Cyber security news and services
Bitcoin Core Developers kept a critical DoS bug, a secret; releases fix

Earlier this week, a bug was found in the Bitcoin’s core code base. Developers got in the rush, and finally released a fix on Tuesday. The bug turned out to be Denial of Service bug (DoS).
Furthermore, if anyone exploited the vulnerability, this could be used to disconnect nodes, or even crash a whole segment of a network. This was enough to rush the developers into action. The bug could be exploited by any miner, to double spend any transaction.
…Chrome is a Google Service that happens to include a Browser Engine

Starting with Chrome 69, logging into a Google Site is tied to logging into Chrome. This is typically the topic where things are complex enough that tweets or 500 character Mastodon toots don’t do it justice. I’d also mention that I prefer to avoid directly linking people’s posts on this, because I dislike the practice of taking discussions out of their original audience and treating them as official or semi-official communications from a given company.
…A perspective from the Bitcoin Cash and Bitcoin Unlimited developer who discovered CVE-2018–17144

Six hundred microseconds. That is about the time that Matt Corallo wanted to shave off of block validation with his pull request in 2016 to Bitcoin Core. 600µs is a lot less than what is saved with more efficient block propagation, like XThin, Compact Blocks, or now Graphene over typical links, especially those that are of similar low-end quality in network speed like Raspberry Pis are in compute speed.
…NCIX Database Servers Sold at Craigslist Without Being Wiped

Canadian retailer NCIX filed for bankruptcy and closed 10 months ago. They were the premiere PC hardware retail store in Canada and even did a sizable business on the other side of the border. However, as Travis Doering of Privacy Fly found out, the company did not go quietly away without doing some damage to their customer’s security first.
Doering recounts meeting up with a Craigslist seller claiming to have NCIX’ Database servers for only $1500 CAD. This includes a Database Server from NCIX and a Database Reporting Server, allegedly legally obtained via Able Auctions. Prior to NCIX shutting down, their assets were sold off through this company.
…Japanese crypto exchange Zaif hacked, losses in the range of $60 million reported

In a major development, Japanese crypto exchange Zaif has been on the receiving end of a hacking incident last week, local media has reported. The hack, which occurred on Sept. 14 but was not discovered until Sept. 17, saw the hacker steal 4.5 billion yen from users hot wallets, as well as 2.2 billion yen from the assets of the company, with total losses amounting to 6.7 billion yen or around $59.7 million. Tech Bureau Inc. which operates the digital currency exchange Zaif said in a press release that the company noticed certain abnormalities on September 17, and the hacking damage was confirmed on September 18.
…Another Victim of the Magecart Assault Emerges: Newegg

While the dust is settling on the British Airways compromise, the Magecart actor behind it has not stopped their work, hitting yet another large merchant: Newegg. Last week we published details on the British Airways compromise immediately after the company made its first advisory public linking the breach of customer credit card information to Magecart. We were able to disclose these details based on our years of tracking the activities and infrastructure of the umbrella of Magecart groups performing digital credit card skimming campaigns.
…Critical Bug Found in Bitcoin Core Invokes the Multiple Client Argument

Over the last 24 hours, the cryptocurrency community has been discussing a critical vulnerability that was found in the Bitcoin Core (BTC) reference client. A bug introduced in Bitcoin Core version 0.14, that also affects all subsequent versions, could have caused a great majority of current Core nodes to crash. According to the developer’s Optech newsletter, Core contributors released a patch that fixes Core version 0.16.2 and the latest 0.16.3 fix requires an immediate upgrade.
…EOS dApp Used Blockchain Backdoor To Remove Tokens From User’s Wallets Without Their Consent

