Cyber security news and services
Researchers Discover New Ways to Hack WPA3 Protected WiFi Passwords

The same team of cybersecurity researchers who discovered several severe vulnerabilities, collectively dubbed as Dragonblood, in the newly launched WPA3 WiFi security standard few months ago has now uncovered two more flaws that could allow attackers to hack WiFi passwords.
Source: thehackernews.com
…5G Is Here—and Still Vulnerable to Stingray Surveillance

At the Black Hat security conference in Las Vegas next week, a group of network communication security researchers will present findings on flaws in the 5G protections meant to thwart the surveillance devices known as stingrays. Also called ‘IMSI catchers’ after the international mobile subscriber identity number attached to every cell phone, stingrays masquerade as legitimate cell towers. Once they trick a device into connecting to it, a stingray uses the IMSI or other identifiers to track the device, and even listen in on phone calls.
…Unplugging From Digital Controls to Safeguard Power Grids

Late last week, the U.S. House of Representatives passed legislation to mandate federal research on a radically ‘retro’approach to protect power grids from cyber attack: unplugging or otherwise isolating the most criticalequipment from grid operators’ digital control systems. Angus King, an independent senator from Maine whose identical bill passedthe Senate last month, says such a managed retreat from networked controls may berequired to thwart the grid’s most sophisticated online adversaries. Grid cyber experts say the Securing Energy Infrastructure Act moving through Congress isa particular testament toMichael Assante, a gifted and passionate cybersecurity expert whodied earlier this monthfrom leukaemia at the age of 48.
…Cybersecurity in the Automotive Industry

Forescout estimates that ‘software in modern cars exceeds 100 million lines of code’ — 15 times greater than in avionics software. That means that hackers have numerous points of entry, whether it’s through mobile apps, cell phone networks, internet access, the vehicle’s Controller Area Network (CAN) bus, or even the onboard diagnostics port. A 2019 Synopsys and SAE study showed that 84% of surveyed automotive professionals worry their current cybersecurity programs aren’t keeping up with the technology they support.
…Zoncolan: How Facebook uses static analysis to detect and prevent security issues
Facebook’s web codebase currently contains millions of lines of Hack code. To handle the sheer volume of code, we build sophisticated systems and tools to augment the comprehensive reviews our security engineers conduct. Today, we are sharing the details of one of those tools, called Zoncolan, for the first time.
Zoncolan helps security engineers scale their work by using static analysis to automatically examine our code and detect potentially dangerous security or privacy issues.
…Amazon allegedly scammed out of $370K by 22-year-old’s return shipments of dirt

James Gilbert Kwarteng, of Palma de Mallorca, Spain, allegedly swindled Amazon by filling up the ordered items’ boxes with dirt and registering with the exact weight of the product. He would then receive a refund from Amazon and sell the original item, according toEl EspañolandEl Diario de Mallorca. The return packages would end up sitting around in Amazon’s warehouses where they aren’t checked often.
…A Technical Analysis of the Capital One Hack

The recent disclosure of yet another cloud security misconfiguration leading to the loss of sensitive personal information made the headlines this past week. This particular incident came with a bit more information from the indictment of the accused party, allowing us to piece together the revealed data and take an educated guess as to what may have transpired leading up to the loss of over 100 million credit card applications and 100 thousand social security numbers. At the root of the hack lies a common refrain: the misconfiguration of cloud infrastructure resources allowed an unauthorized user to elevate her privileges and compromise sensitive documents.
…The Technical Side of the Capital One AWS Security Breach

On July 19th, 2019 Capital One got the red flag that every modern company hopes to avoid – their data had been breached. Over 106 million people affected.
140,000 Social Security numbers. 80,000 bank account numbers. 1,000,000 Social Insurance Numbers.
Pretty messy right? Unfortunately, the 19th wasn’t when the breach occurred.
It turns out that Paige Thompson, aka Erratic, had done the deed between March 22nd and March 23rd 2019.
…Capital One Data Theft Impacts 106M People
On July 29, FBI agents arrested Paige A. Thompsonon suspicion of downloading nearly 30 GB of Capital One credit application data from a rented cloud data server. Capital One said the incident affected approximately 100 million people in the United States and six million in Canada. That data included approximately 140,000 Social Security numbers and approximately 80,000 bank account numbers on U.S. consumers, and roughly 1 million Social Insurance Numbers (SINs) for Canadian credit card customers.
…Russia’s Secret Intelligence Agency Hacked: ‘Largest Data Breach In Its History’

