Cyber security news and services
Automated Facial Recognition: Menace, Farce or Both?

In its letter, the ACLU argues that Amazon, which has in the past opposed secret government surveillance, should not be in the business of selling AFR technology that the company claims can “identify people in real-time by instantaneously searching databases containing tens of millions of faces.” Further, the ACLU insists, Rekognition’s capability to track “persons of interest,” coupled with its other features which “read like a user manual for authoritarian surveillance,” lends itself to the violation and abuse of individuals’ civil rights. Amazon naturally disagrees.
…Sonic Tone Attacks Damage Hard Disk Drives, Crashes OS
Using sonic and ultrasonic soundwaves as a weapon, researchers can disrupt the read, write and storage functions of a hard disk drive (HDD). The method can also be used to crash the host operating system, and in some cases damage targeted drives. Researchers said the attack can be performed by “nearby emitters” that target a computer’s HDD; so, the attacks could be performed by an adversary using inexpensive off-the-shelf speakers or could also be carried out via laptop or desktop speakers.
…A security vulnerability in Git that can lead to arbitrary code execution

The Git community has disclosed an industry-wide security vulnerability in Git that can lead to arbitrary code execution when a user operates in a malicious repository. This vulnerability has been assigned CVE 2018-11235 by Mitre, the organization that assigns unique numbers to track security vulnerabilities in software. Git 2.17.1 and Git for Windows 2.17.1 (2) were released today and include this fix.
…HIDDEN COBRA – Joanap Backdoor

According to reporting of trusted third parties, HIDDEN COBRA actors have likely been using both Joanap and Brambul malware since at least 2009 to target multiple victims globally and in the United States—including the media, aerospace, financial, and critical infrastructure sectors. According to reporting of trusted third parties, HIDDEN COBRA actors have likely been using both Joanap and Brambul malware since at least 2009 to target multiple victims globally and in the United States—including the media, aerospace, financial, and critical infrastructure sectors. Users and administrators should review the information related to Joanap and Brambul from the Operation Blockbuster Destructive Malware Report [1] in conjunction with the IP addresses listed in the .csv
…Asus made a crypto-mining motherboard that supports up to 20 GPUs
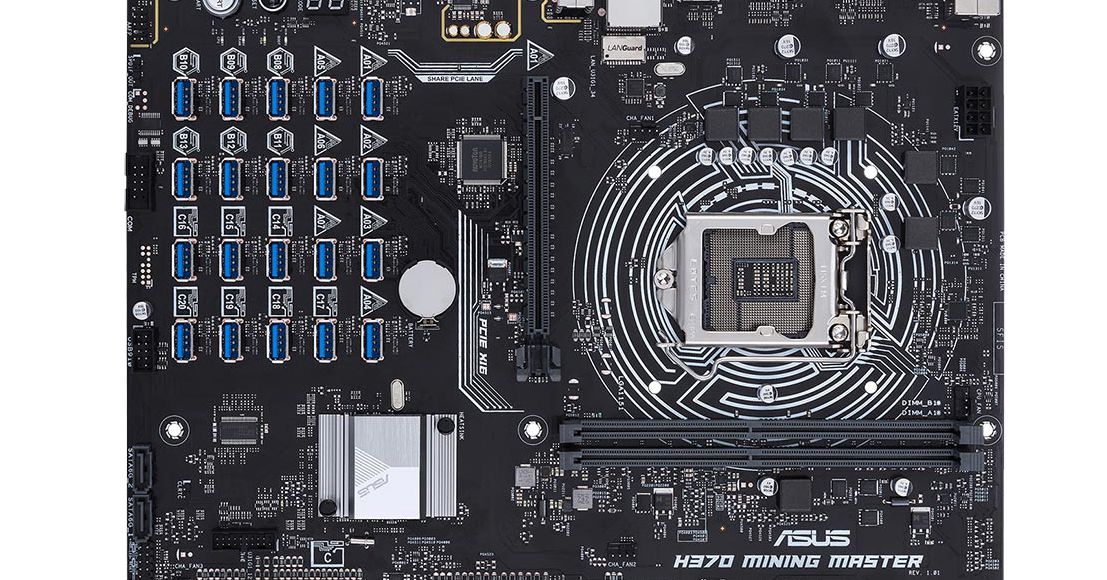
Asus announced the H370 Mining Master motherboard, which is specifically designed for cryptocurrency mining. It supports up to 20 graphics cards along with streamlined connectivity by allowing USB riser cables to plug directly into the PCB over PCIe. Asus announced the H370 Mining Master motherboard today, which is specifically designed for cryptocurrency mining.
It supports up to 20 graphics cards — yes, 20 — along with streamlined connectivity by allowing USB riser cables to plug directly into the PCB over PCIe. Asus’ approach here is going to make maintenance easier, ensure fewer PCIe disconnects, and more accurate diagnostics. This is a better format than just plugging in graphics cards to the motherboard via PCIe, like you would in a gaming desktop, the company says.
…Critical RCE Flaw Discovered in Blockchain-Based EOS Smart Contract System

