Mar. 27, 2018

The Spectre attacks, published earlier this year, take advantage of the speculative execution features of modern processors to leak sensitive information. The new attack, named BranchScope by the researchers, shares some similarity with variant 2 of the Spectre attack, as both BranchScope and Spectre 2 take advantage of the behavior of the processor’s branch predictor.
Source: arstechnica.com
Mar. 16, 2018
The only tools you need are at least one finger–a nose will work too–to type the brand and model of whatever device you want to hack, and a connected web browser. Put that information into a Google search box and, within a few minutes, you will find a site or a forum post somewhere describing how to enter into that device using the manufacturer’s default administration user name and password. Any pedophile, thief, ex-spouse, or regular Peeping Tom can use this information to gain access to any of these devices installed in your home.
Mar. 14, 2018

On a Samba 4 AD DC the LDAP server in all versions of Samba from 4.0.0 onwards incorrectly validates permissions to modify passwords over LDAP allowing authenticated users to change any other users’ passwords, including administrative users and privileged service accounts (eg Domain Controllers).
Source: samba.org
Mar. 13, 2018

The Meltdown and Spectre vulnerabilities in modern CPUs from Intel/AMD/ARM revealed surprising attack vectors in computing. Everything from low level Operating System Kernel components to JavaScript running in Billions of browsers could be exploited by using Spectre variants 1 and 2.
Source: react-etc.net
Mar. 13, 2018

Security researchers warned Tuesday that some AMD processors contain ‘critical’ vulnerabilities, as well as backdoors that the researchers claimed were put in place in systems outsourced to a third-party manufacturer by AMD. The 13 different vulnerabilities were found in AMD Secure Processor, which is used in the company’s EPYC and Ryzen CPUs. These bugs would allow hackers who have already gained a foothold into a computer to install persistent and hard-to-detect malware, researchers warned.
Mar. 13, 2018

A critical vulnerability has been discovered in Credential Security Support Provider protocol (CredSSP) that affects all versions of Windows to date and could allow remote attackers to exploit RDP and WinRM to steal data and run malicious code. CredSSP protocol has been designed to be used by RDP (Remote Desktop Protocol) and Windows Remote Management (WinRM) that takes care of securely forwarding credentials encrypted from the Windows client to the target servers for remote authentication. Discovered by researchers at Cybersecurity firm Preempt Security, the issue (CVE-2018-0886) is a logical cryptographic flaw in CredSSP that can be exploited by a man-in-the-middle attacker with Wi-Fi or physical access to the network to steal session authentication data and perform a Remote Procedure Call attack.
Mar. 13, 2018

Through the advent of Meltdown and Spectre, there is a heightened element of nervousness around potential security flaws in modern high-performance processors, especially those that deal with the core and critical components of company business and international infrastructure. Today, CTS-Labs, a security company based in Israel, has published a whitepaper identifying four classes of potential vulnerabilities of the Ryzen, EPYC, Ryzen Pro, and Ryzen Mobile processor lines. AMD is in the process of responding to the claims, but was only given 24 hours of notice rather than the typical 90 days for standard vulnerability disclosure.
Mar. 13, 2018

The interesting aspect about social engineering is that it capitalizes on the user’s poor decision to execute code that would have been much harder to inject, or that could have been caught by security solutions otherwise. In other words, letting victims do the work remains an effective means for attackers to compromise endpoints.
Source: malwarebytes.com
Mar. 13, 2018

Some readers may remember our Analysis of .git folders in the Alexa Top 1M. WIth our tools we were able to discover and retrieve (hidden) directories and files (even without directory listing). We developed a similar approach of uncovering hidden files again, but this time with the help of .DS_Store files. In this blogpost we will share the methodology, the resulting security implications as well as our results from scanning the Alexa Top 1M and how we could have obtained sensitive files from several websites.
Mar. 13, 2018

