Mar. 26, 2018

Multiple security firms recently identified cryptocurrency mining service Coinhive as the top malicious threat to Web users, thanks to the tendency for Coinhive’s computer code to be used on hacked Web sites to steal the processing power of its visitors’ devices. This post looks at how Coinhive vaulted to the top of the threat list less than a year after its debut, and explores clues about the possible identities of the individuals behind the service.
Mar. 26, 2018

Trend Micro uncovered a new crypto mining campaign targeting Linux servers that exploit the CVE-2013-2618 flaw in Cacti’s Network Weathermap plug-in, which system administrators use to visualize network activity.
Source: securityaffairs.co
Mar. 25, 2018

This post describes a recent attack Minerva’s research team dissected, dubbed GhostMiner, after our solution prevented this infection at a customer site. It provides an example of how malicious miners are evolving to use advanced fileless techniques to succeed in mining Monero and spreading silently on a global scale. In this attack, we also witnessed how competing miners are fighting each other to generate more income for themselves, removing other miners on the endpoint.
Mar. 16, 2018

Mining is the extremely energy-intensive computational process that secures the Bitcoin blockchain and rewards miners with bitcoins. The Bitcoin moratorium was proposed by Plattsburgh Mayor Colin Read earlier this month after local residents began reporting wildly inflated electricity bills in January. The moratorium affects only new commercial Bitcoin operations and will not affect companies that are already mining in the city.
Mar. 14, 2018

One of the biggest campaign operators using Coinhive—an in-browser cryptocurrency mining service—made a measly $7.69 USD after running Coinhive’s script on 11,000 websites for three months, according to a new report published to arXiv last week.
Source: vice.com
Mar. 13, 2018
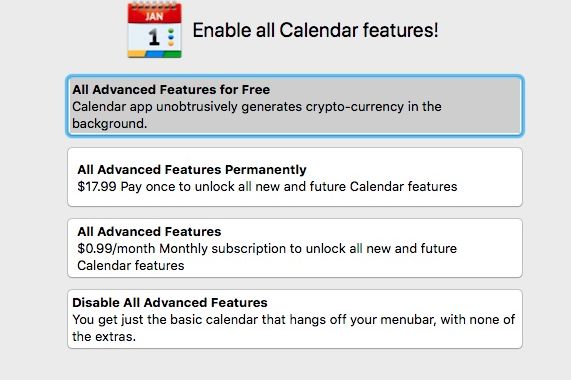
Resource-draining currency miners are a regular part of the Google Play market, as scammers pump out apps that covertly harness millions of devices, in some cases with malware so aggressive it can physically damage phones. A popular title in the Mac App Store recently embraced coin mining openly, and so far Apple gatekeepers haven’t blocked it.
Mar. 8, 2018

Two days ago, Microsoft encountered a rapidly spreading cryptocurrency-mining malware that infected almost 500,000 computers within just 12 hours and successfully blocked it to a large extent. Dubbed Dofoil, aka Smoke Loader, the malware was found dropping a cryptocurrency miner program as payload on infected Windows computers that mines Electroneum coins, yet another cryptocurrency, for attackers using victims’ CPUs.
Mar. 3, 2018

Researchers have discovered an advertising network which has figured out a way to bypass ad blocking software in order to serve website visitors with cryptojacking scripts.
Source: zdnet.com
Mar. 2, 2018

Attackers have generated $3,900 so far in an ongoing campaign that’s exploiting the popular rTorrent application to install currency-mining software on computers running Unix-like operating systems, researchers said Thursday.
Source: arstechnica.com








