Cyber security news and services
MOSQUITO Attack Allows Air-Gapped Computers to Covertly Exchange Data
The team of security researchers—who last month demonstrated how attackers could steal data from air-gapped computers protected inside a Faraday cage—are back with its new research showing how two (or more) air-gapped PCs placed in the same room can covertly exchange data via ultrasonic waves. Air-gapped computers are believed to be the most secure setup wherein the systems remain isolated from the Internet and local networks, requiring physical access to access data via a USB flash drive or other removable media. Dubbed MOSQUITO, the new technique, discovered by a team of researchers at Israel’s Ben Gurion University, works by reversing connected speakers (passive speakers, headphones, or earphones) into microphones by exploiting a specific audio chip feature.
…Data breach victims can sue Yahoo in the United States: judge
Yahoo has been ordered by a federal judge to face much of a lawsuit in the United States claiming that the personal information of all 3 billion users was compromised in a series of data breaches.
Source: reuters.com
…China ALTERED its public vuln database to conceal spy agency tinkering – research

In November 2017, Recorded Future published research examining the publication speed for China’s National Vulnerability Database (CNNVD). While conducting that research, we discovered that China had a process for evaluating whether high-threat vulnerabilities had operational utility in intelligence operations before publishing them to the CNNVD. In revisiting that analysis, we discovered that CNNVD had altered their initial vulnerability publication dates in what we assess is an attempt to cover up that evaluation process.
…‘Snitches Get Stitches:’ How Secure Phones for Criminals Are Sold on Instagram

On Saturday, Motherboard reported that the FBI has arrested the CEO of Phantom Secure, a company allegedly providing security-focused phones to international organized crime groups including the Sinaloa drug cartel. A key issue is whether Phantom deliberately created its product to help facilitate crime, which the criminal complaint alleges.
Source: vice.com
…Hacked Retail Robots Can Assault Customers With Porn and Demand Bitcoin
In their March 9 paper, “Robots want bitcoins too,” IOActive security researches Lucas Apa and Cesar Cerrudo successfully created ransomware that could be used to compromise SoftBank Robotics’ NAO robot. Unlike traditional computer ransomware which threatens customers by encrypting their personal information, in the situation presented by the researches, companies that rely on these robots for service would be forced to make a decision: pay the ransom or cease business.
…20% of all Node.js modules found vunerable to injection attacks

If you’re using JavaScript on the server side (node.js), then you’ll want to understand the class of vulnerabilities described in this paper. JavaScript on the server side doesn’t enjoy some of the same protections as JavaScript running in a browser. In particular, Node.js modules can interact freely with the operating system without the benefit of a security sandbox.
The bottom line is this:
…The South America connection and the leadership on ATM Malware development

Around the globe, the region where criminals had achieved expertise and have become highly professionals is Latin America. As a resulting of this criminal union to steal money directly from ATM, criminals and cybercriminals from Latin America have been developing brand new zero-day techniques and tools that are not found in any other place in the world.
Source: securityaffairs.co
…As the Ice Melts, Nuclear Submarines Train for Arctic War

The US Navy submarines USS Connecticut and USS Hartford are meeting the British Royal Navy sub HMS Trenchant under an ice floe on the Arctic Sea. The subs, each with a crew of more than 100 sailors, combined are bringing along scores of researchers from government agencies and universities.
Source: vice.com
…Somebody’s watching! When cameras are more than just ‘smart’

The researchers at Kaspersky Lab ICS CERT decided to check the popular smart camera to see how well protected it is against cyber abuses. This model has a rich feature list, compares favorably to regular webcams and can be used as a baby monitor, a component in a home security system or as part of a monitoring system.
Source: securelist.com
…DJI Spark hijacking

DJI drones have been on the radar of the hacker community for quite a long time. The interest of its members revolves mostly around unblocking some features of drones, setting control channels of drones to a higher frequency, and removing such restrictions as flight altitude limits or strictly set no-fly zones. Moreover, there are piles of publicly available info about jailbreaking drones.
The most useful know-hows produced by the community are gathered in several Github cross-referenced repositories. Those striving for knowledge may also check the community wiki dji.retroroms.info. For quite a while the website has been accessible as a web archive only, but now the wiki is available again.
…Fuzzing arbitrary functions in ELF binaries

I decided to give a descent test to the LIEF project. Executable parsers are not a new thing but that one picked my curiosity (just like most Quarkslab projects) because it also provides dead simple instrumentation functions. To top it up, LIEF is easy to use and well documented, which is becoming a rare perk in the circus of infosec tools.
Source: github.io
…China eyes ‘black tech’ to boost security as parliament meets
At a highway check point on the outskirts of Beijing, local police are this week testing out a new security tool: smart glasses that can pick up facial features and car registration plates, and match them in real-time with a database of suspects.
Source: reuters.com
…The military keeps encountering UFOs. Why doesn’t the Pentagon care?

