May. 28, 2018
German researchers reckon they have devised a method to thwart the security mechanisms AMD’s Epyc server chips use to automatically encrypt virtual machines in memory. So much so, they said they can exfiltrate plaintext data from an encrypted guest via a hijacked hypervisor and simple HTTP requests to a web server running in a second guest on the same machine. AMD’s data-center processors, as well as its Ryzen Pro line, support what’s called Secure Encrypted Virtualization.
May. 15, 2018
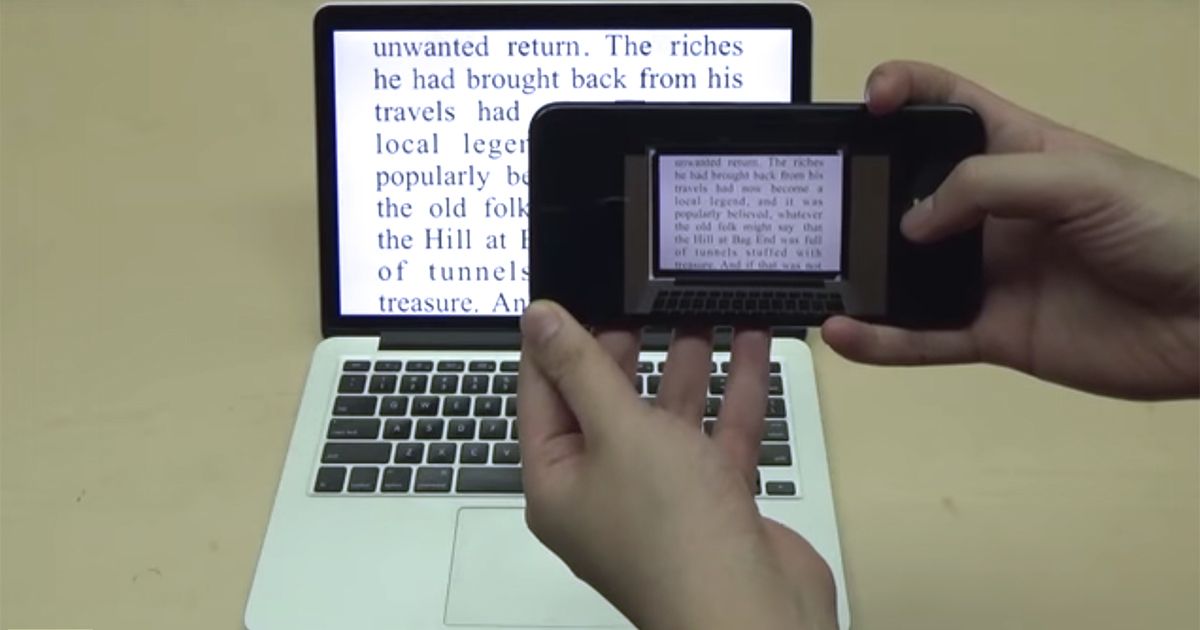
Computer scientists have now invented a way to hide secret messages in ordinary text by imperceptibly changing the shapes of letters. The new technique, named FontCode, works with common font families such as Times Roman and Helvetica. It is compatible with most word-processing software, including Microsoft Word, as well as image-editing and drawing programs, such as Adobe Photoshop and Adobe Illustrator.
FontCode embeds data into texts using minute perturbations to components of letters. This includes changing the width of strokes, adjusting the height of ascenders and descenders, and tightening or loosening the curves in serifs and the bowls of letters such as o, p, and b. A kind of artificial-intelligence system known as a convolutional neural network can recognize these perturbations and help recover the embedded messages. The amount of information FontCode can hide is limited only by the number of letters on which it acts, the researchers say.
May. 14, 2018

The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs. To create these exfiltration channels, the attacker first needs access to the encrypted emails, for example, by eavesdropping on network traffic, compromising email accounts, email servers, backup systems or client computers.
May. 9, 2018

City police plan to begin encrypting all the radio channels they use, ending the public’s ability to listen in. It will go forward if the City Council approves a five-year, $6.2 million plan when they vote May 15 on the budget. In city documents, police said encryption is needed because criminals listen to police communications.
It would greatly increase officer safety and help protect citizens, they wrote.
May. 8, 2018

In the debate over law enforcement access to encrypted devices, technical details matter. The rhetoric has been stark and, dismayingly often, divorced from technical reality. For example, two years ago we were told that only Apple could write software to open the phone of the San Bernardino terrorist; the technical reality turned out to be that an FBI contractor was able to do so.
Apr. 27, 2018

To be effective, Clear wouldn’t be binding on just Apple but rather manufacturers of all computing devices, many of them low-cost products made by bootstrapped manufacturers. That means there would be dozens, hundreds, or probably thousands of PIN vaults mandated under Clear. And each of them would be a potential target for hackers all around the world.
Source: arstechnica.com
Mar. 16, 2018

Last week, Motherboard reported that the FBI had arrested the CEO of Phantom Secure, a company allegedly providing custom, security-focused BlackBerry phones to the Sinaloa drug cartel, among other criminal groups. But the feds aren’t only going after Phantom’s owner: on Thursday, the Department of Justice announced an indictment against other apparent Phantom staff too, and confirmed what one source told Motherboard before it became public knowledge—that authorities have seized Phantom’s domains used for routing messages.
Mar. 13, 2018

We’re pleased to announce that ACMEv2 and wildcard certificate support is live! With today’s new features we’re continuing to break down barriers for HTTPS adoption across the Web by making it even easier for every website to get and manage certificates. ACMEv2 is an updated version of our ACME protocol which has gone through the IETF standards process, taking into account feedback from industry experts.
Mar. 7, 2018

Continuing on in our Encryption 101 series, where we gave a malware analyst’s primer on encryption and demonstrated encryption techniques using ShiOne ransomware, we now look at what it takes to break an encryption. In order for something as powerful as encryption to break, there needs to be some kind of secret flaw. That flaw is often a result of an error in implementation.








