Cyber security news and services
Why the F-35 Isn’t Good Enough for Japan

While the F-35 retains some radar evading capabilities, its radar cross section is over ten times greater than that of the F-22 making it far less survivable — leading some analysts to term it a “pseudo stealthy”fighter. The F-35 has less than half the range of the larger F-22 and lacks the Raptor’s advanced long ranged air-to-air missiles, which for an archipelago nation separated from its potential adversaries by vast seas are major shortcomings. As a single engine light platform with a small arsenal of just four air-to-air missiles, restricted to a below average speed of Mach 1.6 and a very low altitude relative to the Raptor, the F-15J, and elite twin engine Chinese fighters,the F-35 hardly presents an adequate solution to counter China’s growing fleet of J-11 fighters — let alone more advanced platforms more recently deployed by Beijing such as the Su-35 or J-20.
…Three kinds of memory leaks

But when we say “memory leak”, what do we actually mean? In my experience, apparent memory leaks divide into three broad categories, each with somewhat different behavior, and requiring distinct tools and approaches to debug. This post aims to describe these classes, and provide tools and techniques for figuring out both which class you’re dealing with, and how to find the leak.
Source: nelhage.com
…The Pentagon Is Making a Ray Gun to Stop Truck Attacks

Law’s crew has dubbed the device the Radio Frequency Vehicle Stopper. They’re working on two versions. A small one, vaguely resembling an old-time phonograph, can fit in the bed of a truck.
With a range of 50 meters, it is intended for hot pursuits. To deploy it, the driver would pull out in front of the attacker and turn it on.
…Cops take dead man’s smartphone to his corpse in attempt to unlock it

The detectives then attempted to use the fingers on Phillip’s body to unlock his own smartphone, which had been recovered from the scene. Their efforts were not successful.
Source: arstechnica.com
…French museum discovers half of its collection are fakes

A state-owned French art museum has discovered that more than half of its collection consists of worthless fakes and experts fear that other public galleries may also be stuffed with forgeries.
Source: co.uk
…Analysis: Zebrocy used heavily by the Sednit group over last two years

The Zebrocy family consists of three components. In the order of deployment these are a Delphi downloader, an AutoIt downloader and a Delphi backdoor. Figure 1 shows the relationship between these components.
In this article we describe this family and how it can coexist with the older Seduploader reconnaissance tools. We will talk about some similarities to and differences from Downdelph at the end.
…People Are Turning Their Instagram Accounts into Bots

Verified accounts turning themselves into bots, millions of fake likes and comments, a dirty world of engagement trading inside Telegram groups. Welcome to the secret underbelly of Instagram.
Source: buzzfeed.com
…As two Koreas shake hands, Hidden Cobra hackers wage espionage campaign

As Kim Jong Un became the first North Korean leader to step into South Korea, his generals continue to oversee teams of increasingly advanced hackers who are actively targeting the financial, health, and entertainment industries in the US and more than a dozen other countries. The so-called GhostSecret data reconnaissance campaign, exposed Tuesday by security firm McAfee, remains ongoing. It is deploying a series of previously unidentified tools designed to stealthily infect targets and gather data or possibly repeat the same type of highly destructive attacks visited upon Sony Pictures in 2014.
…The ultimate resource list for crypto traders and investors
Read more ⟶
“Drupalgeddon2” Recent Developments
Recently, further developments into other methods to achieve RCE were uncovered. Drupal released advisory SA-CORE-2018-004 with updated versions and patches to fix the newly identified flaws.
Source: trustwave.com
…New C# Ransomware Compiles itself at Runtime
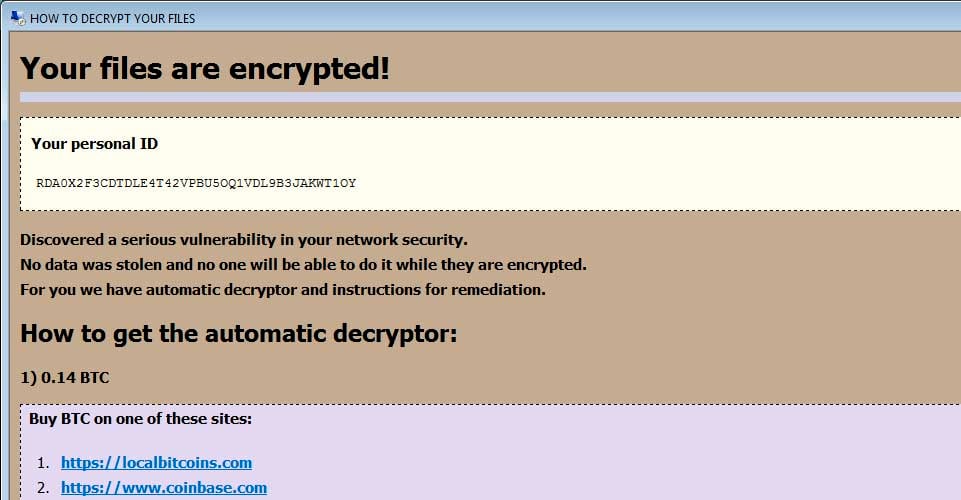
A new in-development ransomwarewas discovered that has an interesting characteristic. Instead of the distributed executable performing the ransomware functionality, the executablescompiles an embedded encrypted C# program at runtime and launches it directly into memory.
Source: bleepingcomputer.com
…Police Body Cameras Could Get Facial Recognition Technology

More than 40 civil rights, technology, media and privacy groups have voiced their concerns about the police body cameras in a letter to the AI Ethics Board, which includes groups like the American Civil Liberties Union, and the NAACP.
Source: fortune.com
…Nuclear Power Plants Have a ‘Blind Spot’ for Hackers. Here’s How to Fix That.

