Cyber security news and services
Anatomy of CVE-2019-5736: A runc container escape!

On Monday, February 11, CVE-2019-5736 was disclosed. This vulnerability is a flaw in runc, which can be exploited to escape Linux containers launched with Docker, containerd, CRI-O, or any other user of runc. But how does it work?
Dive in! Processes interact with the operating system to perform a variety of operations (for example, reading and writing files, taking input, communicating on the network, etc.) via system calls, or syscalls. Syscalls can perform a variety of actions.
…Unauthorized access to Docker Hub database

On Thursday, April 25th, 2019, we discovered unauthorized access to a single Docker Hub database storing a subset of non-financial user data. Upon discovery, we acted quickly to intervene and secure the site. We want to update you on what we’ve learned from our ongoing investigation, including which Hub accounts are impacted, and what actions users should take.
During a brief period of unauthorized access to a Docker Hub database, sensitive data from approximately 190,000 accounts may have been exposed (less than 5% of Hub users). Data includes usernames and hashed passwords for a small percentage of these users, as well as GitHub and Bitbucket tokens for Docker autobuilds. We are asking users to change their password on Docker Hub and any other accounts that shared this password.
…Ghidra: NSA’s reverse engineerin tool released to the public

Ghidra is a software reverse engineering (SRE) framework developed by NSA’s Research Directorate for NSA’s cybersecurity mission. It helps analyze malicious code and malware like viruses, and can give cybersecurity professionals a better understanding of potential vulnerabilities in their networks and systems.
Source: nsa.gov
…How the Spectre and Meltdown Hacks Really Worked

We’re used to thinking of computer processors as orderly machines that proceed from one simple instruction to the next with complete regularity. But the truth is, that for decades now, they’ve been doing their tasks out of order and just guessing at what should come next. They’re very good at it, of course.
So good in fact, that this ability, called speculative execution, has underpinned much of the improvement in computing power during the last 25 years or so. But on 3 January 2018, the world learned that this trick, which had done so much for modern computing, was now one of its greatest vulnerabilities. Throughout 2017, researchers at Cyberus Technology, Google Project Zero, Graz University of Technology, Rambus, University of Adelaide, and University of Pennsylvania, as well as independent researchers such as cryptographer Paul Kocher, separately worked out attacks that took advantage of speculative execution.
…New Security Technology Detects Malicious Cyberattacks on Drones, Cars, and Robots
Sensor-based automatic control technology is now used in hundreds of applications as varied as vehicle accident prevention, agricultural monitoring, and self-balancing robots. But as sensor interaction with the environment increases to enable control systems to “see,”“listen,”and “sense”their environment more accurately, the potential for cyber attacks also grows. To counter this danger,Mitsubishi Electric has developed what it believes is the first sensor-security technology for detecting inconsistencies that appear in sensor measurementswhen a system is under attack.
…Jeff Bezos Protests the Invasion of His Privacy, as Amazon Builds a Sprawling Surveillance State for Everyone Else

On Thursday, Bezos published emails in which the Enquirer’s parent company explicitly threatened to publish intimate photographs of Bezos and his mistress, which wereapparently exchanged between the two through their iPhones, unless Bezos agreed to a series of demands involving silence about the company’s conduct. In a perfect world, none of the sexually salacious material the Enquirer was threatening to release would be incriminating or embarrassing to Bezos: it involves consensual sex between adults that is the business of nobody other than those involved and their spouses. But that’s not the world in which we live: few news events generate moralizing interest like sex scandals, especially among the media.
…QuadrigaX lost $150 million in cryptocurrencies because its founder died and only he knew the wallet password.

