.com
…Your malware reesrch new friend, KLara

While doing threat research, teams need a lot of tools and systems to aid their hunting efforts – from systems storing Passive DNS data and automated malware classification to systems allowing researchers to pattern-match a large volume of data in a relatively short period of time. These tools are extremely useful when working on APT campaigns where research is very agile and spans multiple months. One of the most frequently used tools for hunting new variants of malware is called YARA and was developed by Victor Manuel Alvarez while working for VirusTotal, now part of Alphabet.
…How On Earth Did Russia Hack Our Energy Systems?

The traps themselves are pretty imaginative. Many are based in social media. No one would suspect a cute kitten video of hiding malware.
But they do. And if your co-worker is a kitten-nut, they may not hesitate to download that video without thinking that it is a trap.
Source: forbes.com
…Monero traceability

Monero is a privacy-centric cryptocurrency that allows users to obscure their transactions by includ- ing chaff coins, called “mixins,” along with the actual coins they spend. In this paper, we empirically evalu- ate two weaknesses in Monero’s mixin sampling strat- egy.
Source: arxiv.org
…Fiber Lasers Mean Ray Guns Are Coming
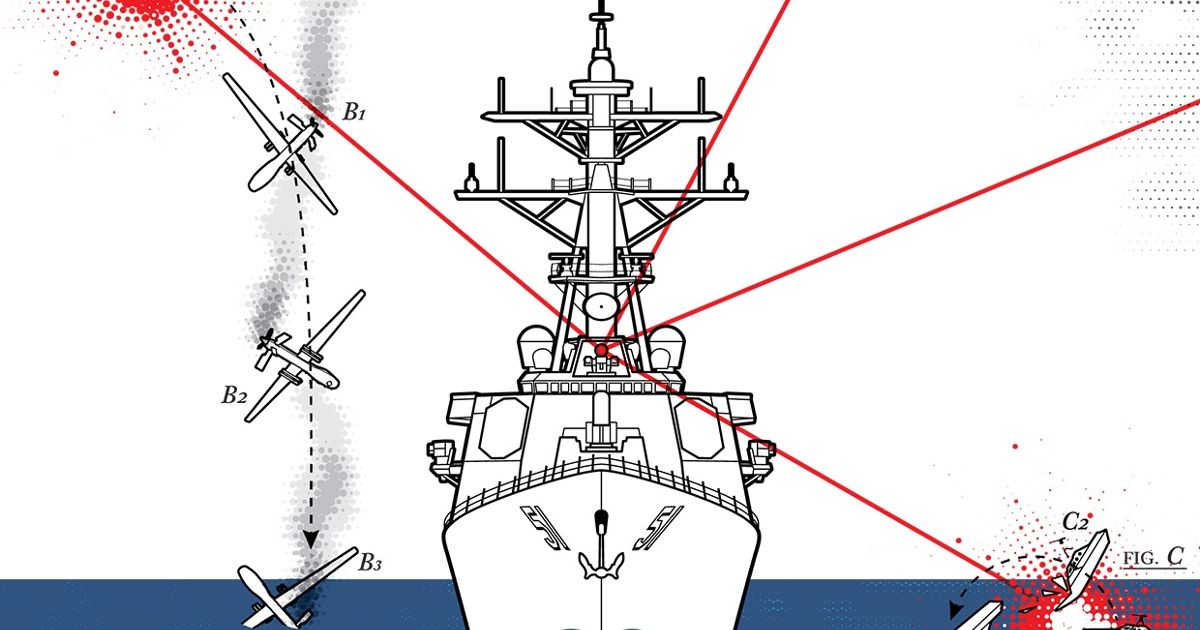
The U.S. Navy’s most advanced laser weapon looks like a pricey amateur telescope. As it emerges from a chassis high on the USS Ponce tolook out onto the daytime sky above the Persian Gulf, its operator sits inadarkened room elsewhere on the ship holding what looks like a game controller. The screen before him is showing a small boat floating near the Ponce, carrying a dark object.
…81% of ICO’s were Scams
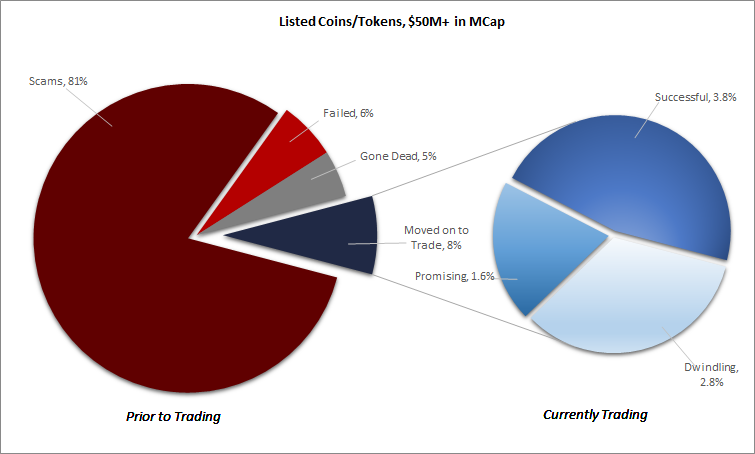
In a recent study, we’ve attempted to classify ICO’s by quality. This encompasses the lifecycle of an ICO, from the original proposal of fundraising availability through to the most mature phase of trading on a cryptocurrency exchange (also known as “online trading platforms”) (“exchange”). This is a high level look above a market cap of $50M only, as an initial attempt to improve on the reporting we have seen to date on percentage failed ICO’s.
…With Musical Cryptography, Composers Can Hide Messages in Their Melodies

