Apr. 26, 2018

The broad definition of a BGP leak would be IP space that is announced by somebody not allowed by the owner of the space. When a transit provider picks up Cloudflare’s announcement of 1.1.1.0/24 and announces it to the Internet, we allow them to do so. They are also verifying using the RIR information that only Cloudflare can announce it to them.
Source: cloudflare.com
Apr. 25, 2018

Last week, an unknown party quietly leaked portions of GrayKey code onto the internet, and demanded over $15,000 from Grayshift—ironically, the price of an entry-level GrayKey—in order to stop publishing the material. The code itself does not appear to be particularly sensitive, but Grayshift confirmed to Motherboard the brief data leak that led to the extortion attempt.
Source: vice.com
Apr. 24, 2018
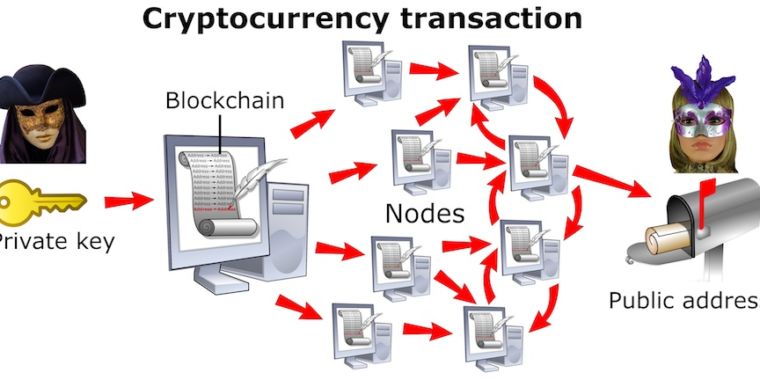
On Monday, Guri published a new paper that applies the same exfiltration techniques to ‘cold wallets,’ which are not stored on devices connected to the Internet. The most effective techniques take only seconds to siphon a 256-bit Bitcoin key from a wallet running on an infected computer, even though the computer isn’t connected to any network. Guri said the possibility of stealing keys that protect millions or billions of dollars is likely to take the covert exfiltration techniques out of the nation-state hacking realm they currently inhabit and possibly bring them into the mainstream.
Apr. 24, 2018
![The “unpatchable” exploit that makes every current Nintendo Switch hackable [Updated]](https://cdn.arstechnica.net/wp-content/uploads/2018/04/switchhax-760x380.jpg)
A newly published ‘exploit chain’ for Nvidia Tegra X1-based systems seems to describe an apparently unpatchable method for running arbitrary code on all currently available Nintendo Switch consoles. Hardware hacker Katherine Temkin and the hacking team at ReSwitched released an extensive outline of what they’re calling the Fusée Gelée coldboot vulnerability earlier today, alongside a proof-of-concept payload that can be used on the Switch.
Apr. 23, 2018

On Tuesday, Department of Justice (DOJ) prosecutors asked a San Francisco federal court judge to impose that sentence on Karim Baratov, a Canadian citizen born in Kazakhstan who was indicted in March 2017 for working with two officers of the Russian Federal Security Service (FSB) -that’s Russia’s successor to the KGB – to pull off the historic Yahoo breach.
Source: sophos.com
Apr. 22, 2018

Gamble was arrested in February of 2016 and he pleaded guilty to ten hacking charges in October of last year. Now 18 years old, he was finally sentenced on Friday afternoon local time in the Old Bailey, the central criminal court in London after his first sentencing hearing in January was postponed. The judge ruled that he will have to spend two years at a youth detention center, according to reports from the court.
Apr. 22, 2018
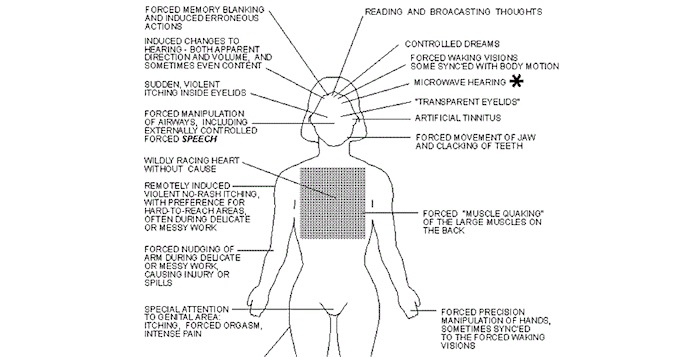
The federal government has absolutely experimented with mind control in a variety of methods, but the documents here do not appear to be official. Waltman had no idea why these documents were included in his request and isn’t sure why the government is holding them. The WSFC did not respond to requests for more information.
Source: boingboing.net
Apr. 19, 2018

