Cyber security news and services
Comcast bug made it shockingly easy to steal customers’ Wi-Fi passwords

A security hole in a Comcast service-activation website allowed anyone to obtain a customer’s Wi-Fi network name and password by entering the customer’s account number and a partial street address, ZDNet reported yesterday. The problem would have let attackers ‘rename Wi-Fi network names and passwords, temporarily locking users out’ of their home networks, ZDNet wrote. Obviously, an attacker could also use a Wi-Fi network name and password to log into an unsuspecting Comcast customer’s home network.
…The Verge Hack, Explained

Cryptocurrency enthusiasts are keen on telling ordinary civilians how safe and secure the Blockchain protocols powering their favorite coins are. Indeed, major cryptocurrencies like Bitcoin and Ethereum have maintained their security quite well—better, arguably, than any other digital asset/payment system in history—which is pretty remarkable, considering that they are unbacked digital money free from any single party’s control with an effective multi-billion dollar bounty on their proverbial heads. Last month, an as-of-yet unidentified attacker was able to severally compromise Verge, a relatively small, privacy-focused cryptocurrency.
…SleuthQL: A SQL Injection Discovery Tool

SleuthQL aims to augment an assessor’s ability to discover SQL injection points by automating some of the request analysis required during a web application assessment. SleuthQL is a Python 3 script to search Burp Suite’s request history for parameters and values that match syntax matching that of database languages, such as SQL. It judges a parameter or value based on whether it matches a regular expression associated with database queries.
…Google and Microsoft Reveal New Spectre Attack
Both Google and Microsoft researchers discovered the bug independently. The bugs work similarly to the Meltdown and Spectre bugs, a reason why they were classified as ‘variant 3a’ and ‘variant 4’ instead of separate vulnerabilities altogether. Variant 3a is a variation of the Meltdown flaw, while Variant 4 is a new Spectre-like attack.
The most important of these two is Variant 4. Both bugs occur for the same reason —speculative execution— a feature found in all modern CPUs that has the role of improving performance by computing operations in advance and later discarding unneeded data. The difference is that Variant 4 affects a different part of the speculative execution process —the data inside the ‘store buffer’ inside a CPU’s cache.
…Barcelona is leading the fightback against smart city surveillance

“Now we have a big contract with Vodafone, and every month Vodafone has to give machine readable data to city hall. Before, that didn’t happen. They just took all the data and used it for their own benefit”
In 2015 Ada Colau, an activist with no experience in government, became mayor of Barcelona. She called for a democratic revolution, and for the last two years city hall, working with civic-minded coders and cryptographers, has been designing the technological tools to make it happen. Their efforts have centred on two things.
…Teen phone monitoring app leaked thousands of user passwords

The mobile app, TeenSafe, bills itself as a ‘secure’ monitoring app for iOS and Android, which lets parents view their child’s text messages and location, monitor who they’re calling and when, access their web browsing history, and find out which apps they have installed. Although teen monitoring apps are controversial and privacy-invasive, the company says it doesn’t require parents to obtain the consent of their children. But the Los Angeles, Calif.-based company left its servers, hosted on Amazon’s cloud, unprotected and accessible by anyone without a password.
…The Evolving Debate Over EIP-999: Can (or Should) Trapped Ether Be Freed?

In November 2017, a pseudonymous actor exploited a vulnerability in Parity’s multi-signature Ethereum wallet library that rendered half a million ether inaccessible to their owners. Ironically, the culprit, Devops199, was trying to patch another vulnerability that allowed hackers to steal $32 million from Parity’s multi-signature wallet accounts back in July of 2017. While tinkering with the popular service’s smart contracts, Devops199 blundered his way into complete ownership of the library that houses the entirety of Parity’s multi-signature wallet accounts.
…Malware and Where to Find Them

We, as malware analysts, are always in need of new samples to analyze in order to learn, train or develop new techniques and defenses. One of the most common questions I get is “Where to find malware to analyze?” so I’m sharing here my private collection of repositories, databases and lists which I use onadaily basis.
Some of them are updated frequentlyandsome of them are not. The short description under each link wasn’t written by me, it was written by the owners of the repositories.
…Potential Spy Devices Which Track Cellphones Found in D.C., Md., Va.
The News4 I-Team found dozens of the potential spy devices while driving around Washington, D.C., Maryland and Northern Virginia. The technology can be as small as a suitcase, placed anywhere at any time, and it’s used to track cell phones and intercept calls. The News4 I-Team found dozens of potential spy devices while driving around Washington, D.C., Maryland and Northern Virginia.
…T-Mobile Employee Made Unauthorized ‘SIM Swap’ to Steal Instagram Account

