Cyber security news and services
There’s a New Cold War Brewing in Space

Much of the push to formalize an off-planetbranch of the U.S. armed forces is motivated by space investment by Russia and China, the latter of which is eager to establish itself as a superpower with plans for an orbiting space station and a permanent outpost on the moon. Meanwhile, Russiaunder President Vladimir Putinhas become increasingly aggressive, annexing Crimea, deploying more sophisticated nuclear weapons and waging conventional warfarein eastern Ukraine and Syria. But he, too, has aspirations, albeit troubled ones, up above.
…Best Buy will stop selling Huawei smartphones

Huawei was widely expected to announce a partnership with AT&T in January at CES to carry the Mate 10 Pro smartphone, but the carrier reportedly backed out because of political pressure. A few days later, Verizon reportedly nixed its own plans to sell Huawei phones. Instead, Richard Yu, CEO of the company’s consumer business, spent his time talking about the phones, which were already in the market elsewhere, as well as touting the Porsche Design variant of the smartphone.
…Non-Lethal Weapon: DOD seeks to use lasers to create shouting will-o-the-wisp
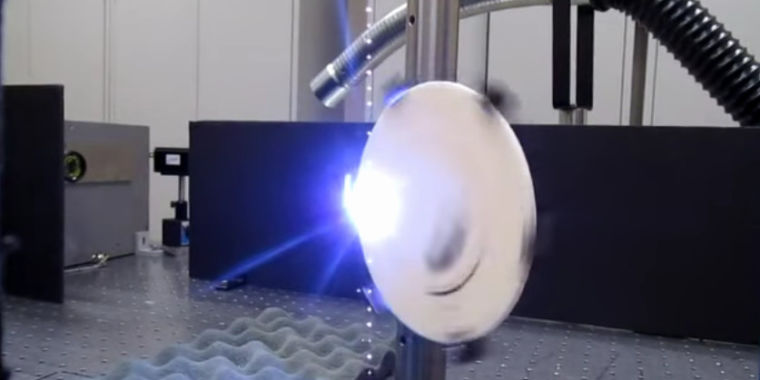
The Non-Lethal Laser-Induced Plasma Effect (NL-LIPE) system can be used to manipulate air molecules, creating a ball of plasma that oscillates to create sound waves with a stream of femtosecond-long laser bursts. A first laser creates the plasma ball, and a second then oscillates the plasma ball to create the sound. As Defense One’s Patrick Tucker reports, the current Laser-Induced Plasma Effect implementation can only manage an indistinguishable mumble—though it can create a wide variety of very distinguishable sounds, as demonstrated in the video below.
…Best bad idea ever? Why Putin’s nuclear-powered missile is possible… and awful
Russia’s advanced arms are based onthecutting-edge, unique achievements ofour scientists, designers, andengineers. One ofthem is asmall-scale, heavy-duty nuclear energy unit that can be installed inamissile like our latest X-101 air-launched missile ortheAmerican Tomahawk missile—asimilar type but with arange dozens oftimes longer, dozens—basically anunlimited range. It is alow-flying stealth missile carrying anuclear warhead, with almost anunlimited range, unpredictable trajectory andability tobypass interception boundaries.
…Google is working on their own Blockchain

By using the blockchain as a layer over its cloud infrastructure for providing data integrity and protection, Google would seek to gain an advantage over its cloud competitors such as AWS, Azure etc and eliminate the risks that appear by being one of the largest data centers in the world.
Source: blockmanity.com
…What is a DAPP?

A DAPP (Decentralized Application) consists of back-end code that runs on a decentralized peer-to-peer network. A DAPP can also have a user interface, created by front end code that makes calls to the back end. DAPPs do not require a central authority to function: they allow for direct interaction between users and providers.
Source: towardsdatascience.com
…Multiversum: This is What a 4th-Generation Blockchain Looks Like

The 4th generation of blockchain is at our doorsteps and it promises to bring us closer to mass adoption than ever before. But before we delve into that, let’s quickly look at the 3 evolutionary phases blockchain technology has gone through since 2008.
Source: medium.com
…SXSW 2018: 10 Crypto & Blockchain Takeaways

As you may know, SXSW is a conference and festival that celebrates the convergence of the interactive, film, and the music industry. This year SXSW took place March 9th through 18th and attracted 300,000 people to Austin, TX. And, let me tell you, a big chunk of them were blockchain enthusiasts.
Source: hackernoon.com
…YouTube’s fake views economy
Views are the currency of YouTube. More views often translates into a higher ranking in user search results, or better circulation numbers in the sidebar, both of which affect the amount of money YouTubers make via ad impressions. What’s more, they’re the measure by which the outside world assigns worth, a credential that makes them more visible to vulnerable populations with malleable views.
A high view count carries with it an air of legitimacy — approval from both YouTube and its users alike. It’s what users are supposed to strive for.
…FBI raids home of spy sat techie over leak of secret comms source code on Facebook