Microarchitectural attacks can also be implemented in JavaScript, exploiting properties inherent to the design of the microarchitecture, such as timing differences in memory accesses. Although JavaScript code runs in a sandbox, Oren et al. demonstrated that it is possible to mount cache attacks in JavaScript. Since their work, a series of microarchitectural attacks have been mounted from websites, such as page deduplication attacks, Rowhammer attacks, ASLR bypasses, and DRAM addressing attacks.
Mar. 13, 2018
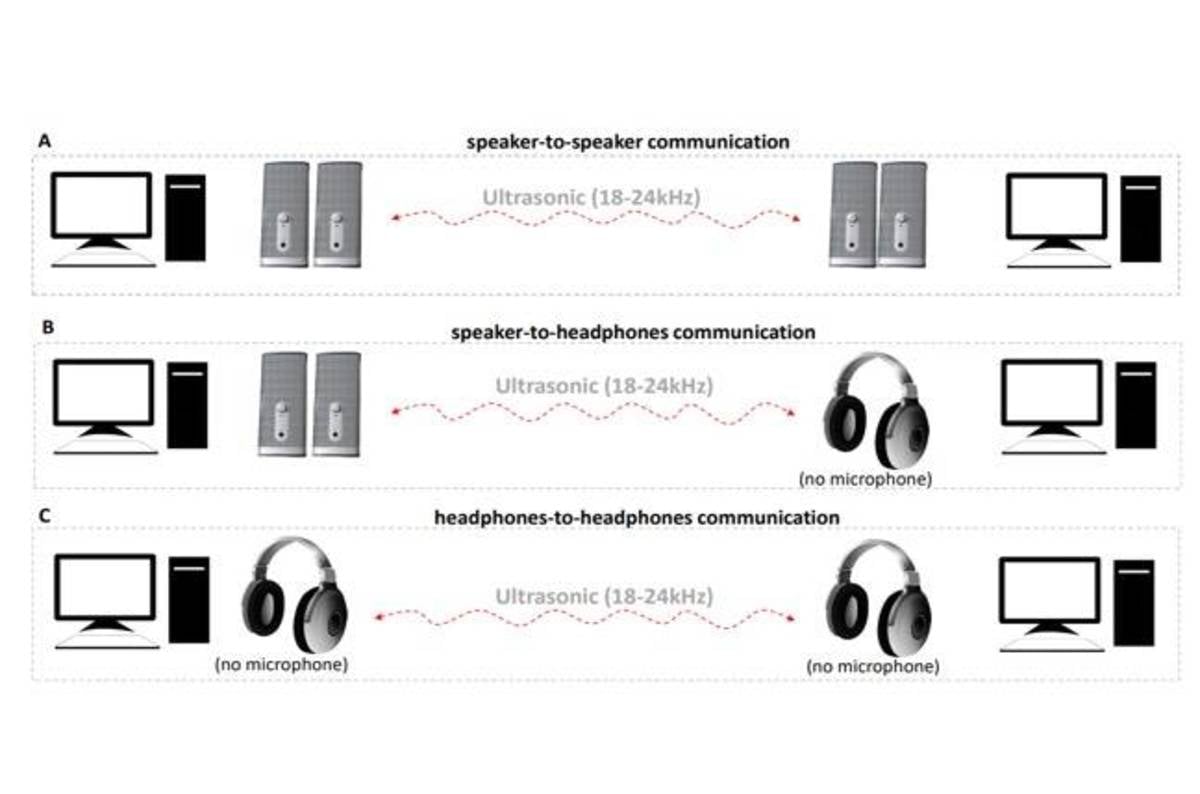
In an academic paper published on Friday through preprint service ArXiv, researchers from Israel’s Ben-Gurion University of the Negev describe a novel data exfiltration technique that allows the transmission and reception of data – in the form of inaudible ultrasonic sound waves – between two computers in the same room without microphones.
Source: co.uk
Mar. 13, 2018
The team of security researchers—who last month demonstrated how attackers could steal data from air-gapped computers protected inside a Faraday cage—are back with its new research showing how two (or more) air-gapped PCs placed in the same room can covertly exchange data via ultrasonic waves. Air-gapped computers are believed to be the most secure setup wherein the systems remain isolated from the Internet and local networks, requiring physical access to access data via a USB flash drive or other removable media. Dubbed MOSQUITO, the new technique, discovered by a team of researchers at Israel’s Ben Gurion University, works by reversing connected speakers (passive speakers, headphones, or earphones) into microphones by exploiting a specific audio chip feature.
Mar. 12, 2018
In their March 9 paper, “Robots want bitcoins too,” IOActive security researches Lucas Apa and Cesar Cerrudo successfully created ransomware that could be used to compromise SoftBank Robotics’ NAO robot. Unlike traditional computer ransomware which threatens customers by encrypting their personal information, in the situation presented by the researches, companies that rely on these robots for service would be forced to make a decision: pay the ransom or cease business.
Mar. 12, 2018

