Cyber security news and services
Phish of GoDaddy Employee Jeopardized Escrow.com, Among Others
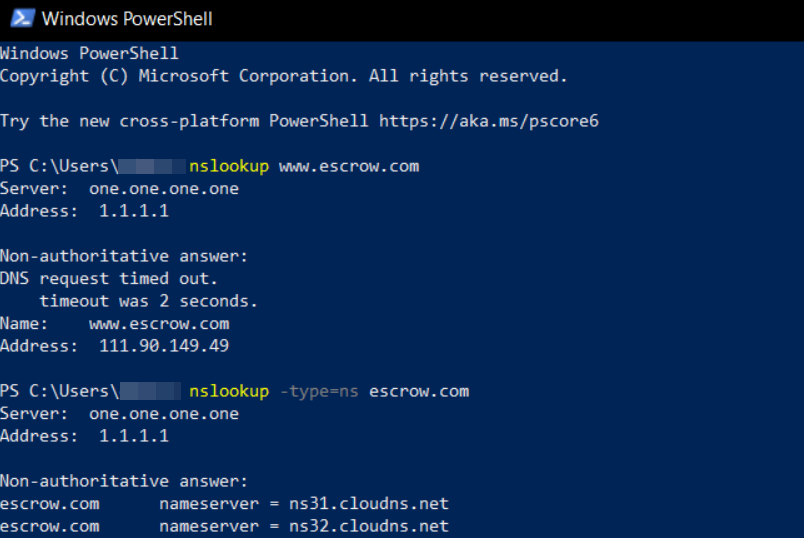
A spear-phishing attack this week hooked a customer service employee at GoDaddy.com,the world’s largest domain name registrar, KrebsOnSecurity has learned. The incident gave the phisher the ability to view and modify key customer records, access that was used to change domain settings for a half-dozen GoDaddy customers, including transaction brokering site escrow.com. Escrow.comhelps people safely broker all sorts of transactions online (ironically enough, brokering domain sales is a big part of its business).
…Alleged Zoom Zero-Days for Windows, MacOS for Sale

Alleged Windows flaw allows for remote code execution and is being flogged for $500,000. Hackers claim they have discovered two zero-day vulnerabilities for the Zoom video conferencing platform that would allow threat actors to spy on people’s private video conferences and further exploit a target’s system. Flaws target Zoom clients for the Windows and the MacOS operating system, accordingto a published report by Vice Motherboard.
…Pastebin Made It Harder To Scrape Its Site And Researchers Are Pissed Off

Pastebin quietly changed its terms and services that allowed researchers to study leaked data, malware, and stolen passwords. The most famous paste site, used by hackers of all stripes to host lists of stolen passwords, announcements of data breaches, and malware has made it harder for security researchers to scrape it looking for that kind of information. Pastebin is one of the most famous websites that allows anyone, even without being registered, to “paste” any kind of text and make it public.
…Academics steal data from air-gapped systems using PC fan vibrations

Israeli researchers use vibrations from CPU, GPU, or PC chassis fans to broadcast stolen information through solid materials and to nearby receives, breaking air-gapped system protections. Academics steal data from air-gapped systems using PC fan vibrations Israeli researchers use vibrations from CPU, GPU, or PC chassis fans to broadcast stolen information through solid materials and to nearby receives, breaking air-gapped system protections. The technique, codenamed AiR-ViBeR, is the latest in a long list of wacky data exfiltration techniques devised by Mordechai Guri, the head of R&D at the Ben-Gurion University of the Negev in Israel.
…Europe publishes draft rules for coronavirus contact-tracing app development

The European Commission (EC) has published a document describing how it thinks member nations can best built a contact-tracing smartphone app to fight the COVID-19 pandemic. Such apps have been adopted by Singapore and India. The UK, USA and Australia have all suggested they’ll soon follow suit.
Apple and Google have weighed in, saying they’ll tune their mobile operating systems to help the apps operate, a crucial step as current apps use Bluetooth yet smartphones don’t allow the wireless protocol to operate constantly. The apps are controversial as their explicit purpose is collecting data about users and then sharing it. But they’re also seen as a tool that will make it possible to loosen lockdowns because, by tracing encounters that lead to infections, they have the potential to make it possible to understand who needs to be in isolation and who can roam more freely.
…The ancient computers in the Boeing 737 Max are holding up a fix
A brand-new Boeing 737 Max gets built in just nine days. In that time, a team of 12,000 people turns a loose assemblage of parts into a finished $120 million airplane with some truly cutting-edge technology: winglets based on ones designed by NASA, engines that feature the world’s first one-piece carbon-fiber fan blades, and computers with the same processing power as, uh, the Super Nintendo. The Max has been grounded since March 2019, after some badly written software caused two crashes that killed 346 people.
…Former Tesla employees brought stolen documents to self-driving startup Zoox

