Cyber security news and services
Doctor slammed by med board for selling $5 homeopathic sound waves for Ebola

The California medical board is threatening to revoke the license of Dr. William Edwin Gray III for selling homeopathic sound files over the Internet that he claims—without evidence or reason—can cure a variety of ailments, including life-threatening infections such as Ebola, SARS, swine flu, malaria, typhoid, and cholera. That leaves Gray’s fate entirely in the hands of the board, which will make a decision in coming weeks, according to the Times. Gray seemed unbothered by the prospect of losing his medical license.
…The FBI wants you to reboot your router NOW to help destroy a botnet
.jpg)
In a public service announcement published Friday and noted by Ars Technica, and a new addition to aUS Department of Justice press release, the FBI explains that it’s hoping that your actions will help the US government destroy a botnet before a Russian hacking group, Sofacy, can harden the malware’s defenses. How would pressing a button on your router help, though? According to the FBI, rebooting your router will destroy the part of the malware that can do nasty things like spy on your activities, while leaving the install package intact.
…Detecting Lies through Mouse Movements
The detection of faked identities is a major problem in security. Current memory-detection techniques cannot be used as they require prior knowledge of the respondent’s true identity. Here, we report a novel technique for detecting faked identities based on the use of unexpected questions that may be used to check the respondent identity without any prior autobiographical information.
While truth-tellers respond automatically to unexpected questions, liars have to “build” and verify their responses. This lack of automaticity is reflected in the mouse movements used to record the responses as well as in the number of errors. Responses to unexpected questions are compared to responses to expected and control questions (i.e., questions to which a liar also must respond truthfully).
…Blocking 500M Users Easier Than Complying with GDPR

For some of America’s biggest newspapers and online services, it’s easier to block half a billion people from accessing your product than comply with Europe’s new General Data Protection Regulation. With about 500 million people living in the European Union, that’s a hard ban on one-and-a-half times the population of the U.S. A&E Television Networks has narrowed its EU blockade to limit the damage to its audience. Websites for its History and Lifetime channels greet the European visitors with a message that its ‘content is not available in your area,’ whereas the website for youth-focused Viceland remains accessible.
…BackSwap malware finds innovative ways to empty bank accounts

To steal money from a victim’s account via the internet banking interface, typical banking malware will inject itself or its specialized banking module into the browser’s process address space. For many reasons, this is not an easy task – first of all, as mentioned before, the injection might be intercepted by a third-party security solution. The injected module also needs to match the bitness of the browser – a 32-bit module cannot be injected into a 64-bit browser process and vice versa.
…Z-Shave Attack Could Impact Over 100 Million IoT Devices
The Z-Wave wireless communications protocol used for some IoT/smart devices is vulnerable to a downgrade attack that can allow a malicious party to intercept and tamper with traffic between smart devices. The attack —codenamed Z-Shave— relies on tricking two smart devices that are pairing into thinking one of them does not support the newer S-Wave S2 security features, forcing both to use the older S0 security standard. An attacker that can trick a smart device into pairing with another device, a PC, or a smartphone app via the older S0 standard, can later decrypt all traffic exchanged between the two because the decryption key is widely known.
…Malware Found in the Firmware of 141 Low-Cost Android Devices