Security researchers have discovered a series of new vulnerabilities in EOS blockchain platform, one of which could allow remote hackers to take complete control over the node servers running the critical blockchain-based applications. EOS is an open source smart contract platform, known as ‘Blockchain 3.0,’ that allows developers to build decentralized applications over blockchain infrastructure, just like Ethereum. Discovered by Chinese security researchers at Qihoo 360—Yuki Chen of Vulcan team and Zhiniang Peng of Core security team—the vulnerability is a buffer out-of-bounds write issue which resides in the function used by nodes server to parse contracts.
…Kenyans will soon need a license to post videos online

A new law is set to come into effect from May 28th, 2018 inKenyaregarding the publishing and broadcasting of any videos for public consumption. Specifically, theKenya Film and Classification Board(KFCB) states that, according to the law, anyone in Kenya broadcasting any videos for public viewing (including on social media and the Internet) will be required to have a filming license. Those who fail to register for a filming license with the KFCB face imprisonment or a fine.
…Two Canadian banks say accounts compromised: CIBC 40,000 and BMO 50,000

Two Canadian banks warned Monday they have been targeted by hackers, and that the personal information of tens of thousands of customers may have been stolen — something that appeared to be confirmed in a letter to the media from someone who said they were demanding a $1-million ransom from the banks. CIBC-ownedSimplii Financial was the first to warn on Monday morningthat hackers had accessed thepersonal and account information of more than 40,000 of the bank’s customers. The bank said it received a tip over the weekend that hackers had obtained the data, and after a preliminary investigation decided to go public on Monday.
…Cryptocurrency Trading App Taylor Loses 2,500 ETH in $1.5M Hack

Cryptocurrency trading app Taylorsuffered a catastrophic hack on May 22 that resulted in the loss of over 2,500 ETH, valued at $1.5 million. In addition, the trading platform lost 7% of the total TAY token supply, potentially crippling the development of the trading software. According to the official statement, the only tokens that remain in the Taylor fund are those in the Founders’ and Advisors’ pools that are held in aninaccessible vesting contract.
…Scammers raid man’s bank account while he waits on hold to fraud hotline

A man watched helplessly as cybercriminals stole £9,000 (nearly US$12,000) from his account at British bank TSB while he waited – for four-and-a-half hours – to get through to the bank’s fraud line, according to a BBC report. Ben Alford, of Weymouth in the United Kingdom, has described how he put in a call to TSB after noticing that somebody had taken out a loan in his name from another bank. While he was logged into his TSB online account and waited for the bank’s fraud department to deal with his phone call, he saw how two sums – £5,000 and £4,000 – were stolen from his account in two transactions.
…Oracle Plans to Drop Java Serialization Support, the Source of Most Security Bugs

Oracle plans to drop support for data serialization/deserialization from the main body of the Java language, according to Mark Reinhold, chief architect of the Java platform group at Oracle. Serialization is the process of taking a data object and converting it into a stream of bytes (binary format), so it can be transported across a network or saved inside a database, only to be deserialized later and used in its original form. Serializing and deserializing data is not a problem by itself, or when the source of the data is known to be safe.
…China is exporting facial recognition software to Africa

