Jun. 29, 2018
PROPagate is a relatively new code injection technique discovered last November. Back then, a security researcher found that an attacker could abuse the SetWindowSubclass API, a function of the Windows operating system that manages GUIs, to load and execute malicious code inside the processes of legitimate apps. The infosec research community deemed the technique innovative, similar in creativity to the AtomBombing technique, albeit both different in their own right.
Jun. 29, 2018

An unknown hacker has temporarily taken control over the GitHub account of the Gentoo Linux organization and embedded malicious code inside the operating system’s distributions that would delete user files. Thankfully, the malicious code fails to trigger properly and users’ files remain safe. How the hacker gained access to Gentoo’s GitHub account still remains a mystery, but since announcing the hack late last night, the Gentoo team says it regained control over their account, albeit their profile remained offline at the time of this article’s publication.
May. 30, 2018

According to reporting of trusted third parties, HIDDEN COBRA actors have likely been using both Joanap and Brambul malware since at least 2009 to target multiple victims globally and in the United States—including the media, aerospace, financial, and critical infrastructure sectors. According to reporting of trusted third parties, HIDDEN COBRA actors have likely been using both Joanap and Brambul malware since at least 2009 to target multiple victims globally and in the United States—including the media, aerospace, financial, and critical infrastructure sectors. Users and administrators should review the information related to Joanap and Brambul from the Operation Blockbuster Destructive Malware Report [1] in conjunction with the IP addresses listed in the .csv
May. 25, 2018

To steal money from a victim’s account via the internet banking interface, typical banking malware will inject itself or its specialized banking module into the browser’s process address space. For many reasons, this is not an easy task – first of all, as mentioned before, the injection might be intercepted by a third-party security solution. The injected module also needs to match the bitness of the browser – a 32-bit module cannot be injected into a 64-bit browser process and vice versa.
May. 25, 2018

News of this group first surfaced after a report in December 2016, when Russian antivirus vendor Dr.Web disclosed that a mysterious threat actor had found a way to penetrate the supply-chain of several mobile carriers, infecting phones with malware. At the time, experts said they found malware in the firmware of at least 26 low-cost Android smartphone and tablets models. Once ousted, Dr.Web hoped crooks would pack up and move on to another operation.
May. 23, 2018

For several months, Talos has been working with public- and private-sector threat intelligence partners and law enforcement in researching an advanced, likely state-sponsored or state-affiliated actor’s widespread use of a sophisticated modular malware system we call ‘VPNFilter.’ We have not completed our research, but recent events have convinced us that the correct way forward is to now share our findings so that affected parties can take the appropriate action to defend themselves. In particular, the code of this malware overlaps with versions of the BlackEnergy malware — which was responsible for multiple large-scale attacks that targeted devices in Ukraine.
May. 21, 2018

We, as malware analysts, are always in need of new samples to analyze in order to learn, train or develop new techniques and defenses. One of the most common questions I get is “Where to find malware to analyze?” so I’m sharing here my private collection of repositories, databases and lists which I use onadaily basis.
Some of them are updated frequentlyandsome of them are not. The short description under each link wasn’t written by me, it was written by the owners of the repositories.
May. 21, 2018

In May 2017, one of the biggest facilitators of cybercrime, Scan4You, went offline after the two main suspects, were arrested in Latvia and extradited to the US by the Federal Bureau of Investigation (FBI). In May 2018, the case against the Scan4You’s operators concluded in a Virginia federal courtroom. Scan4You was set up in 2009 as an online service designed to help malware authors evade detection by security software.
May. 18, 2018
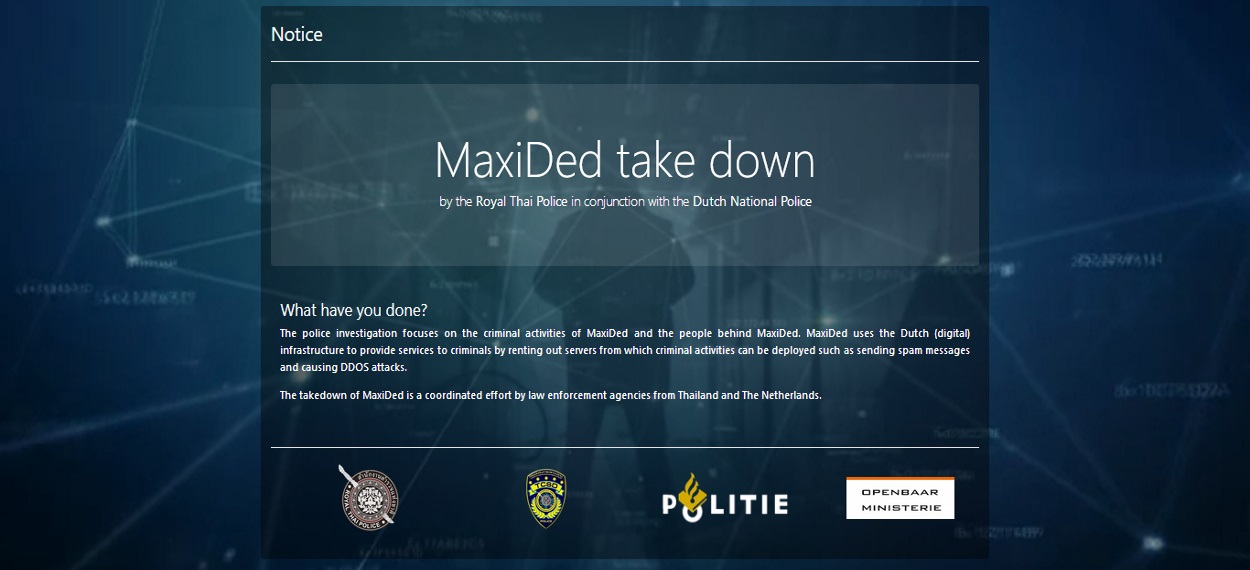
The name of the hosting provider is MaxiDed, a service that has operated since late 2008, but which became increasingly more aggressive with its marketing in the last two years when its ads became a common occurrence on cybercrime forums. According to an archived version of the site, the company offered dedicated servers, VPS, VPN, and server colocation services, claiming to host nearly 2,500 servers across 30 hosting providers in 82 countries. MaxiDed advertised itself as a bulletproof hosting provider, a term used to describe hosting companies that ignore reports of criminal activity or copyright infringement happening on their servers.
May. 18, 2018