Former Apple security engineer Braden Thomas, who now works for a company called Grayshift, warned customers who had bought his GrayKey iPhone unlocking tool that iOS 11.3 would make it a bit harder for cops to get evidence and data out of seized iPhones. A change in the beta didn’t break GrayKey, but would require cops to use GrayKey on phones within a week of them being last unlocked.
Apr. 19, 2018
Hackers initially got onto Piriform’s London networks by using stolen credentials to log into a TeamViewer remote desktop account on a developer PC. From there, the attackers moved laterally to a second computer, always working outside office hours when it was unlikely that people would be using the machines. The attackers installed malware called ShadowPad, sort of customizable malware platform that can be used for an assortment of attacks from DDoS to keylogging, on the compromised computers.
Apr. 17, 2018
The wallet transactions on Etherscan show that almost all of Balina’s tokens were withdrawn from his account during the livestream. This included more than 20 million Nucleus Vision, 2 million Pareto Network, and 1 million Loom among others.
Source: thenextweb.com
Apr. 15, 2018

CVE-2017-0263 is a UAF vulnerability in Menu Management Component in win32k kernel module of Windows operating system, which was reported to be used to attack with an EPS vulnerability to interfere the French election. This article will simply analyze the CVE-2017-0263 part of the attacking sample in order to come up with the operation principle and basic exploiting idea of this vulnerability, and make a brief investigation into the Menu Management Component of Windows Window Manager Subsystem. The analyzing environment is Windows 7 x86 SP1 basic virtual machine.
Apr. 13, 2018

A Motherboard investigation has found that law enforcement agencies across the country have purchased GrayKey, a relatively cheap tool for bypassing the encryption on iPhones, while the FBI pushes again for encryption backdoors.
Source: vice.com
Apr. 10, 2018

Hackers equipped with just a laptop and a $30 handheld FM radio could have hijacked the emergency alert system sirens of San Francisco. The hack could have made them go off whenever they wanted, and made the system broadcast custom messages, according to researchers.
Source: vice.com
Apr. 7, 2018

Learn how to exploit Bluetooth Low Energy for IoT Devices using a step-by-step guide. In this post, we are using Gattacker to perform sniffing and replay based attacks.
Source: attify.com
Mar. 29, 2018

The traps themselves are pretty imaginative. Many are based in social media. No one would suspect a cute kitten video of hiding malware.
But they do. And if your co-worker is a kitten-nut, they may not hesitate to download that video without thinking that it is a trap.
Source: forbes.com
Mar. 26, 2018

Grey Heron was formed from other players in the government hacking space, including Hacking Team, a source familiar with the company said. In private conversations within the surveillance industry that were later detailed to Motherboard, Grey Heron has suggested it sees distancing itself from Hacking Team and its history as a benefit.
Source: vice.com
Mar. 25, 2018

As the FBI pushes once again for backdoors in consumer encryption products, the State Department is apparently taking advantage of a $50 per iPhone unlocking product from Grayshift, a company with an ex-Apple engineer on its staff.
Source: vice.com
Mar. 20, 2018

Security firm Malwarebytes also obtained information on the device and wrote-up a technical post on the technology. Once the box has determined the password, it displays the code on the iPhone screen. Four-digit passcodes can take minutes to a few hours, but six-digit passcodes — now the default on iPhones — can take three days or longer to crack.
But that’s still a significantly shorter amount of time than other known phone-cracking techniques.
Mar. 18, 2018

It’s a worrying development in the direction of isolationism and away from the benefits of competition in the spirit of improving security for all. It comes at a time when relations between the US and China strain under the weight of Huawei security concerns, which are not at all new, but are certainly coming to a head as American companies sever business ties with the firm.
Mar. 16, 2018

The suspected Chinese cyber-espionage group dubbed TEMP.Periscope appeared to be seeking information that would benefit the Chinese government, said FireEye, a U.S.-based provider network protection systems. The hackers have focused on U.S. maritime entities that were either linked to — or have clients operating in — the South China Sea, said Fred Plan, senior analyst at FireEye in Los Angeles.



![The “unpatchable” exploit that makes every current Nintendo Switch hackable [Updated]](https://cdn.arstechnica.net/wp-content/uploads/2018/04/switchhax-760x380.jpg)