Tesla and self-driving startup Zoox have settled a trade secret lawsuit filed last year. Four former Tesla employees were accused of taking confidential documents to Zoox, which the startup admitted this week after the settlement. Self-driving startup Zoox has admitted that four of its employees took confidential documents from their previous employer Tesla, according to a statement issued after the company settled a lawsuit this week over the matter.
…Ransomware leak Boeing, Lockheed Martin, SpaceX documents after contractor refuses to pay

Internal confidential documents belonging to some of the largest aerospace companies in the world have been stolen from an industrial contractor and leaked online. The data was pilfered and dumped on the internet by the criminals behind the DoppelPaymer Windows ransomware, in retaliation for an unpaid extortion demand. The sensitive documents include details of Lockheed-Martin-designed military equipment – such as the specifications for an antenna in an anti-mortar defense system – according to a Register source who alerted us to the blueprints.
…How Apple and Google Are Enabling Covid-19 Bluetooth Contact

The tech giants have teamed up to use a Bluetooth-based framework to keep track of the spread of infections without compromising location privacy. Since Covid-19 began its spread across the world, technologists have proposed using so-called contact-tracing apps to track infections via smartphones. Now, Google and Apple are teaming up to give contact-tracers the ingredients to make that system possible—while in theory still preserving the privacy of those who use it.
…We Saw NSO’s Covid-19 Software in Action, and Privacy Experts Are Worried

We got a demo of the infamous Israeli spyware company’s Coronavirus surveillance software. A number of surveillance tech companies are pivoting to tracking coronavirus-infected citizens. Experts are worried that they are just trying exploit a crisis to expand their questionable businesses.
The rapidly spreading coronavirus has infected more than 900,000 and killed more than 45,000 people all over the world. This unprecedented crisis is also giving a chance to governments, and their technology providers, to ramp up mass surveillance. In the spirit of never letting a good crisis go to waste, several companies around the world— some already notorious and some less public—are pitching and developing surveillance tools to help governments track citizens with the goal of stopping the spread of coronavirus.
…PayPal and Venmo Are Letting SIM Swappers Hijack Accounts

Even after being warned by researchers, some companies still haven’t fixed systems that make it easy for hackers to take over accounts. Several major apps and websites, such as Paypal and Venmo have a flaw that lets hackers easily take over users’ accounts once they have taken control of the victim’s phone number. Earlier this year, researchers at Princeton University found 17 major companies, among them Amazon, Paypal, Venmo, Blizzard, Adobe, eBay, Snapchat, and Yahoo, allowed users to reset their passwords via text message sent to a phone number associated with their accounts.
…Emotet Took Down a Network by Overheating All Computers

Microsoft says that an Emotet infection was able to take down an organization’s entire network by maxing out CPUs on Windows devices and bringing its Internet connection down to a crawl after one employee was tricked to open a phishing email attachment. The Emotetpayload was delivered and executed on the systems of Fabrikam — a fake name Microsoft gave the victim in their case study —five days after the employee’s user credentials were exfiltrated to the attacker’s command and control (C&C) server. Before this, the threat actors used the stolen credentials to deliver phishing emails to other Fabrikam employees, as well as to their external contacts, with more and more systems getting infected and downloading additional malware payloads.
…How xHelper Android Malware Re-Installs Even After Factory Reset

How to remove xHelper malware from Android, cybersecurity researcher unveiled today.
Source: thehackernews.com
…Disease Surveillance and the Fourth Amendment

With the right safeguards, aggressive disease surveillance is likely permissible under the Fourth Amendment. Like governments around the world, the United States is struggling with the “coronavirus trilemma”: It wants to protect lives, ease social isolation, and protect privacy and civil liberties, but it can do only two of those at the same time. In particular, and as South Korea’s successful management of the coronavirus shows, extensive surveillance may be the only way to control the outbreak while preserving some degree of normalcy for economic and social life.
…Google backs Apple’s SMS OTP standard proposal

