Cyber security news and services
Encryption 101: How to break encryption

Continuing on in our Encryption 101 series, where we gave a malware analyst’s primer on encryption and demonstrated encryption techniques using ShiOne ransomware, we now look at what it takes to break an encryption. In order for something as powerful as encryption to break, there needs to be some kind of secret flaw. That flaw is often a result of an error in implementation.
…A Small American Town Wants to Put a Moratorium on Bitcoin Mining

Now, Plattsburgh could become the first municipality in the US to put a moratorium on Bitcoin mining. According to a proposed law tabled by the mayor on March 1, the city is seeking to put an 18-month moratorium on any new Bitcoin mining operations while new regulations around zoning and electricity use are drafted. A public meeting to discuss the proposal is planned for March 15.
…Google Is Quietly Providing AI Technology for Drone Strike Targeting Project

Google, which has made strides in applying its proprietary deep learning tools to improve language translation, and vision recognition, has a cross-team collaboration within the company to work on the AI drone project.
Source: theintercept.com
…‘Stalkerware’ Seller Shuts Down Apps ‘Indefinitely’ After Getting Hacked Again
Retina-X Studios, which sells several products marketed to parents and employers to keep tabs on their children and employees—but also used by jealous partners to spy on their significant others—announced that its shutting down all its spyware apps on Tuesday with a message at the top of its website.
Source: vice.com
…Researchers Bypassed Windows Password Locks With Cortana Voice Commands
Tal Be’ery and Amichai Shulman found that the always-listening Cortana agent responds to some voice commands even when computers are asleep and locked, allowing someone with physical access to plug a USB with a network adapter into the computer, then verbally instruct Cortana to launch the computer’s browser and go to a web address that does not use https—that is, a web address that does not encrypt traffic between a user’s machine and the website. The attacker’s malicious network adapter then intercepts the web session to send the computer to a malicious site instead, where malware downloads to the machine, all while the computer owner believes his or her machine is protected.
…Gozi ISFB Remains Active in 2018, Leverages “Dark Cloud” Botnet For Distribution
Gozi ISFB is a well-known and widely distributed banking trojan, and has been in the threat landscape for the past several years. Banking trojans are a widely distributed type of malware that attackers leverage in an attempt to obtain banking credentials from customers of various financial institutions. The source code associated with Gozi ISFB has been leaked several times over the years, and the robust features available within the Gozi ISFB code base have since been integrated into additional malware, such as GozNym.
…20 ICOs to watch in March

In an attempt to predict startup success from their inception, I and four of my colleagues at NYU developed an AI-powered engine and conducted a digital footprint analysis of more than 6,000 founders using data points such as educational background, employment history, entrepreneurial experience, and personality traits. Based on that training data, our algorithm then predicts how likely a brand new startup is to succeed and gives it a score.
…LTE security flaws could be used for spying, spreading chaos

There have been lots of reasons to be concerned about how easily someone with the right tools and knowledge could do very bad things with cellular communications networks. And while none of them have necessarily been to the level of some of the fictional stunts pulled off on television (see Mr. Robot), new research shows that things are even worse than they appear—and in many cases, that’s because of how carriers have implemented cellular standards.
…Pennsylvania Sues Uber Over Data Breach Disclosure

The stolen Uber data included the names and driver’s license information of around 600,000 drivers—including at least 13,500 from Pennsylvania—as well as data belonging to 25 million users in the US. It impacted over 57 million people in total. ‘Uber violated Pennsylvania law by failing to put our residents on timely notice of this massive data breach,’ Josh Shapiro, the states’s attorney general, said in a statement.
…MoviePass CEO says the app tracks your location before and after movies

Everyone knew the MoviePass deal is too good to be true — and as is so often the case these days, it turns out you’re not the customer, you’re the product. And in this case they’re not even attempting to camouflage that. Mitch Lowe, the company’s CEO, told an audience at a Hollywood event that “we know all about you.”
…Knot Forensics

When someone commits a crime, it’s safe to assume that person wants to get rid of the evidence; they may wear gloves, or conceal their identity. But criminals get caught, often on the most incidental oversights—some as small and seemingly innocent as a knot in a string.
Source: atlasobscura.com
…Coinbase Is Getting Sued for Insider Trading

On December 19, Coinbase made a surprise announcement that it had started to trade a cryptocurrency called Bitcoin Cash. Coinbase has more customers than the mainstream finance company Charles Schwab, so its decision on whether to support a cryptocurrency has a big impact on that cryptocurrency’s value. Indeed, within minutes of Coinbase’s announcement, the price of Bitcoin Cash shot up by nearly $1,000 and all further Bitcoin Cash trades were cancelled.
…Brain-damaging “health attacks” spur US to permanently cut Cuba embassy staff

