Oct. 28, 2019

New PHP7 bug CVE-2019-11043 can allow even non-technical attackers to take over servers. A recently patched security flaw in modern versions of the PHP programming language is being exploited in the wild to take over servers, ZDNet has learned from threat intelligence firm Bad Packets. The vulnerability is a remote code execution (RCE) in PHP 7, the newer branch of PHP, the most common programming language used to build websites.
Sep. 14, 2019

Cybersecurity researchers at AdaptiveMobile Security disclosed a critical vulnerability in SIM cards dubbed SimJacker that could be exploited by remote attackers to compromise targeted mobile phones and spy on victims just by sending an SMS. The SimJacker vulnerability resides in the S@T (SIMalliance Toolbox) Browser dynamic SIM toolkit that is embedded in most SIM cards used by mobile operators in at least 30 countries.
Sep. 8, 2019

A security flaw in Exim mail servers could be exploited by local or remote attackers to execute arbitrary code with root privileges. The Exim development team has addressed a vulnerability in Exim mail server, tracked as CVE-2019-15846, that could be exploited by local and remote attackers to execute arbitrary code with root privileges. The vulnerability is a heap overflow that affects version 4.92.1 and prior of Exim mail server that accept TLS connections.
Aug. 18, 2019

Tulsi Gabbard’s email account went down right after the Democratic Debate and I believe I can provide assistance on where to focus your discovery efforts because I saw how other accounts, such as Jordan B. Peterson, was taken down. I’m going to recount how this happened to him so as to assist you in your legal discovery process.
Source: minds.com
Aug. 17, 2019

Speakers are everywhere, whether it’s expensive, standalone sound systems, laptops, smart home devices, or cheap portables. And while you rely on them for music or conversation, researchers have long known that commercial speakers are also physically able to emit frequencies outside of audible range for humans. At the Defcon security conference in Las Vegas on Sunday, one researcher is warning that this capability has the potential to be weaponized.
Aug. 4, 2019

At the Black Hat security conference in Las Vegas next week, a group of network communication security researchers will present findings on flaws in the 5G protections meant to thwart the surveillance devices known as stingrays. Also called ‘IMSI catchers’ after the international mobile subscriber identity number attached to every cell phone, stingrays masquerade as legitimate cell towers. Once they trick a device into connecting to it, a stingray uses the IMSI or other identifiers to track the device, and even listen in on phone calls.
Dec. 15, 2018

Computer peripheral giant Logitech has finally issued a patched version of its Logitech Options desktop app, after being taken to task for a months-old security flaw. The bug could of allowed adversaries to launch keystroke injection attacks against Logitech keyboard owners that used the app. Google Project Zero security researcher Tavis Ormandy found the bug in September and publicly disclosed the vulnerability this week.
Dec. 15, 2018

Cybersecurity researchers have discovered a critical vulnerability in widely used SQLite database software that exposes billions of deployments to hackers. Dubbed as ‘Magellan’ by Tencent’s Blade security team, the newly discovered SQLite flaw could allow remote attackers to execute arbitrary or malicious code on affected devices, leak program memory or crash applications.
Source: thehackernews.com
Nov. 28, 2018

