May. 8, 2018
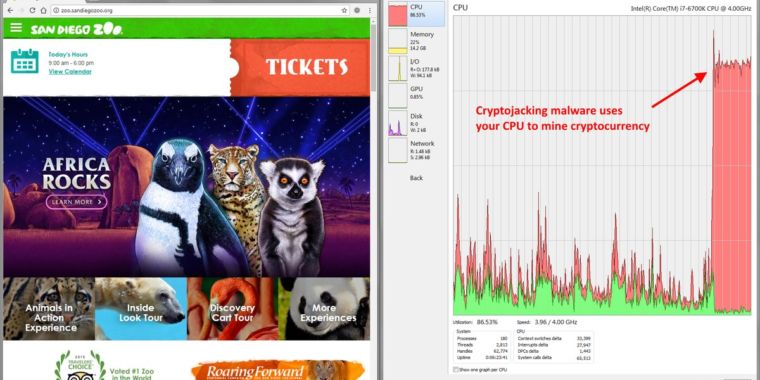
A mass hacking campaign that targets a critical vulnerability in the Drupal content management system has converted more than 400 government, corporate, and university websites into cryptocurrency mining platforms that surreptitiously drain visitors’ computers of electricity and computing resources, a security researcher said Monday. Sites that were hacked included those belonging to computer maker Lenovo, the University of California at Los Angeles, the US National Labor Relations Board, the Arizona Board of Behavioral Health Examiners, and the city of Marion, Ohio, Troy Mursch, an independent security researcher, told Ars on Monday. The Social Security Institute of the State of Mexico and Municipalities, the Turkish Revenue Administration, and Peru’s Project Improvement of Higher Education Quality were also affected.
May. 4, 2018

Kitty, a Monero cryptocurrency which utilizes open-source mining software for browsers, executes a bash script, kdrupal.php, which is written to an infected server disc. This then establishes a backdoor into an infected system separate from the Drupal vulnerability.
Source: zdnet.com
Apr. 29, 2018

Recently, further developments into other methods to achieve RCE were uncovered. Drupal released advisory SA-CORE-2018-004 with updated versions and patches to fix the newly identified flaws.
Source: trustwave.com
Apr. 27, 2018

The flaw exists in the Drupal core package in all supported versions of Drupal, eg. 7.x and 8.x releases. This vulnerability allows attackers to exploit Drupal powered sites from numerous attack vectors.
The end result being the site compromised as remote code can be executed, possibly giving unrestricted control to the hosting environment.
Source: drupal.sh
Mar. 29, 2018

All versions of the Drupal content management system are affected by a highly critical vulnerability that can be easily exploited to take complete control of affected websites in what may turn out to be Drupalgeddon 2.0.
Source: securityweek.com



