Cyber security news and services
CSE Malware ZLab – Malware Analysis Report: The Bandios malware suite
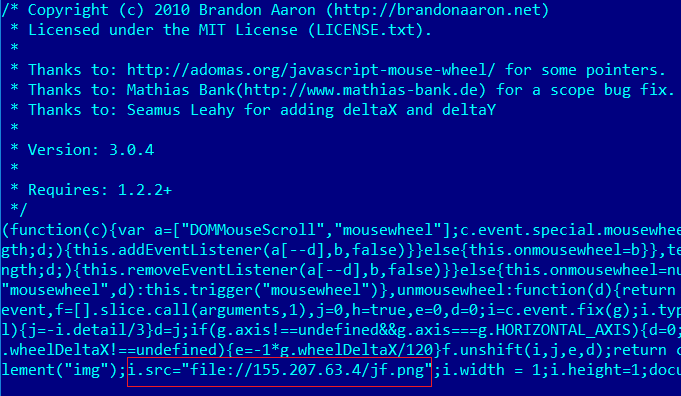
The researchers at CSE ZLab have spotted a new family of malware, tracked as Bandios spreading in the wild. The peculiarity of Bandios malware is the fact that this malware is in a rapid and constant evolution and development.
Source: securityaffairs.co
…Atlanta Spent $2.6M to Recover From $52,000 Ransomware Scare

The City of Atlanta spent more than $2.6 million on emergency efforts to respond to a ransomware attack that destabilized municipal operations last month. Attackers, who infected the city’s systems with the pernicious SamSam malware, asked for a ransom of roughly $50,000 worth of bitcoin. (The exact value has fluctuated due to bitcoin’s volatility.)
Atlanta officials haven’t said whether they paid the ransom, or even tried, but it seems that they may not have even had the chance; the attackers quickly took the payment portal offline, and left the city to fend for itself. So far, the recovery has been far more costly than the initial demand.
…Whether Ethereum is a security

I am often asked, directly, whether I think this coin or that one is a security (and thus required to be registered with the SEC before being offered to the public) or not. Virtually every time I demur.
Source: prestonbyrne.com
…Muhstik Botnet Exploits Highly Critical Drupal Bug