In December, an investigation by a panel of Cuban scientists concluded that there likely were no attacks. The panel determined that the most likely explanation was mass psychogenic illness (MPI), which is essentially a collective delusion among a cohesive group of people that a sickness is spreading among them. But the US doctors who evaluated the affected individuals dismissed this idea, noting that their observed symptoms and injuries were not ones that could be consciously or unconsciously manipulated.
…Brit semiconductor tech ended up in Chinese naval railgun
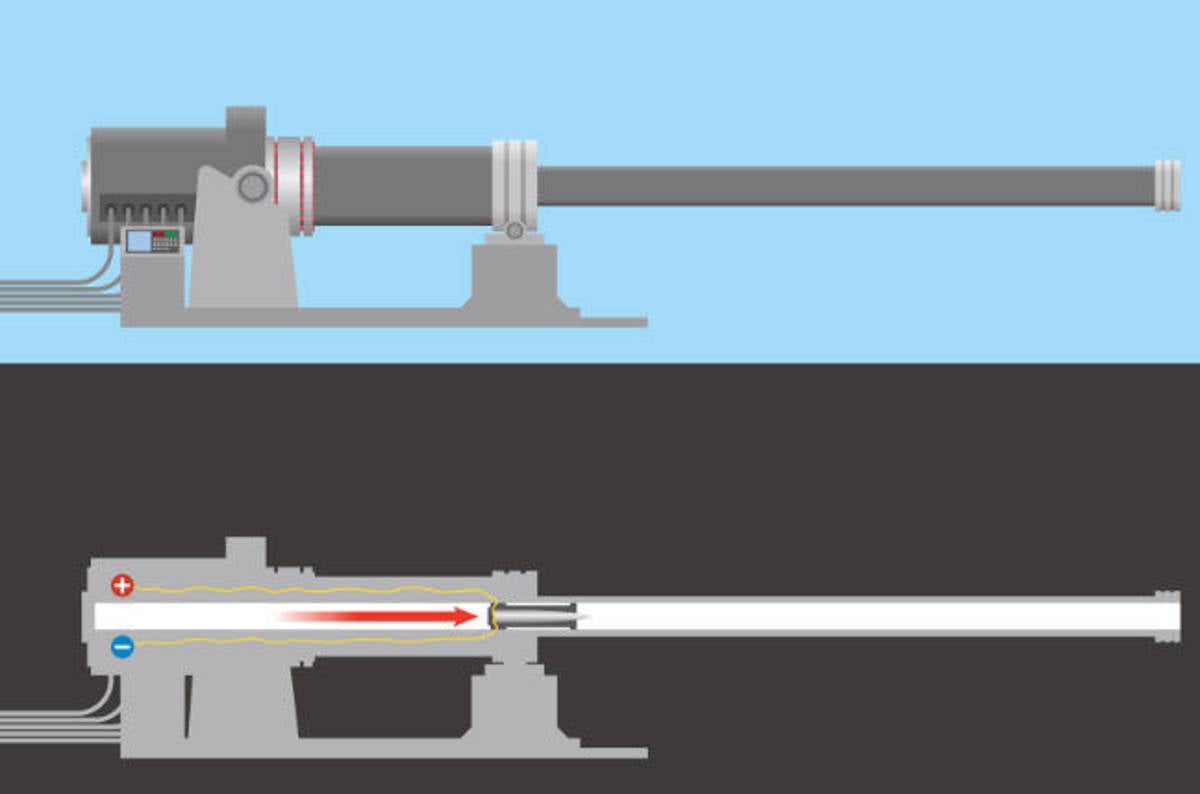
A Chinese firm’s buyout of a British semiconductor company may have directly led to China developing railgun weaponry and electromagnetic aircraft carrier catapults for its navy, according to reports.
Source: co.uk
…I got infected with malware and appreciated by its author
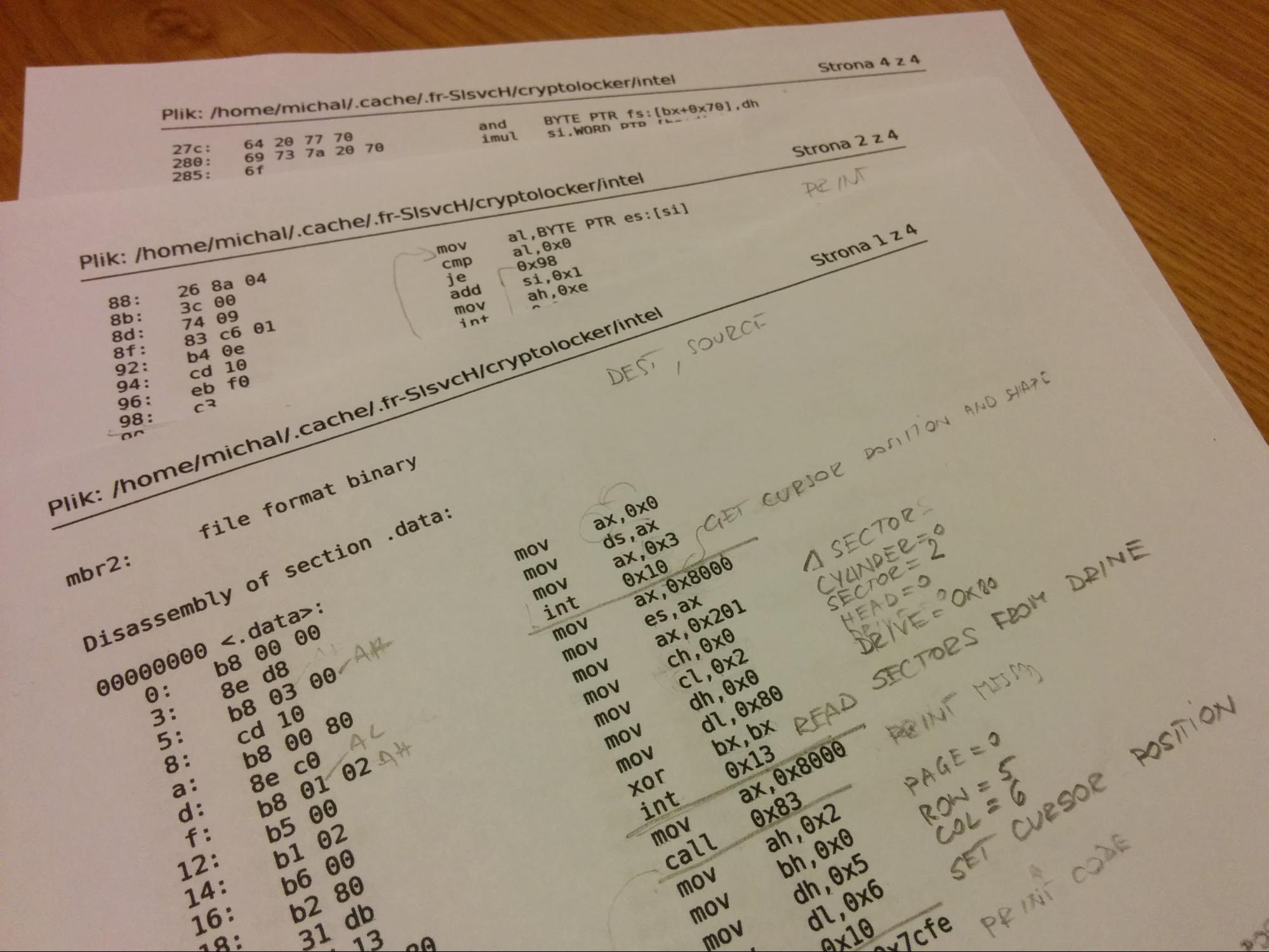
It was a hot summer evening back in August 2014. I was working on my master’s thesis project. The project was about building software controlling a group of mobile robots and at that time I was running some simulations.
The main part was running on a Linux machine, but the simulator had to be run on Windows, so I decided to put it in VMware virtual machine. Looking back, I must admit it was very overcomplicated, but I was still a student and I had a lot of free time.
…It’s time to ditch SMS-based 2 Factor Auth

