Cyber security news and services
Hardcoded Password Found in Cisco Enterprise Software, Again

Cisco released 16 security advisories yesterday, including alerts for three vulnerabilities rated ‘Critical’ and which received a maximum of 10 out of 10 on the CVSSv3 severity score. The three vulnerabilities include a backdoor account and two bypasses of the authentication system for Cisco Digital Network Architecture (DNA) Center. The Cisco DNA Center is a piece of software that’s aimed at enterprise clients and which provides a central system for designing and deploying device configurations (aka provisioning) across a large network.
…Adware Launches In-Browser Mining Sites Pretending to be Cloudflare
FileTouris an adware bundle that is commonly spread as cracks or cheats for games and other software. This bundle is notorious for crossing the line between what is traditionally known as adware and PUPs and more dangerous computer infections such as password-stealing Trojans and miners. This adware bundle has started to create a Windows autorun that automatically launches Chrome and connects to a in-browser mining page when a user logs into Windows.
…Mexican central bank confirmed that SWIFT hackers stole millions of dollars from Mexican Banks

Mexican central bank is the last victim of the SWIFT hackers, officials at the bank confirmed this week that hackers hit the payments system and stole millions of dollars from domestic banks. The attack was discovered in late April and presents many similarities with past attacks against the SWIFT systems. The Mexican central bank did not disclose the name of the banks that were hit by the cyber attack and did not detail the overall amount of money that crooks have stolen.
…Inside the Takedown of Scan4You, a Notorious Malware Clearinghouse
Most antivirus scanners play a classic cat and mouse game: They work by checking software against a frequently updated list of potential threats. In response, a whole industry has built up to help occlude and conceal hacking tools. That includes services that automate the process of checking all sorts of tools, from malware to malicious URLs, against dozens of defense scanners to see if they would get blocked.
…Forget scanning license plates; cops will soon ID you via your roof rack

Such a vast expansion of the tech now means that evading such scans will be even more difficult. For years, Ars has been reporting on automated license plate readers (ALPRs, or simply LPRs)—a specialized camera often mounted on police cars that can scan at speeds of up to 60 plates per second. Those scans are compared against what law enforcement usually dubs a ‘hot list’ before alerting the officer to the presence of a potentially wanted or stolen vehicle.
…Hacker Breaches Securus, the Company That Helps Cops Track Phones Across the US

A hacker has broken into the servers of Securus, a company that allows law enforcement to easily track nearly any phone across the country, and which a US Senator has exhorted federal authorities to investigate. The hacker has provided some of the stolen data to Motherboard, including usernames and poorly secured passwords for thousands of Securus’ law enforcement customers. Although it’s not clear how many of these customers are using Securus’s phone geolocation service, the news still signals the incredibly lax security of a company that is granting law enforcement exceptional power to surveill individuals.
…Telegrab malware hijacks Telegram desktop sessions

Researchers have revealed new malware designed to collect information from messaging service Telegram. On Wednesday, Cisco Talos researchers Vitor Ventura and Azim Khodjibaev said that over the past six weeks, the team has monitored the emergence of what has been called Telegrab. This malware has been designed to collect cache and key files from Telegram, an end-to-end encrypted messaging service.
The malicious code was first spotted in the wild on 4 April 2018, and a second variant emerged only six days later. While the first version of Telegrab only stole text files, browser credentials, and cookies, the second also added new functionality which allowed the malware to collect data from Telegram’s desktop cache — alongside Steam login credentials — in order to hijack active Telegram sessions. The malware impacts the desktop version of Telegram.
…RedHat DHCP remote root execution vulnerability

A command injection bug in Red Hat’s DHCP client could allow an attacker to run any command on your computer. As root. RedHat Linux, together with its stablemates Fedora and CentOS, just patched a serious security bug.
RedHat-based Linux distros include a dhclient script as part of their NetworkManager package – until the latest NetworkManager security patch, this script could be tricked into running text provided in a DHCP reply as if it were a system command of its own. Technically, this sort of bug is known as a command injection vulnerability, because it allows you to sneak in a command where you are supposed to supply data. It’s also a root RCE, short for remote code execution, because you don’t need to login first, and because you get to run the remotely supplied code as a system administrator.
…Hacker Publicly Posts Data Stolen From Government-Linked Cyberespionage Group

