Cyber security news and services
Bitcoin Mining May Be Even Less Economically Viable Than We Thought

New Morgan Stanley analysis reckons that Bitcoin, currently a little over $8,300, needs to clear $8,600 in order for mining to be profitable.
Source: fortune.com
…FDA Wants Medical Devices to Have Mandatory Built-In Update Mechanisms

An FDA document released this week reveals several of the FDA’s plans, including the desire to force device makers to include mandatory update systems inside products for the purpose of delivering critical security patches.
Source: bleepingcomputer.com
…FTC Puts Uber on a Short Leash for Security Breaches

Last week, Uber and the FTC finally settled on a revised consent agreement that now covers both the 2014 and 2016 breaches. The new agreement includes even more comprehensive security and privacy risk assessments, covering the security of Uber’s software development environment and use of the bug bounty.
Source: ieee.org
…Why a Cryptocurrency Mining Giant Is Burning Money in a ‘Black Hole’

Coin burning, if you’re not familiar, is a well-trod path to inflating the value of a cryptocurrency with a fixed supply, like Bitcoin Cash. The value of coins with a fixed supply is based on increasing demand and steadily decreasing supply. If you can accelerate the diminishment of available coin stock, then theoretically that should increase demand for the remaining supply and, in turn, the coin’s value.
…Insecure RSA Conference app leaked attendee data
A mobile application built by a third party for the RSA security conference in San Francisco this week was found to have a few security issues of its own—including hard-coded security keys and passwords that allowed a researcher to extract the conference’s attendee list. The conference organizers acknowledged the vulnerability on Twitter, but they say that only the first and last names of 114 attendees were exposed.
…Teen Who Hacked Ex-CIA Director John Brennan Gets Sentenced to 2 Years of Prison

Gamble was arrested in February of 2016 and he pleaded guilty to ten hacking charges in October of last year. Now 18 years old, he was finally sentenced on Friday afternoon local time in the Old Bailey, the central criminal court in London after his first sentencing hearing in January was postponed. The judge ruled that he will have to spend two years at a youth detention center, according to reports from the court.
…Explore the Hidden Art on the Bitcoin Blockchain in ‘Message From the Mines’
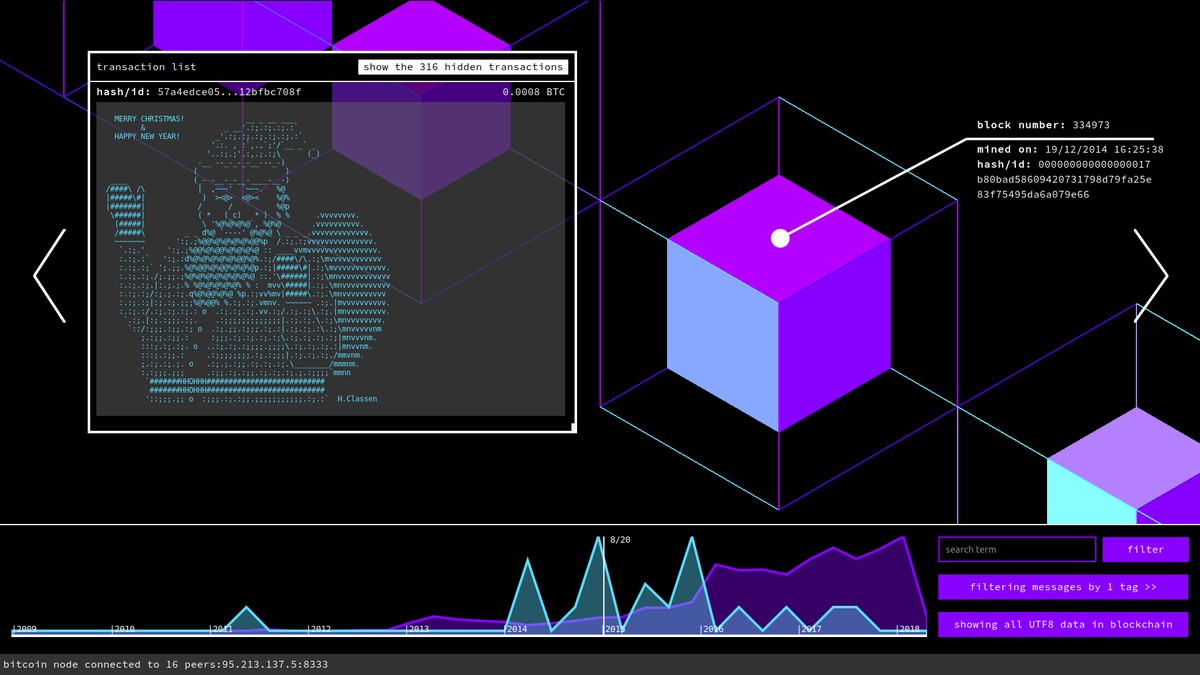
The Bitcoin blockchain now consists of over 500,000 such blocks and a new one is added roughly every ten minutes. Most of these blocks contain data related to sending and receiving Bitcoin, but the blockchain also contains its fair share of short messages—like the one Nakamoto put in the first-ever block of data—photos, and even artworks hidden among the data if you know where to look and how to extract them.
…The taxman matches Bitcoin transactions and bank transfers to identify people
All of the transaction data for Bitcoin and other cryptocurrencies are stored in a public ledger known as Blockchains. The tax office has been admitted generous access to bank transfers and other data, which enables identifying people. By matching the transfers it is evident that in the past most citizens have not reported profits made with virtual currencies.
Source: metropolitan.fi
…Government accidentally sends file on “remote mind control” to journalist
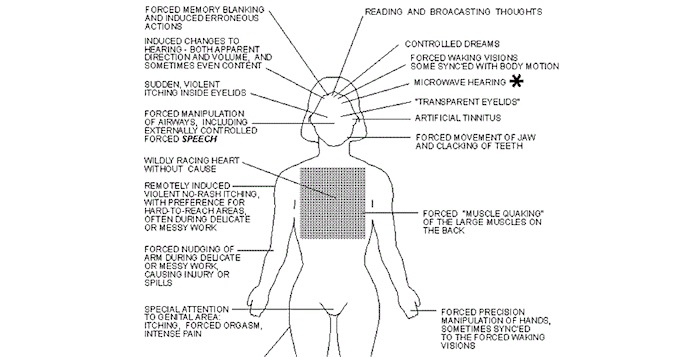
The federal government has absolutely experimented with mind control in a variety of methods, but the documents here do not appear to be official. Waltman had no idea why these documents were included in his request and isn’t sure why the government is holding them. The WSFC did not respond to requests for more information.
Source: boingboing.net
…Palantir Knows Everything About You