For all the promise it holds for the future, artificial intelligence is still guilty of historic bias. Voice recognition software struggles with English accents that are not American or British and facial recognition can be guilty of racial profiling. As this technology increasingly outpaces human discourse on race, China seems to be getting ahead on recognizing a diverse range of faces across the wider world, despite its own struggles with racial insensitivity.
…Epyc fail? We can defeat AMD’s virtual machine encryption, say boffins
German researchers reckon they have devised a method to thwart the security mechanisms AMD’s Epyc server chips use to automatically encrypt virtual machines in memory. So much so, they said they can exfiltrate plaintext data from an encrypted guest via a hijacked hypervisor and simple HTTP requests to a web server running in a second guest on the same machine. AMD’s data-center processors, as well as its Ryzen Pro line, support what’s called Secure Encrypted Virtualization.
…Freezing Your Credit Will Be Free Later This Year

Soon you won’t have to pay to freeze your credit. As part of a new bank deregulation bill passed by Congress on Tuesday, the new law will make it so consumers can both place and remove credit freezes at no cost, a process that currently costs between $2 and $10, depending on where you live, and needs to be done at all three credit bureaus in order to be effective, Lifehacker reports. Interest in credit freezing rose last year when the Equifax hack exposed the personal information of about 148 million Americans.
…The Pentagon Has a Big Plan to Solve Identity Verification in Two Years

The Defense Department is funding a project that officials say could revolutionize the way companies, federal agencies and the military itself verify that people are who they say they are and it could be available in most commercial smartphones within two years. The technology, which will be embedded in smartphones’ hardware, will analyze a variety of identifiers that are unique to an individual, such as the hand pressure and wrist tension when the person holds a smartphone and the person’s peculiar gait while walking, said Steve Wallace, technical director at the Defense Information Systems Agency. Organizations that use the tool can combine those identifiers to give the phone holder a “risk score,” Wallace said.
…A floating Pacific island is in the works with its own government, cryptocurrency and 300 houses

The Floating Island Project plans to create off-shore housing that uses its own currency and operates outside of government regulations. The project is a pilot program in partnership with the government of French Polynesia. A long-term vision for the project is hundreds of new countries floating on the ocean.
The Floating Island Project plans to create off-shore housing that uses its own currency and operates outside of government regulations. The project is a pilot program in partnership with the government of French Polynesia. The project is funded through philanthropic donations via the Seasteading Institute and Blue Frontiers, which sells tokens of the cryptocurrency Varyon.
…Stablecoins: Brilliant idea or ticking time bomb?

If you have been in crypto for more than two minutes, you know one simple fact: Coin prices are really volatile. And that volatility isn’t just tough on investors. It’s also tough on those who provide services to crypto startups in exchange for tokens — and for the crypto startups themselves, who are having to run a business with an ever-changing budget.
Given the growth of the crypto sector in the past year, significantly increased interest by institutional investors and the high volatility of many assets, the concept of stablecoins has seen quite a bit of interest. As the name implies, stablecoins are crypto-assets that seek to hold a consistent value vis-a-vis another currency. There is a lot of great material out there on the topic.
…Bitcoin backlash as ‘miners’ stress power grids in Central Washington

Public hearings for rural electric utilities are rarely sellout events. But the crowd that showed up in Wenatchee two weeks ago for a hearing about Bitcoin mining in Chelan County was so large that utility staff had to open a second room with a video feed for the overflow. As a result, an area famous for apples, wheat and conservative politics has been transformed into a kind of cyber-boomtown, with Bitcoin mining operations that range from large-scale, state-of-the-art warehouses to repurposed cargo containers to backyard sheds.
…ZeppelinOS, a platform for smart contract applications in Ethereum

