Dec. 15, 2018

Cybersecurity researchers have discovered a critical vulnerability in widely used SQLite database software that exposes billions of deployments to hackers. Dubbed as ‘Magellan’ by Tencent’s Blade security team, the newly discovered SQLite flaw could allow remote attackers to execute arbitrary or malicious code on affected devices, leak program memory or crash applications.
Source: thehackernews.com
Aug. 25, 2018

I regularly search for vulnerabilities on big services that allow it and have a Bug Bounty program. Here is my first paper which covers a vulnerability I discovered on one of Facebook’s servers. While scanning an IP range that belongs to Facebook (199.201.65.0/24), I found a Sentry service hosted on 199.201.65.36, with the hostname sentryagreements.thefacebook.com.
Sentry is a log collection web application, written in Python with the Django framework. While I was looking at the application, some stacktraces regularly popped on the page, for an unknown reason. The application seemed to be unstable regarding the user password reset feature, which occasionally crashed.
Aug. 25, 2018

I regularly search for vulnerabilities on big services that allow it and have a Bug Bounty program. Here is my first paper which covers a vulnerability I discovered on one of Facebook’s servers. While scanning an IP range that belongs to Facebook (199.201.65.0/24), I found a Sentry service hosted on 199.201.65.36, with the hostname sentryagreements.thefacebook.com.
Sentry is a log collection web application, written in Python with the Django framework. While I was looking at the application, some stacktraces regularly popped on the page, for an unknown reason. The application seemed to be unstable regarding the user password reset feature, which occasionally crashed.
Jun. 2, 2018

The vulnerability has been present and exploitable in Steam for at least 10 years, according to Tom Court, a security researcher at Contextis, who wrote about the bug on Wednesday. Court said the bug left all 125 million Steam users vulnerable until March of this year, when Valve, the developers of Steam, patched it. In other words, by exploiting this bug, hackers could have executed code on the victim’s machine, effectively taking full control over it.
May. 29, 2018

Security researchers have discovered a series of new vulnerabilities in EOS blockchain platform, one of which could allow remote hackers to take complete control over the node servers running the critical blockchain-based applications. EOS is an open source smart contract platform, known as ‘Blockchain 3.0,’ that allows developers to build decentralized applications over blockchain infrastructure, just like Ethereum. Discovered by Chinese security researchers at Qihoo 360—Yuki Chen of Vulcan team and Zhiniang Peng of Core security team—the vulnerability is a buffer out-of-bounds write issue which resides in the function used by nodes server to parse contracts.
May. 17, 2018

A command injection bug in Red Hat’s DHCP client could allow an attacker to run any command on your computer. As root. RedHat Linux, together with its stablemates Fedora and CentOS, just patched a serious security bug.
RedHat-based Linux distros include a dhclient script as part of their NetworkManager package – until the latest NetworkManager security patch, this script could be tricked into running text provided in a DHCP reply as if it were a system command of its own. Technically, this sort of bug is known as a command injection vulnerability, because it allows you to sneak in a command where you are supposed to supply data. It’s also a root RCE, short for remote code execution, because you don’t need to login first, and because you get to run the remotely supplied code as a system administrator.
May. 4, 2018

The bug (CVE-2018-0264) exists in the platform’s Recording Player for Advanced Recording Format (ARF), which allows users to play back WebEx meeting recordings. The player is installed automatically when a user accesses a recording file hosted on a WebEx server. Cisco WebEx Business Suite meeting sites, Cisco WebEx Meetings sites, the Cisco WebEx Meetings Server and the Cisco WebEx ARF Player itself are all affected.
May. 4, 2018
The proof of concept attack the researchers created to demonstrate their technique takes about two minutes, from a malicious site loading their javascript in the browser to running code on the victim’s phone. It can only run that code, however, within the privileges of the browser. That means it can potentially steal credentials or spy on browsing habits, but it can’t gain deeper access without a hacker exploiting other bugs in the phone’s software.
May. 3, 2018
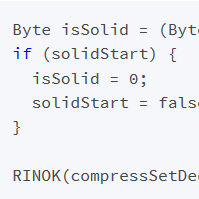
Very abstractly, the bug can be described as follows: The initialization of some member data structures of the RAR decoder classes relies on the RAR handler to configure the decoder correctly before decoding something. Unfortunately, the RAR handler fails to sanitize its input data and passes the incorrect configuration into the decoder, causing usage of uninitialized memory.
Source: landave.io
Apr. 27, 2018

The flaw exists in the Drupal core package in all supported versions of Drupal, eg. 7.x and 8.x releases. This vulnerability allows attackers to exploit Drupal powered sites from numerous attack vectors.
The end result being the site compromised as remote code can be executed, possibly giving unrestricted control to the hosting environment.
Source: drupal.sh