T-Mobile is investigating a retail store employee who allegedly made unauthorized changes to a subscriber’s account in an elaborate scheme to steal the customer’s three-letter Instagram username. The modifications, which could have let the rogue employee empty bank accounts associated with the targeted T-Mobile subscriber, were made even though the victim customer already had taken steps recommended by the mobile carrier to help minimize the risks of account takeover. So-called “port out” scams allow crooks to intercept your calls and messages while your phone goes dark.
…Man faces up to 35 years in prison for helping hackers evade detection by anti-virus software

In May 2017, one of the biggest facilitators of cybercrime, Scan4You, went offline after the two main suspects, were arrested in Latvia and extradited to the US by the Federal Bureau of Investigation (FBI). In May 2018, the case against the Scan4You’s operators concluded in a Virginia federal courtroom. Scan4You was set up in 2009 as an online service designed to help malware authors evade detection by security software.
…LocationSmart Leaked Location Data for Customers of All Major U.S. Mobile Carriers
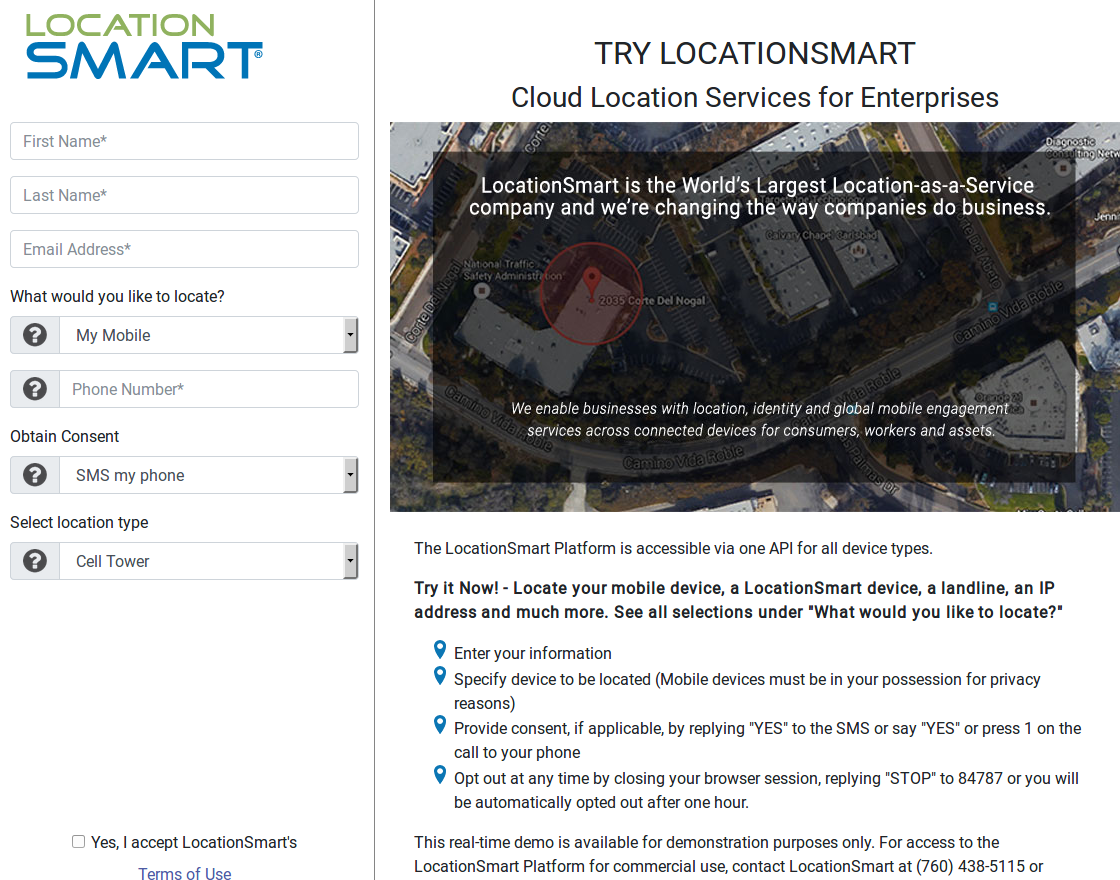
LocationSmart’s demo is a free service that allows anyone to see the approximate location of their own mobile phone, just by entering their name, email address and phone number into a form on the site. LocationSmart then texts the phone number supplied by the user and requests permission to ping that device’s nearest cellular network tower. Once that consent is obtained, LocationSmart texts the subscriber their approximate longitude and latitude, plotting the coordinates on a Google Street View map.
…A bug in Keeper password manager leads to sparring over “zero-knowledge” claim