EOS has recently been in the news following the revelation that an EOS decentralized application (dApp) could access users’ token wallets without their consent through the use of a backdoor technique. More specifically, this EOS dApp is called Trybe, and describes itself as a ”tokenized knowledge sharing network for the crypto and blockchain community”. Issues first arose when Trybe were set to distribute tokens to user accounts through a token airdrop.
…An Overview of the Different Blockchain Consensus Algorithms
Although more casual, less-technical crypto-enthusiasts might not know much on this topic, an essential aspect of any cryptocurrency project is the consensus algorithm that it utilizes. These algorithms accomplish two major objectives. Firstly, it ensures that the next block in a blockchain is the true, master-version of the details.
Secondly, it makes sure that those looking to take advantage of the system and fork the chain are stopped. Either way, the point is that consensus algorithms are the way that cryptocurrencies ensure that their digital tokens aren’t victim to double spending. While essential, there have emerged a wide variety of consensus algorithms amongst the various cryptocurrencies, each with their own pros and cons.
…Open Heart Surgery: Inside Ethereum’s Crucial Replacement of the EVM

The virtual machine that allows ethereum to compute everything in a decentralized way is getting a massive overhaul. At the heart of ethereum lies a virtual computer. Stored across tens of thousands of nodes that make up the platform, the ethereum virtual machine, or EVM, is responsible for executing the countless tokens,dapps, DAOs and digital kittens of which the blockchain is comprised of.
…Robinhood Is Making Millions Selling Out Customers to High-Frequency Traders
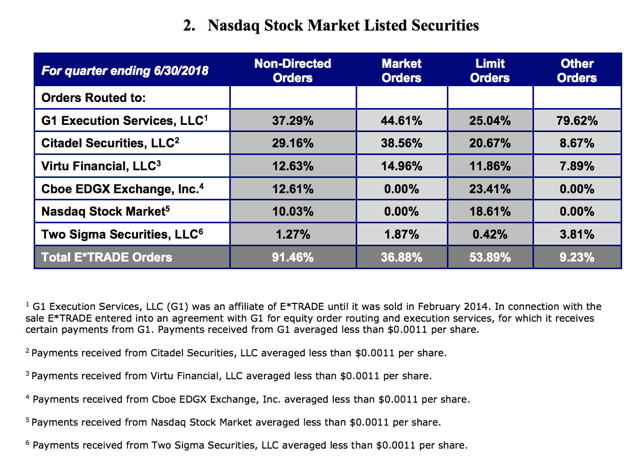
Robinhood is marketed as a commission-free stock trading product but makes a surprising percentage of their revenue directly from high-frequency trading firms. It appears from recent SEC filings that high-frequency trading firms are paying Robinhood over 10 times as much as they pay to other discount brokerages for the same volume. Robinhood needs to be more transparent about their business model.
…A new CSS-based web attack will crash and restart your iPhone

Sabri Haddouche tweeted a proof-of-concept webpage with just 15 lines of code which, if visited, will crash and restart an iPhone or iPad. Those on macOS may also see Safari freeze when opening the link. The code exploits a weakness in iOS’ web rendering engine WebKit, which Apple mandates all apps and browsers use,Haddouche told TechCrunch.
He explained that nesting a ton of elements — such astags — inside a backdrop filter property in CSS, you can use up all of the device’s resources and cause a kernel panic, which shuts down and restarts the operating system to prevent damage. TechCrunch tested the exploit running on the most recent mobile software iOS 11.4.1, and confirm it crashes and restarts the phone. Thomas Reed, director of Mac & Mobile at security firm Malwarebytes confirmed that the most recent iOS 12 beta also froze when tapping the link.
…Google’s prototype Chinese search engine reportedly links searches to phone numbers

Google is reportedly building a prototype system that would tie Chinese users’ Google searches to their personal phone numbers, as part of a new search service that would comply with the Chinese government’s censorship requirements. The Intercept writes that the “Dragonfly” Android app, a secret project revealed by a whistleblower last month, could be linked to a user’s phone number — making it simple to track individual users’ searches. This tracking would be in addition to Dragonfly’s blacklisting of terms like “human rights,” “student protest,” and “Nobel Prize,” which might normally pull up news about Chinese activist and Nobel laureate Liu Xiaobo.
…Tesla Model 3 Stolen From Mall of America Using Only a Smartphone

