Jun. 15, 2018

Seventeen malicious Docker containers earned cryptomining criminals $90,000 in 30 days in what could be a harbinger of things to come. The figure may seem tame compared to some of the larger paydays that cryptojackers have earned. But, researchers at Kromtech Security Center warn containers are shaping up to be the next ripe target for these types of criminals.
Kromtech said the malicious Docker images (17 in total) were pulled down from the Docker Hub image repository. Researchers can’t say for sure how many times the rogue containers were used by Docker Hub users, but Kromtech estimates that the 17 images were downloaded collectively 5 million times during the year they were available. All 17 were removed from Docker Hub on May 10 by Docker, afterFortinetfound the containers and published a report on the images being used to mine cryptocurrency.
May. 4, 2018

Once the malware has been installed, it sets about mining for Monero and hooking up with a crypto-wallet and mining pool; it also connects with its C2 server for updates, and configures itself to infect other machines on the network. Meanwhile, a short VisualBasic script is used to deploy the malware to compromised Apache Struts servers, and it moves laterally by replicating itself like a worm. MassScan meanwhile passes a list of both private and public IP ranges to scan during execution, to find fresh server targets out on the web that it can break into with the SQLck brute-force tool.
Apr. 27, 2018
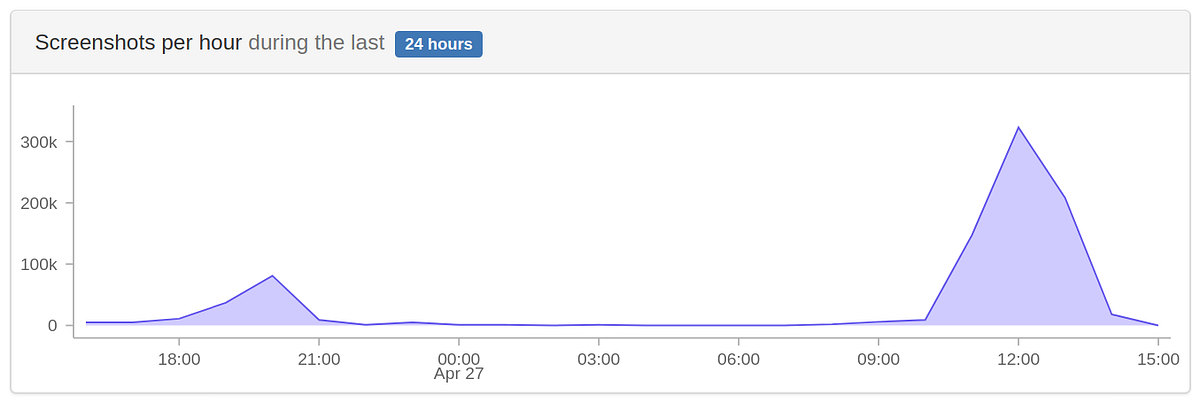
This morning when I opened up my inbox, I had around 150 alert emails from the the logging tool I use. I immediatly though I must have pushed a nasty bug to production and started investigating. I quickly realized some guy was creating new accounts really fast on our screenshot API service and was rapidly using all the free plan credit.
Apr. 27, 2018

The ShadowBrokers’ release of a trove of National Security Agency exploits last year appears to be the gift that keeps on giving, to the hacker community at least: A fresh malware that uses the EternalRomance tool has hit the scene, with Monero-mining as the stated goal. However, more damaging follow-on attacks are likely the endgame.
Source: threatpost.com
Mar. 28, 2018

Monero is a privacy-centric cryptocurrency that allows users to obscure their transactions by includ- ing chaff coins, called “mixins,” along with the actual coins they spend. In this paper, we empirically evalu- ate two weaknesses in Monero’s mixin sampling strat- egy.
Source: arxiv.org
Mar. 26, 2018

Trend Micro uncovered a new crypto mining campaign targeting Linux servers that exploit the CVE-2013-2618 flaw in Cacti’s Network Weathermap plug-in, which system administrators use to visualize network activity.
Source: securityaffairs.co
Mar. 20, 2018

Upon release, the company received instant criticism from the community at large for selling a ‘useless miner.’ The cryptographic algorithm it is designed for, CryptoNight, is mainly used by coins focused on privacy. Monero, the most widely used privacy coin based on CryptoNight, has already proclaimed it will tweak its technology to avoid being minable via the Antminer X3, hence the debate.
Mar. 19, 2018

We just saw an interesting attack technique applied to one of our PostgreSQL servers. After logging into the database, the attacker continued to create different payloads, implement evasion techniques through embedded binaries in a downloaded image, extract payloads to disk and trigger remote code execution of these payloads. Like so many attacks we’ve witnessed lately, it ended up with the attacker utilizing the server’s resources for cryptomining Monero.
Mar. 3, 2018

Security researchers at Akamai, the Internet performance company that helped Github fight off the attack, told Fortune they’ve noticed something novel some of these recent attacks. Hackers have started stuffing the barrage of Internet traffic with ransom notes.
Source: fortune.com