Last week, Motherboard reported that a vigilante hacker had stolen data from a hacking group that researchers say is a government-linked cyberespionage unit. The data included GPS locations, text messages, and phone calls that the group had taken from their own victims. Now, that hacker has seemingly published the stolen data online for anyone to download.
The act itself highlights not only the fact that government hackers can sometimes face retribution, but also the ethical issues that come along with releasing such data to the public. The stolen files were seemingly from a server controlled by the so-called ZooPark group, a hacking outfit that cybersecurity researchers from Kaspersky revealed earlier this month in a report. At the time of the breach, Motherboard cross-referenced the stolen material with details in that Kaspersky report to corroborate the ZooPark link.
…Feds Raid Apartment of Suspected CIA Leaker, Find 10,000 Images of Child Porn

In March 2017, the FBI agents raided the Manhattan apartment of former NSA and CIA operative Joshua Schulte looking for top secret documents and hacking tools that the defendant allegedly leaked to WikiLeaks. We don’t know if they found what they were looking for, but according to court transcripts and documents reviewed by Motherboard, the feds did find at least 10,000 images of child porn on his personal computer, and an IRC-focused file-sharing server that had at least 5 terabytes of data on it. Roughly two weeks before the raid, on March 7, 2017, WikiLeaks started releasing top secret documents allegedly stolen from a CIA hacking group.
…Inside the business model for botnets
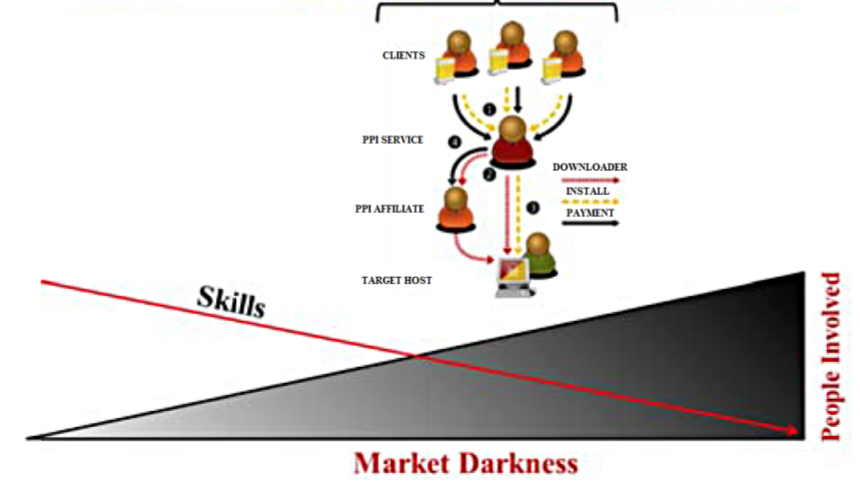
Botnets are shadowy networks of computers controlled by hidden actors and linked to everything thatâs bad on the web. They have been implicated in distributed denial-of-service attacks, spamming campaigns, click fraud, and bank fraud, to name just a few of the nastiest flavors of cybercrime. Clearly somebody, somewhere is making a fortune masterminding this kind of criminal activity.
Today we get an answer of sorts thank to the work of C.G.J. Putman at the University of Twente in the Netherlands and a couple of colleagues. âIt comes as no surprise that the primary motive for the use of botnets is for economic gain,â they say as they map out the costs and revenue streams. All that leads to a rough estimate of the cost of setting up a botnet on a national or international scale.