A new form of cryptominer has been discovered which crashes systems the moment antivirus products attempt to remove the malware. The malware, dubbed WinstarNssmMiner by 360 Total Security researchers, has been used in half a million attempted attacks leveraged at PCs in only three days. On Wednesday, the cybersecurity firm said the cryptomining malware aims to infect PCs in order to steal processing power for the purpose of mining the Monero cryptocurrency.
May. 17, 2018
Most antivirus scanners play a classic cat and mouse game: They work by checking software against a frequently updated list of potential threats. In response, a whole industry has built up to help occlude and conceal hacking tools. That includes services that automate the process of checking all sorts of tools, from malware to malicious URLs, against dozens of defense scanners to see if they would get blocked.
May. 12, 2018

Oh, snap! Just because some packages are available to install directly from the Ubuntu Software Center doesn’t make them safe. This is proved by a recent discovery of malware in some snap packages from the Ubuntu Snaps Store.
At least two of the snap packages, 2048buntu and Hextris, uploaded to the Ubuntu Snaps Store by user Nicolas Tomb, contained malware. All packages by Nicolas have since been removed from the Ubuntu Snaps Store, ‘pending further investigations’.
May. 12, 2018

The researchers found evidence that the threat has been around since at least late 2014.TreasureHunt was firstdiscoveredby researchers at theSANS Institute who noticed the malware generating mutex names to evade detection. TreasureHunt enumerates the processes running on the infected systemsand implement memory scraping functions to extractcredit and debit card information. Stolen payment card data are sent to C&C servers throughHTTP POST requests.
May. 10, 2018

Shamoon, Black Energy, Destover, ExPetr/Not Petya and Olympic Destroyer: All of these wiper malwares, and others like them, have a singular purpose of destroying systems and/or data, usually causing great financial and reputational damage to victim companies. However, the threat actors behind this kind of code, whether they’re bent on sending a political message or simply wanting to cover their tracks after data exfiltration, have adopted various techniques to carry out those activities. Cisco Talos researcher Vitor Ventura, along with contributions from Martin Lee, noted in a report published on Tuesday, that malware with destructive payloads has been around since the early days of virus development.
May. 9, 2018

It is now proven that Electrum Pro steals wallet seeds on creation. Meaning that any coins stored in a wallet created with this tool are accessible to anyone with access to electrum(dot)com. If you mistakenly used this wallet, you should move your coins to a secure wallet as soon as possible.
The proof given is a step by step guide to decompiling the python based binary. The proof claims that within the binary, where the seeds are created, an additional step exists which uploads the seed to electrum(dot)com. The official website for the Electrum wallet is electrum.org, which we can be sure of due to its link on the external site bitcoin.org.
May. 4, 2018

Kitty, a Monero cryptocurrency which utilizes open-source mining software for browsers, executes a bash script, kdrupal.php, which is written to an infected server disc. This then establishes a backdoor into an infected system separate from the Drupal vulnerability.
Source: zdnet.com
May. 3, 2018

By taking thermal readings, the Remote Access Trojan (RAT), which has become a recent menace in India, attempts to find out whether or not VMs are being employed for the purpose of decompiling efforts and reverse engineering.
Source: zdnet.com
Apr. 27, 2018

The ShadowBrokers’ release of a trove of National Security Agency exploits last year appears to be the gift that keeps on giving, to the hacker community at least: A fresh malware that uses the EternalRomance tool has hit the scene, with Monero-mining as the stated goal. However, more damaging follow-on attacks are likely the endgame.
Source: threatpost.com
Apr. 27, 2018

Today, Cisco Talos is uncovering a new piece of malware, which has remained under the radar for the past two years while it continues to be developed. Several weeks ago, we identified the use of the latest version of this RAT (Remote Access Tool). In this article, we will discuss the technical capabilities, the evolution, development and potential attribution of what we are calling GravityRAT.
Apr. 24, 2018
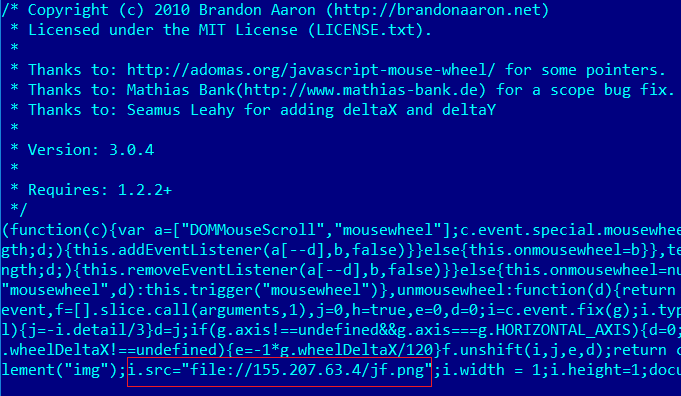
The researchers at CSE ZLab have spotted a new family of malware, tracked as Bandios spreading in the wild. The peculiarity of Bandios malware is the fact that this malware is in a rapid and constant evolution and development.
Source: securityaffairs.co



















