Mar. 15, 2018

Traffic distribution systems act as brokers that both buy and sell traffic from one site to another. They ad value by filtering traffic based on a user’s browser, IP address, geography anduser agent data. When a user clicks on a link that is part of a TDS chain they aresilently redirected to a malicious web pagebased on their profile.
TDS systems are notorious for aiding criminals in distributing web-based malware via exploit kits and fake downloads.
Mar. 14, 2018

Researchers at Kroll Cyber Security first identified PinkKite in 2017 during a nine-month investigation into a large POS malware campaign that ended in December. The campaign is believed to be the first instance of PinkKite identified, according to researchers Courtney Dayter and Matt Bromiley, who presented their findings at Kaspersky Lab’s Security Analyst Summit on Friday.
Source: threatpost.com
Mar. 14, 2018

In today’s day and age, when you ask a security expert about some basic tips to stay safe on the web, one of the most important things he will probably tell you is to download software only from legitimate sources. Sometimes even such a basic and obvious advice might not save you from malware encounters. We found three trojanized applications hosted on download.cnet.com, which is one of the most popular software hosting sites in the world as its Alexa rank (163th) shows.
Mar. 12, 2018

Around the globe, the region where criminals had achieved expertise and have become highly professionals is Latin America. As a resulting of this criminal union to steal money directly from ATM, criminals and cybercriminals from Latin America have been developing brand new zero-day techniques and tools that are not found in any other place in the world.
Source: securityaffairs.co
Mar. 10, 2018
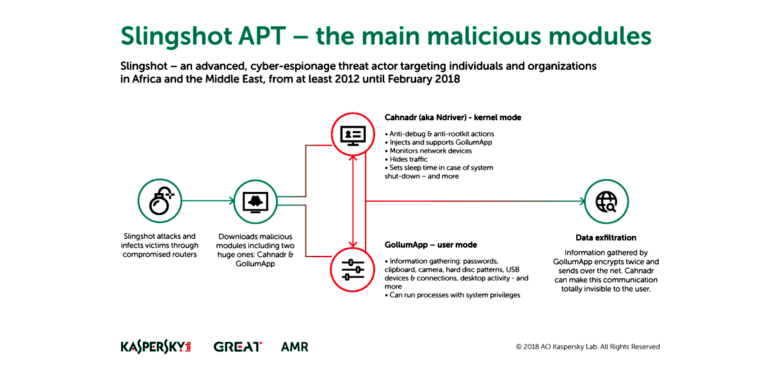
Slingshot—which gets its name from text found inside some of the recovered malware samples—is among the most advanced attack platforms ever discovered, which means it was likely developed on behalf of a well-resourced country, researchers with Moscow-based Kaspersky Lab reported Friday. The sophistication of the malware rivals that of Regin—the advanced backdoor that infected Belgian telecom Belgacom and other high-profile targets for years—and Project Sauron, a separate piece of malware suspected of being developed by a nation-state that also remained hidden for years.
Mar. 10, 2018
Researchers Uncovers a Previously Undetected Highly-Skilled APT Hacking Group Operating Covertly Since 2012, Infecting Mikrotik Routers to Implant Advance ‘Slingshot’ Spying Malware
Source: thehackernews.com
Mar. 10, 2018
Governments and Internet Service Providers in Turkey, Syria and Egypt Caught Infecting Citizens with Cryptocurrency Mining and surveillance malware.
Source: thehackernews.com
Mar. 8, 2018

Two days ago, Microsoft encountered a rapidly spreading cryptocurrency-mining malware that infected almost 500,000 computers within just 12 hours and successfully blocked it to a large extent. Dubbed Dofoil, aka Smoke Loader, the malware was found dropping a cryptocurrency miner program as payload on infected Windows computers that mines Electroneum coins, yet another cryptocurrency, for attackers using victims’ CPUs.
Mar. 7, 2018

Malware was discovered on point of sales systems at more than 160 Applebee’s restaurants, exposing credit card information from unknowing diners.
Source: threatpost.com
Mar. 5, 2018
One of the coolest things about Chrome is the silent, automatic updates that always ensure that users are always running the latest version. While Chrome itself is updated automatically by Google, that update process also includes Chrome’s extensions, which are updated by the extension owners. This means that it’s up to the user to decide if the owner of an extension is trustworthy or not, since you are basically giving them permission to push new code out to your browser whenever they feel like it.
Mar. 1, 2018

The latest zero-day threat to be discovered by Wandera’s mobile threat research team is RedDrop, a family of mobile malware inflicting financial cost and critical data loss on infected devices.
Source: wandera.com
Mar. 1, 2018

According to cybersecurity firm Morphisec, cybercriminals are blasting spam messages that urge recipients to click a link to download a Word document. And when a victim opens the document and enables macros, malware attempts to exploit an Adobe Flash Player bug (CVE-2018-4878) patched by Adobe earlier this month.
Victims who fall for the ploy could ultimately hand over control of their systems to an attacker, according to researchers.
Mar. 1, 2018

Talos has identified two different versions of a RAT, otherwise known as a remote access trojan, that has been written entirely in Python and is wrapped into a standalone executable. The RAT is impacting users of a Brazilian public sector management school.
Source: talosintelligence.com
Mar. 1, 2018

Wandera, a mobile security firm which spotted weaknesses in the CBS Sports app and mobile site back in 2016, uncovered the malware when a user clicked on an ad for the Chinese search engine Baidu. Their action redirected them to huxiawang[dot]cn, a distribution site which contains landing pages encouraging users to download one of 53 apps tainted by RedDrop. Those affected programs claim to help users learn a new language or dive into space exploration, for example, with engaging functionality.
Mar. 1, 2018
A deep analysis of the Mobef ransomware revealed that it implements a number of functionalities, such as the capability to encrypt files, not only on the local drive but also on removable drives and network shares.
Source: securityaffairs.co