Early 17th- and 18th-century mathematicians and cryptologists such as John Wilkins and Philip Thicknesse argued that music cryptography was one of the most inscrutable ways of transporting secret messages. They claimed that music was perfect camouflage, because spies would never suspect music. When played, the music would sound so much like any other composition that musically trained listeners would be easily fooled, too.
…VirusBay Aims To Make Malware Analysis More Social

For those looking to learn about and share malware samples, a site called VirusBay may be what you are looking for. VirusBay’s goal is to make malware analysis more social by providing a place for researchers to upload samples, request samples, and discuss them with other researchers.
Source: bleepingcomputer.com
…The phenomenon of smart contract honeypots

Hardly a week passes without large scale hacks in the crypto world. It’s not just centralised exchanges that are targets of attackers. Successful hacks such as the DAO, Parity1 and Parity2 have shown that vulnerabilities in smart contracts can lead to losing digital assets worth millions of dollars.
Attackers are driven by making profits and with the incredible value appreciation in 2017 in the crypto world, individuals and organisations who hold or manage digital assets are often vulnerable to attacks. Especially smart contracts have become a prime target for attackers for the following reasons:
…Logs in High Sierra Show Plaintext Password for APFS Encrypted External Volumes
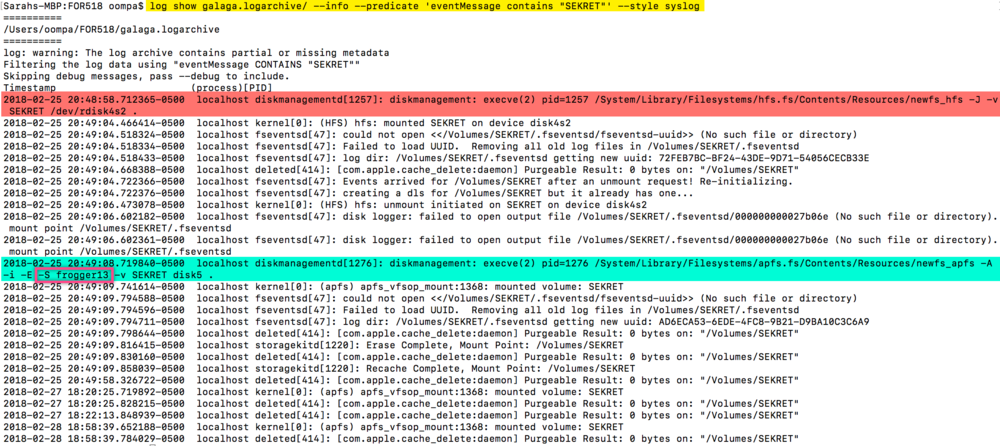
It may not be noticeable at first (apart from the highlighting I’ve added of course), but the text “frogger13” is the password I used on a newly created APFS formatted FileVault Encrypted USB drive with the volume name “SEKRET”. (The new class images have a WarGames theme, hence the shout-outs to classic video games!)
Source: mac4n6.com
…It’s not just Spectre: Researchers reveal more branch prediction attacks

The Spectre attacks, published earlier this year, take advantage of the speculative execution features of modern processors to leak sensitive information. The new attack, named BranchScope by the researchers, shares some similarity with variant 2 of the Spectre attack, as both BranchScope and Spectre 2 take advantage of the behavior of the processor’s branch predictor.
Source: arstechnica.com
…Adding ERC20 Support to Coinbase

