Cyber security news and services
Exploits in C/C++ to compiled JavaScript / WebAssembly

The Meltdown and Spectre vulnerabilities in modern CPUs from Intel/AMD/ARM revealed surprising attack vectors in computing. Everything from low level Operating System Kernel components to JavaScript running in Billions of browsers could be exploited by using Spectre variants 1 and 2.
Source: react-etc.net
…Researchers Say AMD Processors Have Serious Vulnerabilities and Backdoors

Security researchers warned Tuesday that some AMD processors contain ‘critical’ vulnerabilities, as well as backdoors that the researchers claimed were put in place in systems outsourced to a third-party manufacturer by AMD. The 13 different vulnerabilities were found in AMD Secure Processor, which is used in the company’s EPYC and Ryzen CPUs. These bugs would allow hackers who have already gained a foothold into a computer to install persistent and hard-to-detect malware, researchers warned.
…CredSSP Flaw in Remote Desktop Protocol Affects All Versions of Windows

A critical vulnerability has been discovered in Credential Security Support Provider protocol (CredSSP) that affects all versions of Windows to date and could allow remote attackers to exploit RDP and WinRM to steal data and run malicious code. CredSSP protocol has been designed to be used by RDP (Remote Desktop Protocol) and Windows Remote Management (WinRM) that takes care of securely forwarding credentials encrypted from the Windows client to the target servers for remote authentication. Discovered by researchers at Cybersecurity firm Preempt Security, the issue (CVE-2018-0886) is a logical cryptographic flaw in CredSSP that can be exploited by a man-in-the-middle attacker with Wi-Fi or physical access to the network to steal session authentication data and perform a Remote Procedure Call attack.
…Let’s Encrypt wildcard support launched today

We’re pleased to announce that ACMEv2 and wildcard certificate support is live! With today’s new features we’re continuing to break down barriers for HTTPS adoption across the Web by making it even easier for every website to get and manage certificates. ACMEv2 is an updated version of our ACME protocol which has gone through the IETF standards process, taking into account feedback from industry experts.
…The International Monetary Fund Has a Dystopian Vision for the Blockchain

The International Monetary Fund is an ideological enemy to Bitcoin and decentralized virtual currencies in general. The Washington, DC-based organization centrally controls a global system of payments and loans, often given to struggling nations on the condition that they impose strict austerity. Now, the IMF wants to use the same technology behind Bitcoin to regulate it.
Source: vice.com
…Reversing a Self-Modifying Binary with radare2
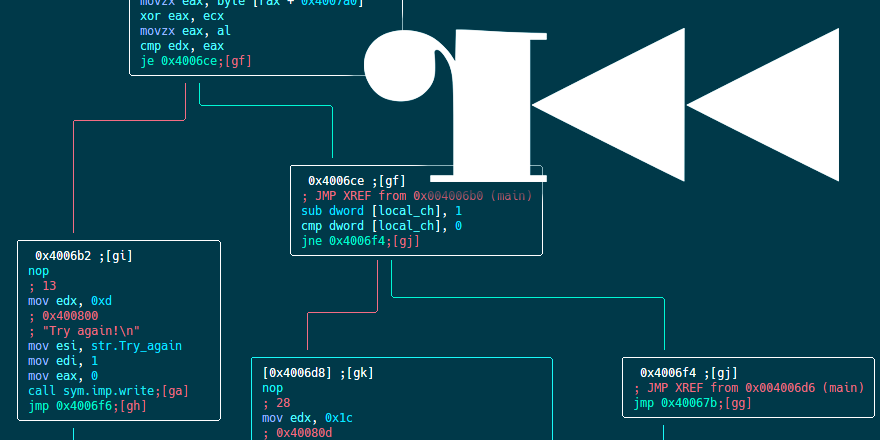
It took me three months to finish writing this article. I had so many tasks on my to-do list that sadly this one was pushed down to the bottom of the list. Last weekend I made a promise to myself that until Sunday I’m going to finish writing it, I successfully kept my word and here it is, another radare2 tutorial.
Source: megabeets.net
…Security Researchers Publish Ryzen Flaws, Gave AMD 24 Hours Prior Notice

Through the advent of Meltdown and Spectre, there is a heightened element of nervousness around potential security flaws in modern high-performance processors, especially those that deal with the core and critical components of company business and international infrastructure. Today, CTS-Labs, a security company based in Israel, has published a whitepaper identifying four classes of potential vulnerabilities of the Ryzen, EPYC, Ryzen Pro, and Ryzen Mobile processor lines. AMD is in the process of responding to the claims, but was only given 24 hours of notice rather than the typical 90 days for standard vulnerability disclosure.
…China-Linked APT15 Used Myriad of New Tools To Hack UK Government Contractor