Why x86 won’tsurvivex86 is a micro-architecture created by Intel that has been around since 1978. It powers most laptops, and more than likely powers the one you’re using right now. It’s considered powerful, effective, and reliable… until a few months ago.
A short history of leaks and exploits found in the x86 micro-architecture found in 2018 alone:- Meltdown,- Spectre,- SMT/Hyper threading found to be a security threat. Seems like a small amount, right? No.
Nov. 22, 2018
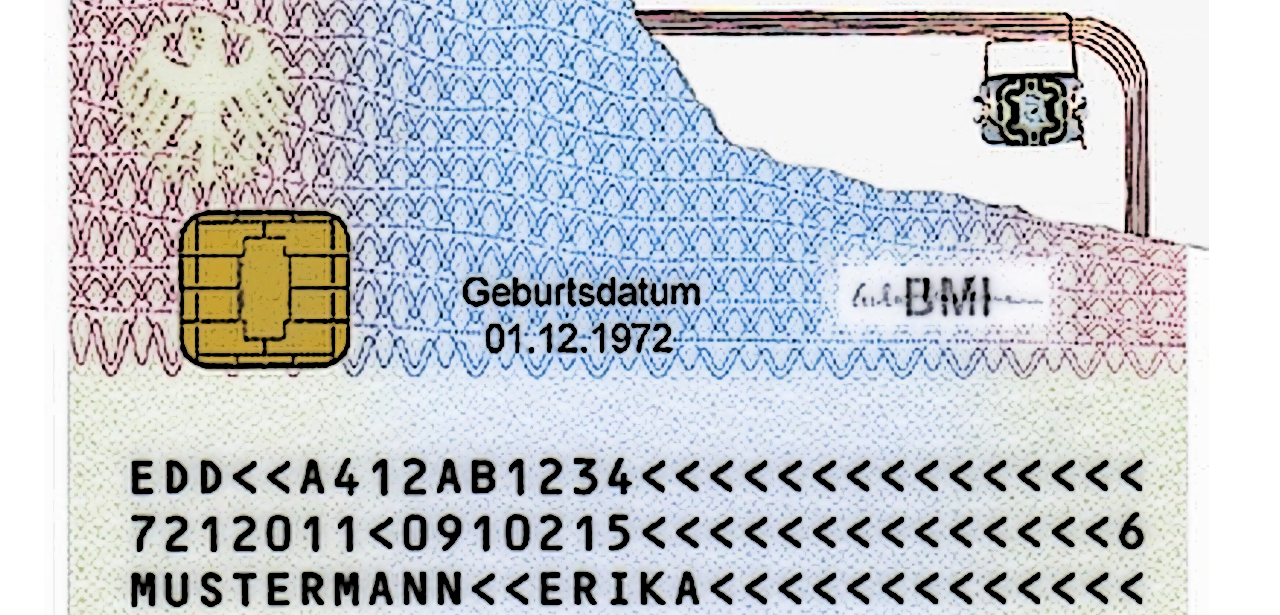
German identity cards issued since 2010 come with a radio frequency identification chip that stores information about the holder. This includes name, date of birth and a biometric picture. If the holder so chooses, it can also store their fingerprints.
The new cards are machine-readable and can be used as travel documents in most countries in Europe, as well as for authentication into online government services (tax, mail) or for age verification. Authentication via the RFID chip is possible using a smartcard reader and an eID client application that communicates with the RFID chip and an authentication server to validate the login data. To prevent tampering with the ID card data, the authentication server checks the validity of the information and then signs its reply, so that the web service can trust the legitimacy of the data received.
Oct. 27, 2018

A software security engineer has identified 12 Python libraries uploaded on the official Python Package Index (PyPI) that contained malicious code. The 12 packages have been discovered in two separate scans by a security engineer who goes online by the name of Bertus, and have long been removed from PyPI before this article’s publication. All packages were put together and worked following a similar pattern.
Sep. 10, 2018

Zerodium, a company that buys and sells vulnerabilities in popular software, has published details today on Twitter about a zero-day vulnerability in the Tor Browser, a Firefox-based browser used by privacy-conscious users for navigating the web through the anonymity provided by the Tor network. In a tweet, Zerodium said the vulnerability is a full bypass of the ‘Safest’ security level of the NoScript extension that’s included by default with all Tor Browser distributions. NoScript is a browser extension that uses a whitelist approach to let the user decide from what domains the browser can execute JavaScript, Flash, Java, or Silverlight content.
Jul. 7, 2018

A team of academics from the University of California, Irvine (UCI), have presented a type of attack that could enable a malefactor to retrieve sensitive information you entered via your keyboard – possibly up to a minute after you typed it. The researchers had 30 users enter 10 different passwords, both strong and weak, on four common external keyboards. Using a thermal imaging camera, the researchers then scanned the residual heat left on the recently-pressed keys.
Jun. 15, 2018