Keeper, a password manager maker that recently and controversially sued a reporter, has fixed a bug that a security researcher claimed could have allowed access to a user’s private data. The bug — which the company confirmed and has since fixed — filed anonymously to a public security disclosure list, detailed how anyone controlling Keeper’s API server could gain access to the decryption key to a user’s vault of passwords and other sensitive information. The researcher found the issue in the company’s Python-powered script called Keeper Commander, which allows users to rotate passwords, eliminating the need for hardcoded passwords in software and systems.
…A flaw in a connected alarm system exposed vehicles to remote hacking

Car hacking has become a major focus in the security community in recent years, as more vehicles are hooked up to the cellular internet. But while convenient to control your car from your phone, it’s also opened up new points for attack — which could have real-world consequences. You might not even realize you’re a Calamp user.
Many apps, including the vehicle tracking app Viper SmartStart, which lets users locate, start, and control their car from their phone, connects to the outside world using a Calamp modem to its cloud-based servers. The researchers found that the Viper mobile app, while secure, was connecting to two different servers — one used by Viper, and another run by Calamp. Using the same credentials as the app, the researchers were also able to log in and gain complete access to the Calamp server, the researchers said in their write-up.
…This Guy Heated Bath Water With Bitcoin Mining and It Worked Too Well
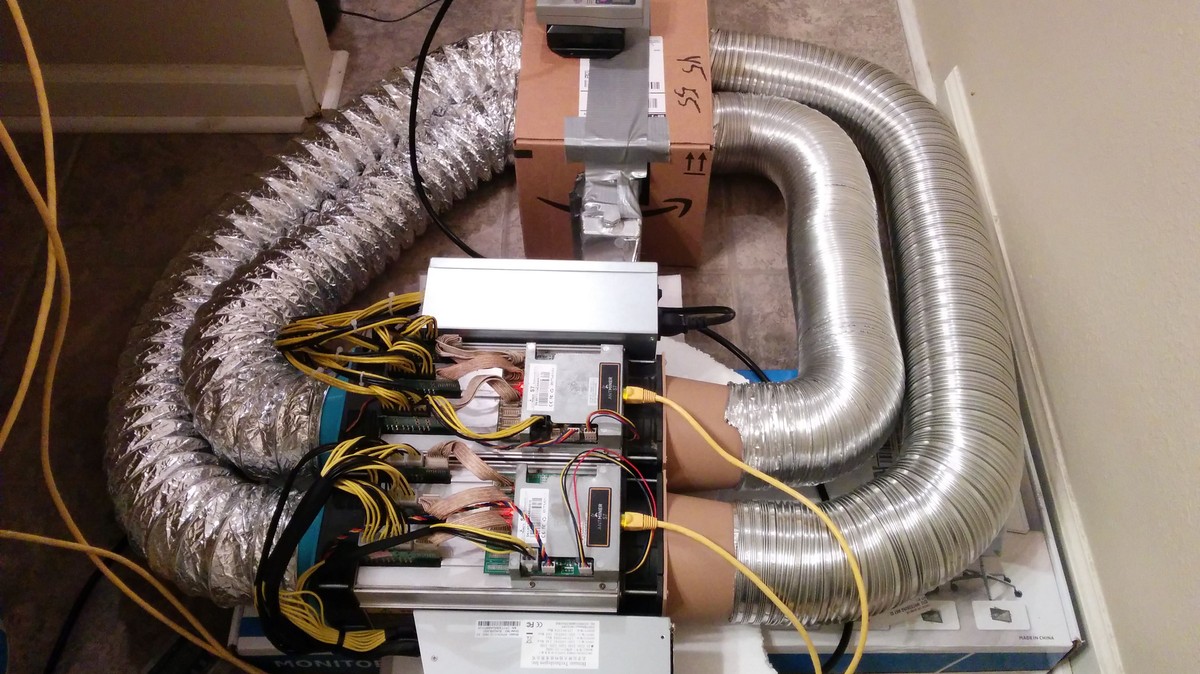
For hobbyists trying to strike it rich with cryptocurrency mining, but who don’t have access to gigantic warehouses where they can park the hardware, making money means packing a bunch of very loud and very hot computers into your house or apartment. Some at-home cryptocurrency miners are harnessing the heat that powerful mining equipment—called ASICs—give off. Motherboard’s Daniel Oberhaus used mining equipment (albeit graphics cards, not ASICs) to stay warm during a storm once, and a Redditor posting under the handle “gta3uzi” just took it to another level.
…EU parliaments website in violation of GDPR
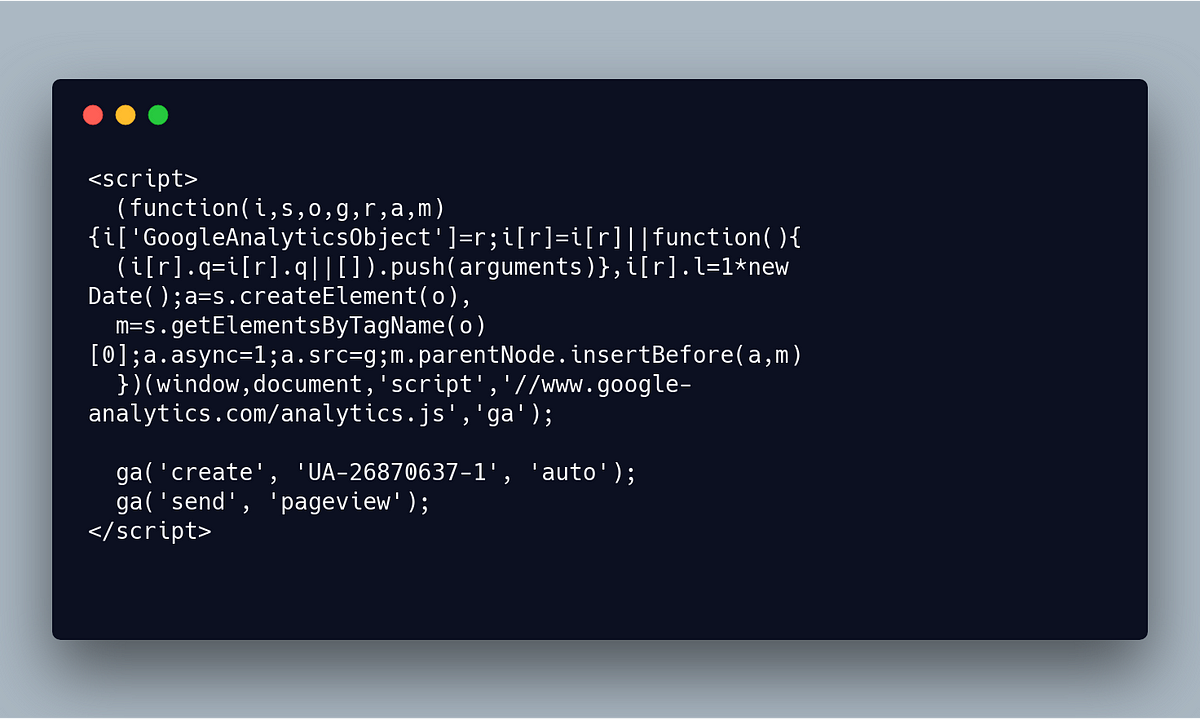
After reading an interview (german content) of the EU-Commisioner for Justice, Consumers and Gender Equality Věra Jourová with the German newspaper “Die Zeit” in which she stated that the GDPR is so easy, even she could implement it, I got very curious and wanted to see how compliant the EU’s websites are. It took me less than five minutes to spot a violation: on the website of the EU Parliament Google Analytics is being used to track the visitors without the neccesary anonymizeIP flag, which in turn causes Google to store the complete IP address without anonymizing the last octet. You can take a look for yourself by checking the source code of this page (archived version in case it gets fixed in the meantime).
…Alexa, Siri and Google can be tricked by commands you can’t hear