On Monday, the Feds confirmed to The Register they have executed a search warrant at the Virginia home of John Glenn Weed, who worked for the National Reconnaissance Office – which runs Uncle Sam’s spy satellite fleet. The NRO called in the g-men after a screenshot of its classified source code was posted in 2017 on a Facebook profile belonging to one William Amos.
…SwissRealCoin promises a stable cryptocurrency backed by Swiss real estate

Liquidity and volatility are two issues that dog almost every blockchain technology startup and cryptocurrency, which is why “stablecoins” are becoming popular. Backed by gold, oil, fiat, and other, more established currencies, assets, and utilities, stablecoins offer an interesting alternative to regular cryptocurrencies.
Source: venturebeat.com
…Facebook’s Cambridge Analytica scandal, explained

Last Friday, reporters from The New York Times and The Observer of London told Facebook that Cambridge had retained copies of private data for about 50 million Facebook users. Facebook says Cambridge promised in 2015 that the data would be deleted. Facebook responded to the new revelations by banning Cambridge and several of its associates from Facebook.
Source: arstechnica.com
…Chinese Companies Are Buying Up Cash-Strapped U.S. Colleges

Chinese companies are taking advantage of America’s financially strapped higher-education system to buy schools, and the latest deal for a classical music conservatory in Princeton, New Jersey, is striking chords of dissonance on campus.
Source: bloomberg.com
…Canada Is Gearing Up to Regulate Cryptocurrency

The main concern for proponents of cryptocurrency is that regulation will be introduced in a way that will stifle innovation in the sector, as Hamel tweeted before the hearing. In China, a major hub for cryptocurrency innovation and infrastructure, the government has begun to ramp up a widespread clampdown on cryptocurrency. For example, last year the government restricted trading on exchanges, pushing market leaders OKCoin and Huobi to launch cryptocurrency-only sites, OKex and Huobi Pro respectively.
…15-Year-old Finds Flaw in Ledger Crypto Wallet

Hardware wallets like those sold by Ledger are designed to protect the user’s private keys from malicious software that might try to harvest those credentials from the user’s computer. The devices enable transactions via a connection to a USB port on the user’s computer, but they don’t reveal the private key to the PC.
Source: krebsonsecurity.com
…Lightning on Stellar: Technical Spec and Roadmap

Lightning is a scaling solution for distributed payment networks, originally proposed for the Bitcoin blockchain. Lightning is designed to allow users to make off-chain payments through routers and hubs. Lightning even has the potential to support cross-protocol payments, such as a payment where the sender sends Bitcoins on the Bitcoin network and the recipient receives lumens on the Stellar network, without having to trust any parties in between.
…Telegram forced to give encryption keys to Russian authorities

Telegram, founded by Russian entrepreneur Pavel Durov, has been fighting an effort by the FSB, the state’s security service formerly known as the KGB, which last year demanded that the company hand over its private encryption keys.
Source: zdnet.com
…The NSA Worked to “Track Down” Bitcoin Users, Snowden Documents Reveal

Classified documents provided by whistleblower Edward Snowden show that the National Security Agency indeed worked urgently to target bitcoin users around the world — andwielded at least one mysterious source of information to “help track down senders and receivers of Bitcoins,” according to a top-secret passage in an internal NSA report dating to March 2013. The data source appears to have leveraged the NSA’s ability to harvest and analyze raw, global internet traffic while also exploiting an unnamedsoftware programthat purported to offer anonymity to users, according to other documents.
…Orbitz says hacker stole two years’ worth of customer data

The travel booking site said about 880,000 payment cards were affected. According to the statement, the company found evidence in March that an attacker had access to the company’s legacy systems between October and December last year. It was during that time the hacker accessed customer data from the previous two years — between January 2016 and December 2017 — which included names, dates of birth, postal and email addresses, gender, and payment card information.
…US spy lab wants to geolocate any video or photo taken outdoors

If the cave happened to be around the corner from the town library or a Starbucks, you might be in luck. Then, you could get help from something like Google PlaNet: a deep-learning machine that was initially trained on 126 million photos with EXIF data in order to learn how to work out the location of almost any photo, just going by its pixels, no EXIF data needed.
…