Red faces in Moscow this weekend, with the news that hackers have successfully targetedFSB—Russia’s Federal Security Service. The hackers managed to steal 7.5 terabytes of data from a major contractor, exposing secret FSB projects to de-anonymize Tor browsing, scrape social media, and help the state split its internet off from the rest of the world. The data was passed to mainstream media outlets for publishing.
…Amazon confirms it keeps your Alexa recordings basically forever

If you (like so many of us) hate listening to recordings of your own voice, you may be in for an unpleasant future, as Amazon has confirmed it hangs on to every conversation you’ve ever had with an Alexa-enabled device until or unless you specifically delete them. That confirmation comes as a response to a list of questions Sen. Chris Coons (D-Delaware) sent to Amazon CEO Jeff Bezos in May expressing ‘concerns’ about how Amazon uses and retains customers’ Alexa voice assistant data. Amazon’s response to Coons, as first reported by CNET, confirms that the company keeps your data as long as it wants unless you deliberately specify otherwise.
…Kubernetes CLI tool security flaw lets attackers run code on host machine

The Kubernetes project has patched today a dangerous security flaw that could allow for clever hacks where attackers may run code on the host machine. The vulnerability doesn’t impact the Kubernetes system itself, but kubectl (Kube control), the official command-line utility for working with Kubernetes installations. Security researchers have discovered a security flaw in the kubectl cp (copy) operation that is used to transfer files from containers to a user’s host machine.
…A Second U.S. City Has Banned Facial Recognition

Somerville, Massachusetts just became the second U.S. city to ban the use of facial recognition in public space. The ‘Face Surveillance Full Ban Ordinance,’ which passed through Somerville’s City Council on Thursday night, forbids any “department, agency, bureau, and/or subordinate division of the City of Somerville” from using facial recognition software in public spaces. The ordinance passed Somerville’s Legislative Matters Committee on earlier this week.
…DARPA’S $1.5-Billion Remake of U.S. Electronics
About a year ago, the U.S.Defense Advanced Research Projects Agency pulled back the covers on its five-year, $1.5-billion scheme to remake the U.S. electronics industry. The Electronics Resurgence Initiative included efforts in “aggressive specialization” for chip architectures, systems that are smart enough to reconfigure themselves for whatever data you throw at them, open-source hardware, 24-hour push-button system design, and carbon-nanotube-enabled 3D chip manufacturing, among other cool things. As always with DARPA, this is high-risk research;but if even half of it works out, it could change the nature not just of what kinds of systems are designed but also of who makes them and how they’re made.
…Key Conjurer: Our Policy of Least Privilege

Hi, my name is Reza Nikoopour and I’m a security engineer on the Security team at Riot. My team is responsible for securing Riot infrastructure wherever we’re deployed – whether that means internal or external data centers or clouds. We provide cloud security guidance to the rest of Riot, and we’re responsible for Key Conjurer, our open source AWS API programmatic access solution.
…It’s Surprisingly Easy to Hack the Precision Time Protocol

When it comes to synchronizing large and important networks, for instance in the energy or financial sectors, every microsecond counts. Different protocols have been designed and implemented to achieve such precision. One of the most effective approaches is called IEEE 1588-2008 or the Precision Time Protocol (PTP).
But while PTP can in theory help networks synchronizetheir actions to within a microsecond, a team of computer scientists recently demonstrated that PTP also makes it possible—in multiple ways—to hack such a system. In a network using PTP, one central clock, referred to as a “master” clock, is responsible for coordinating and communicating time to “slave” clocks across the network (these controversial terms were recently removed fromthe popular programming language Python, but continue to be used in many fields). The master clock accomplishes this by sending time-stamped data packets to the slaves.
…For two hours, a large chunk of European mobile traffic was rerouted through China