Phone numbers are not reliable. Phone numbers can be hijacked. Phone numbers change.
Phone numbers stop working when you are traveling and not roaming. Phone numbers don’t work when you are using in-flight Wi-Fi. Phone numbers can stop receiving text messages/calls for a million of other reasons, effectively either (1) locking users out of an account or (2) compromising the account altogether.
…How I discovered Instagram’s upcoming video calling feature on iOS
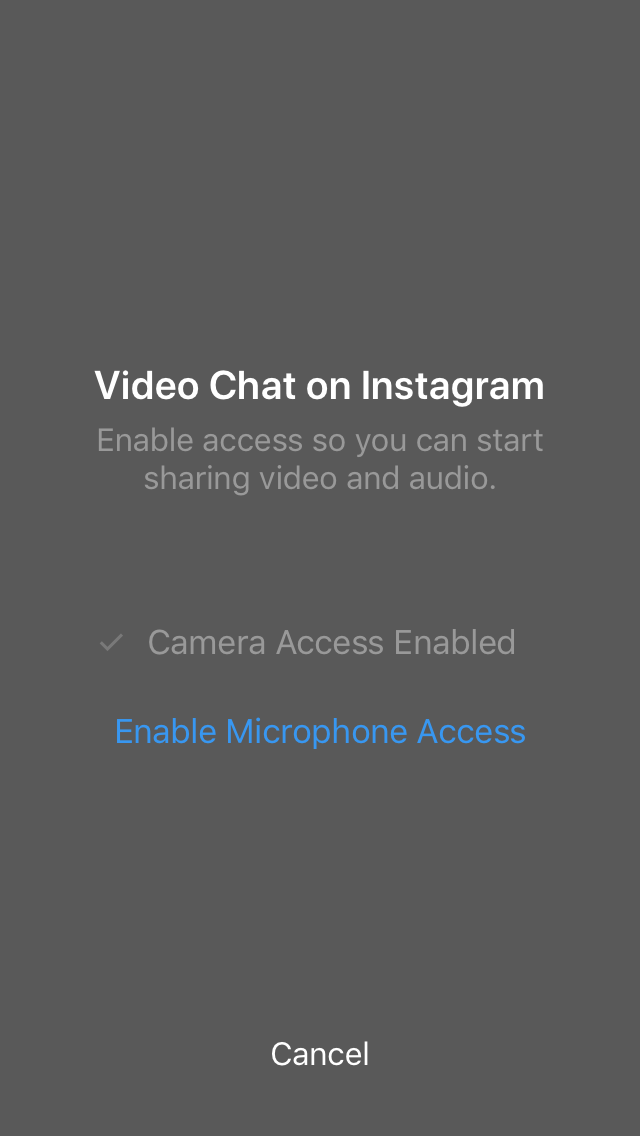
Yesterday I managed to grab some screenshots of a video calling UI on Instagram. This is the story of how that happened. I think the description of the process will be pretty useful to anyone who’s interested in reverse engineering to find hidden features.
Source: medium.com
…Why the roots of patent trolling may be in the patent office