We’re excited to announce our intention to support the Ethereum ERC20 technical standard for Coinbase in the coming months. This paves the way for supporting ERC20 assets across Coinbase products in the future, though we aren’t announcing support for any specific assets or features at this time. We are announcing this both internally and to the public as consistent with our process for adding new assets.
…Watch Someone Break Into a Hotel Room Using Just a Paper Menu

In a simple, yet sort of terrifying video, YouTuber and locksmith “MM Developer” demonstrates how easy it is to break into a hotel room door with just a paper restaurant menu—no social engineering or lock-picking skills required.
Source: vice.com
…How a Political Engineering Firm Exposed Their Code Base

Coming amidst a firestorm of scrutiny about how political operations can use and harvest consumer information, including from social media networks like Facebook, the UpGuard Cyber Risk Team can now reveal that a large code repository originating from AggregateIQ, a Canadian political data firm active in the 2016 US presidential race, was left publicly downloadable online. Revealed within this repository is a set of sophisticated applications, data management programs, advertising trackers, and information databases that collectively could be used to target and influence individuals through a variety of methods, including automated phone calls, emails, political websites, volunteer canvassing, and Facebook ads. Also exposed among these tools are numerous credentials, keys, hashes, usernames, and passwords to access other AIQ assets, including databases, social media accounts, and Amazon Web Services repositories, raising the possibility of attacks by any malicious actors encountering the exposure.
…New Spyware Company ‘Grey Heron’ Is Linked to Hacking Team

Grey Heron was formed from other players in the government hacking space, including Hacking Team, a source familiar with the company said. In private conversations within the surveillance industry that were later detailed to Motherboard, Grey Heron has suggested it sees distancing itself from Hacking Team and its history as a benefit.
Source: vice.com
…Europol tracks down suspected leader of Carbanak malware campaigns

According to Europol, the cybercriminals have been active since 2013, striking banks in over 40 countries in order to steal at least €1 billion, estimated at roughly €10 million per successful heist.
Source: zdnet.com
…Who and What Is Coinhive?

Multiple security firms recently identified cryptocurrency mining service Coinhive as the top malicious threat to Web users, thanks to the tendency for Coinhive’s computer code to be used on hacked Web sites to steal the processing power of its visitors’ devices. This post looks at how Coinhive vaulted to the top of the threat list less than a year after its debut, and explores clues about the possible identities of the individuals behind the service.
…Is The Future Of Blockchains DAGs ?— 5 Lessons From The Hashgraph Event In NYC on March 13th
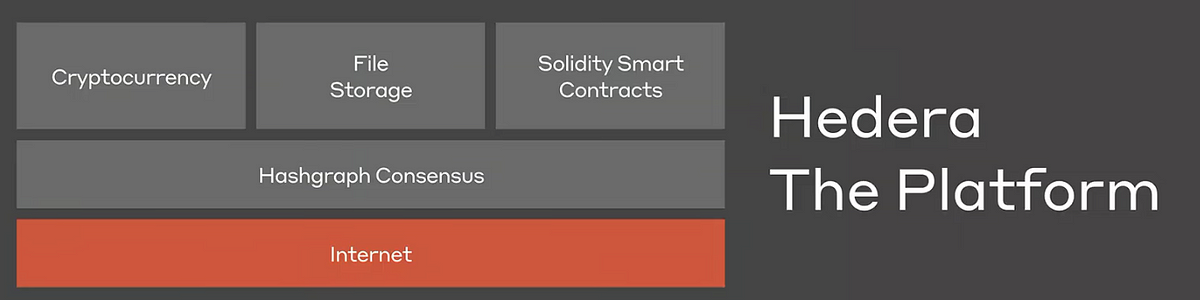
Two weeks ago, with more than 1,000 other Crypto enthusiasts, I had the pleasure of attending the NYC launch event for Hadera Hashgraph, a new public blockchain promising vastly faster throughput.
Source: medium.com
…Code your own Proof of Stake blockchain in Go
There are many thought leaders trying to find alternatives to Proof of Work. The most promising one so far is Proof of Stake. There are already production-ready blockchains based on Proof of Stake like Nxt and Neo.
Ethereum is probably moving to Proof of Stake—their Casper project is already live on their test net.
Source: medium.com
…IRS reminds taxpayers to report virtual currency transactions

Virtual currency transactions are taxable by law just like transactions in any other property. The IRS has issued guidance in IRS Notice 2014-21for use by taxpayers and their return preparers that addresses transactions in virtual currency, also known as digital currency.
Source: irs.gov
…