Peter Thiel’s data-mining company is using War on Terror tools to track American citizens. The scary thing? Palantir is desperate for new customers.
Source: bloomberg.com
…iOS Sync Glitch Lets Attackers Control Devices

Researchers found a new iOS vulnerability called ‘trustjacking,’ which exploits a feature called iTunes Wi-Fi Sync to give attackers persistent control over victims’ devices.
Source: threatpost.com
…Windows Exploitation Tricks: Exploiting Arbitrary File Writes for Local Elevation of Privilege
An arbitrary file write vulnerability is where a user can create or modify a file in a location they could not normally access. This might be due to a privileged service incorrectly sanitizing information passed by the user or due to a symbolic link planting attack where the user can write a link into a location which is subsequently used by the privileged service. The ideal vulnerability is one where the attacking user not only controls the location of the file being written but also the entire contents.
…Amazon Wins Patent for Data Stream to ‘Identify’ Bitcoin Users for Law Enforcement

The patent, which was filed in 2014 but approved on Tuesday, comes at a time when regulators’ desire to track and police cryptocurrency is running up against the technology’s core promises of pseudonymity for users. Bitcoin users, for example, are represented in the virtual currencies ledger by strings of text and numbers generated by a cryptographic algorithm. Taxation for Bitcoin thus relies on self-reporting.
…Upgradeable smart contracts in Ethereum

Ethereum contracts are immutable but there is a way to design contracts which can be upgraded, so you can fix bugs quickly and add features. We’ll see how to create upgradable contracts.
Source: zohaib.me
…A Sobering Look at Fake Online Reviews
Bryan Seely, a security expert who has written extensively about the use of fake search listings to conduct online bait-and-switch scams, said the purpose of sites like those that Seorehabs pays people to create is to funnel calls to a handful of switchboards that then sell the leads to rehab centers that have agreed to pay for them. Many rehab facilities will pay hundreds of dollars for leads that may ultimately lead to a new patient. After all, Seely said, some facilities can then turn around and bill insurance providers for thousands of dollars per patient.
…Tens of thousands of Facebook accounts compromised in days by malware

The malware was designed to copy the credentials in a way that wouldn’t be detected by antivirus programs. The copying process, for instance, remained active for less than one minute. The malware didn’t steal general credentials, and it copied cookies and saved passwords by querying copies of the original cookies and LoginData files rather than through other means.
Source: arstechnica.com
…Basis Protocol/Basecoin: the worst idea in cryptocurrency, reborn

UPDATE, 4/18/18 – it appears Basecoin has changed its name to “Basis Protocol” and has alsoraised $133 million from top Valley investors anyway. Despite the fact that it’s an economic dumpster fire.
Source: prestonbyrne.com
…The Cat-and-Mouse Game Between Apple and the Manufacturer of an iPhone Unlocking Tool

Former Apple security engineer Braden Thomas, who now works for a company called Grayshift, warned customers who had bought his GrayKey iPhone unlocking tool that iOS 11.3 would make it a bit harder for cops to get evidence and data out of seized iPhones. A change in the beta didn’t break GrayKey, but would require cops to use GrayKey on phones within a week of them being last unlocked.
…PBot: a Python-based adware

Recently, we came across a Python-based sample dropped by an exploit kit. Although it arrives under the disguise of a MinerBlocker, it has nothing in common with miners. In fact, it seems to be PBot/PythonBot: a Python-based adware.
Source: malwarebytes.com
…A ‘Cryptocurrency’ Without a Blockchain Is Eating My City

The Toronto-based startup’s origins lie in a Facebook group created by founder Emily Bitze in 2013. It began as an insider-y scene of young people bartering used stuff—the cardinal rule was “no money allowed in this zone.” The group soon exploded into having more than 60,000 members in the Toronto area alone, with spinoffs in numerous cities.
Bunz was a critical entry point for many newcomers to a secondhand market for furniture, knick-knacks, food, and whatever else. People made friends, found housing, and formed bands through the Facebook group and its many offshoots.
…