…Hiding Information in Plain Text
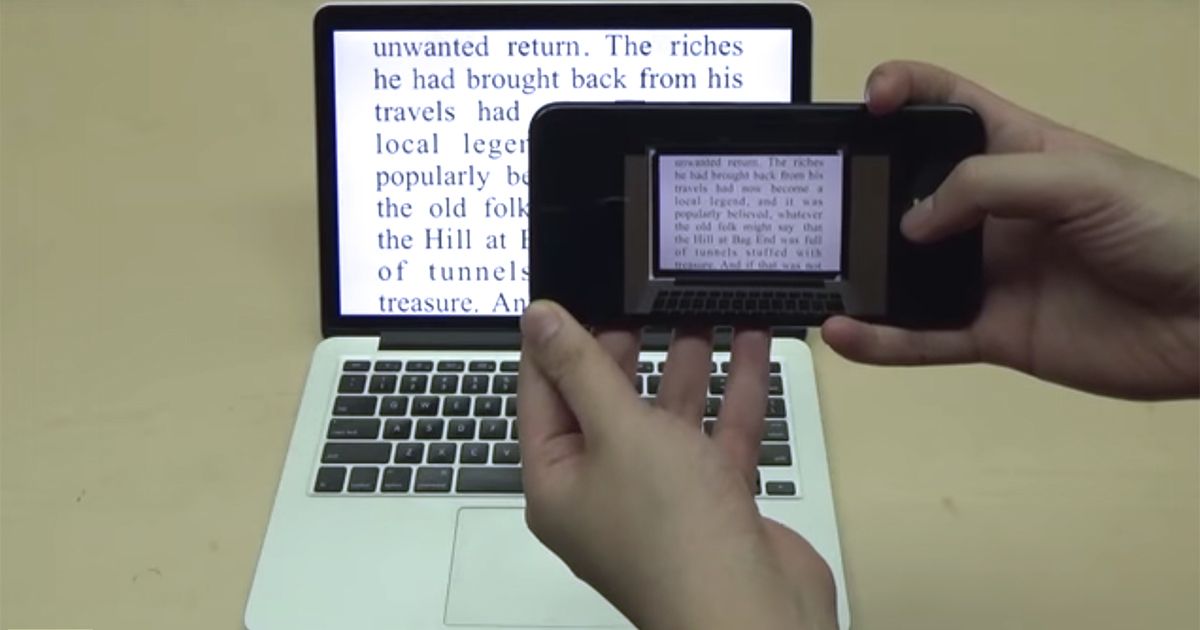
Computer scientists have now invented a way to hide secret messages in ordinary text by imperceptibly changing the shapes of letters. The new technique, named FontCode, works with common font families such as Times Roman and Helvetica. It is compatible with most word-processing software, including Microsoft Word, as well as image-editing and drawing programs, such as Adobe Photoshop and Adobe Illustrator.
FontCode embeds data into texts using minute perturbations to components of letters. This includes changing the width of strokes, adjusting the height of ascenders and descenders, and tightening or loosening the curves in serifs and the bowls of letters such as o, p, and b. A kind of artificial-intelligence system known as a convolutional neural network can recognize these perturbations and help recover the embedded messages. The amount of information FontCode can hide is limited only by the number of letters on which it acts, the researchers say.
…A tale of two zero-days

Late in March 2018, ESET researchers identified an interesting malicious PDF sample. A closer look revealed that the sample exploits two previously unknown vulnerabilities: a remote-code execution vulnerability in Adobe Reader and a privilege escalation vulnerability in Microsoft Windows. The use of the combined vulnerabilities is extremely powerful, as it allows an attacker to execute arbitrary code with the highest possible privileges on the vulnerable target, and with only the most minimal of user interaction.
…US cell carriers are selling access to real-time phone location data

Four of the largest cell giants in the US are selling your real-time location data to a company that you’ve probably never heard about before. In case you missed it, a senator last week sent a letter demanding the Federal Communications Commission (FCC) investigate why Securus, a prison technology company, can track any phone ‘within seconds’ by using data obtained from the country’s largest cell giants, including AT&T, Verizon, T-Mobile, and Sprint, through an intermediary, LocationSmart. The story blew up because a former police sheriff snooped on phone location data without a warrant, according The New York Times.
…Turkey’s Government Tried to Hack Hundreds of Protesters Over Twitter, Researchers Say

