Jun. 15, 2018

Seventeen malicious Docker containers earned cryptomining criminals $90,000 in 30 days in what could be a harbinger of things to come. The figure may seem tame compared to some of the larger paydays that cryptojackers have earned. But, researchers at Kromtech Security Center warn containers are shaping up to be the next ripe target for these types of criminals.
Kromtech said the malicious Docker images (17 in total) were pulled down from the Docker Hub image repository. Researchers can’t say for sure how many times the rogue containers were used by Docker Hub users, but Kromtech estimates that the 17 images were downloaded collectively 5 million times during the year they were available. All 17 were removed from Docker Hub on May 10 by Docker, afterFortinetfound the containers and published a report on the images being used to mine cryptocurrency.
May. 30, 2018
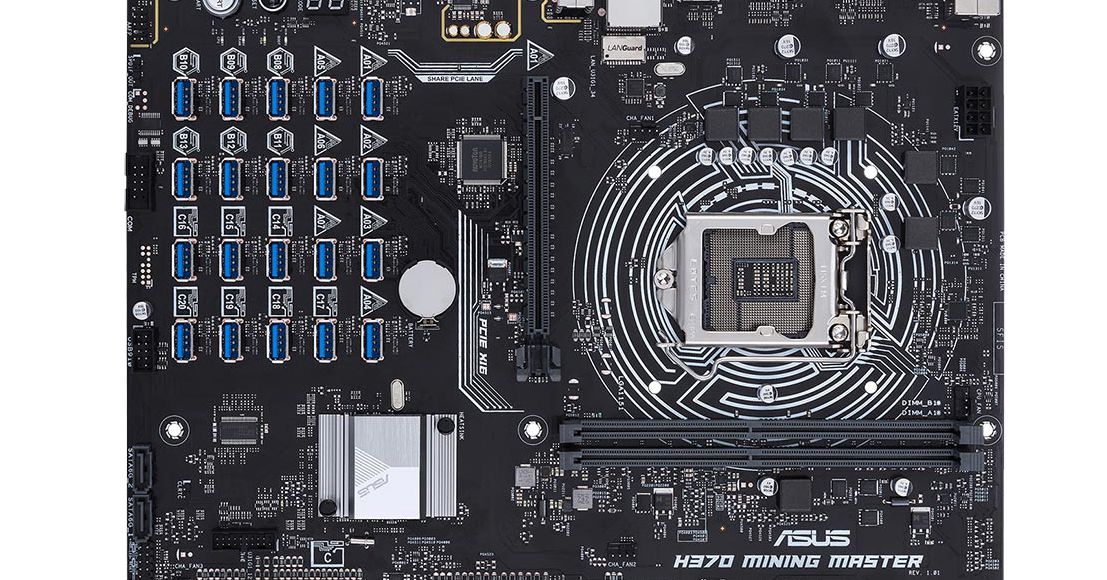
Asus announced the H370 Mining Master motherboard, which is specifically designed for cryptocurrency mining. It supports up to 20 graphics cards along with streamlined connectivity by allowing USB riser cables to plug directly into the PCB over PCIe. Asus announced the H370 Mining Master motherboard today, which is specifically designed for cryptocurrency mining.
It supports up to 20 graphics cards — yes, 20 — along with streamlined connectivity by allowing USB riser cables to plug directly into the PCB over PCIe. Asus’ approach here is going to make maintenance easier, ensure fewer PCIe disconnects, and more accurate diagnostics. This is a better format than just plugging in graphics cards to the motherboard via PCIe, like you would in a gaming desktop, the company says.
May. 28, 2018