If you’re using JavaScript on the server side (node.js), then you’ll want to understand the class of vulnerabilities described in this paper. JavaScript on the server side doesn’t enjoy some of the same protections as JavaScript running in a browser. In particular, Node.js modules can interact freely with the operating system without the benefit of a security sandbox.
The bottom line is this:
Mar. 12, 2018

The researchers at Kaspersky Lab ICS CERT decided to check the popular smart camera to see how well protected it is against cyber abuses. This model has a rich feature list, compares favorably to regular webcams and can be used as a baby monitor, a component in a home security system or as part of a monitoring system.
Source: securelist.com
Mar. 11, 2018

There is a weakness common to any software letting you protect a piece of data with a password: how does that password translate into an encryption key? If that conversion is a fast one, then you better don’t expect the encryption to hold. Somebody who gets hold of that encrypted data will try to guess the password you used to protect it.
Mar. 10, 2018
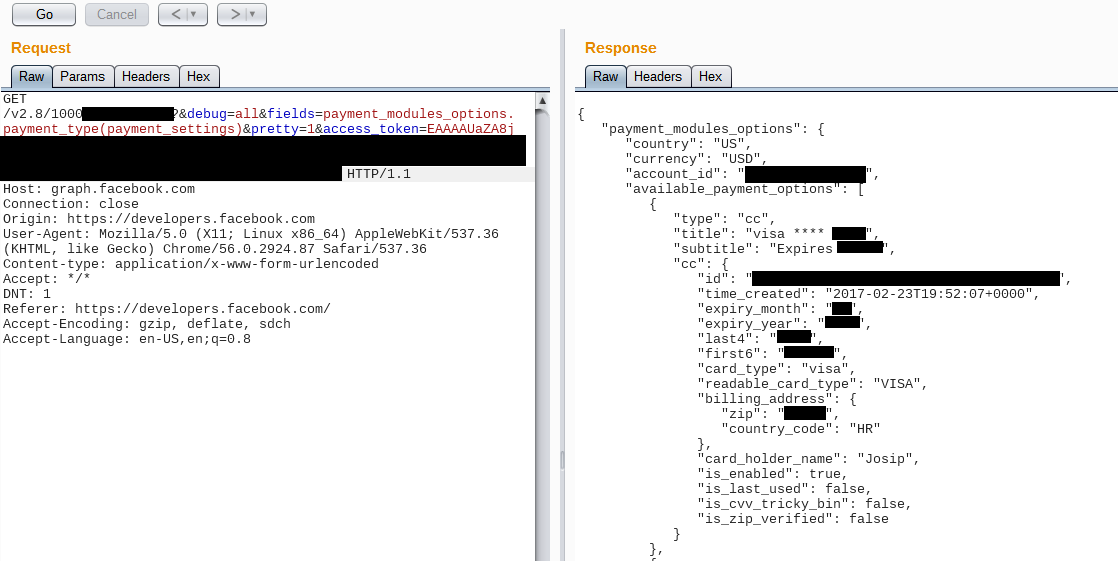
Facebook has a GraphQL endpoint which can only be used by some of their own first-party applications. Generally, you need a user (or page) access_token to query the GraphQL endpoint.
I have decided to try using Facebook for Android application’s client token, but the endpoint returned an error message:
Source: josipfranjkovic.com
Mar. 8, 2018

Multiple vulnerabilities have been discovered in PHP, the most severe of which could allow an attacker to execute arbitrary code. PHP is a programming language originally designed for use in web-based applications with HTML content. PHP supports a wide variety of platforms and is used by numerous web-based software applications.
Successfully exploiting the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the affected application. Depending on the privileges associated with the application, an attacker could install programs; view, change, or delete data; or create new accounts with full user rights. Failed exploitation could result in a denial-of-service condition.
Mar. 7, 2018

We reported an overflow vulnerability in the base64 decode function of Exim on 5 February, 2018, identified as CVE-2018-6789. This bug exists since the first commit of exim, hence ALL versions are affected. According to our research, it can be leveraged to gain Pre-auth Remote Code Execution and at least 400k servers are at risk.
Patched version 4.90.1 is already released and we suggest to upgrade exim immediately.
Mar. 7, 2018

A critical remote code vulnerability in the Exim mail transfer agent (MTA), tracked as CVE-2018-6789, affects most of the email servers online. It has been estimated that as in March 2017, the total number of Internet’s email servers running Exim was over 560,000, that corresponds to 56% of all Mail (MX) Server online.
Source: securityaffairs.co



