These days, companies in charge of some of the United States’ most critical infrastructure hire WhiteScope, Rios’s cybersecurity firm, to breach systems and then explain how they did it, all to prepare for the real thing. He and his team of researchers have picked apart the communication systems used by airplanes and cars. But sometimes Rios’s tests stray into unforeseen territory.
…I built a screenshot API and some guy was mining cryptocurrencies with it
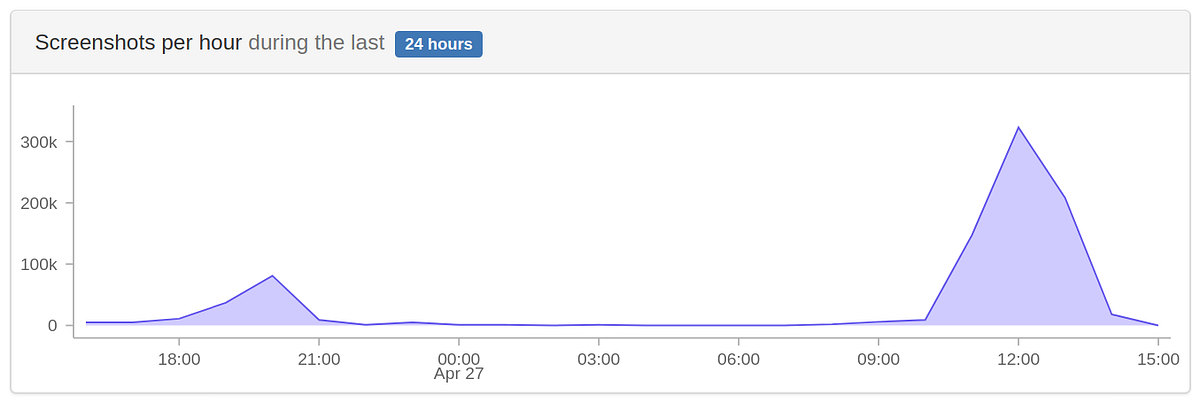
This morning when I opened up my inbox, I had around 150 alert emails from the the logging tool I use. I immediatly though I must have pushed a nasty bug to production and started investigating. I quickly realized some guy was creating new accounts really fast on our screenshot API service and was rapidly using all the free plan credit.
…Impersonators who are paid to flirt on dating apps

Every morning I wake up to the same routine. I log into the Tinder account of a 45-year-old man from Texas—a client. I flirt with every woman in his queue for 10 minutes, sending their photos and locations to a central database of potential “Opportunities.”
For every phone number I get, I make $1.75.
Source: qz.com
…Ray Ozzie’s plan for unlocking encrypted phones gets a chilly reception

To be effective, Clear wouldn’t be binding on just Apple but rather manufacturers of all computing devices, many of them low-cost products made by bootstrapped manufacturers. That means there would be dozens, hundreds, or probably thousands of PIN vaults mandated under Clear. And each of them would be a potential target for hackers all around the world.
Source: arstechnica.com
…PyRoMine Uses NSA Exploit for Monero Mining and Backdoors

The ShadowBrokers’ release of a trove of National Security Agency exploits last year appears to be the gift that keeps on giving, to the hacker community at least: A fresh malware that uses the EternalRomance tool has hit the scene, with Monero-mining as the stated goal. However, more damaging follow-on attacks are likely the endgame.
Source: threatpost.com
…Immortalize Your Terrible Tweets on the Blockchain for the Low, Low Price of $9

After signing up for an account and putting in payment information, all you have to do is reply to the tweet you want archived with ‘ @totheblockchain.’ The bot will automatically post the tweet to the blockchain and charge you the $9 fee.
Source: vice.com
…GravityRAT – The Two-Year Evolution Of An APT Targeting India

Today, Cisco Talos is uncovering a new piece of malware, which has remained under the radar for the past two years while it continues to be developed. Several weeks ago, we identified the use of the latest version of this RAT (Remote Access Tool). In this article, we will discuss the technical capabilities, the evolution, development and potential attribution of what we are calling GravityRAT.
…Drupal Remote Code Execution vulnerability exploited widely

The flaw exists in the Drupal core package in all supported versions of Drupal, eg. 7.x and 8.x releases. This vulnerability allows attackers to exploit Drupal powered sites from numerous attack vectors.
The end result being the site compromised as remote code can be executed, possibly giving unrestricted control to the hosting environment.
Source: drupal.sh
…