Public hearings for rural electric utilities are rarely sellout events. But the crowd that showed up in Wenatchee two weeks ago for a hearing about Bitcoin mining in Chelan County was so large that utility staff had to open a second room with a video feed for the overflow. As a result, an area famous for apples, wheat and conservative politics has been transformed into a kind of cyber-boomtown, with Bitcoin mining operations that range from large-scale, state-of-the-art warehouses to repurposed cargo containers to backyard sheds.
May. 18, 2018
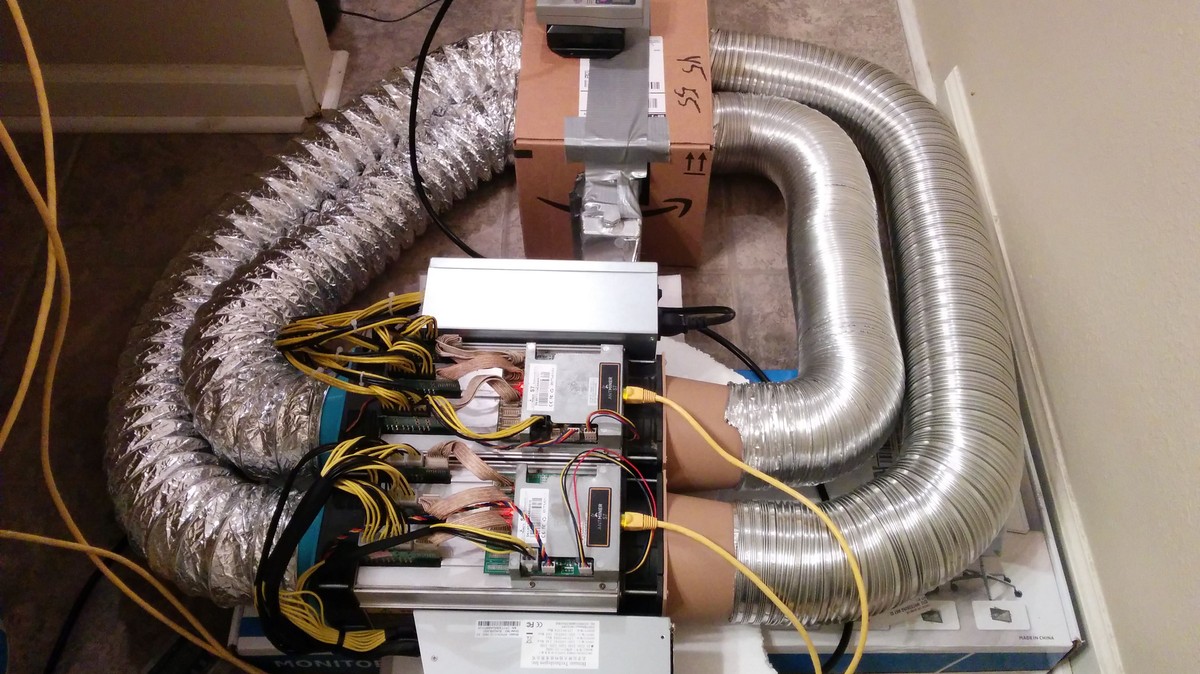
For hobbyists trying to strike it rich with cryptocurrency mining, but who don’t have access to gigantic warehouses where they can park the hardware, making money means packing a bunch of very loud and very hot computers into your house or apartment. Some at-home cryptocurrency miners are harnessing the heat that powerful mining equipment—called ASICs—give off. Motherboard’s Daniel Oberhaus used mining equipment (albeit graphics cards, not ASICs) to stay warm during a storm once, and a Redditor posting under the handle “gta3uzi” just took it to another level.
May. 17, 2018
FileTouris an adware bundle that is commonly spread as cracks or cheats for games and other software. This bundle is notorious for crossing the line between what is traditionally known as adware and PUPs and more dangerous computer infections such as password-stealing Trojans and miners. This adware bundle has started to create a Windows autorun that automatically launches Chrome and connects to a in-browser mining page when a user logs into Windows.
May. 12, 2018
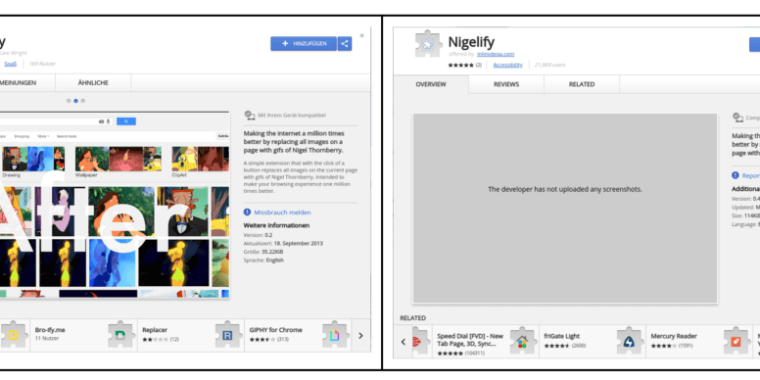
The extensions were being pushed in links sent over Facebook that led people to a fake YouTube page that asked for an extension to be installed. Once installed, the extensions executed JavaScript that made the computers part of a botnet. The botnet stole Facebook and Instagram credentials and collected details from a victim’s Facebook account.
The botnet then used that pilfered information to send links to friends of the infected person. Those links pushed the same malicious extensions. If any of those friends followed the link, the whole infection process started all over again.
May. 9, 2018