Troubled Canadian crypto exchange QuadrigaCX owes its customers $190 million and cannot access most of the funds, according to a court filing obtained by CoinDesk. In a sworn affidavit filed Jan. 31 with the Nova Scotia Supreme Court, Jennifer Robertson, identified as the widow of QuadrigaCX founder Gerald Cotten, said the exchangeowes its customers roughly $250 million CAD ($190 million) in both cryptocurrency and fiat. The company previously announced it hadfiled for creditor protectionon its website, but the filing itself provides greater details about its predicament.
…Hundreds of Bounty Hunters Had Access to AT&T, T-Mobile, and Sprint Customer Location Data for Years

In January, Motherboard revealed that AT&T, T-Mobile, and Sprint were selling their customers’ real-time location data, which trickled down through a complex network of companies until eventually ending up in the hands of at least one bounty hunter. Motherboard was also able to purchase the real-time location of a T-Mobile phone on the black market from a bounty hunter source for $300. In response, telecom companies said that this abuse was a fringe case.
…Open sourcing ClusterFuzz
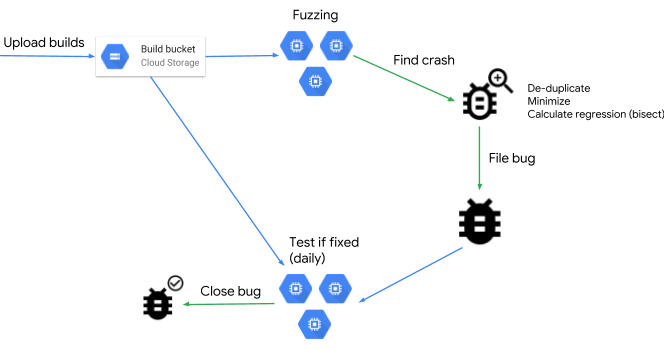
ClusterFuzz has found more than 16,000 bugs in Chrome and more than 11,000 bugs in over 160 open source projects integrated with OSS-Fuzz. It is an integral part of the development process of Chrome and many other open source projects. ClusterFuzz is often able to detect bugs hours after they are introduced and verify the fix within a day.
Source: googleblog.com
…The Big DNS Privacy Debate at FOSDEM

This weekend at the excellent FOSDEM gathering there were no less than three presentations on DNS over HTTPs. Daniel Stenberg presented a keynote session “DNS over HTTPS – the good, the bad and the ugly” (video), Vittorio Bertola discussed “The DoH Dilemma” while Daniel, Stéphane Bortzmeyer and I formed a DNS Privacy Panel expertly moderated by Jan-Piet Mens. I want to thank Daniel, Jan-Piet, Rudolf van der Berg, Stéphane & Vittorio for proofreading & improving this post, but I should add this does not imply an endorsement from anyone!
…A Scammer Used YouTube’s Copyright System to Ransom Creators

A scammer was found to be manually abusing YouTube’s automated copyright system in an effort to hold YouTube channels ransom. By submitting multiple fake copyright “flags” on videos, the scammer was able to bring at least two YouTube accounts to the brink of automatic deactivation under YouTube’s “three strikes” policy, even getting past YouTube employees who double-checked the suspicious claim. According to YouTube, anti-abuse teams initially identified the requests as suspicious and asked for more information.
…Mayhem, the Machine That Finds Software Vulnerabilities, Then Patches Them

Back in 2011, when the venture capitalist Marc Andreessen said that “software is eating the world,” it was still a fresh idea. Now it’s obvious that software permeates our lives. From complex electronics like medical devices and autonomous vehicles to simple objects like Internet-connected lightbulbs and thermometers, we’re surrounded by software.
And that means we’re all more exposed to attacks on that software than everbefore. Every year, 111 billion lines are added to the mass of software code in existence, and every line presents a potential new target. Steve Morgan, founder and editor in chief at the research firm Cybersecurity Ventures, predicts that system break-ins made through a previously unknown weakness—what the industry calls “zero-day exploits”—will average one per day in the United States by 2021, up from one per week in 2015.
…Who Controls Bitcoin Core?
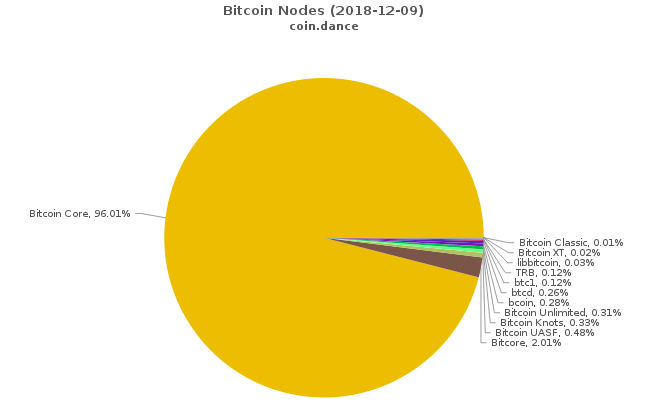
The question of who controls the ability to merge code changes into Bitcoin Core’s GitHub repository tends to come up on a recurring basis. This has been cited as a “central point of control” of the Bitcoin protocol by various parties over the years, but I argue that the question itself is a red herring that stems from an authoritarian perspective—this model does not apply to Bitcoin. It’s certainly not obvious to a layman as to why that is the case, thus the goal of this article is to explain how Bitcoin Core operates and, at a higher level, how the Bitcoin protocol itself evolves.
…Leaked Documents Show How Instagram Polices Stories