In December, the Defense Departmentdeclassified twovideos documenting encounters between U.S. Navy F-18 fighters and unidentified aircraft. The first video captures multiple pilots observing and discussing a strange, hovering, egg-shaped craft, apparently one of a “fleet” of such objects, according to cockpit audio. The second shows a similar incident involving an F-18 attached to the USS Nimitz carrier battle group in 2004.
…Governments rely on Sandvine network gear to deliver spyware and miners

Researchers athuman rights research groupCitizen Lab have discovered that netizens in Turkey, Egypt and Syria who attempted to download legitimate Windows applications from official vendor websites (i.e. Avast Antivirus, CCleaner, Opera, and 7-Zip) have been infected with a nation-state malware.
Source: securityaffairs.co
…Master password in Firefox or Thunderbird? Do not bother

There is a weakness common to any software letting you protect a piece of data with a password: how does that password translate into an encryption key? If that conversion is a fast one, then you better don’t expect the encryption to hold. Somebody who gets hold of that encrypted data will try to guess the password you used to protect it.
…Senate Bill Meant To Punish Equifax Might Actually Reward It

The Equifax data breach affected around 148 million Americans. As the Washington Post reported, the affected people’s compromised information includes even partial driver’s license data. According to Bloomberg, this has made Equifax somewhat of a pariah in Washington.
Ironically, however, the Senate bill designed to punish the consumer credit reporting agency might actually reward it. A last-minute change, an amendment to the bill offered by its author Senate Banking Committee Chairman Mike Crapo, might help Equifax make millions of dollars in revenue.
…The SEC Kills Crypto Exchanges
It was only a matter a of time. There were clearly signs this was going to happen already out there when the SEC went after defunct “exchange” BitFunder. Today, the SEC made its biggest announcement yet: all the crypto exchanges are illegal unless they register with the SEC.
Why is this important? It turns out the entire $400B cryptocurrency ecosystem is based on trading altcoins or utility tokens.
…SgxSpectre Attack Can Extract Data from Intel SGX Enclaves

A new variation of the Spectre attack has been revealed this week by six scientists from the Ohio State University. Named SgxSpectre, researchers say this attack can extract information from Intel SGX enclaves. Intel Software Guard eXtensions (SGX) is a feature of modern Intel processors that allow an application to create so-called enclaves.
This enclave is a hardware-isolated section of the CPU’s processing memory where applications can run operations that deal with extremely sensitive details, such as encryption keys, passwords, user data, and more.
…Potent malware that hid for six years spread through routers
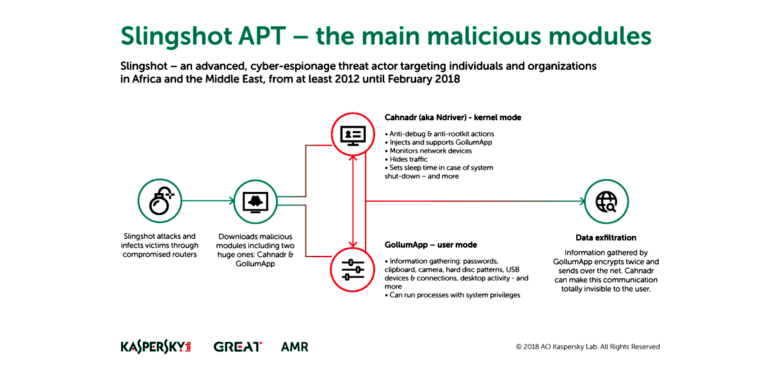
Slingshot—which gets its name from text found inside some of the recovered malware samples—is among the most advanced attack platforms ever discovered, which means it was likely developed on behalf of a well-resourced country, researchers with Moscow-based Kaspersky Lab reported Friday. The sophistication of the malware rivals that of Regin—the advanced backdoor that infected Belgian telecom Belgacom and other high-profile targets for years—and Project Sauron, a separate piece of malware suspected of being developed by a nation-state that also remained hidden for years.
…Hackers, Not Users, Lose Money in Attempted Cryptocurrency Exchange Heist

Binance, one of the largest cryptocurrency exchanges on the Internet, said today that hackers and a well-executed phishing campaign are to blame for the Bitcoin sell-offs from yesterday’s afternoon.
Source: bleepingcomputer.com
…