Cyber security news and services
Adware vendors buy Chrome Extensions to send ad- and malware-filled updates
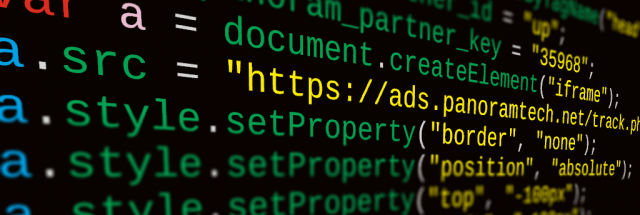
One of the coolest things about Chrome is the silent, automatic updates that always ensure that users are always running the latest version. While Chrome itself is updated automatically by Google, that update process also includes Chrome’s extensions, which are updated by the extension owners. This means that it’s up to the user to decide if the owner of an extension is trustworthy or not, since you are basically giving them permission to push new code out to your browser whenever they feel like it.
…Undocumented Double-Spend Risk in Bitcoin
There is a third category of double-spends that is not documented: double-spending through full node consensus failure. The risk for this grows every day.
Source: medium.com
…A Likely Explanation for the “Sonic Weapon” Used at the U.S. Embassy in Cuba

Last August, reports emerged that U.S. and Canadian diplomats in Cuba had suffered a host of mysterious ailments. Speculation soon arose that a high-frequency sonic weapon was to blame. Acoustics experts, however, were quick to point out the unlikeliness of such an attack.
Among other things, ultrasonic frequencies—from 20 to 200 kilohertz—don’t propagate well in air and don’t cause the ear pain, headache, dizziness, and other symptoms reported in Cuba. Also, some victims recalled hearing high-pitched sounds, whereas ultrasound is inaudible to humans.
…From SpankChain to Bigboobscoin, Startups Keep Trying to Get People to Pay for Sex on the Blockchain

The affair between the sex industry and cryptocurrency isn’t new. Porn has historically been ahead of the curve tech-wise, and this holds true for Bitcoin adoption. Back in 2013, UK escort service VIP Passion started accepting Bitcoin payments.
Two years later, sex workers started posting Twitter tutorials on how to use Bitcoin to pay for advertisements on Backpage.com when major credit cards pulled their services from the platform due to rampant sex trafficking.
…Putin’s Hypersonic Weapon Appears to Be a Modified Iskander Ballistic Missile

Yesterday’s bizarrely ominous presentation by Russian Vladimir Putin, where he showcased six super weapons that will supposedly give Russia an asymmetric edge over its potential foes—namely the United States—is still reverberating throughout the national security community. After we posted our master recap of the event and the weapons concepts featured in it, we and our incredible discussion crew here at The War Zone went to work dissecting what was presented in an attempt to parse fact from fiction.
…MI5 agents can commit crime in UK, government reveals

The prime minister was on Thursday forced to publish the text of a direction to the Investigatory Powers Commissioner’s Office, the spying watchdog, on governing “security service participation in criminality”.
Source: theguardian.com
…U.S. Has Been Watching Russia’s Nuclear-Powered Cruise Missiles Crash and Burn

Successful or not, if Russia is test flying these weapons, this means it has been repeatedly crashing nuclear reactors into the ground or the ocean.
Source: thedrive.com
…Ethereum fixes serious “eclipse” flaw that could be exploited by any kid

Developers of Ethereum, the world’s No. 2 digital currency by market capitalization, have closed a serious security hole that allowed virtually anyone with an Internet connection to manipulate individual users’ access to the publicly accessible ledger.
Source: arstechnica.com
…Hackers Are Stuffing DDoS Attacks with Monero Ransom Notes

Security researchers at Akamai, the Internet performance company that helped Github fight off the attack, told Fortune they’ve noticed something novel some of these recent attacks. Hackers have started stuffing the barrage of Internet traffic with ransom notes.
Source: fortune.com
…China Presses Its Internet Censorship Efforts Across the Globe

Within its digital borders, China has long censored what its people read and say online. Now, it is increasingly going beyond its own online realms to police what people and companies are saying about it all over the world.
Source: nytimes.com
…Bitcoin thirst spurs Icelandic heist—“Grand theft on a scale unseen before”

In Iceland, bitcoin mining will soon use more energy than its residents. Eleven people have been arrested in Iceland as a result of what local media are calling the “Big Bitcoin Heist”—600 mining computers were recently stolen from Icelandic data centers in four separate burglaries between December 2017 and January 2018.
Source: arstechnica.com
…Powerful New DDoS Method Adds Extortion

Attackers have seized on a relatively new method for executing distributed denial-of-service (DDoS) attacks of unprecedented disruptive power, using it to launch record-breaking DDoS assaults over the past week. Now evidence suggests this novel attack method is fueling digital shakedowns in which victims are asked to pay a ransom to call off crippling cyberattacks.
Source: krebsonsecurity.com
…U.S. Navy awards Lockheed Martin a $150M contract to develop laser weapons

A $150 million Lockheed contract will allow destroyers to use Star Wars technology against smaller targets.
Source: bloomberg.com
…A Supreme Court Case That Could Give Tech Giants More Power

Big tech platforms — Amazon, Facebook, Google — control a large and growing share of our commerce and communications, and the scope and degree of their dominance poses real hazards. A bipartisan consensus has formed around this idea. Senator Elizabeth Warren has charged tech giants with using their heft to “snuff out competition,” and even Senator Ted Cruz — usually a foe of government regulation — recently warned of their “unprecedented” size and power.
…WebKit exploit write-up
The proof of concept for this exploit can be found on the Chromium bug page. This bug was reported by lokihardt from Google Project Zer0. The bug can be found in Element::setAttributeNodeNS().
Let’s take a look at a code snippet:
Source: github.com
…Facebook Threatens Satire Site Over CNN Story That Snopes Rated ‘False’

Christian satire site The Babylon Bee received a terse warning from Facebook this week after the ‘independent fact-checkers’ at Snopes reported that one of the site’s humor articles was ‘false.’
Source: pjmedia.com
…A $5 Billion Cryptocurrency Has Enraged Cryptographers

IOTA is a cryptocurrency that’s been around since 2014 and is designed for micro-transactions between machines in the Internet of Things. IOTA is the tenth-largest cryptocurrency with a roughly $5 billion market cap. It doesn’t use a standard blockchain like most cryptocurrencies, but instead uses a Directed Acylic Graph (DAG) it calls “the Tangle” among other attempts at innovation.
For example, IOTA infamously used an in-house algorithm called Curl instead of the well-studied algorithms that underprin other digital coins.
…New LTE attacks can snoop on messages, track locations and spoof emergency alerts

A slew of newly discovered vulnerabilities can wreak havoc on 4G LTE network users by eavesdropping on phone calls and text messages, knocking devices offline, and even spoofing emergency alerts.
Source: zdnet.com
…Here’s the Letter Israel Sent to Solicit Zero-Days From American Hackers

Often, the best way to get something is to simply ask for it. That’s probably what the Israeli government thought when it sent an email to several American researchers and firms who make so-called zero-days, tools that take advantage of vulnerabilities in software that are unknown to the company that makes the software.
Source: vice.com
…Bitcoin faces regulatory crackdown, Bank of England warns

The Bank of England has warned that bitcoin faces a regulatory crackdown, warning that “inherently risky” cryptocurrencies are failing to fulfil their most basic function as money.
Source: theguardian.com
…