Researchers are warning a recently discovered and highly critical vulnerability found inDrupal’s CMS platform is now being actively exploited by hackers who are using it to install cryptocurrency miners and to launch DDoS attacks via compromised systems. At the time of the disclosure, last month, researchers said they were not aware of any public exploits.
Source: threatpost.com
…New hacks siphon private cryptocurrency keys from airgapped wallets
On Monday, Guri published a new paper that applies the same exfiltration techniques to ‘cold wallets,’ which are not stored on devices connected to the Internet. The most effective techniques take only seconds to siphon a 256-bit Bitcoin key from a wallet running on an infected computer, even though the computer isn’t connected to any network. Guri said the possibility of stealing keys that protect millions or billions of dollars is likely to take the covert exfiltration techniques out of the nation-state hacking realm they currently inhabit and possibly bring them into the mainstream.
…Transcription Service Leaked Medical Records
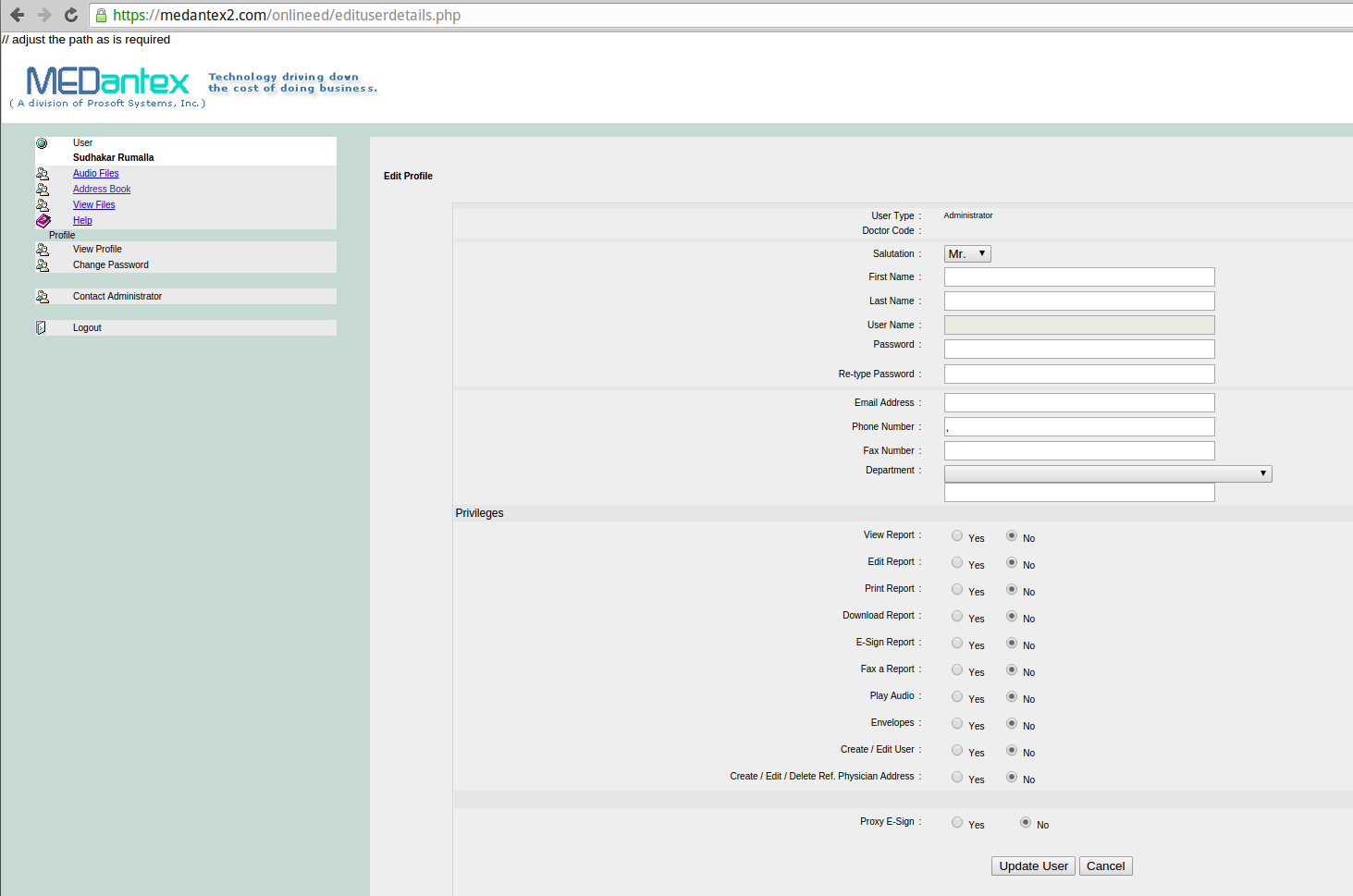
MEDantex, a Kansas-based company that provides medical transcription services for hospitals, clinics and private physicians, took down its customer Web portal last week after being notified by KrebsOnSecurity that it was leaking sensitive patient medical records — apparently for thousands of physicians.
Source: krebsonsecurity.com
…The “unpatchable” exploit that makes every current Nintendo Switch hackable [Updated]
![The “unpatchable” exploit that makes every current Nintendo Switch hackable [Updated]](https://cdn.arstechnica.net/wp-content/uploads/2018/04/switchhax-760x380.jpg)
A newly published ‘exploit chain’ for Nvidia Tegra X1-based systems seems to describe an apparently unpatchable method for running arbitrary code on all currently available Nintendo Switch consoles. Hardware hacker Katherine Temkin and the hacking team at ReSwitched released an extensive outline of what they’re calling the Fusée Gelée coldboot vulnerability earlier today, alongside a proof-of-concept payload that can be used on the Switch.
…Hackers Behind Healthcare Espionage Infect X-Ray and MRI Machines