News of this group first surfaced after a report in December 2016, when Russian antivirus vendor Dr.Web disclosed that a mysterious threat actor had found a way to penetrate the supply-chain of several mobile carriers, infecting phones with malware. At the time, experts said they found malware in the firmware of at least 26 low-cost Android smartphone and tablets models. Once ousted, Dr.Web hoped crooks would pack up and move on to another operation.
…The Ethereum-blockchain size has exceeded 1TB, and yes, it’s an issue
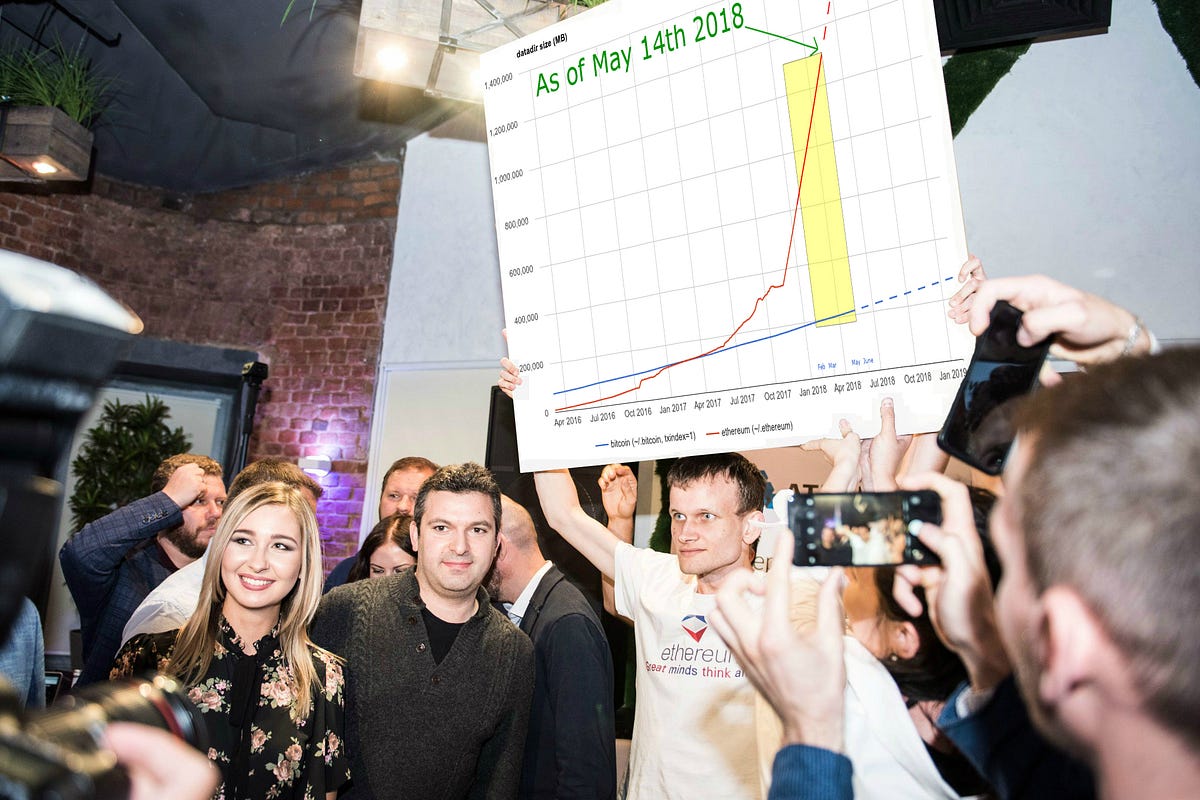
This is not about archival nodes. This is about about staying in sync, after the fact. My Argument: Ethereum’s runaway data directory size is just the tip.
My Prediction: It will all work, until it doesn’t. My Suggestion: Transpose. My Argument: Ethereum’s runaway data directory size is just the tip.
My Prediction: It will all work, until it doesn’t. My Suggestion: Transpose. My Argument:
…Blockchain vs. Distributed Ledger Technologies Part 2: Governing Dynamics

It should be acknowledged that if database coordination and more efficient allocation of code is the desired functionality of a system, then blockchain may not necessarily be the solution for which an organization is looking. Distributed ledger technology (DLT) systems like IBM Fabric or R3 Corda are capable of similar functionalities as blockchain systems, but it should be taken into consideration that blockchains are a separate subset of distributed ledgers that have additional functionality beyond code coordination. Blockchains are capable of functions that distributed ledgers are not in terms of instantiation of digital value based on the composition of the system.
…The DoJ is reportedly probing the murky world of bitcoin trading
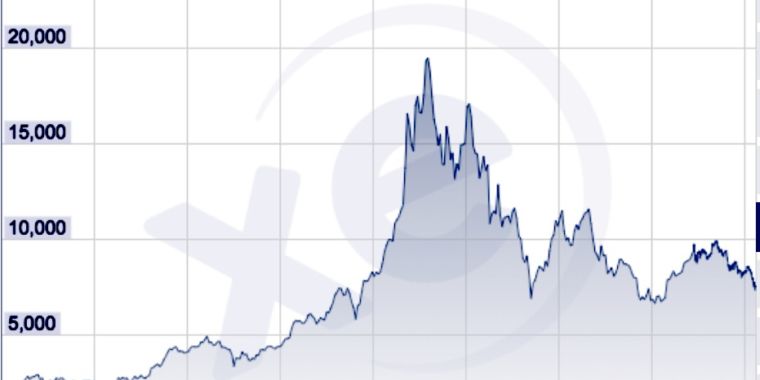
Bitcoin and other cryptocurrencies have taken a wild ride over the past 18 months. Now, according to Bloomberg News, the US Department of Justice has opened a criminal investigation into whether price manipulations have contributed to the meteoric rises and crushing falls. The coins prosecutors are examining include bitcoin and ether, which have both bounced up and down over the past 18 months.
…3 Charged In Fatal Kansas ‘Swatting’ Attack

Federal prosecutors have charged three men with carrying out a deadly hoax known as “swatting,” in which perpetrators call or message a target’s local 911 operators claiming a fake hostage situation or a bomb threat in progress at the target’s address — with the expectation that local police may respond to the scene with deadly force. While only one of the three men is accused of making the phony call to police that got an innocent man shot and killed, investigators say the other two men’s efforts to taunt and deceive one another ultimately helped point the gun. According to prosecutors,the tragic hoax started with a dispute over a match in the online game “Call of Duty.”
…The Pentagon Released New Documents About the ‘Tic-Tac UFO’