Newly leaked internal documents obtained by Motherboard detail how Instagram polices content published through its Instagram Stories feature, which allows users to publish short videos and static images that generally stay on profiles for 24 hours. The fact that they often have multiple discrete parts can make it particularly difficult to moderate stories, the documents show. In particular, the documents show how Instagram’s moderators have to grapple with the context of a story.
…China’s APT10

You’ve decided to tackle a high-end luxury apartment, the kind of building with multiple Picassos in the penthouse. You could spend weeks or months casing the place, studying every resident’s schedule, analyzing the locks on all the doors. You could dig through trash for hints about which units have alarms, run through every permutation of what the codes might be.
Or you could also just steal the super’s keys. According to a Justice Department indictment Thursday, that is effectively what China has done to the rest of the world since 2014. That’s when the country’s elite APT10—short for “advanced persistent threat”—hacking group decided to target not just individual companies in its long-standing efforts to steal intellectual property, but instead focus on so-called managed service providers.
…Hackers bypassed vein based authentication with a fake hand

A couple of researchers demonstrated how to bypass vein based authentication using a fake hand build from a photo. If you consider vein based authentication totally secure, you have to know that a group of researchers demonstrated the opposite at the Chaos Communication Congress hacking conference. Vein based authentication scan invisible vein pattern (i.e. shape, size, and position of a user’ s veins) of the palm, back of the hand, fingers, etc, to identify the user.
…NSA to release a free reverse engineering tool

The US National Security Agency will release a free reverse engineering tool at the upcoming RSA security conference that will be held at the start of March, in San Francisco. The software’s name is GHIDRA and in technical terms, is a disassembler, a piece of software that breaks down executable files into assembly code that can then be analyzed by humans. The NSA developed GHIDRA at the start of the 2000s, and for the past few years, it’s been sharing it with other US government agencies that have cyber teams who need to look at the inner workings of malware strains or suspicious software.
…PNC Bank testing dynamic CVV codes to combat online card fraud

US-based PNC Bank is in the middle of a pilot project that aims to test out credit cards with constantly changing card verification values (or CVVs) to reduce online credit card fraud. The dynamic CVV is displayed on the back of such a card in e-ink, and changes according to an algorithm supplied by Visa. Services like Apple Pay and Google Pay try to combat online card theft by using tokenization to obscure a person’s card numbers from theft while online.
…Logitech Keystroke Injection Flaw Went Unaddressed for Months

Computer peripheral giant Logitech has finally issued a patched version of its Logitech Options desktop app, after being taken to task for a months-old security flaw. The bug could of allowed adversaries to launch keystroke injection attacks against Logitech keyboard owners that used the app. Google Project Zero security researcher Tavis Ormandy found the bug in September and publicly disclosed the vulnerability this week.
…Critical SQLite Flaw Leaves Millions of Apps Vulnerable to Hackers

Cybersecurity researchers have discovered a critical vulnerability in widely used SQLite database software that exposes billions of deployments to hackers. Dubbed as ‘Magellan’ by Tencent’s Blade security team, the newly discovered SQLite flaw could allow remote attackers to execute arbitrary or malicious code on affected devices, leak program memory or crash applications.
Source: thehackernews.com
…