May. 21, 2018

We, as malware analysts, are always in need of new samples to analyze in order to learn, train or develop new techniques and defenses. One of the most common questions I get is “Where to find malware to analyze?” so I’m sharing here my private collection of repositories, databases and lists which I use onadaily basis.
Some of them are updated frequentlyandsome of them are not. The short description under each link wasn’t written by me, it was written by the owners of the repositories.
May. 10, 2018

Shamoon, Black Energy, Destover, ExPetr/Not Petya and Olympic Destroyer: All of these wiper malwares, and others like them, have a singular purpose of destroying systems and/or data, usually causing great financial and reputational damage to victim companies. However, the threat actors behind this kind of code, whether they’re bent on sending a political message or simply wanting to cover their tracks after data exfiltration, have adopted various techniques to carry out those activities. Cisco Talos researcher Vitor Ventura, along with contributions from Martin Lee, noted in a report published on Tuesday, that malware with destructive payloads has been around since the early days of virus development.
May. 3, 2018
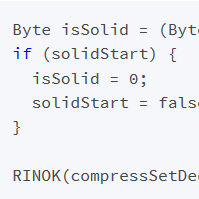
Very abstractly, the bug can be described as follows: The initialization of some member data structures of the RAR decoder classes relies on the RAR handler to configure the decoder correctly before decoding something. Unfortunately, the RAR handler fails to sanitize its input data and passes the incorrect configuration into the decoder, causing usage of uninitialized memory.
Source: landave.io
May. 1, 2018

This post outlines and presents the rediscovery, vulnerability analysis and exploitation of a zero-day vulnerability that was originally discovered and exploited by the CIA’s ‘Engineering Development Group’; remotely targeting MikroTik’s RouterOS embedded operating system that was discovered during the ‘Vault 7’ leak via WikiLeaks in March of 2017.
Source: seekintoo.com
Apr. 29, 2018

The Zebrocy family consists of three components. In the order of deployment these are a Delphi downloader, an AutoIt downloader and a Delphi backdoor. Figure 1 shows the relationship between these components.
In this article we describe this family and how it can coexist with the older Seduploader reconnaissance tools. We will talk about some similarities to and differences from Downdelph at the end.
Apr. 24, 2018
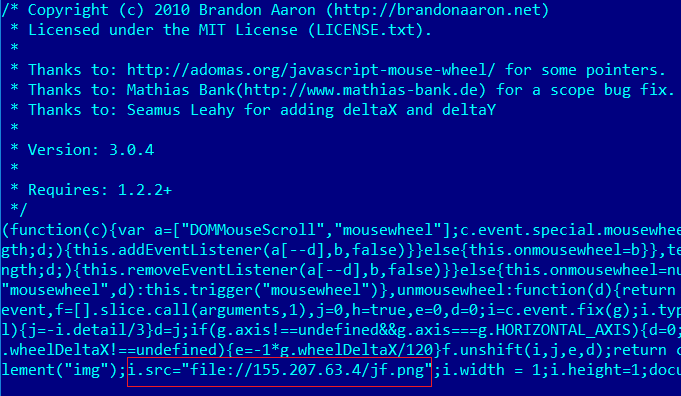
The researchers at CSE ZLab have spotted a new family of malware, tracked as Bandios spreading in the wild. The peculiarity of Bandios malware is the fact that this malware is in a rapid and constant evolution and development.
Source: securityaffairs.co
Mar. 7, 2018

The number of Flash Player exploits has recently declined, due to Adobe’s introduction of various measures to strengthen Flash’s security. Occasionally, however, an exploit still arises. On January 31, Kr-Cert reported a zero-day vulnerability, identified as CVE-2018-4878, being exploited in the field.
(Adobe has released an update to fix this flaw.) We analyzed this vulnerability and found that it bypassed the byte array mitigation feature that was introduced to prevent “length corruption” attacks in Flash. This post will focus on how the exploit bypasses the length checks.
Mar. 7, 2018

A large number of banks, credit unions and other financial institutions just pushed customers onto new e-banking platforms that asked them to reset their account passwords by entering a username plus some other static identifier — such as the first six digits of their Social Security number (SSN), or a mix of partial SSN, date of birth and surname. Here’s a closer look at what may be going on (spoiler: small, regional banks and credit unions have grown far too reliant on the whims of just a few major online banking platform providers).
Mar. 6, 2018

There have been lots of reasons to be concerned about how easily someone with the right tools and knowledge could do very bad things with cellular communications networks. And while none of them have necessarily been to the level of some of the fictional stunts pulled off on television (see Mr. Robot), new research shows that things are even worse than they appear—and in many cases, that’s because of how carriers have implemented cellular standards.
Mar. 3, 2018

IOTA is a cryptocurrency that’s been around since 2014 and is designed for micro-transactions between machines in the Internet of Things. IOTA is the tenth-largest cryptocurrency with a roughly $5 billion market cap. It doesn’t use a standard blockchain like most cryptocurrencies, but instead uses a Directed Acylic Graph (DAG) it calls “the Tangle” among other attempts at innovation.
For example, IOTA infamously used an in-house algorithm called Curl instead of the well-studied algorithms that underprin other digital coins.