Security researcher Charles Dardaman explains on his blog, how he was able to use Microsoft’s own documentation of how to use JavaScript functions in the Insider Preview edition of Excel to link a spreadsheet to the Coinhive cryptomining service. Right now, JavaScript in Excel custom functions is only supported in the Developer Preview edition to Office 365 subscribers enrolled in the Office Insiders program. But it seems inevitable that in the not too distant future it will be available in more widely-used versions of Excel as well.
May. 9, 2018

On Monday, Bitcoin ABC said in a security advisory that a critical vulnerability has been found in Bitcoin ABC version 0.17.0 which has the potential to cause an unintended split in the Bitcoin Cash network. In order to exploit the vulnerability, an attacker would need to construct a malicious transaction which could be accepted into Bitcoin ABC and consequently mined into a block. Once this block has been established, the block would then reject all other versions of Bitcoin Cash compliant implementations.
May. 8, 2018
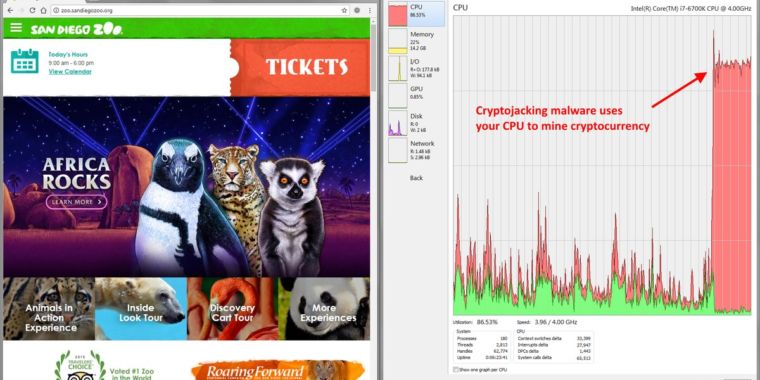
A mass hacking campaign that targets a critical vulnerability in the Drupal content management system has converted more than 400 government, corporate, and university websites into cryptocurrency mining platforms that surreptitiously drain visitors’ computers of electricity and computing resources, a security researcher said Monday. Sites that were hacked included those belonging to computer maker Lenovo, the University of California at Los Angeles, the US National Labor Relations Board, the Arizona Board of Behavioral Health Examiners, and the city of Marion, Ohio, Troy Mursch, an independent security researcher, told Ars on Monday. The Social Security Institute of the State of Mexico and Municipalities, the Turkish Revenue Administration, and Peru’s Project Improvement of Higher Education Quality were also affected.
May. 4, 2018