Google backs Apple’s SMS OTP standard proposal Apple’s proposal to standardize the format of SMS OTPs (one-time passcodes) moves to the WICG. Google is now backing a standard proposed by Apple engineers in January to create a default format for one-time passcodes (OTP) sent via SMS to users during the two-factor authentication (2FA) process. The standard, proposed by Apple engineers working on the Safari WebKit project, has now reached the status of official Web Platform Incubator Community Group (WICG) specification draft.
…Fingerprint cloning: Myth or reality?

What are the security improvements in fingerprint scanning since it was first defeated on the iPhone 5? How does 3-D printing technology impact fingerprint authentication?
Define a threat model to the attacks to provide a realistic context.
Source: talosintelligence.com
…Microsoft Buys Corp.com So Bad Guys Can’t

In February, KrebsOnSecurity told the story of a private citizen auctioning off the dangerous domain corp.com for the starting price of $1.7 million. Domain experts called corp.com dangerous because years of testing showed whoever wields it would have access to an unending stream of passwords, email and other sensitive data from hundreds of thousands of Microsoft Windows PCs at major companies around the globe. This week, Microsoft Corp. agreed to buy the domain in a bid to keep it out of the hands of those who might abuse its awesome power.
…Dangerous Domain Corp.com Goes Up for Sale
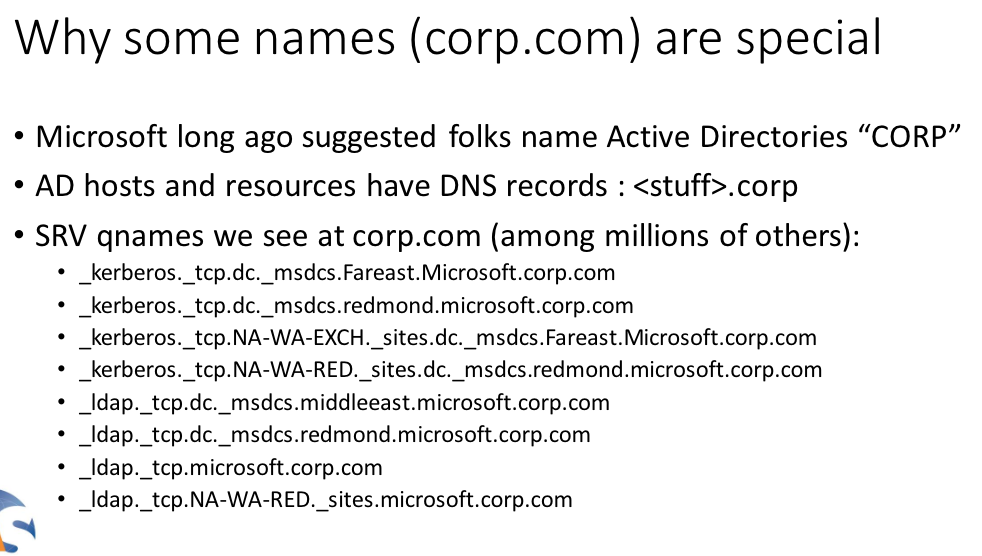
As anearly domain name investor, Mike O’Connor had by 1994 snatched up several choice online destinations, including bar.com, cafes.com, grill.com, place.com, pub.com and television.com. Some he sold over the years, but for the past 26 years O’Connor refused to auction perhaps the most sensitive domain in his stable — corp.com. It issensitive because years of testing shows whoever wields it would have access to an unending stream of passwords, email and other proprietary data belonging to hundreds of thousands of systems at major companies around the globe.
…Cloudflare Axes Google reCAPTCHA Due to Privacy, Price

Cloudflare’s CEO said it is replacing Google’s reCAPTCHA tool with hCaptcha due to pricing, privacy and availability concerns.
Source: threatpost.com
…YouTube borked when users enable Firefox anti-fingerprinting

Firefox users have recently started to notice that YouTube does not display videos properly when they enable the browser’s anti-fingerprinting technology for better privacy.
Source: bleepingcomputer.com
…