Today we’re excited to announce the first mainnet release of ZeppelinOS, a platform for developing, managing, and operating smart contract applications in Ethereum. You can start using it right now at zeppelinos.org. Until now, it was difficult and costly to fix problems in smart contracts.
Hundreds of millions of dollars were put at risk because of easy-to-fix vulnerabilities, but fixing them was too costly or even impossible. With ZeppelinOS, that will no longer be a problem. Developers can now build smart contracts that can be easily upgraded over time.
…GDPR Version of USA Today Is 500KB Instead of 5.2MB
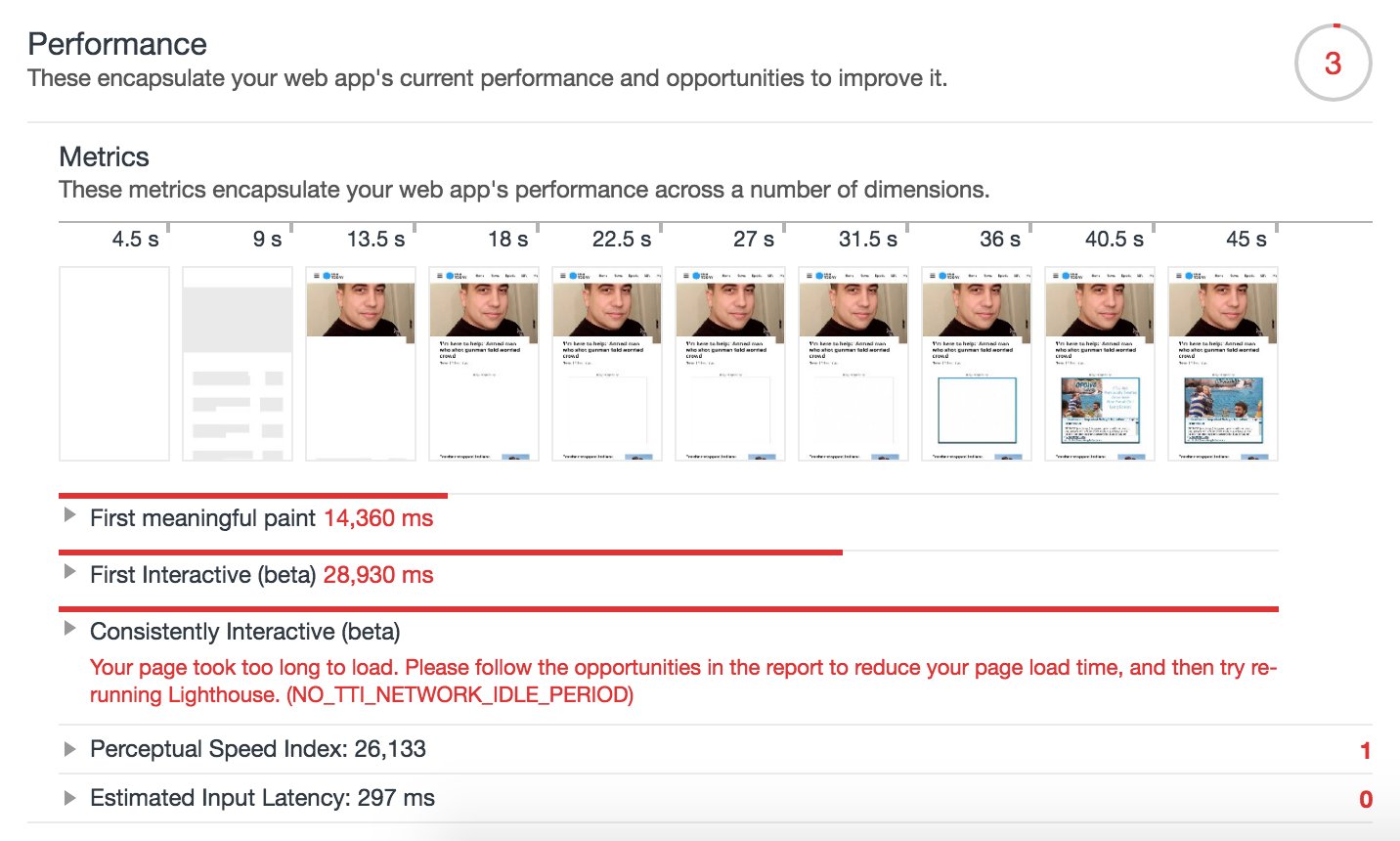
“Because of #GDPR, USA Today decided to run a separate version of their website for EU users, which has all the tracking scripts and ads removed. The site seemed very fast, so I did a performance audit. How fast the internet could be without all the junk! ?
5.2MB → 500KB”
Source: twitter.com
…