According to researchers, theAPT15 group was able to deploy three backdoors – identified as RoyalCli, RoyalDNS andBS2005 – on an unnamed UK contractor’s systems. These backdoors helped the threat actor collect data related to the UK government’s military technology. The networks were compromised from May 2016 until late 2017 and infected over 30 contractor controlled hosts,said the NCC Group, whichfirst revealed its report on the attack at Kaspersky Lab’s Security Analyst Summit last week.
…Hancitor: fileless attack with a kernel trick

The interesting aspect about social engineering is that it capitalizes on the user’s poor decision to execute code that would have been much harder to inject, or that could have been caught by security solutions otherwise. In other words, letting victims do the work remains an effective means for attackers to compromise endpoints.
Source: malwarebytes.com
…Time of death? A therapeutic postmortem of connected medicine

To find a potential entry point into medical infrastructure, we extract the IP ranges of all organizations that have the keywords “medic”, “clinic”, “hospit”, “surgery” and “healthcare” in the organization’s name, then we start the masscan (port scanner) and parse the specialized search engines (like Shodan and Censys) for publicly available resources of these organizations.
Source: securelist.com
…ACLU is Suing the Government for Info About TSA Device Searches

Flying sucks enough as it is, but a Transportation Security Administration employee deciding to root around in your laptop or cellphone can make it even worse. This practice of searching electronic devices has been going on for years at international airports, but this was limited to travelers flying in and out of the US. Recently there has a large uptick in the number of devices searched by Customs and Border Protection agents: Last year, CBP officials searched 30,000 devices, up from just 5,000 in 2015.
…NSA Retreats From Targeted PCs If They’re Already Infected by Other APT Malware

This utility, going by the codename of ‘Territorial Dispute,’ is meant to alert NSA operators about the presence of other cyber-espionage hacking groups on a compromised computer and allows an NSA operator to retreat from an infected machine and avoid further exposure of NSA hacking tools and operations to other nation-state attackers.
Source: bleepingcomputer.com
…Scanning the Alexa Top 1M for .DS_Store files

Some readers may remember our Analysis of .git folders in the Alexa Top 1M. WIth our tools we were able to discover and retrieve (hidden) directories and files (even without directory listing). We developed a similar approach of uncovering hidden files again, but this time with the help of .DS_Store files. In this blogpost we will share the methodology, the resulting security implications as well as our results from scanning the Alexa Top 1M and how we could have obtained sensitive files from several websites.
…JavaScript Zero: real JavaScript, and zero side-channel attacks

Microarchitectural attacks can also be implemented in JavaScript, exploiting properties inherent to the design of the microarchitecture, such as timing differences in memory accesses. Although JavaScript code runs in a sandbox, Oren et al. demonstrated that it is possible to mount cache attacks in JavaScript. Since their work, a series of microarchitectural attacks have been mounted from websites, such as page deduplication attacks, Rowhammer attacks, ASLR bypasses, and DRAM addressing attacks.
…Here’s How Litecoin overtakes Bitcoin, and Amazon is the Key

Amazon as a Tech company and everything store, is perhaps the only thing Millennials trust more than investing in cryptocurrencies. We’ve now reached a point where Big Tech will race to adopt them and it could change the future of banking and payments.
Source: medium.com
…German Income Tax on Virtual Currencies

Last week, the Frankfurt School of Finance & Management hosted CryptoTax for a seminar on the German taxation regime. The webinar recording is available on YouTube (in German only), and the key points have been summarized here for the benefit of a global audience.
Source: medium.com
…There’s a currency miner in the Mac App Store, and Apple seems OK with it
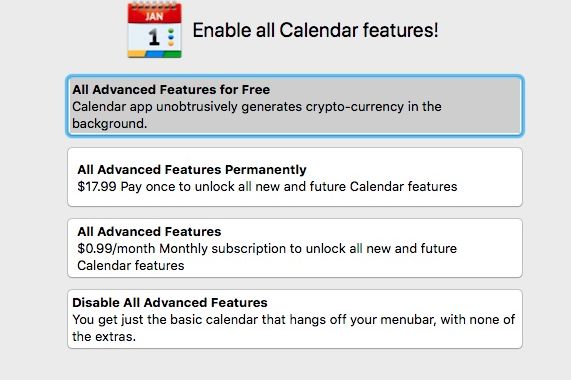
Resource-draining currency miners are a regular part of the Google Play market, as scammers pump out apps that covertly harness millions of devices, in some cases with malware so aggressive it can physically damage phones. A popular title in the Mac App Store recently embraced coin mining openly, and so far Apple gatekeepers haven’t blocked it.
…Regaxor: Fuzzing Regexes for Fun and Not‐So‐Much Profit

