May. 30, 2018
Using sonic and ultrasonic soundwaves as a weapon, researchers can disrupt the read, write and storage functions of a hard disk drive (HDD). The method can also be used to crash the host operating system, and in some cases damage targeted drives. Researchers said the attack can be performed by “nearby emitters” that target a computer’s HDD; so, the attacks could be performed by an adversary using inexpensive off-the-shelf speakers or could also be carried out via laptop or desktop speakers.
May. 30, 2018

The Git community has disclosed an industry-wide security vulnerability in Git that can lead to arbitrary code execution when a user operates in a malicious repository. This vulnerability has been assigned CVE 2018-11235 by Mitre, the organization that assigns unique numbers to track security vulnerabilities in software. Git 2.17.1 and Git for Windows 2.17.1 (2) were released today and include this fix.
May. 29, 2018

Security researchers have discovered a series of new vulnerabilities in EOS blockchain platform, one of which could allow remote hackers to take complete control over the node servers running the critical blockchain-based applications. EOS is an open source smart contract platform, known as ‘Blockchain 3.0,’ that allows developers to build decentralized applications over blockchain infrastructure, just like Ethereum. Discovered by Chinese security researchers at Qihoo 360—Yuki Chen of Vulcan team and Zhiniang Peng of Core security team—the vulnerability is a buffer out-of-bounds write issue which resides in the function used by nodes server to parse contracts.
May. 28, 2018
German researchers reckon they have devised a method to thwart the security mechanisms AMD’s Epyc server chips use to automatically encrypt virtual machines in memory. So much so, they said they can exfiltrate plaintext data from an encrypted guest via a hijacked hypervisor and simple HTTP requests to a web server running in a second guest on the same machine. AMD’s data-center processors, as well as its Ryzen Pro line, support what’s called Secure Encrypted Virtualization.
May. 25, 2018
The Z-Wave wireless communications protocol used for some IoT/smart devices is vulnerable to a downgrade attack that can allow a malicious party to intercept and tamper with traffic between smart devices. The attack —codenamed Z-Shave— relies on tricking two smart devices that are pairing into thinking one of them does not support the newer S-Wave S2 security features, forcing both to use the older S0 security standard. An attacker that can trick a smart device into pairing with another device, a PC, or a smartphone app via the older S0 standard, can later decrypt all traffic exchanged between the two because the decryption key is widely known.
May. 22, 2018

A security hole in a Comcast service-activation website allowed anyone to obtain a customer’s Wi-Fi network name and password by entering the customer’s account number and a partial street address, ZDNet reported yesterday. The problem would have let attackers ‘rename Wi-Fi network names and passwords, temporarily locking users out’ of their home networks, ZDNet wrote. Obviously, an attacker could also use a Wi-Fi network name and password to log into an unsuspecting Comcast customer’s home network.
May. 22, 2018
Both Google and Microsoft researchers discovered the bug independently. The bugs work similarly to the Meltdown and Spectre bugs, a reason why they were classified as ‘variant 3a’ and ‘variant 4’ instead of separate vulnerabilities altogether. Variant 3a is a variation of the Meltdown flaw, while Variant 4 is a new Spectre-like attack.
The most important of these two is Variant 4. Both bugs occur for the same reason —speculative execution— a feature found in all modern CPUs that has the role of improving performance by computing operations in advance and later discarding unneeded data. The difference is that Variant 4 affects a different part of the speculative execution process —the data inside the ‘store buffer’ inside a CPU’s cache.
May. 18, 2018

Keeper, a password manager maker that recently and controversially sued a reporter, has fixed a bug that a security researcher claimed could have allowed access to a user’s private data. The bug — which the company confirmed and has since fixed — filed anonymously to a public security disclosure list, detailed how anyone controlling Keeper’s API server could gain access to the decryption key to a user’s vault of passwords and other sensitive information. The researcher found the issue in the company’s Python-powered script called Keeper Commander, which allows users to rotate passwords, eliminating the need for hardcoded passwords in software and systems.
May. 18, 2018

Car hacking has become a major focus in the security community in recent years, as more vehicles are hooked up to the cellular internet. But while convenient to control your car from your phone, it’s also opened up new points for attack — which could have real-world consequences. You might not even realize you’re a Calamp user.
Many apps, including the vehicle tracking app Viper SmartStart, which lets users locate, start, and control their car from their phone, connects to the outside world using a Calamp modem to its cloud-based servers. The researchers found that the Viper mobile app, while secure, was connecting to two different servers — one used by Viper, and another run by Calamp. Using the same credentials as the app, the researchers were also able to log in and gain complete access to the Calamp server, the researchers said in their write-up.
May. 18, 2018

As tens of millions of happy delighted owners know, Siri, Alexa, Cortana and Google, will do lots of useful things in response to voice commands. But what if an attacker could find a way to tell them to do something their owners would rather they didn’t? Researchers have been probing this possibility for a few years and now, according to a New York Times article, researchers at the University of California, Berkeley have shown how it could happen.
May. 18, 2018