As tens of millions of happy delighted owners know, Siri, Alexa, Cortana and Google, will do lots of useful things in response to voice commands. But what if an attacker could find a way to tell them to do something their owners would rather they didn’t? Researchers have been probing this possibility for a few years and now, according to a New York Times article, researchers at the University of California, Berkeley have shown how it could happen.
…Dutch police seize servers of MaxiDed, a provider known for hosting malware ops
The name of the hosting provider is MaxiDed, a service that has operated since late 2008, but which became increasingly more aggressive with its marketing in the last two years when its ads became a common occurrence on cybercrime forums. According to an archived version of the site, the company offered dedicated servers, VPS, VPN, and server colocation services, claiming to host nearly 2,500 servers across 30 hosting providers in 82 countries. MaxiDed advertised itself as a bulletproof hosting provider, a term used to describe hosting companies that ignore reports of criminal activity or copyright infringement happening on their servers.
…Binary SMS – The old backdoor to your new thing

SMS is a weak link in a handset’s security. With it you can interact, remotely, with an application on someone’s phone when the phone is not connected to the internet: Despite being older than many of its users, Short Messaging Service (SMS) remains a very popular communications medium and is increasingly found on remote sensors, critical infrastructure and vehicles due to an abundance of cellular coverage.
…Brutal cryptocurrency mining malware crashes your PC when discovered

A new form of cryptominer has been discovered which crashes systems the moment antivirus products attempt to remove the malware. The malware, dubbed WinstarNssmMiner by 360 Total Security researchers, has been used in half a million attempted attacks leveraged at PCs in only three days. On Wednesday, the cybersecurity firm said the cryptomining malware aims to infect PCs in order to steal processing power for the purpose of mining the Monero cryptocurrency.
…