Once the malware has been installed, it sets about mining for Monero and hooking up with a crypto-wallet and mining pool; it also connects with its C2 server for updates, and configures itself to infect other machines on the network. Meanwhile, a short VisualBasic script is used to deploy the malware to compromised Apache Struts servers, and it moves laterally by replicating itself like a worm. MassScan meanwhile passes a list of both private and public IP ranges to scan during execution, to find fresh server targets out on the web that it can break into with the SQLck brute-force tool.
May. 4, 2018

Kitty, a Monero cryptocurrency which utilizes open-source mining software for browsers, executes a bash script, kdrupal.php, which is written to an infected server disc. This then establishes a backdoor into an infected system separate from the Drupal vulnerability.
Source: zdnet.com
May. 3, 2018
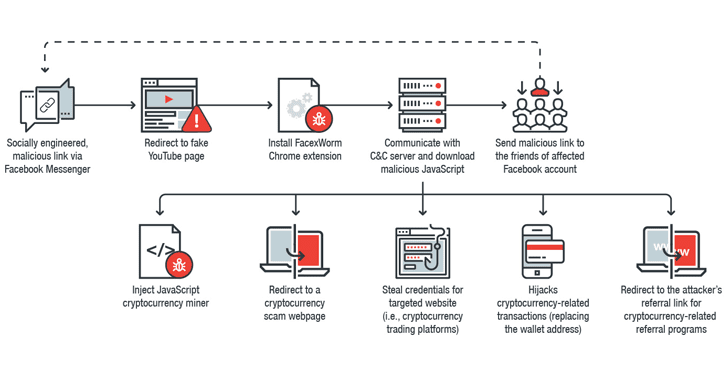
To spread itself further like a worm, the malware requests OAuth access token for the Facebook account of the victim, using which it then automatically obtains the victim’s friend list and sends that malicious, fake YouTube video link to them as well.
Source: thehackernews.com
Apr. 27, 2018
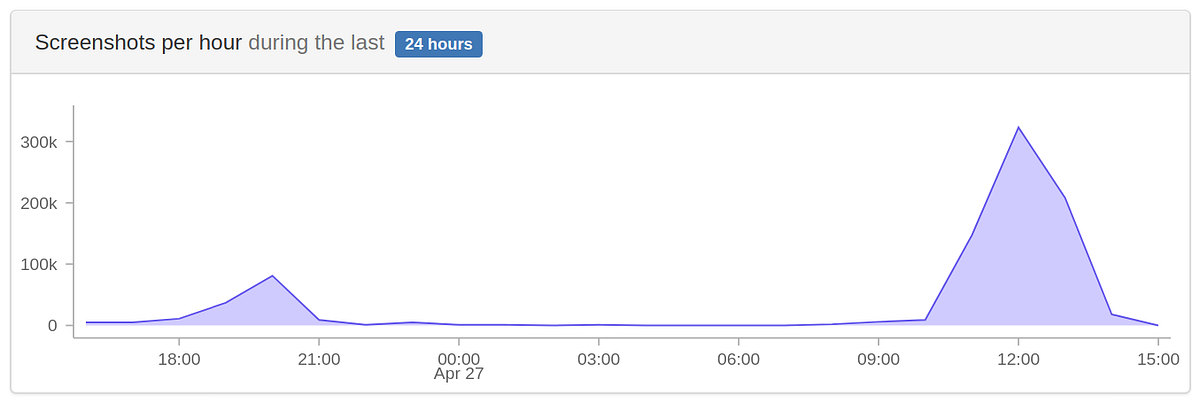
This morning when I opened up my inbox, I had around 150 alert emails from the the logging tool I use. I immediatly though I must have pushed a nasty bug to production and started investigating. I quickly realized some guy was creating new accounts really fast on our screenshot API service and was rapidly using all the free plan credit.
Apr. 22, 2018