Now, a local investigative news team in Las Vegas obtained a 13-page document prepared for the military that analyzes what happened that day in 2004. The investigation was led by George Knapp, a journalist who made a name for himself in the 80s for substantiating parts of a story peddled by the prominent UFOlogist Bob Lazar, who claimed to have worked at Area 51. The report describes how the Anomalous Aerial Vehicle (AAV) seen by the two F18 pilots were able to “descend ‘very rapidly’ from approximately 60,000 feet down to approximately 50 feet in a matter of seconds.”
…Woman says Amazon recorded private conversation, sent it out to random contact

A Portland family contacted Amazon to investigate after they say a private conversation in their home was recorded by Amazon’s Alexa — the voice-controlled smart speaker — and that the recorded audio was sent to the phone of a random person in Seattle, who was in the family’s contact list. A Portland family contacted Amazon to investigate after they say a private conversation in their home was recorded by Amazon’s Alexa — the voice-controlled smart speaker — and that the recorded audio was sent to the phone of a random person in Seattle, who was in the family’s contact list.
…Losses from BEC scams rising fast and furious

A new report by the FBI’s Internet Crime Complaint Center has shown that complaints about scams and fraud are rising now at a record high and have resulted in reported losses of up to $1.42 billion In a typical BEC scam, a criminal dupes a company’s finance department into carrying out an unauthorized transfer of funds. Importantly, the target must be fooled into believing that the request has come from an executive within the company or from an outside firm that does business with it, so the scam involves a measure of social engineering, email spoofing, or computer intrusion.
…Bitcoin Gold Hit by Double Spend Attack, Exchanges Lose Millions

A malicious miner successfully executed a double spend attack on the Bitcoin Gold network last week, making BTG at least the third altcoin to succumb to a network attack during that timespan. Bitcoin Gold director of communications Edward Iskra first warned users about the attack on May 18, explaining that a malicious miner was using the exploit to steal funds from cryptocurrency exchanges. To execute the attack, the miner acquired at least 51 percent of the network’s total hashpower, which provided them with temporary control of the blockchain.
…Sounds, pressure, brain injury: Case of US gov’t employee in China raises alert

The case draws eerie similarities to mysterious ‘health attacks’ in Cuba. The US government issued an alert Wednesday following reports that a government employee stationed in southern China experienced “subtle and vague, but abnormal, sensations of sound and pressure” and sustained a brain injury.
Responding to an email from the New York Times, a spokesperson for the United States Embassy in Beijing said that the unnamed employee was working in the US consulate in the city of Guangzhou, just northwest of Hong Kong, and experienced a variety of symptoms from late 2017 until April of this year. In statements to the BBC, she noted that the employee had been sent back to the US. Last Friday, the 18th of May, “the embassy was told that the clinical findings of [an] evaluation matched mild traumatic brain injury,” she wrote.
…Backdoor Account Found in D-Link DIR-620 Routers
Discovered by Kaspersky Lab researchers, this backdoor grants an attacker access to the device’s web panel, and there’s no way in which device owners can disable this secret account. To prevent abuse, Kaspersky researchers have refrained from disclosing the backdoor’s account username and password. The backdoor account (CVE-2018-6213) is just one of four vulnerabilities Kaspersky researchers found in the firmware of these devices following a recent security audit.
…New VPNFilter malware targets 100,000s of networking devices worldwide

For several months, Talos has been working with public- and private-sector threat intelligence partners and law enforcement in researching an advanced, likely state-sponsored or state-affiliated actor’s widespread use of a sophisticated modular malware system we call ‘VPNFilter.’ We have not completed our research, but recent events have convinced us that the correct way forward is to now share our findings so that affected parties can take the appropriate action to defend themselves. In particular, the code of this malware overlaps with versions of the BlackEnergy malware — which was responsible for multiple large-scale attacks that targeted devices in Ukraine.
…Over a dozen vulnerabilities uncovered in BMW vehicles

After 13 months of research, the team discovered 14 vulnerabilities which could place connected cars at risk of compromise. The tests were conducted with BMW’s backing and in laboratory conditions. Impacted vehicles are included in the automaker’s i Series, X1 sDrive, 5 Series, and 7 Series.
In total, as documented in Keen Security Lab’s technical report (.PDF), nine of the attack scenarios presented required physical access to the target vehicle, while five were based on using a mobile Internet connection. The vulnerabilities permitted attackers to access the head unit — otherwise known as the infotainment system — and T-box components including the Telematics Control Unit and Central Gateway Module of the vehicles involved in the tests, leading to the creation and deployment of exploit chains designed to seize control of CAN buses. The exposure of CAN buses to attack is a serious issue considering that these buses connect all of a car’s functions.
…Police use of Amazon’s face-recognition service draws privacy warnings

Amazon is actively courting law-enforcement agencies to use a cloud-based facial-recognition service that can identify people in real time, the American Civil Liberties Union reported Tuesday, citing the documents obtained from two US departments. The service, which Amazon markets under the name Rekognition, can recognize as many as 100 people in a single image and can compare images against databases containing tens of millions of faces. Company executives describe deployment by law enforcement agencies as common use case.
…