It all started with the public disclosure of a HackerOne report submitted to Keybase by another researcher. It was a minor character escaping issue, but one that probably had the highest impact of all vulnerability reports submitted to their program—given that it was issued their highest bounty payout at the time. I immediately noticed the ‘patch’ they implemented was insufficient, and it was only a matter of minutes before I submitted a new vulnerability report (as quickly and as fast as possible).
…Air gapping PCs won’t stop data sharing thanks to sneaky speakers
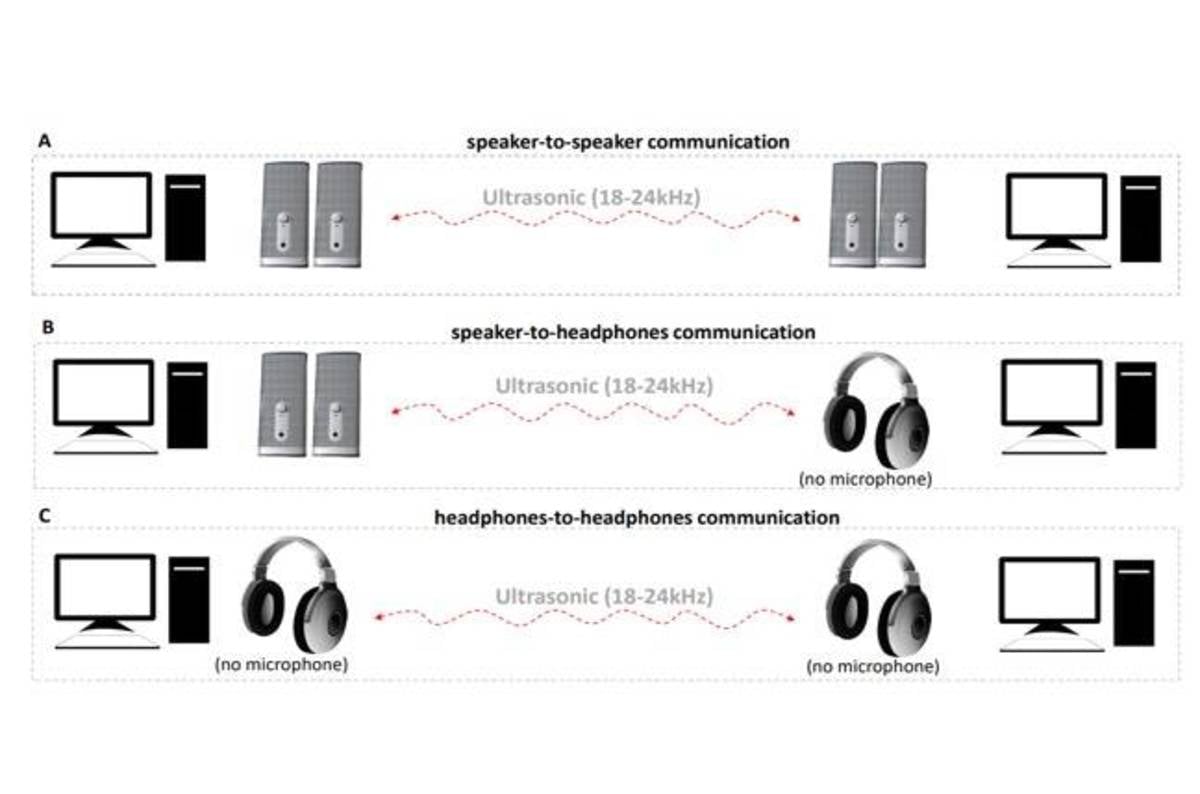
In an academic paper published on Friday through preprint service ArXiv, researchers from Israel’s Ben-Gurion University of the Negev describe a novel data exfiltration technique that allows the transmission and reception of data – in the form of inaudible ultrasonic sound waves – between two computers in the same room without microphones.
Source: co.uk
…Questions for TSA after reports of laptop and phone searches on domestic flights

There are a growing number of reports of the Transportation Security Administration (TSA) searching the electronic devices of passengers on domestic flights in the US, according to the American Civil Liberties Union (ACLU), which has sued the federal agency for records. The ACLU Foundation of Northern California filed a lawsuit against the TSA on Monday demanding that the government disclose its policies for searching the computers and cellphones of domestic travelers, arguing that anecdotal accounts have raised concerns about potential privacy invasions.
…