Cisco released 16 security advisories yesterday, including alerts for three vulnerabilities rated ‘Critical’ and which received a maximum of 10 out of 10 on the CVSSv3 severity score. The three vulnerabilities include a backdoor account and two bypasses of the authentication system for Cisco Digital Network Architecture (DNA) Center. The Cisco DNA Center is a piece of software that’s aimed at enterprise clients and which provides a central system for designing and deploying device configurations (aka provisioning) across a large network.
May. 17, 2018

Researchers have revealed new malware designed to collect information from messaging service Telegram. On Wednesday, Cisco Talos researchers Vitor Ventura and Azim Khodjibaev said that over the past six weeks, the team has monitored the emergence of what has been called Telegrab. This malware has been designed to collect cache and key files from Telegram, an end-to-end encrypted messaging service.
The malicious code was first spotted in the wild on 4 April 2018, and a second variant emerged only six days later. While the first version of Telegrab only stole text files, browser credentials, and cookies, the second also added new functionality which allowed the malware to collect data from Telegram’s desktop cache — alongside Steam login credentials — in order to hijack active Telegram sessions. The malware impacts the desktop version of Telegram.
May. 17, 2018

A command injection bug in Red Hat’s DHCP client could allow an attacker to run any command on your computer. As root. RedHat Linux, together with its stablemates Fedora and CentOS, just patched a serious security bug.
RedHat-based Linux distros include a dhclient script as part of their NetworkManager package – until the latest NetworkManager security patch, this script could be tricked into running text provided in a DHCP reply as if it were a system command of its own. Technically, this sort of bug is known as a command injection vulnerability, because it allows you to sneak in a command where you are supposed to supply data. It’s also a root RCE, short for remote code execution, because you don’t need to login first, and because you get to run the remotely supplied code as a system administrator.
May. 15, 2018

The new bunch of Spectre-like flaws revealed last week won’t be patched for at least 12 days. German outlet Heise, which broke news of the eight Spectre-like vulnerabilities last week has now reported that Intel wants disclosure of the flaws delayed until at least May 21. Last week, Heise noted that one participant in the planned coordinated release would include a Google Project Zero disclosure, which as far as The Register can discern has not yet happened.
May. 14, 2018

The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs. To create these exfiltration channels, the attacker first needs access to the encrypted emails, for example, by eavesdropping on network traffic, compromising email accounts, email servers, backup systems or client computers.
May. 14, 2018
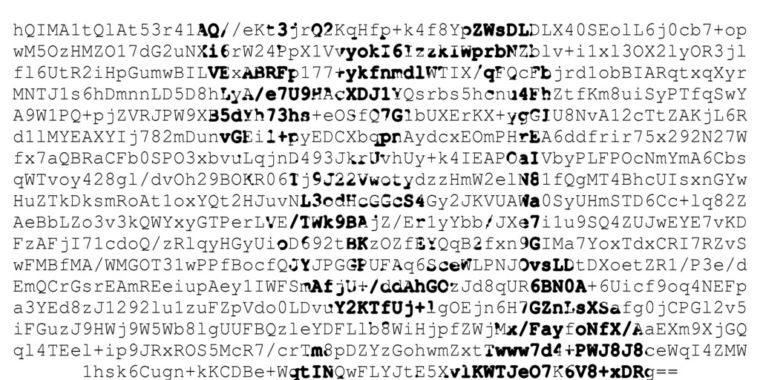
The Internet’s two most widely used methods for encrypting e-mail–PGP and S/Mime–are vulnerable to hacks that can reveal the plaintext of encrypted messages, a researcher warned late Sunday night. He went on to say there are no reliable fixes and to advise anyone who uses either encryption standard for sensitive communications to remove them immediately from e-mail clients. Little is publicly known about the flaws at the moment.
May. 12, 2018

A few weeks ago, I came across a vulnerability that affected all current versions of Electron at the time (< 1.7.13, < 1.8.4, and < 2.0.0-beta.3). The vulnerability allowed nodeIntegration to be re-enabled, leading to the potential for remote code execution. If you’re unfamiliar with Electron, it is a popular framework that allows you to create cross-platform desktop applications using HTML, CSS, and JavaScript.
Some popular applications such as Slack, Discord, Signal, Atom, Visual Studio Code, and Github Desktop are all built using the Electron framework. You can find a list of applications built with Electron here. Electron applications are essentially web apps, which means they’re susceptible to cross-site scripting attacks through failure to correctly sanitize user-supplied input.
May. 9, 2018

To cut a long story short, Dave didn’t just figure out a vulnerability that was theoretically exploitable, he also created a proof-of-concept (PoC) exploit that showed how to create a RAR file that, when opened, would sneakily and unexpectedy launch the Calculator app. Generally speaking, if a PoC can pop up CALC.EXE without asking, it could be modified to run any other command, including malware, invisibly to the user.
May. 6, 2018

The US Food and Drug Administration (FDA) last month approved a firmware patch for pacemakers made by Abbott’s (formerly St Jude Medical) that are vulnerable to cybersecurity attacks and which are at risk of sudden battery loss.
Source: sophos.com
May. 4, 2018
If you use the same password for multiple services (please don’t do that), or have your Twitter account connected to other login credentials online, you should change these passwords immediately. The logs that exposed users’ passwords were internal, but if anyone could see them at all the safest thing to do is change them.
Source: vice.com



