Coin burning, if you’re not familiar, is a well-trod path to inflating the value of a cryptocurrency with a fixed supply, like Bitcoin Cash. The value of coins with a fixed supply is based on increasing demand and steadily decreasing supply. If you can accelerate the diminishment of available coin stock, then theoretically that should increase demand for the remaining supply and, in turn, the coin’s value.
Apr. 10, 2018

Cryptocurrency miners are always looking for a way to save on electricity costs. Sometimes that involves funding huge mining operations moving to small towns to take advantage of cheap hydro power, or developing obscure mining rig set ups that use Teslas or human body heat as their source of power.
Source: vice.com
Apr. 10, 2018

On April 6, Monero tweaked its mining algorithm “to curb any potential threat of ASICs and preserve ASIC resistance.” That same day, Ethereum core developers met to discuss whether they should change Ethereum’s algorithm and ultimately decided not to for the time being, much to the chagrin of the Ethereum community.
Source: vice.com
Apr. 5, 2018
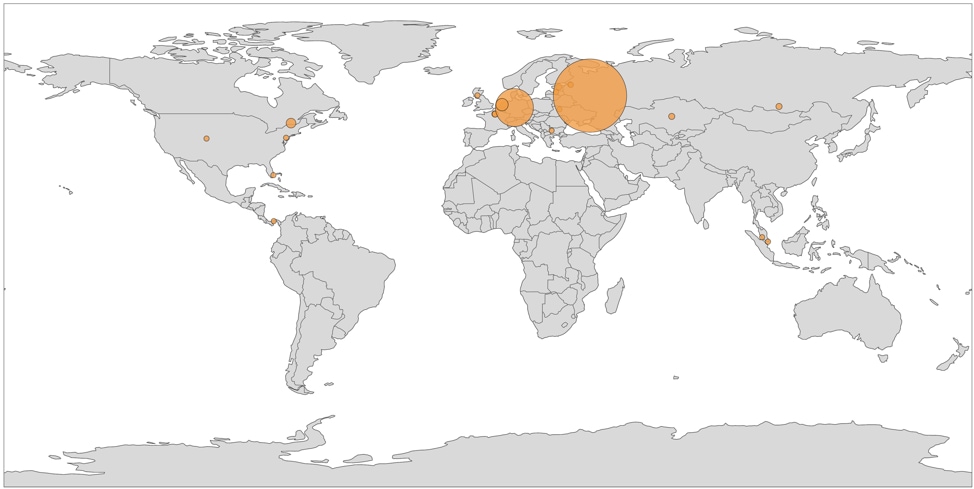
Rarog has been seen primarily used to mine the Monero cryptocurrency, however, it has the capability to mine others. It comes equipped with a number of features, including providing mining statistics to users, configuring various processor loads for the running miner, the ability to infect USB devices, and the ability to load additional DLLs on the victim.
Source: paloaltonetworks.com
Apr. 4, 2018

In recent months, the topic of cryptocurrency has been a permanent news fixture — the value of digital money has been see-sawing spectacularly. Such pyrotechnics could hardly have escaped the attention of scammers, which is why cryptocurrency fluctuations have gone hand in hand with all kinds of stories. These include hacked exchanges, Bitcoin and Monero ransoms, and, of course, hidden mining.
Source: securelist.com
Apr. 4, 2018
In theory, cryptojacking can be used for legitimate purposes, like raising revenue for a publishing platform or collecting funds for charitable causes. But in practice, the technology has largely been implemented maliciously, or at least secretly, consuming processing resources on victim devices and potentially interfering with and damaging these targets. Bad actors can use locally installed malware to steal a victim device’s computing power, embed miners directly into websites to target casual web users without needing to install anything, or hide miners in the most innocuous applets and tools.
Mar. 31, 2018

As some solution providers explore the market for cryptocurrency mining rigs, Intel is looking into making a Bitcoin mining hardware accelerator that could reduce energy use and make the process more profitable.
Source: crn.com