Dubbed ‘Orangeworm,’ the hacking group has been found installing a wormable trojan on machines hosting software used for controlling high-tech imaging devices, such as X-Ray and MRI machines, as well as machines used to assist patients in completing consent forms.
Source: thehackernews.com
…How DNA Transfer Framed Lukis Anderson for Murder
We leave traces of our genetic material everywhere, even on things we’ve never touched. That got Lukis Anderson charged with a brutal crime he didn’t commit. We leave traces of our genetic material everywhere, even on things we’ve never touched.
That got Lukis Anderson charged with a brutal crime he didn’t commit.
Source: themarshallproject.org
…We don’t know what to do if a satellite gets hacked
Hundreds of multi-ton liabilities—soaring faster than the speed of sound, miles above the surface of the earth—are operating on Windows-95.
Source: theoutline.com
…Quantum Blockchains Could Act Like Time Machines

Superposition lets one qubit perform two calculations at once, and if two qubits are linked through a quantum effect known as entanglement, they can help perform 2^2 or four calculations simultaneously; three qubits, 2^3 or eight calculations; and so on. In principle, a quantum computer with 300 qubits could perform more calculations in an instant than there are atoms in the visible universe. A powerful enough quantum computer could successfully break conventional cryptography, including that protecting blockchains.
…Cryptomining Campaign Returns Coal and Not Diamond
Soon after a launch of a new cryptocurrency, Bitvote, in January, Talos discovered a new mining campaign affecting systems in India, Indonesia, Vietnam and several other countries that was tied to Bitvote.
Source: talosintelligence.com
…Cryptocurrencies Were Never Good for Anybody But the Rich

The value of cryptocurrencies across the board skyrocketed last year due to speculative investing, and it feels as though early attempts to position digital money as a populist and democratic alternative to traditional finance are falling apart at the seams. But cryptocurrency has always been about the rich getting richer.
Source: vice.com
…Yahoo mega-breach hacker faces nearly 8 years in prison

On Tuesday, Department of Justice (DOJ) prosecutors asked a San Francisco federal court judge to impose that sentence on Karim Baratov, a Canadian citizen born in Kazakhstan who was indicted in March 2017 for working with two officers of the Russian Federal Security Service (FSB) -that’s Russia’s successor to the KGB – to pull off the historic Yahoo breach.
Source: sophos.com
…The US Navy Wants Undersea Gas Stations for Underwater Drones

A California company is working on an underwater refueling station that can top off the fuel cells of undersea surveillance drones, allowing the vehicles to venture farther and work longer.
Source: vice.com
…How China Is Buying Its Way into Europe

For more than a decade, Chinese political and corporate leaders have been scouring the globe with seemingly bottomless walletsin hand. From Asia to Africa, the U.S. and Latin America, the results are hard to ignore as China has asserted itself as an emerging world power. Less well known is China’s diffuse but expanding footprint in Europe.
Source: bloomberg.com
…Energetic Bear/Crouching Yeti: attacks on servers
Energetic Bear/Crouching Yeti is a widely known APT group active since at least 2010. The group tends to attack different companies with a strong focus on the energy and industrial sectors. Companies attacked by Energetic Bear/Crouching Yeti are geographically distributed worldwide with a more obvious concentration in Europe and the US.
In 2016-2017, the number of attacks on companies in Turkey increased significantly.
Source: securelist.com
…One year after ICO mania, these big-money projects are delivering

And there’s been a lot of concern that, after their huge ICO fundraises and with no contractual obligation to deliver a product, founders would have little incentive to stick around and do the hard work. But we’re now one year in, and it’s heartening to see that real, meaningful products are shipping.
Source: venturebeat.com
…The Web of Profit: A look at the cybercrime economy

Last April, I started a conversation with cybersecurity company Bromium. The company was keen to uncover where the streams of revenue generated by cybercrime eventually go and whether this money is ultimately supporting other areas of crime. Over the past 10 months, I have been examining this question, and I must say there have been some eyebrow-raising findings.
Source: venturebeat.com
…Google’s Project Zero exposes unpatched Windows 10 lockdown bypass

The newly disclosed bypass is a medium-severity issue that affects Windows 10 S or any Windows 10 machine with user mode code integrity (UMCI) enabled, such as enterprise Windows 10 PCs configured with Microsoft’s virtual container known as Device Guard.
Source: zdnet.com
…