In recent years, American companies have faced a growing threat from patent assertion entities derisively called ‘patent trolls.’ These often shadowy firms make money by threatening patent lawsuits rather than creating useful products. A recent study suggests that the roots of the patent trolling problem may lie with the US Patent and Trademark office—specifically with patent examiners who fail to thoroughly vet patent applications before approving them.
…Researchers Find 34,200 Vulnerable Ethereum Smart Contracts

A scan of nearly one million Ethereum smart contracts has identified 34,200 vulnerable contracts that can be exploited to steal Ether, and even freeze or delete assets in contracts the attackers don’t own.
Source: bleepingcomputer.com
…How Airlines don’t care about your privacy: Case Study Emirates.com
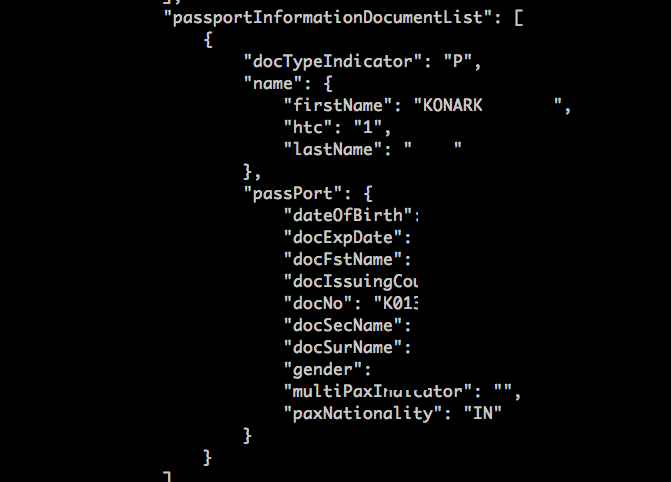
Now imagine this, I said “You try to check-in for your flight online, and see the error message — This booking does not exist. You try again, this surely is a mistake. Nope, still the same error message.
The call center person repeats the same words. This has to be a mistake! You check your email, and there it is — staring back at you — email confirmation of cancellation.
…