For more than two hours on Thursday, June 6, a large chunk of European mobile traffic was rerouted through the infrastructure of China Telecom, China’s third-largest telco and internet service provider (ISP). The incident occurred because of a BGP route leak at Swiss data center colocation company Safe Host, which accidentally leaked over 70,000 routes from its internal routing table to the Chinese ISP. The Border Gateway Protocol (BGP), which is used to reroute traffic at the ISP level, has been known to be problematic to work with, and BGP leaks happen all the time.
…Household Radar Can See Through Walls and Knows How You’re Feeling
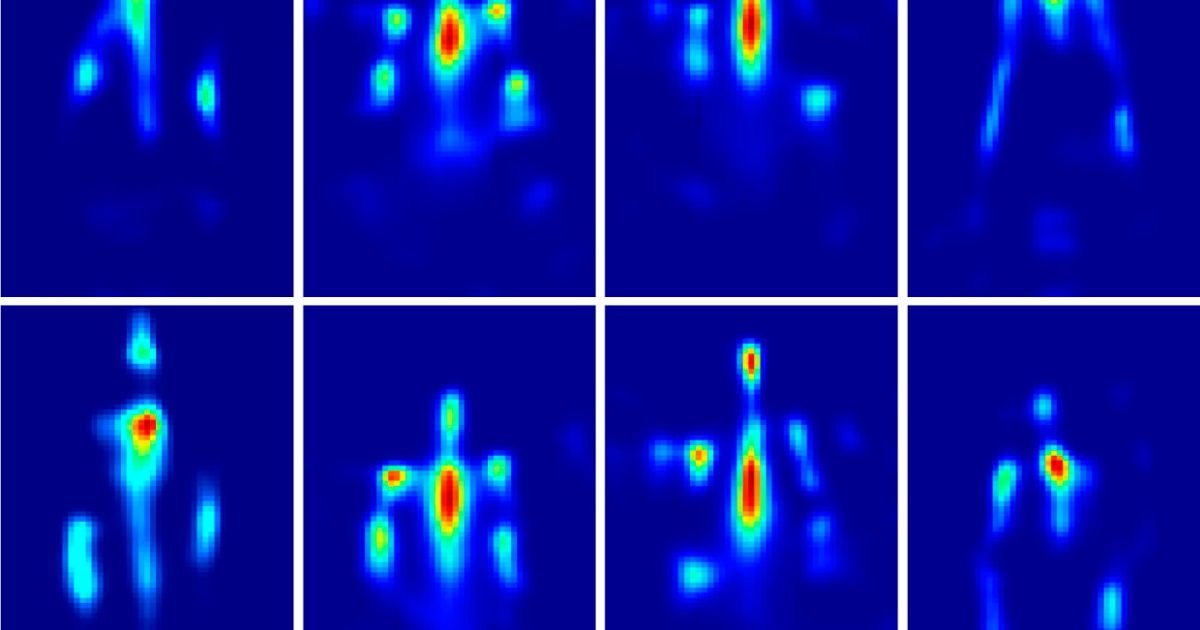
When I was a boy, I secretly hoped I would discover latent within me some amazing superpower—say,X-ray vision or the ability to read people’s minds. Lots of kids have such dreams. But even my fertile young brain couldn’t imagine that one day I would help transform such superpowers into reality.
Nor could I conceive of the possibility that I would demonstrate these abilities to the president of the United States. And yet two decades later, that’s exactly what happened. There was, of course, no magic or science fiction involved, just new algorithms and clever engineering, using wireless technology that senses the reflections of radio waves emanating from a nearby transmitter.
…SEC suing Kik for unregistered ICO

The Securities and Exchange Commission today sued Kik Interactive Inc. for conducting an illegal $100 million securities offering of digital tokens. The SEC charges that Kik sold the tokens to U.S. investors without registering their offer and sale as required by the U.S. securities laws. As alleged in the SEC’s complaint, Kik had lost money for years on its sole product, an online messaging application, and the company’s management predicted internally that it would run out of money in 2017.
…Advanced Linux backdoor found in the wild escaped AV detection

Researchers say they’ve discovered an advanced piece of Linux malware that has escaped detection by antivirus products and appears to be actively used in targeted attacks. HiddenWasp, as the malware has been dubbed, is a fully developed suite of malware that includes a trojan, rootkit, and initial deployment script, researchers at security firm Intezer reported on Wednesday. At the time Intezer’s post went live, the VirusTotal malware service indicated Hidden Wasp wasn’t detected by any of the 59 antivirus engines it tracks, although some have now begun to flag it.
…