A little bit of social engineering can go a long way. With cars becoming more connected than ever, cybersecurity is a hot-button topic that extends past your computer screen and into your car. Using a bit of technology, an alleged car thief was able to get his hands on a Model 3 at the Mall of America and drive away without needing a key.
…Almost half of US cellphone calls will be scams by next year, says report

Many of us are already conditioned to ignore phone calls from unknown numbers. A new study seems to validate that M.O. By next year, nearly half of the mobile phone calls we get will be scams, according to a new report from First Orion, a company that provides calls management and protection forT-Mobile,MetroPCs,Virgin Mobileand others.
The percentage of scam calls in US mobile traffic increased from 3.7 percent last year to 29.2 percent this year, and it’s predicted to rise to 44.6 percent in 2019, First Orion said in a press release Wednesday. The most popular method scammers use to try to get people to pick up the phone is called ‘neighborhood spoofing,’ where they disguise their numbers with a local prefix so people presume the calls are safe to pick up, First Onion said. Third-party call blocking apps may help protect consumers from known scam numbers, but they can’t tell if a scammer hijacks someone’s number and uses it for scam calls.
…Bitmex Accused of Manipulating Ethereum’s Price
A crypto trading exchange with eye-watering margins of 100x has angered ethereans after Bitmex’s CEO, Arthur Hayes, appeared to tell his customers, under an official Bitmex account, to short eth. Hayes then goes on to use some very colorful and highly professional language in contrast to his public tweet which said: No punting here, but to all the Bitmex customers, which are automatically subscribed to a “newsletter,” he told them eth is “a double digit” colorful coin. In other words, Bitmex hates ethereum and as of today Bitmex is apparently handling $3 billion in trading volumes for the eth/usd perpetual swap.
…In a Few Days, Credit Freezes Will Be Fee

Later this month, all of the three major consumer credit bureaus will be required to offer free credit freezes to all Americans and their dependents. Maybe you’ve been holding off freezing your credit file because your home state currently charges a fee for placing or thawing a credit freeze, or because you believe it’s just not worth the hassle. If that accurately describes your views on the matter, this post may well change your mind.
…Exploit vendor drops Tor Browser zero-day on Twitter

Zerodium, a company that buys and sells vulnerabilities in popular software, has published details today on Twitter about a zero-day vulnerability in the Tor Browser, a Firefox-based browser used by privacy-conscious users for navigating the web through the anonymity provided by the Tor network. In a tweet, Zerodium said the vulnerability is a full bypass of the ‘Safest’ security level of the NoScript extension that’s included by default with all Tor Browser distributions. NoScript is a browser extension that uses a whitelist approach to let the user decide from what domains the browser can execute JavaScript, Flash, Java, or Silverlight content.
…IBM secretly used New York’s CCTV cameras to train its surveillance software

New technology is making surveillance cameras more powerful than ever. Such systems are often developed away from the public eye, as detailed in a new report showing how IBM worked with the NYPD to create software that could search CCTV footage for individuals based on their skin tone. Features like searching for individuals based on age, gender, and skin tone IBM’s software was reportedly developed and tested on surveillance cameras run through the Lower Manhattan Security Initiative (pictured).
…Proof-of-Stake is a Rebranded Version of the Old Financial System

Over the last few years, there’s been a lot of projects, both public and private, that are attempting to create a next-generation blockchain or something better than Satoshi’s Bitcoin. A great majority of these projects have condemned proof-of-work (PoW) cryptocurrencies because they think they waste resources, and many of these new blockchains have chosen to use a proof-of-stake (PoS) system. However, PoS has many flaws and introduces a distribution process that advocates an ugly planned economy that’s propagated by ancient thinking and basically the old banking system.
…