Hackers—apparently working for the Turkish government— attempted to infect a large number of Turkish dissidents and protesters by spreading spyware on Twitter, according to a new report by digital rights organization Access Now. The organization’s researchers found seven new samples of spyware made by the infamous surveillance tech vendor FinFisher. One of them targeted several Turkish protesters who attended a large series of protests against the government of Recep Tayyip Erdoğan in June and July 2017, known as the March for Justice, according to the report.
…Detecting Cloned Cards at the ATM, Register
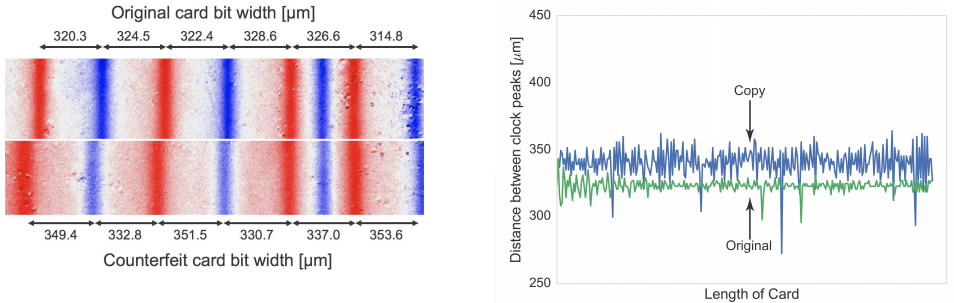
Researchers at the University of Florida found that account data encoded on legitimate cards is invariably written using quality-controlled, automated facilities that tend to imprint the information in uniform, consistent patterns. Cloned cards, however, usually are created by hand with inexpensive encoding machines, and as a result feature far more variance or “jitter” in the placement of digital bits on the card’s stripe. Gift cards can be extremely profitable and brand-building for retailers, but gift card fraud creates a very negative shopping experience for consumers and a costly conundrum for retailers.
…Second wave of Spectre-like CPU security flaws won’t be fixed for a while

The new bunch of Spectre-like flaws revealed last week won’t be patched for at least 12 days. German outlet Heise, which broke news of the eight Spectre-like vulnerabilities last week has now reported that Intel wants disclosure of the flaws delayed until at least May 21. Last week, Heise noted that one participant in the planned coordinated release would include a Google Project Zero disclosure, which as far as The Register can discern has not yet happened.
…The World’s First Trade Finance Transaction on the Blockchain Involves Soybeans

Here’s what happened: HSBC issued a letter of credit for U.S. food and agriculture firm Cargill to Dutch lender ING. The trade finance transaction involved a shipment of soybeans from Argentina to Malaysia. Using blockchain technology, this letter is stored on an open, distributed ledger where every transaction is visible to anyone with access to the system.
This eliminates the need for paper reconciliation and a long chain of digital (and paper) communication between the two parties. HSBC and ING said the exchange was performed in 24 hours, whereas it normally takes five to 10 days for such a transaction to go through traditional methods. HSBC used the “Corda” platform, which was developed by blockchain company R3.
…Rail Europe had a three-month long credit card breach

If you booked train tickets for a European getaway in the past few months, you might want to check your bank statements. Rail Europe, a site used by Americans to buy train tickets in Europe, has revealed a three-month data breach of credit cards and debit cards. The announcement came in a letter filed with the California attorney general, in which the company said hackers put credit card-skimming malware on its website between late-November 2017 and mid-February 2018.
…EFail – Vulnerabilities in end-to-end encryption technologies OpenPGP and S/MIME

The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs. To create these exfiltration channels, the attacker first needs access to the encrypted emails, for example, by eavesdropping on network traffic, compromising email accounts, email servers, backup systems or client computers.
…