Seventeen malicious Docker containers earned cryptomining criminals $90,000 in 30 days in what could be a harbinger of things to come. The figure may seem tame compared to some of the larger paydays that cryptojackers have earned. But, researchers at Kromtech Security Center warn containers are shaping up to be the next ripe target for these types of criminals.
Kromtech said the malicious Docker images (17 in total) were pulled down from the Docker Hub image repository. Researchers can’t say for sure how many times the rogue containers were used by Docker Hub users, but Kromtech estimates that the 17 images were downloaded collectively 5 million times during the year they were available. All 17 were removed from Docker Hub on May 10 by Docker, afterFortinetfound the containers and published a report on the images being used to mine cryptocurrency.
Jun. 14, 2018
Microsoft has patched a vulnerability in the Cortana smart assistant that could have allowed an attacker with access to a locked computer to use the smart assistant and access data on the device, execute malicious code, or even change the PC’s password to access the device in its entirety. The issue was discovered by Cedric Cochin, Cyber Security Architect and Senior Principle Engineer at McAfee. Cochin privately reported the problems he discovered to Microsoft in April.
Jun. 14, 2018

Moodle is a widely-used open-source e-Learning software with more than 127 million users allowing teachers and students to digitally manage course activities and exchange learning material, often deployed by large universities. In this post we will examine the technical intrinsics of a critical vulnerability in the previous Moodle release detected by RIPS Code Analysis. It is located in the Quiz component of Moodle and can be successfully exploited through the teacher role in order to perform remote code execution.
Jun. 13, 2018
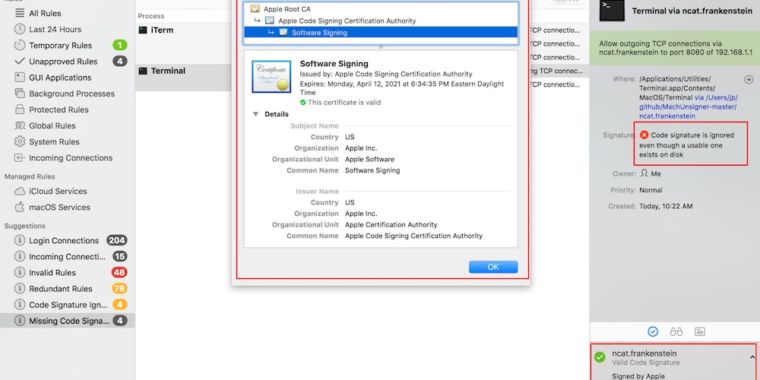
For almost 11 years, hackers have had an easy way to get macOS malware past the scrutiny of a host of third-party security tools by tricking them into believing the malicious wares were signed by Apple, researchers said Tuesday. Digital signatures are a core security function for all modern operating systems. The cryptographically generated signatures make it possible for users to know with complete certainty that an app was digitally signed with the private key of a trusted party.
Jun. 13, 2018

The issue is not new, being first spotted by the team at Qihoo 360 Netlab in February, this year, when they detected an Android worm that was spreading from Android device to Android device, infecting them with a cryptocurrency miner named ADB.Miner. The ADB.Miner worm exploited the Android Debug Bridge (ADB), a feature of the Android OS used for troubleshooting faulty devices. In the default version of the Android OS, the ADB feature is turned off, and users need to manually enable it while connecting their device via a USB connection.
Jun. 12, 2018

Canada’s family-reunification program is using a common spreadsheet application to select candidates as part of a process critics say is flawed and open to manipulation. As the first step in the program, the federal government uses Microsoft Excel to randomly pick applications in its lottery, The Globe and Mail has learned. Experts have warned that using Excel to conduct such a sensitive lottery could be problematic, and that the lottery process itself may make the system less fair over all.
Jun. 2, 2018

The vulnerability has been present and exploitable in Steam for at least 10 years, according to Tom Court, a security researcher at Contextis, who wrote about the bug on Wednesday. Court said the bug left all 125 million Steam users vulnerable until March of this year, when Valve, the developers of Steam, patched it. In other words, by exploiting this bug, hackers could have executed code on the victim’s machine, effectively taking full control over it.



















